Tor Browser 7.5 is released

The Tor Browser Team is proud to announce the first stable release in the 7.5 series. This release is available from the Tor Browser Project page and also from our distribution directory.
This release features important security updates to Firefox.
Apart from the usual Firefox security updates it contains some notable improvements compared to the 7.0 series. Here are the highlights:
-
We redesigned parts of the Tor Browser user interface. One of the major improvements for our users is our new Tor Launcher experience. This work is based on the findings published at 'A Usability Evaluation of Tor Launcher', a paper done by Linda Lee et al. At our work we iterated on the redesign proposed by the research, improving it even further. Here are the main changes we would like to highlight:
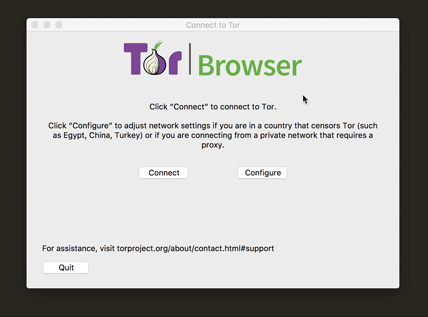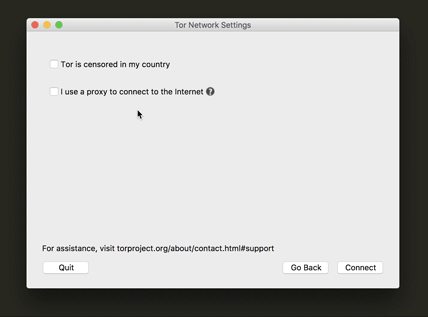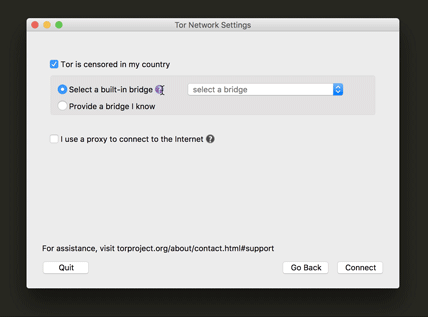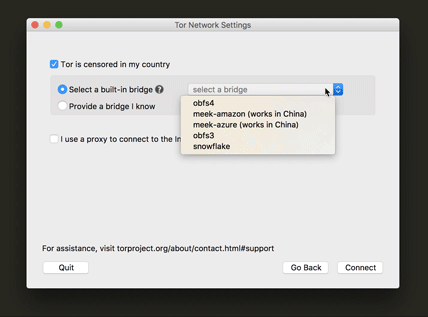
Welcome Screen
Our old screen had way too much information for the users, leading many of them to spend great time confused about what to do. Some users at the paper experiment spent up to 40min confused about what they needed to be doing here. Besides simplifying the screen and the message, to make it easier for the user to know if they need to configure anything or not, we also did a 'brand refresh' bringing our logo to the launcher.
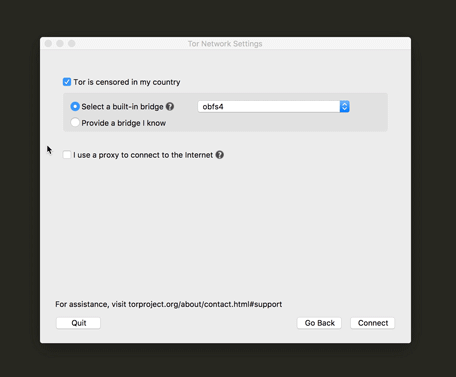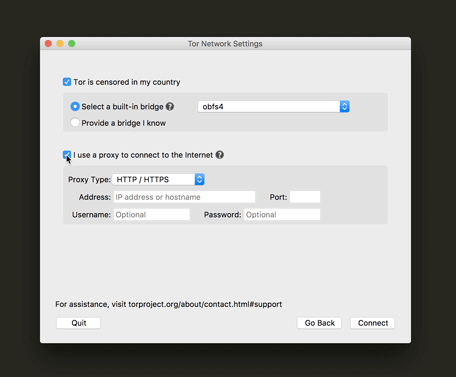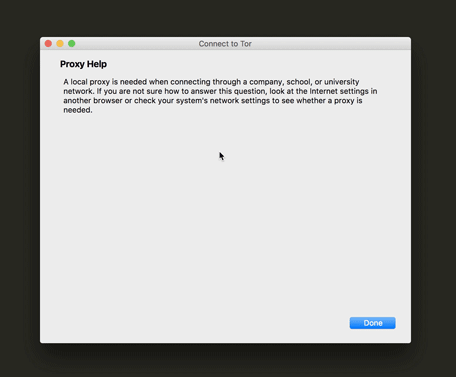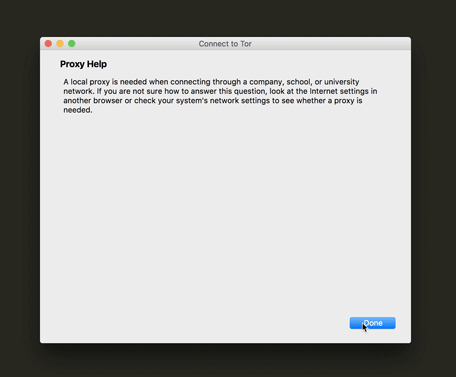
Censorship circumvention configuration
This is one of the most important steps for a user who is trying to connect to Tor while their network is censoring Tor. We also worked really hard to make sure the UI text would make it easy for the user to understand what a bridge is for and how to configure to use one. Another update was a little tip we added at the drop-down menu (as you can see below) for which bridge to use in countries that have very sophisticated censorship methods.
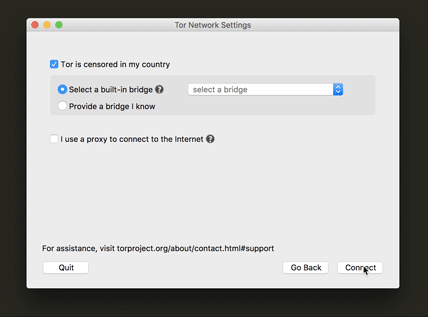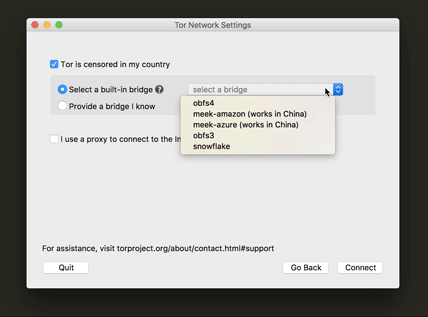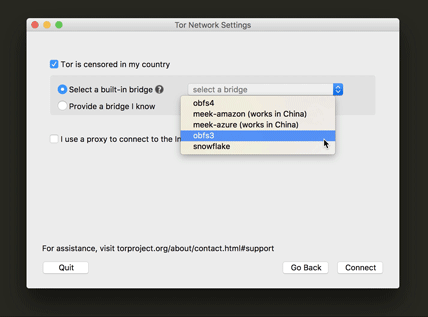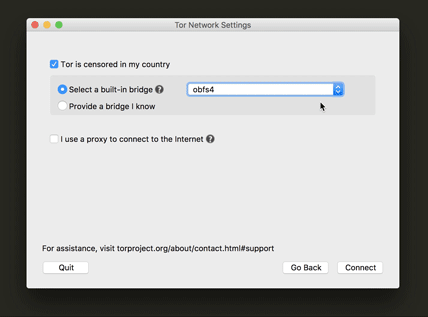
Proxy help information
The proxy settings at our Tor Launcher configuration wizard is an important feature for users who are under a network that demands such configuration. But it can also lead to a lot of confusion if the user has no idea what a proxy is. Since it is a very important feature for users, we decided to keep it in the main configuration screen and introduced a help prompt with an explanation of when someone would need such configuration.
As part of our work with the UX team, we will also be coordinating user testing of this new UI to continue iterating and make sure we are always improving our users' experience. We are also planning a series of improvements not only for the Tor Launcher flow but for the whole browser experience (once you are connected to Tor) including a new user onboarding flow. And last but not least we are streamlining both our mobile and desktop experience: Tor Browser 7.5 adapted the security slider design we did for mobile bringing the improved user experience to the desktop as well.
- We ship the first release in Tor's 0.3.2 series, 0.3.2.9. This release includes support for the Next Generation of Onion Services.
- On the security side we enabled content sandboxing on Windows and fixed remaining issues on Linux that prevented printing to file from working properly. Additionally, we improved the compiler hardening on macOS and fixed holes in the W^X mitigation on Windows.
- We finally moved away from Gitian/tor-browser-bundle as the base of our reproducible builds environment. Over the past weeks and months rbm/tor-browser-build got developed making it much easier to reproduce Tor Browser builds and to add reproducible builds for new platforms and architectures. This will allow us to ship 64bit bundles for Windows (currently in the alpha series available) and bundles for Android at the same day as the release for the current platforms/architectures is getting out.
The full changelog since Tor Browser 7.0.11 is:
- All Platforms
- Update Firefox to 52.6.0esr
- Update Tor to 0.3.2.9
- Update OpenSSL to 1.0.2n
- Update Torbutton to 1.9.8.5
- Update Tor Launcher to 0.2.14.3
- Bug 23262: Implement integrated progress bar
- Bug 23261: implement configuration portion of new Tor Launcher UI
- Bug 24623: Revise "country that censors Tor" text
- Bug 24624: tbb-logo.svg may cause network access
- Bug 23240: Retrieve current bootstrap progress before showing progress bar
- Bug 24428: Bootstrap error message sometimes lost
- Bug 22232: Add README on use of bootstrap status messages
- Bug 10573: Replace deprecated nsILocalFile with nsIFile (code clean-up)
- Translations update
- Update HTTPS Everywhere to 2018.1.11
- Update NoScript to 5.1.8.3
- Bug 23104: CSS line-height reveals the platform Tor Browser is running on
- Bug 24398: Plugin-container process exhausts memory
- Bug 22501: Requests via javascript: violate FPI
- Bug 24756: Add noisebridge01 obfs4 bridge configuration
- Windows
- OS X
- Linux
- Android
- Bug 22084: Spoof network information API
- Build System
- All Platforms
- Switch from gitian/tor-browser-bundle to rbm/tor-browser-build
- Windows
- Linux
- All Platforms
Comments
Please note that the comment area below has been archived.
WOOOOOOOOOOHOOOOOOO…
WOOOOOOOOOOHOOOOOOO SNOWFLAKE COMES TO Tor Browser Stable BUILDS FINALLY (for Linux and Mac) :D :D
To run a Snowflake bridge:
I'm not sure when the Snowflake addon will be available but it will make running a Snowflake bridge so much easier!
Snowflake is not yet…
Snowflake is not yet included in the stable series. It is still in the alpha series only.
lol the second gif contained…
lol the second gif contained it and I thought it was made from the stable series.
WebRTC? iFrames? Javascript?…
WebRTC? iFrames? Javascript?
Are you a fan of the usage of Adobe Flash for privacy solutions as well?
