China blocking Tor: Round Two

Experts in China tell us Tor is not being singled out, that all "circumvention" tools are being subjected to the censorship regime of the Great Firewall of China as politically sensitive anniversaries come about. We also hear people in China need their privacy too, even if they never leave the Chinese Internet.
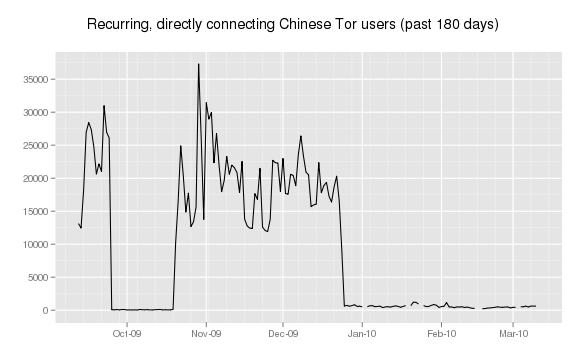
However, it appears China is getting better at blocking Tor. Here's a graph of returning users to the Tor Network from China:
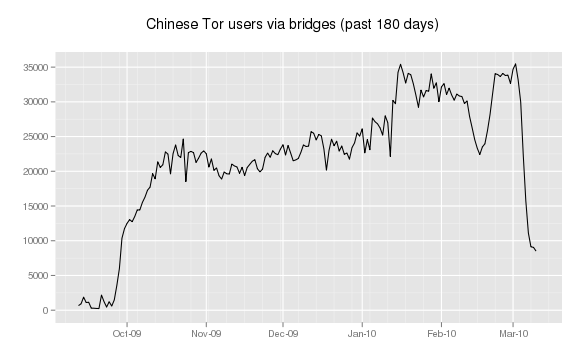
However, most Tor users in China switched to non-public relays, called bridges, over the past few months. Interestingly, the GFW has also started blocking some of the more popular bridges:
All of this data, and more, are available at http://metrics.torproject.org/.
Run a bridge, help someone else get to their favorite websites and forums.
Comments
Please note that the comment area below has been archived.
I would GUESS not but is
I would GUESS not but is there a way to tell if the bridge one was might be one that was blocked?
I have has problem after problem after installing the last two versions to the point of about giving up.
Excuse me a way to tell if
Excuse me a way to tell if the Bridge I was running has been blocked?
And again I would guess not as I had reinstalled and still am about to give up.
JustMe
Excuse me a way to tell if
Excuse me a way to tell if the Bridge I was running has been blocked?
And again I would guess not as I had reinstalled and still am about to give up.
JustMe
I'm currently behind GFW. I
I'm currently behind GFW. I added the bridges and am still blocked. :( It shows "establishing an encrypted directory connection failed (done)". I wonder how those 10k users climbed over the damn wall.
just repeat stop TOR/ start
just repeat stop TOR/ start TOR from the control panel as long as you get through, don't waste your time waiting for 'establishing encrypted ...'
TOR seems to memorise working constellations, so connect every day, otherwise you'll get stuck with TOR trying out previously working bridges.
If I can't get over the GFW,
If I can't get over the GFW, Can I a bridge?
To the Tor developers:
To the Tor developers: Please make all new Tor users bridges by default, not just clients.
it's hard to climb the GFW
it's hard to climb the GFW in China now.
yeah finally i get though
yeah finally i get though the GFW,it sucks!!
Some bridge works and some
Some bridge works and some doesn't.I use ping and telnet to check the bridges.All ping good,but some can't telnet ,and some return immediately with exit. The result of tor with these bridges is "establishing an encrypted directory connection failed (done)".And i tryed 2 day to find a useful bridge. With this bridge, ping and telnet return both good.
BTW,the captcha's image is
BTW,the captcha's image is too hard to read,i have try 3 times to get through.
I don't understand the link
I don't understand the link to 'http://metrics.torproject.org/' as it only appears to be "The Tor Translation Portal"? Do I need to register to see purty graphs?
http://metrics.torproject.org
http://metrics.torproject.org/ is the metrics portal. The Translation Portal is a different virtual host on the same IP address for now, but only at https://translation.torproject.org. What browser are you using that isn't requesting the website by name? If you request the website by IP address, you'll receive the translation portal.
Right, thanks for the reply.
Right, thanks for the reply. I've figured it out. I have the NoScript Firefox add-on configured to rewrite http:// to https:// on secure sites like *.torproject.org. It's just something I've done for a while now as I find a fair few https:// sites have a habit of falling back to http:// here and there if/when they mess up the hyperlinks, so I tend to force it for security. .............................................................................................................................
