Measuring Tor and Iran (Part two)

Two weeks ago we posted early measurements about the growth of Tor usage in Iran. Since then we have improved our math, and used more data sources. This work is part of our metrics project, where we're learning about the Tor network to improve its availability and performance while keeping our users safe.
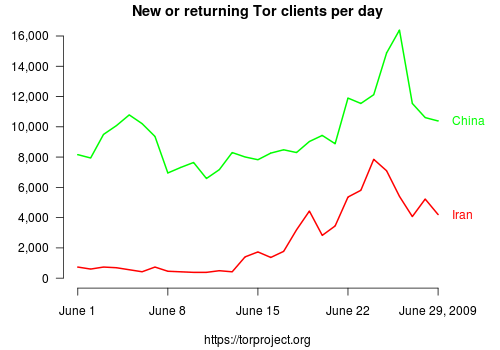
The first graph shows the estimated number of new and returning Tor clients per day coming from China and Iran. So for example, there were around 7800 new and returning Iranian Tor users on June 24. By "returning", we mean Tor clients that were off for at least several days, so they didn't have cached directory information. We added China as a comparison for the Iran numbers: you can see the results of the recent Green Dam fiasco and attempts to block Google services. Many more details and math are here.
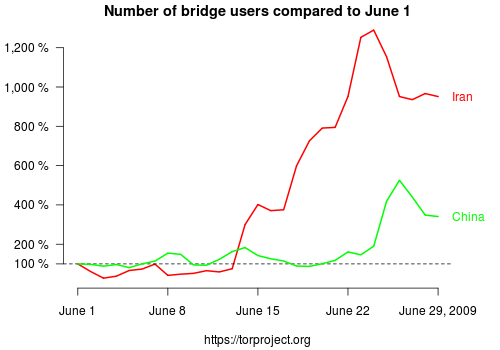
The second graph shows the growth in bridge users coming from Iran and China. Bridges are like normal relays except that they are not listed in a public directory and therefore they're harder to block. We show "growth compared to June 1" because we don't yet have a good estimate of the absolute number of bridge users. The number is probably an order of magnitude smaller than the number of "regular" Tor users. But still, we can say that bridge usage from Iran has boosted to 950% as compared to June 1. For more information on these numbers see this report.
While it is great to see that so many people in Iran find the Tor network useful, we should continue our attempts to make Tor even better. Your contribution could be to set up a bridge or relay as many others recently did. You might also consider setting up an exit relay, possibly with the help of these instructions. But middle nodes and bridges are helping as well!
Comments
Please note that the comment area below has been archived.
special build to help iran?
hi there,
is it possible to have a special build only allowing my exit node for clients originating in china, iran etc.? unfortunately i don´t know very much about this software but am unwilling to hassle with problems from my isp. right now i´m running only in bridge mode.
i think there might be a lot more people out there like me that would install a special iran package without having to think about it anymore
ftd
not likely
It is not possible for an exit node to know the originator of requests, without sniffing the data (violating user privacy and legally endangering yourself).
This is false: there's no
This is false: there's no *technical* way for the exit node to know the client except with collusion with other nodes in the circuit. If only legal consequences be the stopper for the exit node to figure out the client then Tor would be dead before birth.
Chinese people need tor to
Chinese people need tor to surf the internet freely indeed.
Tor is blocked in Iran; bridges do not work
Tor is apparently blocked in Iran and nothing happens when you try to connect hrough Tor... the relays list is empty... even bridges do not work... disappointing... really disappointing.
seems the situation in Iran
seems the situation in Iran is worse than China....
Tor works fine in Iran
It depends upon your network. Tor is working fine for me in Iran.
Some user from China say
Some user from China say can't connect the tor network these days, but it's work fine for me since the beginning.
tor is fine in iran
i use tor in iran since the election and its working for me but it is really slow....another thing i use macos maybe this why...
Please keep everyone updated
Please keep everyone updated about the status of TOR connection in Iran. If demonstrations intensify again soon, it would be good to coordinate to provide them with more relays.
tor doesnt work here
from now on tor doesnt work in iran...i there is no tor connection anymore and i used every bridge i could find..plz inform me what i have to do?
i have macosx and use tor network via vidalia
plz inform me
re: tor doesnt work here
You should some people running bridges, or follow the directions at https://www.torproject.org/bridges#UsingBridges
TORCHAT
Why there is no info on torproject.org about torchat?
It seems to me easier to quickly deploy for oppressed people.
Is't a bad project? (compared to trying to use tor+pidgin+pifgin-otr, not easy on *nix boxes?
http://en.wikipedia.org/wiki/TorChat
http://code.google.com/p/torchat/
re: TORCHAT
Because we don't produce torchat and no one has thoroughly analyzed the code. Feel free to submit a detailed security analysis.
how i can create a tor-mingw" dir
https://git.torproject.org/checkout/tor/master/doc/tor-win32-mingw-crea… <--- check this out...
i can't create a "tor-mingw" directory
please help me;;;;
it's easy
"mkdir tor-mingw"
The tor nodes in China
The tor nodes in China increase in recent months.
https://blog.torproject.org/blog/measuring-tor-and-iran-part-two
Thank you, you answered the question I have been searching for which was whether or not to place keywords when blog commenting. mirc . chat . http://www.hayda.net/