WebRTC? iFrames? Javascript?…
Please read on Snowflake's architecture instead of making ridiculous assumptions.
Not the same anon, but…
Not the same anon, but architecture means nothing if static client source can't be guaranteed.
Not that ridiculous as long…
Not that ridiculous as long you have any basic perception on internetsecurity issues that are going on in this world.
Simple reading about basic security and the misfit of webrtc technology (and iframes, javascripts and flash as well).
"Uncovering 2017’s Largest Malvertising Operation"
https://blog.confiant.com/uncovering-2017s-largest-malvertising-operati…?
Enabling Webrtc in Torbrowser (or actually any browser) and allowing iframes as well is just a kind of bizarre view on privacy and security because this technology 'talks too much!' and both are also a security risk you should not allow.
Just some simple reading, no professor techtalks about architectures, that's all it takes to get both feet on the ground again.
Do you know the difference…
Do you know the difference between opening a SINGLE TAB that has iframes, WebRTC, JS, from a trusted website, and between allowing malvertising?
Malvertising is the example…
Malvertising is the example for the misusage of techniques.
Fingerprinting (allowing webgl also) needs you to allow javascripts and webgl, or webrtc and iframes makes phishing techniques more possible.
Why? Moste people do not have any clue what is happening on many websites and who they are connecting to besides the domain they see in the url bar.
But, it is not the criminals we are afariad for here right? This website, Torproject is mainly about other people that are a threat to innocent people. And these people just use the same techniques criminals are using and vice versa.
So, tell me, why is it a good idea to just cooperate in advance with the people that are threatening you by making your defence ultimate weak by allowing javascripts, wengl, iframes and audio video tecnique that can reveal your identity?
And that is what someone make a litlle dance of joy for, a mindset of people lowering their torbrowser settings itstead of seeting hat security in its highest modus and forbid those iframes.
No iframes and no javascripts is less attack surface, but yes indeed it has the downside for the social media addictive, you do not see your favorite twitter or instagram images right away.
Another side o this topic, bandwith, I would be curious what would happen with Tortraffic if everybody that uses torbrowser was just blocking iframes for one day.
Would it drop by 5 times or more?
Our addiction (or yours) tot social media is already a big threat to the world, do not make it more worse by forcing people tot allow more usage of javascript, webgl, iframes and this webrtc profiling sjt.
The best browser is a clean browser and it seems already an enormous challenge for torproject (and mozilla users) to be aware of all the new fancy rappy things in every new release and take in out or break again to end up with a clean, safe browser.
Technique is ment to serve people and not to threaten people, when it does both, you shoul strongly consider tot completly avoid that technique or at least as much as possible.
You can do that certainly with iframes, webgl and webrtc, and a lot of times with a lot of javascropt too, just loo at the loading time of many pages and how many domains are passing underneath the browser screen.
The more you block, the faster the loading, the lower bandwith, the safer browsing.
Keep it as simple you can get, because mozilla has shown at least the last 5 years how many trouble you get if you are taking that other direction some people would say the bloatware direction, i would say the unneccesary complicated direction.
Keep that esr version clean!
Put the safety setting higher and don't 'bend as a service' for the people that are a threat to you by lowering your security because of all the easyness and fancy new shiny stuff.
yes, and unfortunately a…
yes, and unfortunately a longer (reasonable) answer was censored (again, happens a lot over here last years).
I don't think so. Please be…
I don't think so. Please be a bit patient of posts are not shown immediately especially when a weekend is involved. We don't have many moderators for this blog.
sorry for that, this time…
sorry for that, this time you were completely right. sorry for that.
Just wanted to say that I am…
Just wanted to say that I am often frustrated when my comments do not appear, but I always try to bear in mind the point gk just made---which has been pointed out in this blog before, but probably bears more frequent repetition.
Among "cosmetic" changes I'd like to see ASAP are:
o reorganize torproject.org website to present first the most recent and the most useful to the greatest number of Tor users, especially new Tor users,
o regular Friday "ask anything" blog where commentators can worry over potential security flaws, propose new features, etc., and get some feedback from TP,
o refactor the blog to eliminate annoying issues which appear to be related to Javascript, improve rapid posting of thoughtful comments, improve spambot resistance, etc.
o faster TP response to emergencies (IMO the Meltdown/Spectre qualifies as something which would obviously cause considerable concern among well-informed Tor users),
o better communication in other languages (e.g. Spanish).
But I realize that TP has very limited resources and I accept that just now it may be more urgent to direct key Tor people to work on researching the latest technical attacks, fixing bugs, reaching out to the media and to policy makers, etc. etc.
Sometimes we all just need to try to be patient and to save our strength for the biggest current threats.
Just chiming in so forgive…
Just chiming in so forgive me if I missed something, but the simple answer regarding features in single tabs is that Firefox is largely a single-process browser. AFAIK currently there is no strong degree of isolation between tabs. At least that was historically the reason Torbutton never had tab-by-tab modes, it was either on or off for the whole browser. In other words: because technical reasons.
As another commenter mentioned, malvertising isn't really any different from any other use of those features.
Love it !! Thanks to all the…
Love it !! Thanks to all the people working together.
Maybe something good will come out of the bad...
Thanks so much
Peace and Susunzi
Thanks for your work…
Thanks for your work.
Is this version already build with selfrando?
No, selfrando is still in…
No, selfrando is still in the alpha series only.
I know some of you (o/ tjr)…
I know some of you (o/ tjr) aren't very excited about Selfrando, but will it be available for stable release before the next switch to the new ESR? And what will be its future in the 60 ESR roadmap?
We have https://trac…
We have https://trac.torproject.org/projects/tor/ticket/23073 detailing the requirements for getting it into the stable series. There is not much left to be honest but it did not get the priority for 7.5. I am not sure when it will be included to be honest. Patches are welcome!
21:30:44.932 browser…
21:30:44.932 browser.ownerGlobal is null 1 ext-utils.js:800
getBrowserId chrome://browser/content/ext-utils.js:800:9
chrome://browser/content/ext-tabs.js:79:26
runSafeSyncWithoutClone resource://gre/modules/ExtensionUtils.jsm:71:14
emit/promises< resource://gre/modules/ExtensionUtils.jsm:384:55
from self-hosted:595:17
emit resource://gre/modules/ExtensionUtils.jsm:383:20
WebRequestEventManager/register/listener chrome://extensions/content/ext-webRequest.js:51:7
runChannelListener resource://gre/modules/WebRequest.jsm:721:24
errorCheck resource://gre/modules/WebRequest.jsm:568:7
observeActivity resource://gre/modules/WebRequest.jsm:536:12
hi…
hi
1-TorBrowser is soo slowly in mac os,(just 2mb/s)
how can speed up?
-
2-in TorBrowser content, cant find "torrc" file to use this solution for speed up:
https://www.youtube.com/watch?time_continue=23&v=W1NlylDyzCU
Half of the us (and many…
Half of the us (and many other parts in the world) wished they had an internet connection of 'just' 2 mb a second.
Does it give just two mb with torrent sharing and big downloads, then it could be on purpose.
> cant find "torrc" file to…
> cant find "torrc" file to use this solution for speed up
Please don't do this. The link redirects through multiple ad splash pages, one of them blocks you if you try downloading it over tor, it asks you to install a third-party file without explaining what it does or link you to documentation, all of which are suspicious before you get the file. But then if you overwrite the default tor configuration with this completely unreviewed one, it could make your traffic stand out from other tor users, or it could force your tor traffic through an adversarial node. You have no idea unless you read tor's documentation and understand exactly what configuration the file applies and whether that configuration is safe. Think. You would be overwriting highly-secure privacy software with a file given to you by some random Joe on the internet.
Get better internet, I have…
Get better internet, I have used tor browser on windows 10, and 2 different linux distros and they all worked fine, its you.
> Get better internet,…
> Get better internet,
"Let them eat cake"?
This kind of attitude is self-defeating for the Tor community. We must persuade/help "ordinary people" all around the world to use Tor (wisely). Unkindly suggesting they have only to blame if they live in a region where few alternatives are available when it comes to Internet providers only helps our enemies.
I've been having a similar…
I've been having a similar problem. Starting roughly the same time all of my systems can only get about 25kbps over Tor. This includes a Qubes desktop on WiFi and an android phone on 4G. Really odd considering everything is different between then, including the ISP. I used to get around 1Mbps. The problem is still going on, and I think it might have something to do with recent versions of Tor, but I don't really know.
Point is I've never gotten anywhere near 2Mbps over Tor before. (And if you're talking 2MB/s and not 2Mbps, that's 8 times more insane.)
Is there any more…
Is there any more information about Tor Browser for Android? Or is all the information just related to Orbot?
We are working on Tor…
We are working on Tor Browser for Android. We have hired two developers a while ago and are preparing the move from Orfox to Tor Browser for Android. We hope to have at least alpha releases up later this year.
Thanks for telling us!
Thanks for telling us!
Will there be an Orbot…
Will there be an Orbot update in the interim? I'm stuck on 52.2 on Intel Tegra with Reading Mode not working at all.
The Guardianproject folks…
The Guardianproject folks are updating Orbot from time to time. So, yes, I guess there will be updates available until we launch Tor Browser for Android.
Just thanks!
Just thanks!
Mozilla has destroyed their…
Mozilla has destroyed their browser and you seem to act as if it's no problem. Webextensions fundamentally does not work with a hardened, locked down browser. If you harden in about:config and disable javascript APIs, extensions lose access to these APIs as well, meaning if you need certain security tools to have access to these APIs there is no way unless the browser is fundamentally redesigned to prevent javascript that is run (not that I would recommend running any) by third party sites from also accessing these APIs. Separate javascript contexts must be set up such that specific APIs can be enabled for each extension as necessary, and then the old setup of having as many APIs disabled as possible can be maintained for the 3rd party site context. If someone were being ambitious, a system that intercepted API calls in each of these contexts and listed requested APIs and allowed the user to selectively allow/deny specific calls for the browser session or permanently, etc would be great. However, the chances of anything like that appearing are zero.
Mozilla every day makes their browser more and more dumbed down. I ask both Mozilla and TorProject to please stop the PR and focus on power users, the only users you have left who care about you at all, instead of promoting the incompetent, clueless users which Silicon Valley has managed to churn out worldwide. Perhaps if you focused on power users, we'd have less "regular users"!
Mozilla keeps whitewashing core issues, adding intrusive bloat/spyware and entertaining the ignorant userbase with more nonsense, while in the background they neuter and reduce configurability of their browser often without discussion, and destroy the tiny bit left of their competent userbase. The main thing Firefox had over Chromium was its configurability and ability to be manually yet practically hardened according to a power user's needs, which only Chromium's developers historically reacted to with hostility, but now it would seem that same culture of hostility has infected Mozilla, which alongside their incompetence is a great mix. What a shame. Using the argument of "security" is laughable at best. Yes the old extension systems had core security issues. However, I really don't see how webextensions has really solved this. In fact that it relies on the same javascript engine as third party websites in some ways it has actually reduced security. The main thing that was needed was isolation, removal of bloat, permissions system that controlled API access, etc. Webextensions brings little of value and actually makes the browser more exploitable in certain scenarios.