So any way, clicking http://metrics.torproject.org/ was being rewrote to https://metrics.torproject.org/ by NoScript which then ended up redirected by the server to https://translation.torproject.org/, I guess... :)
tor can vist anywhere,is the
tor can vist anywhere,is the real proxy. I can`t leave her. Now,chian has blocking bridge, I keep chang the bridge this svere days, so bad ,no one work.,even it cuold ping.
I try this three bridge 91.194.60.102:443
bridge 24.247.112.27:443
bridge 88.198.1.68:8080
right now ,but do not work.
( I use the free gate to get here. )
I am a Chinese who have just
I am a Chinese who have just successfully crossed the GFW, like six months ago the my tor intergrated within a firefox proved to be useless. I couldnot connect any server and even I luckly made one the speed was dreadfully slow. Now I am using an openvpn to browse your blog and I wanna know there is really no way to fight the GFW back and relive tor in China?
From our testing, using Tor
From our testing, using Tor in China requires bridges. China GFW is quite successfully blocking most of the public tor relays.
fucking crazy GFW, see my
fucking crazy GFW, see my middle finger.
I met the following problem:
"establishing an encrypted directory connection failed (done)".
I need help to over GFW now!
So GFW admins can send a
So GFW admins can send a 'get bridges' email and block new bridges as soon as they come out. I feel this is what is happening, I am having to Change bridges every other day. This was not the case 6 weeks ago.
Yes, they can. We take this
Yes, they can. We take this into account when giving out bridges. In order to share information, you have to assume the adversary is going to receive the information as well. Right now it seems China is blocking 50% of bridges given out via https. We've released bridge addresses via other methods since October that are 100% working even today.
waiting for you to deal this
waiting for you to deal this new challenge.
A Chinese Boy want freedom~~
did you try different port
did you try different port numbers in firewall settings in network section.
My Tor browser was working
My Tor browser was working past few days until last night. I have about 20 relays. So I definitely know some are getting through.
Everytime I tried to load Tor Browser (Tor/Polipo/Vidalia), tor.exe would crash.
WTF.......
tor.exe keeps crashing now,
tor.exe keeps crashing now, whats happening?
I am a college student in
I am a college student in China and have a new problem coming out in March that even if I use the latest bridge addresses sent by E-mail, Tor is difficult to be connected. I GUESS GFW is blocking bridges now and I hope we can have some counter-plans.
Same here in Beijing. Tried
Same here in Beijing. Tried a series of new private bridges. None works. I'm guessing its no longer a problem of bridges being blocked, but some essential function of tor is being blocked...
I see many users from China
I see many users from China on a bridge running here, so it might be that a lot of blocked bridges haven't noticed/reconfigured yet to fix the original problem.
You are right....After
You are right....After seeing your reply I emailed for new bridges again. Received four, one of which I didn't have and it connected.
Wellm spoke too early.
Wellm spoke too early. After a few hours, it stopped working again. Emailed again for new bridges, received four more new ones, but none of them actually work!
I agree with one poster above, maybe its time to make all new installs of the tor software as bridges by default. If p2p works, I can't see why each user being a bridge would not work.
The newest bridges got from
The newest bridges got from mail is not working.
Or maybe I have other problems in setting?
I've no idea...
Do u guys have the same issue here?
Yes. Unfortunately I have
Yes. Unfortunately I have the same problem. None of the bridges I got via email worked. Now am climbig the wall using psiphone. Not sure how long this will last. What are the other methods of releasing bridges that where talked above?
The ones on the website seem to be blocked too.
These guys are realy going on my nerves!
My experience is that the
My experience is that the GFW is monitoring the Gmail (from google) now, If a chinese send a mail to: bridges@torproject.org, GFW will automatically monitor the Gmail he used, they can read all they want to read in this Gmail, so the bridges will be blocked in a short time--after the GFW machine was set up. So the point is how to send and receive bridges safely.
r you sure???? gmail uses
r you sure????
gmail uses https
The gfw admins can sign up
The gfw admins can sign up for gmail too.
GFW is monitoring the Gmail
GFW is monitoring the Gmail now, so the problems above are just so so ...
The piont is how to send your mail safely. Windows OS is just not safe !
I really don't understand
I really don't understand any of this. After this first happened my bridge stopped being used, usually 1000+ chinese users in my "who has used your bridge", then a couple days later 1-8 chinese users and now 50+ chinese users again? how can they still be connecting?;o
I don't know but maybe some
I don't know but maybe some connections manage to successfully negotiate the 3-way handshake to register as someone "who has used your bridge" before the DPI resets the connection. I have no idea but just a thought.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Is the bridge still blocked? Have you reconfigured the ORPort yet?
Yes, now 2k+ users in who
Yes, now 2k+ users in who has used my bridge from china again!