I hope the TorProject does not let itself be entirely compromised since it relies on Mozilla for a browser, and instead voices these issues, because otherwise frankly TorBrowser will be just as dead as Firefox, which would be a shame.
So please TorProject, avoid the PR and nonsense, focus on securing your browser and making it practical/configurable for power users instead of wasting all your time on a userbase that are already too far gone to save.
+1
+1
+1
+1
+1
+1
If you harden in about…
If you harden in about:config and disable javascript APIs, extensions lose access to these APIs as well
That is not an issue for the Tor Browser Bundle. They maintain a fork of firefox, so there's nothing stopping them from just moving the old XUL code to the browser core itself and shunning add-ons altogether. Nobody should ever be installing any new add-ons or changing any settings anyway, to avoid getting fingerprinted.
> Nobody should ever be…
> Nobody should ever be installing any new add-ons or changing any settings anyway, to avoid getting fingerprinted.
On the one hand, I agree with this as general advice. Smart Tor people who have thought hard about many sides to various issues, and who probably know more than we do, are making decisions in an effort to keep most of us mostly safer, and we need to mostly trust them to make the decisions, in the current threat environment, which provide the most benefit for the most Tor users.
On the other hand: the slider is intended as a (necessary) compromise between two competing realities, both of which must be recognized:
o providing anonymity demands everyone look the same, as far as possible
o at-risk people confront a very different mix of likely threats depending up real time details of where they are, who they are associating with, what they are doing with electronic devices, etc.
So adjusting the security slider is one change which IMO every Tor user should feel free to make according to his/her best estimate of what makes most sense for them personally in the moment in terms of the trading better security for worse anonymity or vice versa.
Yes, that's true. What was…
Yes, that's true. What was meant I believe is to avoid messing with
about:configvalues or other customizations which are not governed by the security slider.I hate to rain on your…
I hate to rain on your parade because you make a lot of really important points here, but
1) the documentation strongly discourages installing extensions in Tor Browser, and
2) the documentation strongly discourages changing about:config settings
because both can make you vulnerable to fingerprinting attacks. Actually it's pretty much guaranteed if we're talking about after-market disabling specific JavaScript APIs.
the webextension version of…
the webextension version of noscript is inferior to the xul version, so quantum/webextensions in esr will be a threat to tbb.
"webextension version of…
"webextension version of noscript is INFERIOR [...]"
An understatement -unfortunately )-:
https://hackademix.net/
thanxx
thanxx
I share your frustration…
I share your frustration about some design decisions, but I think you need to take a much wider view to appreciate all the factors which go into making them.
Tor Browser and other products are built by Tor Project, an NGO based in the US with a handful of paid employees and precarious funding. Even as Tor software products are subjected to endless technical attacks by well funded enemies, Tor Project is subjected to increasingly dangerous legal and political attacks. To counter the former, we need Tor Project to continue to exist. Obviously. And to ensure that TP continues to exist, IMO it is essential to *grow* the userbase worldwide, not to *shrink* it as you seem to want to do.
Let me point out two specific reasons why this point should be self-evident.
First: for years many Tor users around the world expressed increasing concern that TP's funding mostly came from sources tied to obscure portions of the US State Department or even USIC. Further, as all the worlds governments continue to shift towards dramatically increased authoritarianism, those "freedom-building" portions of the USG have come under increasing attack within "the swamp", seriously endangering their continued existence. This could lead to most TP funding simply disappearing, almost overnight.
Further, many users who depend upon Tor have expressed concern that because the USG has provided most of the funding for TP, the USG inevitably will exert undue influence upon TP policy decision and even technical decisions which could perhaps result in opening up holes of which Tor developers are unaware. (C.f. NSA's manipulation of NIST to weaken cryptographic protocols in obscure ways which no-one noticed.) As a result of these concerns, when Shari Steele became CEO, she made it a priority to evolve TP away from a funding model dependent upon highly endangered USG grants and towards funding based upon direct user contributions, similarly to US based NGOs such as ACLU and EFF (Steele previously worked at EFF). And clearly, to succeed in this, TP needs to greatly broaden the user base for Tor products, not to shrink it.
Further, it is clear that all around the world The People are calling for more privacy, even in CN. Tor products are among the very few which are available right now, are battle-tested, and usable by most non-technical citizens, and IMO as a matter of principle, the US tech world (which bears some responsibility for enabling NSA's "collect it all"/"pwn it all" global dragnet) has an urgent moral obligation attempt to redress NSA's abuses by providing privacy/security/anonymity-enhancing tools like Tor.
Second: Former FBI Director Comey, current FBI Director Wray, and deputy AG Rod Rosenstein are among the senior USG officials who have been insistently calling that a divided, weak, and self-loathing Congress slip a provision into some law which would outlaw non-backdoored encryption in the USA, which means to some extent, almost everywhere. Tor Project has repeatedly stated that the project will never put a secret federal backdoor into Tor. Assuming they mean, "not even under threat of imprisonment", if the provision which Rosenstein and the others demand are enacted (probably in dead of night, with no debate, in the context of a rider on some last second attempt to avoid the next USG shutdown), then Tor Project will become an illegal NGO. What then? I don't know, but it is certainly reasonable to fear that Tor products might simply no longer be available to anyone anywhere.
(As a matter of fact, Tor Project has not recently reiterated the "no backdoors ever" vow, and IMO it is not possible to repeat this vow too often, so Shari or Roger, please repeat it in unambiguous language!)
> So please TorProject, avoid the PR and nonsense, focus on securing your browser and making it practical/configurable for power users instead of wasting all your time on a userbase that are already too far gone to save.
Tor does not continue to exist by some magical process independent of the course of human events, and Tor Project does exist in a political vacuum.
If you want to continue to use new versions of Tor products, you should support growing the user base, not shrinking it.
This is not inconsistent with continuing to request specific features which you hope will improve security/anonymity for everyone.
I wonder why not to move Tor…
I wonder why not to move Tor Project from the US to Canada?
> I wonder why not to move…
> I wonder why not to move Tor Project from the US to Canada?
CA is alas one of the FVEY countries (US, UK, CA, AU, NZ).
When the Trudeau government was elected there was briefly hope that CSE (Canada's NSA) would cease cooperation with NSA in illegal dragnet surveillance, but that hope seems to have died.
OTH, the University of Toronto's Munk School of Journalism hosts Citizen Lab, which has done wonderful work in exposing malware abuses by "little" governments like Ethiopia, sometimes even by CN. So far, alas, Citizen Lab has not been able to expose abuses by FVEY governments.
Some years ago, there was hope that Iceland might prove to be a data refuge, but this was quickly brought into question by a horrific corruption scandal. Traditionally neutral countries like Switzerland or Finland beckon, but Switzerland is endangered by a dispute with USG over banking secrecy, and Finland is subject to bullying by RU as well as US. Hong Kong is increasingly dangerous.
Germany might be the best bet, but also seems to harbor the greatest concentration of (mostly non-German) spooks.
Belgium has waffles, but is also bugged like nobody's brother.
I think the only solution is for TP to ask advice from HRW and Amnesty how to establish a legal presence as an NGO based in multiple continents.
And to keep in mind the possibility of going underground.
What then?…
What then?
Set up headquarters in another country, build a stronger presence inside the Tor network, appeal to cryptocurrency enthusiasts. Laugh as America turns itself into China. https://www.techdirt.com/articles/20180117/02201339017/chinas-solution-…
> Laugh as America turns…
> Laugh as America turns itself into China.
I read that Tech dirt article too (shout out to Tech dirt, the exemplar of endangered journalism, and took it as vindication of my warnings here since many years.
No US media (AFAIK) have even attempted to study the effects on opinions in the US business community of ingenious CN propaganda (e.g. China Daily) which is doing so much to quietly convert the USA into a hateful model of technology-enabled authoritarianism.
The biggest untold aspect of the Snowden leaks story is the begged question of just what USG intends to do with all the data it is slurping up in all those ever-multiplying ever-expanding dragnet surveillance programs.
The answer, it appears, is precrime. Or even pre-thoughtcrime. CN is pointing the way, but US intends to go much further, according to NCTC, FBI and National Laboratory white papers. Most amazing of all: this is not even much of a secret, many of the discussion of how to implement American precrime is in openly published whitepapers. But apparently no muckraking journalists are reading them.
Given all the constant "save the children!" rhetoric coming from FBI, you'd think some swamp creature would perceive the problem with NCTC's explicit goal of identifying future bad actors/thinkers starting from age 2-7, which is quite literally their target group, and this shocking fact is not even secret. It is specifically mentioned in several obscure but unclassified documents.
We need LANL's counterpart to Snowden to bring out the secret documents, which are apparently even more horrifying that the unclassified ones.
Not all Tor Project…
Not all Tor Project employees are US citizens... it's not like ITAR is an issue for them. As the software is open source, if the organization itself could not legally exist in the US, development would likely resume in another country, under another organization, where it is legal. The software could be trivially forked and resumed like nothing happened (after some logistical nightmares, at least). US developers would either simply stop contributing, or would contribute anonymously.
As for the risk of backdoors, again, Tor is open source. Anyone can read the source code, and anyone can read every single changed line between two versions. Sure, it would be possible to insert a bug with some clever abuse of undefined behavior and other C oddities, but it will not ensure a backdoor will get through, much less get through undetected for any significant periods of time. Even if you do not read the source code, others do. The devs do, many programmers do, I do. That's a lot of eyes on the code. Could it be better? Yes. But should we be freaking out about the risk of backdoors? No. It's better to worry about the sad state of Firefox (and by extension, Tor Browser) security than it is to worry about the political future of Tor Project.
> As for the risk of…
> As for the risk of backdoors, again, Tor is open source. Anyone can read the source code, and anyone can read every single changed line between two versions.
The problem with this argument is that NSA messed with at least one protocol (a public standard for a pseudo-random number generator published by NIST) and nobody noticed--- not even the supposed experts who work for NIST. (This was one of the many revelations from the Snowden leaks, and was discussed at length in this blog a few years ago.)
In other words, some of the most crucial elements of Tor can be meaningfully critiqued by only a tiny handful of cryptographic researchers. If USG arrests them all--- all those who live in the US and do not already work for NSA, that is--- it could be almost impossible for "anyone" to recognize that a subtle "backdoor" has been introduced into the published source code.
There has never been a more desperate need for technically able "fresh blood" in math and computer science than at present. The problem is that USG funds the education of most of the students and too many of them are forced into working for USG upon graduation.
The only answer, I think, is to try to be bold by trying to build campus organizations which try to persuade US techies to follow the example of Snowden by working for The People by working against the Universal Adversary.
NSA boycott, anyone?
I hope the new addon GUI in…
I hope the new addon GUI in next FF59 release midjear? is somewhat ...usable.
When you look at https://hackademix.net
blog from author of NoScript, the new GUI api mozilla is forcing. You can't escape and it forces a lot of confusion.
The classic menu is practical, the new one ...TEEMING only? Scary)-:
Mozilla may not be perfect…
Mozilla may not be perfect but when it came to what /really/ matters-- punishing /crimethink/-- they did the Right Thing (TM): they fired Brendan Eich.
+1
+1
I keep getting the message:…
I keep getting the message:
Unable to start Tor.
Failed to get hashed password.
It won't start after that. It always worked for me previously.
What operating system are…
What operating system are you on? Does this happen with a clean, new Tor Browser 7.5 as well?
I hope that this annoying…
I hope that this annoying bug will be resolved as soon as possible.
"Temporarily allow all this page" breaks JS on all already opened HTTPS sites (on Medium Security)
https://trac.torproject.org/projects/tor/ticket/24126
Wow! Somebody except me…
Wow! Somebody except me found that bug annoying.
FUCK GFW
FUCK GFW
how did time sonwflake…
how did time sonwflake-client into Debin Gnu/Linux :)
Doesn't work on Windows…
Doesn't work on Windows Vista x64.
Fully broken. Nothing works, Tor doesn't launch, Mozilla doesn't respond. Plenty errors.
I have only Vista Windows on all my PCs and some on XP (didn't test on XP though). And I'm not going to update to later Windows with MS spying on you. Never ever.
Mind that Vista works great on new AMD Ryzen, so that it ! Also recommended plenty people and companies to stay on Vista... best Windows ever.
I may have to download a 7.0 version of Torbrowser and stay on it, deactivate updates.
Mind that Mozilla bigger than 52 wont work on Vista too.
What does "fully broken"…
What does "fully broken" mean and "Tor doesn't launch"? Do you get error messages during start? Does this happen with a clean, new Tor Browser as well? How far in the start-up process are you coming with that one? Are you seeing some dialogs/windows and the browser is crashing then?
Do you have some antivirus/firewall tool that could block Tor Browser from running?
Vista has no security…
Vista has no security updates. Forget about it.
Vista is so secure that it's…
Vista is so secure that it's not needed. Ever asked yourself why MS replaced it ???
Just have to let it as is with it's security features. People were annoyed by the fact that they had security alerts and couldn't do anything they wanted, especially in user mode.
Windows 7 is Vista with security features dropped and lot of pathes to help.
Windows 10 is Windows 7 + ugly and stupid interface + spyware + all security features on (besides MS spying on you all time) and forced pathes which put their security features and spyware back every time you touch them.
I have Vista systems running everyday without any reinstall, no Virus, since when Vista came out 10 years ago. Most are C2Q with 8GB RAM, updated graphics (Nvidia Maxwell) so they run pretty well.
And I agree with the guy who says Firefox is becoming junkware like Chrome and all the stuff running after commercial features.
Fact is this has become so since Brendan Eich has been fired for private misbehaviour, that kind of stresses who are the people in charge now at Mozilla. Branching off at 52.x level is the good move for Torbrowser.
I hope TorBrowser is rapidly fixed to work on Vista again.
Vista doesn't even deny…
Vista doesn't even deny mapping pages to null addresses... I would call that a nasty security issue. Not to mention all the "security" features Vista added (read: UAC) are completely broken. UAC is a joke. 7 is slightly better, 8 is a lot better, 10 is better still (it doesn't render fonts in kernelspace anymore, though it still renders some windows and scrollbars that way...). 10 also has a boatload of new security features that make EMET practically obsolete. Now, is Windows 10 "good"? No. It's a privacy nightmare. But to say that Vista is secure in any way is just insane. Better than XP, but still shit.
Browser launches but Tor…
Browser launches but Tor doesn't seem to. Very weird. But even browser is half down. It must be killed to close the opened Windows. There is no response when trying to surf. It should be something even if Tor is down (since it should try to connect the proxy). It's simply as if the people compiling never tested on Vista (x64). Version 7.0.11 works great.
7.5 "Doesn't work on Windows…
7.5 "Doesn't work on Windows Vista x64"--the same for me. A connection is made, but when a window opens no page loads. I tried a new identity and received this message: "TypeError: frameLoader.tabParent is null". I restored Tor to its original settings (no add-ons etc.) and still no page loads. I uninstalled Tor 7.5 and reinstalled it and was successful up to pressing "Finish" when a blank window opens and no page loads.
Does it work better for you…
Does it work better for you if you set
browser.tabs.remote.autostart.2tofalsein yourabout:configand restart (in case you can actually change things there).SUPER!!!!
SUPER!!!!
trying to get onto a…
Trying to get onto a craigslist listing, I keep getting:
"This IP has been automatically blocked.
If you have questions, please email: blocks-b1514257262462964@craigslist.org"
Okay. Usually I click on "New Tor circuit for this site" and, on the new circuit, the site comes in. Often I have to click "new tor circuit" a couple of times, but then I guess the right countries are circuited and it comes up, no problem. But...
yesterday and today no matter how many times I do that I can't get the site to come up. A funny thing, I started to notice, was that Bulgaria kept being the first IP address, after "This browser", then I saw that it was the exact same IP address, in Bulgaria, every time. Something must be wrong, if every time I ask Tor to reroute me through a new set of onion-layers I keep being sent through the same one address.
The clearnet sites you visit…
The clearnet sites you visit can see only the exit node, the final IP, not the other nodes of your circuit to it. Many sites choose to block all known Tor exit nodes reasoning that Tor users who might behave maliciously cannot be blocked individually. Some help sites for network security admins compile lists of all Tor exit node IPs that website admins can import into their firewalls to block Tor traffic. Craigslist is doing something like this. Some exit nodes might not be blocked because they haven't been discovered yet by the people who compile the lists. The IPs of all Tor nodes except bridge nodes are published by the Tor network so that circuits can be created in the first place.
Some clearnet sites choose not to block but put Captchas, some requiring Tor users to enable JavaScript, as gates in the path of all Tor users before allowing them to view the site. Cloudflare's services are notorious for blocking and monitoring Tor users. Tor Project has FAQ pages describing options for website administrators who are considering to block or restrict Tor traffic:
https://www.torproject.org/docs/faq-abuse.html.en
The first node in your circuit is called the guard node. Tor developers have been increasing the guard rotation period since around version 0.2.7 in 2013. It is normal now for the first IP of your circuits to stay the same for many months. Research papers have found it statistically likely for a global adversary to correlate traffic entering and leaving the Tor network if your guard node changes frequently:
https://tor.stackexchange.com/questions/13328/guard-nodes-how-long-is-t…
https://blog.torproject.org/improving-tors-anonymity-changing-guard-par…
If you really want, you can change your guard node by deleting Tor Browser and downloading a fresh copy or by configuring Tor Browser to use a bridge node.
It's your entry guard that…
It's your entry guard that is not supposed to change when you click "new circuit". More here: https://www.torproject.org/docs/faq#EntryGuards
Craigslist might store…
Craigslist might store cookies in your session that could identify you as the same visitor. Rather than "New Circuit", try "New Identity" (warning: closes all tabs).
Tor Browser 7.5 is better…
Tor Browser 7.5 is better than ever! I use it to surf all of my favorite porn sites and my female boss doesn't know shit!
This comment is just awesome…
This comment is just awesome. Thanks for this. I needed the laugh!
If you run into Jeff…
If you run into Jeff Sessions there, say "hi" from all o'us!
it sounds have been…
it sounds have been configured for the windows users only !
Disable logjam : security.ssl3.dhe_rsa_aes_256_sha
Disable ciphers with ECDH (non-ephemeral) : security.ssl3.ecdh_rsa_aes_128_sha
Disable 3DES : security.ssl3.rsa_des_ede3_sha
Disable ciphers with DSA/128-bit cyphers : security.ssl3.dhe_rsa_aes_128_sha
Disable ciphers with DSA : security.ssl3.dhe_rsa_aes_256_sha
Disable ciphers with ECDH (non-ephemeral) : lol
should be set to false
security.enable_tls
security.ssl.require_safe_negotiation
security.ssl.treat_unsafe_negotiation_as_broken
should be set to true
& puny code ?
& an implementation of the nice calomel addon ?
it is not poorly secured but could be set for the linux users a bit more hardened.
Qualified plus one…
Qualified plus one.
> Disable logjam : security.ssl3.dhe_rsa_aes_256_sha
> Disable ciphers with DSA/128-bit cyphers : security.ssl3.dhe_rsa_aes_128_sha
I keep noticing that certain otherwise valuable activist and independent news media sites remain vulnerable to at least one of these.
There is a small conundrum here: is it better to insist on safer crypto at the expense of confusing puzzled non-power users who don't understand why they get a message warning that some site's encryption is broken (and probably fear that the site has suffered an intrusion, rather than that it is not well maintained from a security perspective).
At the very least, I hope TP leadership will try to ensure that this kind of default configuration decision is regularly revisited to take account of increasing cybersecurity mindfulnees among activists and news organizations, and current threats as observed in the wild (or reasonably expected to become common in the near future, e.g. Meltdown attacks on unpatched Cloud servers with Intel processors).
Does this update contain the…
Does this update contain the Spectre/Meltdown mitigations from upstream?
Tor Browser was not affected…
Tor Browser was not affected by them as we both had reduced the timing precision for fingerprinting reasons before and SharedArrayBuffers are disabled in ESR 52.
Well, well, gk. As you're…
Well, well, gk. As you're saying there's no censorship in the blog, where is my reply here, disproving your comment? It seems this blog 'eats' some comments, because other comments, posted that day, are visible now.
Thanks, this is good to know…
Thanks, this is good to know!
I wish TP had posted promptly when the Meltdown/Spectre vulns were announced in early Jan. (Roger is pretty good at explaining complicated matters.)
Of course, it contains. But…
Of course, it contains. But it doesn't mean it's not vulnerable to that class of attacks.
as far as i know, one can't…
as far as i know, one can't exploit the flaw if js is disabled.
My understanding (of the…
My understanding (of the Meltdown flaw) is significantly different:
This is not one attack but a fundamental flaw which will enable a whole class of attacks. Currently known proof-of-concept Meltdown attacks require, AFAIK, that the attacker use some "ordinary exploit" to gain a local presence on the attacked device--- most likely a Cloud Computing server hosting sensitive information about millions of people, but quite possibly a workstation or laptop used by a reporter, activist, doctor, lawyer etc. So it is not just USG agencies (which have moved aggressively into the cloud) which should be very worried; at-risk individuals should also try hard to take proactive countermeasures.
In the case of attacks on at-risk individuals, some experts have specifically stated that exploits of zeroday flaws or unpatched flaws in javascript are one of the most likely ways that attackers will seek to gain a local presence on a PC in order to begin a Meltdown attack seeking to capture the most dangerous information, such as cryptographic material residing in the kernel space memory of a running PC with a mounted encrypted external drive holding (for example) casework for a sensitive lawsuit.
IMO the prospect of Meltdown attacks does at the very least demand a discussion of whether an "emergency adjustment" of the default slider configuration might be warranted.
After installing update…
After installing update, Avast Antivirus saying that 7.5 update is malware.
I clicked that it is Not Harmful in some kind of popup in avast.
Is my 7.5 update safe??
Because I updated from that Green Tor button Check Update.