Don't Chinese's
Don't Chinese's patience....Until now I have changed about 30 groups of bridges
Once a time the Chinese didn't know how to suf the net via the bridges, and then your chinese users was little but now many Chinese knows it. so....
Let me suggest.... 1. People
Let me suggest....
1. People can only get latest bridges through gmail account that are already registered 2 or more months.
2. People can not get bridges through bridges.torproject.org ( I found it's very easy to get a lot of bridges by simply clicking button "Use a New Identity" and refresh page)
3. Reduce the number of bridges display given to 2 bridges each time.
GFW starts blocking bridges.... oh my God....
torproject should change the
torproject should change the way they provide bridges, email is never safe.
We give out bridges via 6
We give out bridges via 6 different methods. email is only one. We assume an adversary is going to try to discover all methods and therefore all bridges.
However to average users
However to average users like me, only one method seems available: through gmail.If that's the case, whats the point?
bridges are offered by
bridges are offered by gmail, website, qq account, twitter account, and two other methods that aren't via internet.
what happens if they start
what happens if they start blocking all of google? maybe we should be able to send e-mails through yahoo as well?
Is there a way to use the
Is there a way to use the metrics to generate user statistics on any country? There are numerous graphs pre-generated for a couple dozen countries, but how would I see the number of users in Russia over a period of time?
yeah, i'm out..thank you for
yeah, i'm out..thank you for all your working
Hi there, Thanks for you
Hi there,
Thanks for you guys doing this. I have a business in China and need to use google sites in China.
What I recon is to charge for the bridges(100RMB/per year) and you guys can secure the bridges links(rather than simply sending auto-reply emails), not for every one to use. The user has to pay.
Currently, GFW seems blocking most of bridges, I tried couple of these yesterday. Neither worked.
What do you think?
Not good idea, GFW also can
Not good idea, GFW also can pay it and block it.
GFW techs work for a boss
GFW techs work for a boss that can pay for the bridges... So each person should get different bridges. . . That might have a chance... but they already know who are the TOR users, and can intercept information about bridges...
Not good idea, GFW also can
Not good idea, GFW also can pay it and block it.
today I see TOR is working
today I see TOR is working VERY NORMALLY and VERY FAST. Did GFW act up or did it quit for now?
Could this change be a trap or something?
The game needs to change! If
The game needs to change!
If you are in China, any innovations TOR comes up with, will be picked up by the GFW staff, who are not particularly concerned with the material being blocked, but with the game of blocking.
Even if you have https:// for Google mail, the GFW techy too can get an account and find the new bridges as they come out. The Chinese techy has the advantage: has access to the Tor Project site; thus any solutions discussed here, will be accessible to the GFW Tech staff. He also has access to email, thus they can also know who is using the bridges, and stay alert to everything that person connects to. So they'll find a way to break it too. So they need to monitor a limited number of users, and with that alone, they will keep TOR from working in nearly 99% of the cases.
How does TOR staff know someone coming here, or mail inquiry sent, isn't a GFW techy getting ready to hijack the new solutions?
Internet traffic out of China is routed through a handful of servers in various regions. Thus, cataloging, and filtering and staticizing gives the GFW technicians the best of all worlds. The number of people attempting to cross the GFW is so huge, that a police solutions would be impossible, thus a technical solution is preferable, and is the solution that will be pursued.
So guys, put your thinking caps on. Remember: any viable solution presented in this site can be read by the GFW folks.
I posted this about 6 hours
I posted this about 6 hours ago (actually something similar, since I didn't keep a copy), and I don't see it the thread, so maybe it went into the void.
The author of the main article naively states, "it appears China is getting better at blocking Tor."
GFW personnel (or any other country that practices blocking sites), are quite experts at the same stuff US and other countries' wizards of cyberspace. They also have the advantage that they themselves are are not blocked (why would they? They're running the blocks and will list their IP, etc. as exceptions). So they are a step ahead of the general public, and a small step behind TOR, since they can come here, and be infiltrating subscribers... they may even be contributing code for each of the fixes.
So it's time to change the game, and find ways that can't be so easily penetrated...
I had an interesting thought... why would so much money be spent on blocking 3500 connections? (Assuming the graph is in units of 1.) And how easy it is to make lists of the people who live where the attempting computer or Internet connection is...
Here is an idea:
Here is an idea:
first, find a firiend out of the GFW.
second, ask your friend to get bridges through: bridges@torproject.org
third, your friend send an email with the bridges to you, Attention! The key words must be like this way to avoid the GFW: b#ri#dg#es(bridges), and so on....
fourth, you get the bridges.