I guess what's happening is…
I guess what's happening is that your Avast tool has never seen this Tor Browser before and now thinks "Holy shit this must be malware then". Our updates are signed so that someones tampered with them and your browser is still working is very unlikely.
We know Avast is a garbage…
We know Avast is a garbage. Now you know too.
"I updated from that Green…
"I updated from that Green Tor button Check Update."
You are very probably OK. Tor Browser downloads updates from torproject.org by HTTPS over Tor. The variable is app.update.url in about:config. Only bad if Tor server or website certificate is hacked or exe changed after reproducible build and before signing. Not probable.
If you download new installer on TorProject website, you can verify signatures in sig file under download button.
https://www.torproject.org/docs/verifying-signatures.html.en
Hello: Thanks
Hello:
Thanks
UITour:startSubTour: No…
UITour:startSubTour: No feature option specified UITour.jsm:1946
This is https://trac…
This is https://trac.torproject.org/projects/tor/ticket/25045 now, thanks. If you have further information on how to reproduce that issue we would be grateful. Please add it to the bug ticket in that case, thanks!
Please remove that nagging…
Please remove that nagging canvas warning on every second website
Developers seem to be bullet…
Developers seem to be bullet-proof in their decision of not fixing it for years.
Oh my, special snowflakes…
Oh my, special snowflakes have arrived!
tor-win32-0.3.2.9.zip…
tor-win32-0.3.2.9.zip is different between 7.5 and 8.0a1, why?
We are not building the…
We are not building the Windows bundles on Ubuntu anymore in the alpha series but rather switched to Debian. While I have not checked that I think that's very likely the reason for the difference.
Only EXEs are different…
Only EXEs are different. libfaketime?
Please fix control port…
Please fix control port
getinfo hs/client/desc/id/c5yc3v2qss6n7dddeazg32i4gkywxwdgd6johziwkzh2wphk3nf4tnid
551 Invalid address
What are you doing and what…
What are you doing and what is not working? On which system?
The new Tor Launcher UI is…
The new Tor Launcher UI is obviously an improvement, but once the user configures it (in most use cases once and forever) the UI wastes a lot of screen space to merely display a logo, a progress bar, and progress info.
I admit the uniformity of window size between configuration stage and connecting stage is fancy (the uniformity which in most cases the user will notice only once), but not enough to redeem the waste of screen space.
Get ready for more bells &…
Get ready for more bells & whistles.
As long as it fits in low…
As long as it fits in low resolution displays such as 640x480 and RasPi displays, I'm fine with it. It disappears quickly anyhow. Maybe the slow end-users in the study were confused by the separate popup progress bar. Wasn't the progress bar or update bar on a large empty UI in the past?
I still can't use twitter at…
I still can't use twitter at all. I've got "allow scripts globally" enabled and all objects unblocked, but none of the buttons work: Tweet, Retweet, Like, Edit Profile, arrows for drop-down menus etc etc. I click and they get highlighted but nothing happens.
So, you don't have the…
So, you don't have the security slider at level "low"? I guess instead you have it at "high" and are just allowing scripts? Or what exactly is your setup?
Yup that did it. I had…
Yup that did it. I had security setting on "Safest" and switched it to "Standard" and now everything works. Didn't even know about that. Thanks for your help.
Years ago when I tried…
Years ago when I tried Twitter with Tor, they immediately disabled my account and wanted my phone number. Good luck.
I was able to use it just…
I was able to use it just fine with Tor a few years ago. Then I logged in again recently after a long break and it was disabled, so I appealed and they restored it.
Same with facebook. Only…
Same with facebook. Only connected once with Torbrowser by mistake. They blocked my account and asked for my ID Card scan (phone number insufficient for Facebook).
They never got it.
It seems that ReCAPTCHA …
It seems that ReCAPTCHA (which comes up all the time if you search Google, visit CloudFlare protected websites etc.) is currently not serving CAPTCHA challenges to Firefox-on-Android (including Orfox/TorBrowser-on-Android) users, with a "browser not supported" message that points to https://support.google.com/recaptcha/answer/6223828?hl=en
Can anyone reproduce this issue? If so, is a mitigation planned, perhaps adding compatibility for whatever APIs ReCAPTCHA is relying on and supplying a different browser identity that they do support?
When I post a comment on…
When I post a comment on High or Medium security, sometimes the preview doesn't show up, and when it redirects me back to the blog post after clicking Save, the green "in moderator queue" box doesn't show up, and the blog post page refreshes infinitely.
Just updated to TBB v7.5…
Just updated to TBB v7.5... dies under firejail. Dies independently of firejail. Executes mutual suicide pact with torbrowser-launcher package (which worked until seconds ago, with and without firejail). Re-installed torbrowser-launcher; no joy.
Death notice follows...
================
firejail /usr/bin/torbrowser-launcher 4:32
Reading profile /etc/firejail/default.profile
Reading profile /etc/firejail/disable-common.inc
Reading profile /etc/firejail/disable-programs.inc
Reading profile /etc/firejail/disable-passwdmgr.inc
** Note: you can use --noprofile to disable default.profile **
Parent pid 10161, child pid 10162
Child process initialized
Tor Browser Launcher
By Micah Lee, licensed under MIT
version 0.2.8
https://github.com/micahflee/torbrowser-launcher
Refreshing local keyring...
gpgkeys: HTTP fetch error 1: unsupported protocol
Traceback (most recent call last):
File "/usr/bin/torbrowser-launcher", line 30, in
torbrowser_launcher.main()
File "/usr/lib/python2.7/dist-packages/torbrowser_launcher/__init__.py", line 62, in main
app = Launcher(common, url_list)
File "/usr/lib/python2.7/dist-packages/torbrowser_launcher/launcher.py", line 91, in __init__
if not self.common.settings['installed'] or not self.check_min_version():
File "/usr/lib/python2.7/dist-packages/torbrowser_launcher/launcher.py", line 603, in check_min_version
for line in open(self.common.paths['tbb']['versions']).readlines():
IOError: [Errno 2] No such file or directory: '/home/user/.local/share/torbrowser/tbb/x86_64/tor-browser_en-US/Browser/TorBrowser/Docs/sources/versions'
Parent is shutting down, bye...
================
*This is marriage...?!?*
Yup, explanation and…
Yup, explanation and workaround (®works-for-me©)
Looks like TBB has moved faster than torbrowser-launcher package. This is not the first time it happened, unfortunately.
As a result, TBB is still just fine, but torbrowser-launcher is broken: it no longer finds what it is searching for, to determine if it needs to take care of upgrading TBB itself (e.g. first time or very obsolete, I see this feature as very usefull), or just launch it. When it fails to find these bits, then instead of deciding to try launching TBB gracefully anyway, it collapses.
Solution will come with a future version of torbrowser-launcher, I guess. I didn't look at the version available in sid as yet (version number is just higher), but its changelog doesn't mention anything about this, as I understand it.
Until then, we may open a terminal and just run TBB directly:
~/.local/share/torbrowser/YOURARCH/YOURTBBFOLDER/Browser/start-tor-browser
(YOURARCH: e.g. "i686", YOURTBBFOLDER: e.g.: torbrowser-browser_FR)
One step further, we may register TBB as a local app for the current user, then use the new launcher instead of torbrowser-launcher one, bypassing entirely the latter. Same as above, adding one argument:
~/.local/share/torbrowser/YOURARCH/YOURTBBFOLDER/Browser/start-tor-browser --register-app
(this results in a duplicate "icon" etc. also named "Tor Browser" in the available applications list for the current system user, but with a distinct description and which can be placed e.g. in desktop panels alongside or instead of the one from torbrowser-launcher)
I guess torbrowser-launcher package needs some love.
Maybe also, TBB release team could care a little bit more about its user base.
(Probably not the correct…
(Probably not the correct forum for this but...) I would estimate that a full 60% of pages I visit are now blocked by cloudflare. In addition - on the exceedingly rare occation that I do actually enable js etc and lower my security settings to the point that the recaptcha will in fact work - google is now in many cases throwing up the very tiring "automated queries" error.
How is it possible that cloudflare controls/censors such a large part of the internet and, far more importantly, why is nothing being done about it?!
Read here. https://trac…
Read here. https://trac.torproject.org/projects/tor/ticket/24351
Thank you for the link. Not…
Thank you for the link. Not sure why I was unable to find that myself,,
Reposting -- it appears that…
Reposting -- it appears that unless NoScript is disabled, (attempted) posts here disappear into the void.
Anyway: automatically upgraded to "Tor Browser 7.5 (based on Mozilla Firefox 52.6.0) (64-bit)" under macOS 10.12.6; Tor crashes whenever I open a (specific) folder of bookmarks. This folder has 14 bookmarks -- so "a lot", but not A LOT. This seems to be replicable -- three or four crashes so far -- but if I close some of the tabs quickly, sometimes it doesn't crash. Didn't have this behavior in previous versions, needless to say.
Also, since I'm here: any reason not to have a global setting for declining canvas requests? If Tor is recommending not allowing as a matter of course, better to have it remembered somewhere to apply always. [I'd be ok with it remembering yea or nay for specific sites, and asking for new ones, but that's a way to fingerprint, sort of, if the attackers get ahold of the physical machine, right?]
Interesting, what crash log…
Interesting, what crash log do you get? Could you open a ticket at our bug tracker https://bugs.torproject.org describing your issue and attaching the crash output? Thanks!
Re: the canvas prompt: there is no particular reason for not having that option right now. There is a bug report in our bug tracker: https://trac.torproject.org/projects/tor/ticket/23227 which urges us to implement that feature. One thing to think about, though, is what to do with all the broken sites that only work with canvas enabled if the user flipped the preference (and is now stuck). Maybe that's bad luck then or maybe there is something smarter we could do. I don't know yet.
torbrowser-launcher &…
torbrowser-launcher &
[1] 4884
shit@linux-lvps:~> Tor Browser Launcher
By Micah Lee, licensed under MIT
version 0.2.8
https://github.com/micahflee/torbrowser-launcher
Refreshing local keyring...
shit@linux-lvps:~> Keyring refreshed successfully...
No key updates for key: EF6E286DDA85EA2A4BA7DE684E2C6E8793298290
Traceback (most recent call last):
File "/usr/bin/torbrowser-launcher", line 30, in
torbrowser_launcher.main()
File "/usr/lib/python2.7/site-packages/torbrowser_launcher/__init__.py", line 62, in main
app = Launcher(common, url_list)
File "/usr/lib/python2.7/site-packages/torbrowser_launcher/launcher.py", line 91, in __init__
if not self.common.settings['installed'] or not self.check_min_version():
File "/usr/lib/python2.7/site-packages/torbrowser_launcher/launcher.py", line 603, in check_min_version
for line in open(self.common.paths['tbb']['versions']).readlines():
IOError: [Errno 2] No such file or directory: '/home/shit/.local/share/torbrowser/tbb/x86_64/tor-browser_en-US/Browser/TorBrowser/Docs/sources/versions'
[1]+ Exit 1 torbrowser-launcher
Yep this isn't good. Tumbleweed install.
<br />mkdir ~/.local/share…
Do not fix it like that,…
Do not fix it like that, this could add even more troubles.
See comment about "start-tor-browser" launcher instead.
Yup, I guess Tor will loose…
Yup, I guess Tor will loose many newbies for this and/or they'll loose some personal data e.g. bookmarks over a blinded reinstall.
Good news is, torbrowser-launcher's reinstall feature seems to still work just fine so maybe, some will try that route. So far it results in the same error (both localized and English versions), but there's a chance they don't entirely give up before a fixed tarball is published.
Here, all upgraded instances (from 7.0.11 to 7.5) now die with the same error. Looking quickly at one of them, this path is invalid, there is no "sources" subfolder. Won't be able to dig tickets or investigate any further until much later today, so I came here to see if, at least, the blog post had been updated with some warning, or anyone else had commented.
Should we not recommend to DISABLE auto upgrade until this is resolved, whenever this is not too late?
Tried to answer this as a…
Tried to answer this as a reply above.
Why wont my tor browser load…
Why wont my tor browser load? Ive been using this thing for over a year and it just started taking the piss for no reason. keeps saying trying to establish circuit
installed on windows 7 …
installed on windows 7
EMET detect a SimExecFlow coming from TorBrowser and close the app (crash).
Note : There was already some problems to make TBB work with EAF and EAF+ in EMET, but it wasn't the only App requiring to disable these two mitigation. As far as I know only TBB 7.5 requires to disable SimExecFlow.
Incidentally, this page has a very strange behaviour. Sometimes everything works okay and the minute after it keeps reloading until I hit the "escape" key. And all the "reply" button and the "join discussion" form disappear. Weird.
now stable :-(
now stable :-(
Yes, this is a known issue,…
Yes, this is a known issue, see https://trac.torproject.org/projects/tor/ticket/13893 for a long history of comments. Interestingly enough some users where under the impression that this got fixed for 32bit bundles with the switch to ESR 52. However, that does not seem to be the case for you at least. The proper fix is to get away from GCC 5 as the compiler used for the Windows bundles to GCC 6 where this problem seems to have been fixed. We are working on that: https://trac.torproject.org/projects/tor/ticket/20301.
fixed, fixed, without…
fixed, fixed, without sandbox. GCC 7.3 is out. How does it work with that?
This is weird, after copying…
This is weird, after copying the pref.js and user.js from my TBB7 folder to the TBB7.5 folder, it works. I didn't change anything on EMET, but now I can launch TBB 7.5.
I don't know which settings is responsible for this. Maybe "browser.tabs.remote.autostart.2" that I changed from "true" to "false" in TBB 7.
On the subject, when Emet crashed TBB 7.5, I've noticed that one instance of firefox.exe remain in the task manager. According to "process explorer.exe", the instance is on "suspended" state, when I click on resume, then firefox.exe shut down correctly.
I hope these infos can help.
ps : Yes, I confirm (my…
ps : Yes, I confirm (my previous message hasn't been posted yet) after a fresh install that "browser.tabs.remote.autostart.2" was the guilty setting.
Problem solved, thank you.
Interesting, thanks for…
Interesting, thanks for letting us know.
[EDIT]
FWIW: It seems that EMET is not compatible with sandboxing enabled. What you do with flipping that preference is outright disabling the sandbox Firefox ships. I think I'd rather rely on that one than on EMET, though. We have a long history of trying to make Tor Browser compatible with EMET (see: https://trac.torproject.org/projects/tor/ticket/13893) and it seems we still have some way to go.
It might be worth knowing whether that is actually just a Tor Browser issue or whether Firefox is affected as well. Does EMET work for you with a vanilla Firefox 52 ESR (see: https://www.mozilla.org/en-US/firefox/organizations/all/ for test versions).
EMET is not compatible with…
Hilarious! And Windows 1709 too? How could you think like that? Of course, Firefox is not affected. Just update your compiler. (It could fix sandbox on Vista and x64 too.)
You missed the "It seems"…
You missed the "It seems" before the quote. It was a theory I had and I am fine I am wrong with my idea and the issue lies somewhere else.
Theory about Mozilla/Google…
Theory about Mozilla/Google is developing a sandbox incompatible with Windows?
Hilarious #2! Sandbox level 1 has almost no protections vs. EMET.
Right now I've tested with…
Right now I've tested with Firefox Quantum. No problem with remote.autostart2 enabled. I expected a crash but no.
I used to disable remote.autostart stuff on Firefox 52 because I don't like to have too many process in the task manager. That's just me.
As I said, FF didn't work with EAF and EAF+ in EMET but so did many others apps.
I'll reinstall FF 52 ESR and run some tests in the future.
See you.
didn't work with EAF and EAF…
Update your Windows and EMET.
So I've installed and runned…
So I've installed and runned FF 52 ESR 32bits and 64bits out-of-the box, no crashes. Emet didn't complain for neither of them.
And I confirm that remote.autostart2. was enabled.
Weird...
I don't know, maybe it's remote.autostart2 + something else in Tor Browser like one of the extensions or something.
Good luck.
Thanks for testing!
Thanks for testing!
torbrowser 7.5 no starting…
torbrowser 7.5 no starting due to missing versions file.
After upgrade to 7.5 and closing and re-launching torbrowser, it will no longer launch.
Python error of missing file ~/.local/share/torbrowser/tbb/x86_64/tor-browser_en-US/Browser/TorBrowser/Docs/sources/versions
sources directory does not exist.
torbrowser now starts with no problems
I think this is a bad idea…
I think this is a bad idea. as you don't know if it will keep working with future versions of TBB and/or torbrowser-launcher, because neither will expect that this folder and file had been re-created manually by the user after TBB upgrade to 7.5. It could even "break things", depending on how torbrowser-launcher's maintainer decides to fix the issue.
Fact is, torbrowser-launcher still succeeds at launching TBB after the upgrade from 7.11 to 7.5, but only the first time. I did not read TBB source code, but I the only explanation I can think of is that TBB 7.5, during its first session, decides to do some clean up and deletes this part of its file tree, which it considers obsolete, and will likely do this again at least during each future upgrade.
Using "start-tor-browser --register-app" as a temporarly measure, as I described in my previous comment, should be more robust.
torbrowser 7.5 no starting…
I have torbrowser to symbolic link to start-tor-browser -- that works.
(Preview seems not work)
Cannot communicate securely…
Cannot communicate securely with peer: no common encryption algorithm(s). Error code: SSL_ERROR_NO_CYPHER_OVERLAP
good network
good network
Fedora 25 Cinnamon:Restart…
Fedora 25 Cinnamon:Restart Tor button does not work.
I had to download Tor 7.5 and to configure everything
because the update of 7.11 is not working...
Are you also starting Tor…
Are you also starting Tor Browser via the torbrowser-launcher package (I seem to remember it's in Fedora too)? If that's so, read my previous comments about it here.
https://forums.informaction…
https://forums.informaction.com/viewtopic.php?f=7&t=24484
I have same problem.Other Add-on not working.
That's probably https://trac…
That's probably https://trac.torproject.org/projects/tor/ticket/25000. There is a workaround mentioned in this ticket and we'll fix the bug in our next release.
I didn't find the new tor…
I didn't find the new tor launcher easier to use. It's following most recent software by making features harder to find (or removing control from the user altogether) and dumbing down the interface with lots of white space. Please bring back Vidalia!
Vidalia was nice but it didn…
Vidalia was nice but it didn't scale well and it was apparently abandoned by its creator some years ago. So a better way would be to continue to try to improve the current way Tor Browser tries to accomplish some of the desirable functions of Vidalia.
The special interest agenda,…
The special interest agenda, and other, censorship better stop. You are public, not private. On top of that, censorship is 100% out of step with the legal intent behind Tor's existence and funding. Those stupid little donation stunts don't change anything.
WE get to promote OUR views. YOU don't get to do shit.
WE don't have to talk to you certain ways. YOU have to talk to us certain ways.
WE pay you. YOU serve US.
Wooh! Someone finally said…
Wooh! Someone finally said it! But the problem isn't that they won't post comments like that one. They will because doing so scores them some cheap symbolic value. Anyone can say "we're against censorship" but that's as far as it goes at Tor.
Try posting something grittier about their practices and policies. You'll be lucky if you even get the confirmation message. I can understand problems of topicality, spam and maybe a few other things, but this problem spans every whim and quirk of the highly paid employees at Tor and it is most definitely about their politics and stands on social issues.
I am another Tor user, a…
I am another Tor user, a contributor but not affiliated with Tor Project in any way.
> On top of that, censorship is 100% out of step with the legal intent behind Tor's existence and funding.
So you believe your comments are being censored?
I've been using Tor for many many years, and my own comments often fail to appear. But while this is frustrating, I generally assume they just got buried under what I hear is a mountain of commentbot junk.
> Those stupid little donation stunts don't change anything.
As a long time Tor user, I vigorously dispute the claim that Tor Project's long term project of moving from a USG-dependent funding model to a user-supported funding model (as at EFF, ACLU, etc) "won't change anything". I think this drive can and must succeed, and it will change everything. For the better.
Please join me, everyone, in contributing something, no amount is too small, to Tor Project!
Thank you.
Thank you.
Any news about Vista x64 fix…
Any news about Vista x64 fix for TorBrowser ? Both programs (Tor + Firefox) have problems as already described. Clearly became incompatible after version 7.0.11 (who worked and still works fine).
Take care that some new compilers and api are made Vista incompatible by MS on purpose. There is no benefit in using them on Tor Browser.
Hopefully I think Tor…
Hopefully I think Tor Browser will be better than the previous ones.
Am I missing something, I…
Am I missing something, I thought torbrowser 7.5 was meant to allow me to visit onion v3 links?
"Problem loading" on every v3 site I try.
Try these. Riseup worked…
Try these. Riseup worked for me.
https://trac.torproject.org/projects/tor/wiki/doc/NextGenOnions
I am having the exact same…
I am having the exact same problem on TAILS 3.5 with TOR Broswer 7.5
Same problem. I'm using…
Same problem. I'm using Tails 3.5 which is supposed to come with Tor 7.5 . All v3 sites that I attempt to go to immediately say unable to connect.
All tabs crash after a few…
All tabs crash after a few seconds.Never had any problem ever before 7.5.
What operating system are…
What operating system are you on? Does it work better for you if you set
browser.tabs.remote.autostart.2tofalsein yourabout:configand restart?keeps crashing for me,i get …
keeps crashing for me,i get "gah.your tab crashed" all the time.
What operating system are…
What operating system are you on? Does it work better for you if you set
browser.tabs.remote.autostart.2tofalsein yourabout:configand restart?I don't have time to check…
I don't have time to check,it crashes immediately
Okay, then you could try to…
Okay, then you could try to change the
extensions-overrides.jsfile before you start. You can find it in your Tor Browser directory inBrowser\TorBrowser\Data\Browser\profile.default\preferences. Open it withnotepador some other editor and add at the end of the filepref("browser.tabs.remote.autostart.2", false);. Save and restart.It keeps crashing…
It keeps crashing nevertheless,i use win'10 home.