The gfw can't monitor all of the sending and receiving of the Email of everyone. the one who just receive an ordinary email from his/her friends won't get the attention of the GFW.
My tor just keeps
My tor just keeps starting.
And the message log says:
[20:48:12] DNS Hijacking Detected - Tor detected that your DNS provider is providing false responses for domains that do not exist. Some ISPs and other DNS providers, such as OpenDNS, are known to do this in order to display their own search or advertising pages.
Well,who can help me with this?
I knew little about what you
I knew little about what you said, I only know that GFW is doing something to the DNS server, such as the one in Taiwan. Some days ago Taiwan said they have to clean the DNS pollution that did by "some people"......
I want to connect the tor
I want to connect the tor with two computer systems, but i don't know how to go about it. Please if there is anyone who knows how to connect it with 2pcs. plz get in touch with me through this email addess: alabondotun@yahoo.com
help...GFW blocking
help...GFW blocking Tor...even the bridges don't work...HELP!!!
same here, no bridges
same here, no bridges working anymore
Yesterday afternoon [China
Yesterday afternoon [China Time] the bridges published on the website were all three working. By this morning they are all unreachable.
The bridges published today are not working either.
It seems the Chinese government is seriously increasing its efforts to block TOR. We must be getting closer to June 4th.
Another day without any
Another day without any working bridges. so sad...
We need HELP, seriously.
Yes. china has blocked all
Yes. china has blocked all bridges that were served up via https://bridges.torproject.org. email, qq, and social network bridges continue to work. you should find some of those.
so where can I find the
so where can I find the social network bridges?
You'll find them on one of
You'll find them on one of the most well known social networks. However, you will not be able to see them until you are granted access.
Note that they were working OK until this morning. (China Unicom, Beijing)
In my own experiences,
In my own experiences, sometimes I may connect to the Tor network directly(Start>All Programs>Vidalia Bundle>Tor>Tor)while having difficulty to do so via the Vidalia Control Panel. I check it out with Wireshark, and it turns out when connecting via the Vidalia Control Panel, Tor contacts the Directory Servers first(which might be down), then the Relay Servers. This might not work if all the enlisted Directory Servers are down. On the other hand, if I try to connect to Tor directly, Tor contacts the Relay Servers from a cache(I haven't figured out where it is), hence it works.(Though all the Directory Servers were blocked, some of the Relays might not be)
So here is the strategy for this difficult period of time:
Try to collect working bridges from e-mail, https://bridges.torproject.org or whatever you got, run Tor from the Vidalia Control Panel and collect some Relay info while you are surfing happily. Next time, when the Vidalia Control Panel doesn't work, don't panic. Just run Tor directly, it might bounce you out of the Matrix. And of course from time to time, you need to collect some reachable Directory Server to repeat this process to make sure the cache has a reachable Relay.
So far this hasn't failed me yet and good luck with you guys.
For me, I always use the traditional proxy solution as a fallback strategy. If you don't know any, I recommend Google's VTunnel.(But there are really tons of them out there)
Jerry Mouse
--Who always defeats the Big Bad Cat
Just some thought on how to
Just some thought on how to prevent easy access to bridge ip addresses, and thus being blocked: Maybe we can consider some sort of encryption, say encrypting the addresses with a public key and decrypting with the private key only Tor knows. In theory, unless this private key is leaked, there is no way to retrieve the real ip address easily. Although someone can still sniff the network to find out where the network traffic goes (If there is a way to disguise this, it would be more effective. However, doubt it!), the cost to find out the real ip increases significantly and the whole process is hard to automate. Hopefully with this, the speed to add more bridges will outpace the speed of being blocked. Not a security expert, but just my 2 cents for Tor developers to consider. I believe together "freedom of speech" we can protect.
It seems impossible to get
It seems impossible to get working bridges anymore through email. It's like they have finally found a way to block Tor in China. No matter how many bridges I get they all seem to get stuck on Problem bootstrapping stuck at 10% Finishing handshake with directory server DONE. Can any of the people who created Tor help us?
ask others how they have tor
ask others how they have tor working in china, use their bridges.
I tried TOR with bridges.
I tried TOR with bridges. But I also suffered from the problem of "bootstrapping stuck at 10%".
I am very angry with the recent blocking of one of my favorite website. I swear I will find a way to penetrate the G*F*W.
Thanks the contributors of TOR anyway. I am grateful with all your efforts.
you just need different
you just need different bridges.
hello i'm not from china but
hello
i'm not from china but my isp blocks internet connection.
i not able to connect the tor network' i always get the same announcement.
"establishing an encrypted directory connection failed (done)"
i replaced several bridges,but it won't help.
any idea?
thx
more bridges is the answer
more bridges is the answer for now.