Do you have some Antivirus…
Do you have some Antivirus/Firewall software installed? If so, which one? Could you test whether uninstalling it fixes the problem? (disabling it is often not enough)
thank you for your work, my…
Thank you for your work, my dear reptilians!
If you mean Pepe, isn't he…
If you mean Pepe, isn't he an amphibian?
Tis hard to please the whole…
Tis hard to please the whole lot , ain't it ? Thanks a lot for your time and effort , guys and gals...!
oh nice, even thought my…
oh nice, even thought my network is only 10KB/s, i still using Tor, because the chinese police is fucking my network and spying on it.
Both updates this month…
Both updates this month failed!! They would neither restart nor therefore work tor. The earlier one to version 7.0.11 was such a hassle redownloading and finally restoring tor on my own, after the same thing happened trying the 7.5 update today, 1/2017, I just reloaded 7.0.11 and await tor, or mozilla, or whoever is going to disable it until it thus stops working (i hope that is not soon). Unhappy.
Which operating system are…
Which operating system are you on? Could you enable update logging and report back which error you are seeing? Set
app.update.logtotrueand then open the browser console with Ctrl+Shift+J when downloading/installing the update. You should see debug output there.This update broke my marker…
This update broke my marker addon. Please fix!!
https://forums.informaction.com/viewtopic.php?f=7&t=24484
Torbrowser failed restart…
Torbrowser failed restart after download of 7.5
Starting it again worked
( Preview seems not work on comment ... )
My opinion. Just keep…
My opinion. Just keep Torbrowser 7.0.11. Disable automatic updates and even alerts to update (though not all possible). Install Torbrowser 7.5 somewhere else as Torbrowser2, in a portable way. Use the one that works. My opinion, 7.5 is full of unsolved problems and new incompatibilities.
Could you name those please,…
Could you name those please, so that we can fix them? I am fine if you add them as a comment to this blog post but if you could open trac tickets at https://trac.torproject.org that would rock. Thanks!
How do I download tor on an…
How do I download tor on an iPhone? Or is that still not really possible?
There is no Tor Browser for…
There is no Tor Browser for iPhone, correct. The best tool available is OnionBrowser right now, see: https://trac.torproject.org/projects/tor/wiki/org/teams/CommunityTeam/S…
how to fix this?…
how to fix this?
frameLoader.tabParent is null
It might be that the enabled…
It might be that the enabled sandboxing is not working for you, hm. Which Windows version are you using?
v3 sites don't works with 7…
v3 sites don't works with 7.5! (fresh install)
Try to load the page and always "Problem loading page"
WHY???
I'm autoquote myself. I've…
I'm autoquote myself. I've changed several first node (blacklisting the IPs on my firewall) and now v3 sites work fine. But there are some general problems with v3 sites because they go up/down frequently.
BTW, 7.5 works good with the normal .onion sites and the rest of the web.
It is written on the…
It is written on the download page :
Tor Browser
Version 7.5 (2018-01-23) - Windows 10, 8, 7, Vista, and XP
This is FALSE. Torbrowser 7.5 is completly incompatible with Vista x64 !!! Both, Firexof part and the Tor part DO NOT work on Vista 64.
Tried on several computers. This is simply put "not working".
You need to go back to Torbrowser 7.0.11 and configure it before anything to stay away from automated updates.
If you got in the menu, your links tranfered, you need to save them from Torbrowser 7.5 before deleting Torbrowser and restore them in 7.0.11.
Take care not to update to 7.5 if it was not automated, before this major bug, if this is one, is repaired.
You could help us debug that…
You could help us debug that and try to find a fix for your problem. So, you said the Tor part is not working either on Vista 64bit. Could you download the expert bundle (32bit), extract it and run it on your machine? (The link to the file is: https://archive.torproject.org/tor-package-archive/torbrowser/7.5/tor-w… and to the signature: https://archive.torproject.org/tor-package-archive/torbrowser/7.5/tor-w…) What error are you getting?
I am very glad to see TP…
I am very glad to see TP using some thoughtful advice from a researcher who has studied usability issues!
However, I am concerned that your work in trying to improve usability (which is a good idea in general) will be rather quickly "buried" if TP neglects the needed follow up:
o reorganize the website so that the most up-to-date and most useful (to newbies) data is easy to find; for example
+ the nice "videos" [animated images] above showing how to use the new interface,
+ "follow these simple steps" tutorials on verifying the detached signature of the tarball,
+ EFF's diagram of the onion concept (a Snowden leak shows NSA teaches bad guys using it; why shouldn't we teach the world using it?),
+ links to EFF's "Surveillance Self-defense", ACLU's "They are Watching" sites, Riseup
(examples of information *not* useful to newbies would include the original Tor design specification and outdated technical information now of interest primarily to historians of technology not to newcomers to the Tor community),
o list of key people and Tor Board must be kept up to date and easy to find,
o statement of principles must be kept up to date and easy to find (in particular, keep trying to make "no backdoors ever" less ambiguous and easier to understand, perhaps by saying the same thing five different ways and by defining all terms e.g. [software application level] "backdoor"),
o list of Tor products and their status (mature, beta) must be easy to find and kept up to date,
o to help at risk people (e.g. soda tax advocates, bloggers, journalists) better understand the technical attacks they might reasonably expect to confront in the months and years ahead, I think the following should also be easy to find in TP's website:
+ link to EFF's collection (not up to date alas) of published Snowden leaks,
+ in particular, to GCHQ/NSA attacks on Tor circa 2012,
+ link to Micah Lee's encryption for activists tutorial,
+ link to WP "Top Secret America", The Intercept "Cell Spies", Wikileaks "Spy Files" sites,
+ link to Citizen Lab site (e.g. reports on Ethiopian government cyberattacks on USPERS),
+ links to best nontechnical explanations of Shellshock, Krack, Meltdown, Spectre flaws,
o institute a regular Friday post in this blog allowing users to "ask us anything", or make suggestions in the comments; sure it will be a pain to keep out spambot comments from such a regular posting, but such an institution will surely be useful and reassuring to newbie Tor users and non-US Tor users in particular, if they see a genuine question being answered promptly and authoritatively; many newbie questions are best answered by citing a link or two and currently these are too hard to find if for security reasons you don't keep them in browser bookmarks (see above for a better way to keep the most quotable links handy)
o ask Tails people to check the blog for questions about Tails; Tails Project is listed as partner of Tor Project so it is confusing and off-putting when some comment in the blog here angrily suggests that Tails questions don't belong here; of course they do; the purpose of this blog is or ought to be to offer helpful information to the Tor community--- including not only node operators, other volunteers and "power users", but also "ordinary users", especially newbies!
o in short, look over your entire website and outreach activities, and ask a hard question about everything you see: does this enhance our *current* drives to persuade/enable more ordinary people all over the world to use Tor (wisely) every day?
> Meltdown, Spectre flaws…
> Meltdown, Spectre flaws
While using Tails 3.5 (running on a laptop which uses an Intel chip) to comment in this blog, I am definitely seeing the unfortunate effects of the patch against Meltdown! This is interesting because although I upgraded Tails as soon as 3.4 and 3.5 became available, this is the first time I've definitely seen the slowdown due to preventing the problematic speculative execution.
Needless so say, as one journalist wrote, the needs of security must always come before matters of convenience, so I am happy to cope with changes.
Who do I contact to offer to…
Who do I contact to offer to help with UI or branding for Tor?
We have a UX mailing list …
We have a UX mailing list (https://lists.torproject.org/cgi-bin/mailman/listinfo/ux) and regular UX team meetings on IRC (https://trac.torproject.org/projects/tor/wiki/org/teams/UxTeam) Feel free to subscribe and contribute, and welcome to the meetings!
If you want to start working right away on branding issues in Tor Browser for instance, have a look at our bug tracker: https://trac.torproject.org/projects/tor/query?status=!closed&keywords=….
Since I use 7.5 I see in my…
Since I use 7.5 I see in my task manager constantly something being uploaded and downloaded. This was never before. What's that about?
And everytime I delete history in Tor, after logging in and out somwhere with my email, and refresh de page I see my email already filled in the box. How is that possible?
Not sure yet. Does this…
Not sure yet. Does this happen with a clean, new Tor Browser 7.5 as well? Do you see the email address filled in the box after doing a "New Identity" as well (click on the green onion icon -> New Identity)?
Already reported on TBB 7.0…
Already reported on TBB 7.0 series, see https://blog.torproject.org/comment/273040#comment-273040
TBB ships with several sites allowed by default to install add-ons.
Even after they are removed, they are re-allowed upon restart.
This HUGE security hole still exists in TBB 7.5.
The excuse that they can't remove them because they get NoScript updates via those sites
is bull@#$%. The commenter was exactly correct who said that starting from firefox is a
bad idea for security. Better to start from scratch.
> Better to start from…
> Better to start from scratch.
Generally speaking, I share your concerns about possible security holes in Tor Browser.
But I think we need to place the decision to base Tor Browser on Firefox-ESR in context. Modern browsers are enormously complex things, and users (even Tor users) expect them to do many things seamlessly. That means browsers require a big team to make-- and also, as you know, it means they are hard to secure. Given the small size of the Tor Project's budget and developer staff, and the enormority of the technical/political threats TP must confront, I think it makes good sense to base Tor Browser on an existing open source browser.
There may be merit to discussing the possibility of basing Tor Browser on another open source browser, but this would raise another issue, the fact that making big changes in something millions of at risk people rely upon can be more dangerous than opting for slow evolution of something we know more or less works for most users.
So generally speaking, I feel we must place our trust in the TB developers to make the best (or "least bad"?) decision when choices are available.
Tor for Windows works…
Tor for Windows works perfectly but Tor for Linux does not.A strange
situation in the sphere of anonymity and security. :)
> Tor for Windows works…
> Tor for Windows works perfectly but Tor for Linux does not.
This is a very sweeping and ambiguously stated claim made without any evidence whatever.
You claim "Tor for Linux" does not work perfectly. Do you mean Tor Browser 7.5 for 64 bit Linux? Did you download the tarball from torproject.org and verify the detached signature before installing it on your 64 bit computer running some Linux distribution?
For all we know at this point, you tried to install 64-bit Tor Browser on an old 32-bit laptop, for example.
I am just an ordinary Tor user, not affiliated with Tor Project, but I've see enough comments to know that the more detail you can provide, the better, assuming you actually want TP to help you fix a genuine problem.
> A strange situation in the sphere of anonymity and security. :)
The Tor community is under constant assault, ranging from technical attacks (e.g. from Carnegie-Mellon nasties) to state-sponsored disinformation/suasion campaigns (e.g. those documented a few years ago in this blog).
Tor Project has very few paid employees and runs mostly on volunteer labor.
Given the forces arrayed against the Tor community, I feel we deserve a great deal of credit for having proven (so far) much harder to kill off than some of the nastiest governments on Earth wish.
I wanted to watch a new…
I wanted to watch a new story video in Australia that only plays to Australia, so I set exitnodes to Australia's country code (AU). This worked and Tor is exiting in Australia. I went to the news web page and it saw me from Australia and drew the page. But when I go to play the video it fails and says I am from the wrong country.
How is it the video was able to determine my real IP address? Is this an HTML5 thing, and I thought by default Tor prevented videos from obtaining your real IP? I am confused.
How do I configure Tor 7.5 to not give up my real IP to a video stream?
My guess: when your Tor…
My guess: when your Tor Browser requested the page it used an exit server in AU, so the remote server gave you the exit server the page and it passed back down the circuit to you. But when your Tor Browser requested the video, owing to the vagaries of CDN networks, that was on a different server using a different URL domain and Tor created a new circuit for the second connection, for which the exit server was not in AU.
> I set exitnodes to Australia's country code (AU).
Or maybe my guess is wrong!
Tails may be safer for you, because Tails does better at avoiding leakages of your real IP.
Hi there,…
Hi there,
An error occured when I was trying to verify the signautre of tor browser 7.5 using GPG4WIN, plz see below:
gpg: requesting key 93298290 from hkp server pool.sks-keyservers.net
gpg: no valid OpenGpg data found
gpg: total number processed: 0
gpg: keyserver communications error : keyserver helper internal error
gpg: keyserver communications error: General error
Could you help me to see what is the problem?
Many thanks in advance!
Sounds like it might not be…
Sounds like it might not be listed in that keyserver, or something else went wrong on the server.
That key (the TBB signing key) has been around for a long time so it should have propagated to that keyserver. I checked and it is in pgp.mit.edu. Try downloading it there. Search for
"0x93298290"
My guess is this is due to something innocuous, but you certainly shouldn't install the new TBB until you can verify the detached signature.
noscript icon still jumping …
noscript icon still jumping (update to 5.1.8.4)
PERFECT
PERFECT
It crushes immediately after…
It crashes immediately after opening in win'10 home,never had ANY problems with previous editions for many years.
What do you mean with "after…
What do you mean with "after opening". Do you see a browser windows that is crashing then? Or does this mean right after you are double-clicking on the link to start Tor Browser? Do you see any error message?
EDIT:
Oh, and does this happen with a newly installed Tor Browser as well?
It starts normally,it works…
It starts normally,it works for a few seconds and then i get either "windows closed the application" or "the tab has crashed",and everything after that crashes immediately.
Uninstalled it,made a clean install,previously was updated from earlier editions,it seems to work fine now.
Thank you!
I am getting very many…
I am getting very many
"Your connection is not secure"
and similar. In fact my tor is almost useless. What to do? Its been happening before 7.5 too.
> I am getting very many …
> I am getting very many "Your connection is not secure" and similar.
More detail would help, but I guess the problem is not with Tor but with the fact that browsers generally are complaining more these days about cryptographic misconfigurations. Possibly what is happening is that the browser is expecting a secure connection but an encountering poorly encrypted or unencrypted connection when you click on some link in some webpage. One common way in which this can happen is that a webpage includes "hard links" to third party websites, often holding pictures illustrating news stories, etc. Does this sound at all like what you were doing when you saw these error messages?
I cannot use obfs4 built-in…
I cannot use obfs4 built-in bridge after upgrade TorBrowser from 7.01 to 7.5 (windows + linux), WHY ? please help !
What errors do you get if…
What errors do you get if you start Tor Browser from a terminal on Linux?
not working on Vista x64
not working on Vista x64
We have https://trac…
We have https://trac.torproject.org/projects/tor/ticket/25112 for that. Does the workaround in comment:3 in that ticket work for you?
I'm having the same problem!
I'm having the same problem!
"Unable to connect"…
"Unable to connect"
"Your connection is not secure"
or a simple
"404"
or just and infinite attempt to connect.
This has been the case even before 7.5.
All under Knoppix 8.1 on a Toshiba satellite.
The first three things that…
The first three things that happened today was
Unable to connect
Your connection is not secure
Secure Connection Failed
while e.g. youtube worked fine.
Today I got…
Today I got
Secure Connection Failed
when trying to use onion version of DuckDuckGo
Today I could not connect to…
Today I could not connect to the onion version of DuckDuckGo
Secure Connection Failed
What should I do?
Had some trouble posting this. Maybe there is another version of this.
Yesterday I tried to add…
Yesterday I tried to add that I was unable to connect to the onion version of DuckDuckGo
Secure Connection Failed
was the problem reported.
My comment did not stick. Now trying again.
I have now twice, different…
I have now twice, different nights, tried to add a comment that I cannot even reach DuckDuckGo's onion site. I get
Your connection is not secure
My attempts, at least the second, went as far as that you promised me to considered them in a review, but they vanish without a trace. Have you found them of little interest?
This is the fourth time I…
This is the fourth evening I try to add that off and on I cannot even reach the onion version of DuckDuckGo. Often I get
Secure Connection Failed
other times Firefox just never reach DuckDuckGo.
The problem goes on. Often I…
The problem goes on. Often I cannot even reach onion version of DuckDuckGo. And the last few times I have not been able to add comments to this blog.
Is this a issue or what is…
Is this a issue or what is tor compromised
http://deepdot35wvmeyd5.onion/2018/01/31/leak-shows-us-army-nsa-comprom…
Does not look good to me
There is no security…
There is no security classification on the document when something like this would be considered confidential. The guy even left his name and face in the picture which would be very dumb if he wanted to leak such information.
Thank you
Thank you
Wow, I just went through the…
Wow, I just went through the entire comment thread to make sure this hasn't been discussed already. The people who work on Tor have the patience of saints.
Anyway, I just noticed a typo on the changelog for version 7.5. That contains the following line:
* Bug 21245: Add da translation to Torbutton and keep track of it
I'm sure that "da" is supposed to be "a". So when time permits, you might want to change that.
Actually, no, it is not a…
Actually, no, it is not a typo. It means the danish translation (country code "da") got added to Torbutton. :)
Blank "pr" in cached…
Blank "pr" in cached-microdesc-consensus file is right?
r DrinkPaint 163.172.190.130 9001 9030
s Fast Running Stable V2Dir Valid
v Tor 0.2.9.11
pr
w Bandwidth=1380
Does the setting "plugin…
Does the setting plugin.disable_full_page_plugin_for_types still exist? (I have it and its value is set to application/pdf.)
Is there an easy way to reset all about:config settings to default, without reinstalling Tor Browser?
Thank you for your work.
Looking at the Firefox…
Looking at the Firefox source code, yes, it still exists in Firefox 52. No, there is no easy way to reset all the changes preferences. That's one of the reasons we encourage to use the security slider as doing so allows resetting crucial security preferences in a controlled and reproducible way.
Problem dowloading Tor…
Problem dowloading Tor Browser
My System is Windows 8.1
I'm writing from Browser Mozilla Firefox 52.6.0.6607
Last charged : Tor browser 7.5 (don't know if clean) 23 Jan 2018
Until old version all worked OK - Now loading is ever blocked - Copied clip board messages where loading stopped with warning messages:
2/6/2018 7:17:19 AM.000 [WARN] Proxy Client: unable to connect to 154.35.22.9:443 ("general SOCKS server failure")
2/6/2018 7:17:19 AM.500 [WARN] Proxy Client: unable to connect to 154.35.22.12:80 ("general SOCKS server failure")
2/6/2018 7:17:20 AM.500 [WARN] Proxy Client: unable to connect to 154.35.22.10:80 ("general SOCKS server failure")
2/6/2018 7:17:20 AM.500 [WARN] Proxy Client: unable to connect to 192.99.11.54:443 ("general SOCKS server failure")
I think IP Addresses are located USA
Any suggestion?
Can I uninstall and clean all registers of Tor Browsre and Mozilla and then reinstall all?
Dear sirs…
Dear sirs
How do you make sure the exit IP address is always one country. You used to put a line in Torrc file but it no longer seems to work. Could you advise what the procedure is now?
Yours
Allister Denyer
TOR is as far as I know…
TOR is as far as I know intended for all kinds of users (not just the technically expert ones), but it's not evident to me (maybe because I'm not a technically expert one) why all users are prompted to download every new version.
With the exception of those updates that include security-related improvements, it often doesn't seem that there is any reason to install certain updates, despite being encouraged to by prompting from TOR.
Couldn't TOR be specific about which users really need (or can benefit from) updates as they're released, instead of just automatically recommending every update to every user?
> it's not evident to me …
> it's not evident to me (maybe because I'm not a technically expert one) why all users are prompted to download every new version.
This can be inconvenient but it's the only way to ensure you have the latest everything bundled in a tested package (Tor Browser bundle). There is a maxim in the cybersecurity world which holds that everyone needs to patch *everything* they use, because leaving anything unpatched opens up a hole. Security experts often find themselves trying to clean up the mess which results when (all too often) bad actors exploit just such a hole.
seriously are people really…
seriously are people really still using tor like it's actually safe
Many people use Tor every…
Many people use Tor every day, so if you have evidence that some of them may be endangered by a specific flaw, please give technical details sufficient for devs to fix the problem.
Tutto OK molte grazie.
Tutto OK molte grazie.
TBB 7.5(with Tor 0.3.2.9) is…
TBB 7.5(with Tor 0.3.2.9) is connecting slow when using Guard with Tor 0.3.2.9 or is it a problem with the first hop/Guard?
Guard has enough Bandwidth, bigger as 10000, heartbeat is inconspicuous.
I just recently updated to…
I just recently updated to the new Tor 7.5 and my Tor will now no longer work?
It keeps saying something about connection disabled or something like that?
I've checked my clock and it's fine!
I've looked everywhere and can't figure this out..
You see, I can install an older version of Tor and it works PERFECTLY fine but NOT when I update to the new version, so now why is this?
It's hard to say. Do you…
It's hard to say. Do you have some log output that might be helpful?
I have a problem with the…
I have a problem with the CAPTCHA on many sites. Is there some kind of formula or something I am not aware of?
Does anyone know if theres a…
Does anyone know if theres a safe app for sms text messageing that cant b traced back to who sent it
Nice work - thanks…
Nice work - thanks.
Would it be possible to have a version of Tor Browser that can be installed on Windows like a regular browser (in additional to the portable TBB)?
What does a regular browser…
What does a regular browser differently? Registry entries? And installation + different profiles for different users? That's tricky. There are no concrete plans yet for providing those features.
v.good
v.good
To whom it may concern…
To whom it may concern
My TBB stopped working after an autoupgrade, the bootstrap process appears unaffected, however, the browser cannot load any webpages, it keep saying 'Secure Connection Failed'.
I tried to use new identity, use various bridge modes, didn't help one bit. Suspecting a corrupted update, I downloaded a fresh copy of installer using VPN, and the problem still persists.
I'm on windows7 64bit, previous version of TBB works fine. Please help.
Do you have some Kaspersky…
Do you have some Kaspersky tool installed or any other firewall/antirivus tool? This ticket may help you then: https://trac.torproject.org/projects/tor/ticket/25333
Since this weekend, the…
Since this weekend, the website torproject.org is unreachable - through tor AND plain firefox. I live in Belgium and used telenet and orange as provider. Just this blog is reachable, the download pages and other links in this blog are unreachable too (connection timed out). Problem in BE with restrictions on our internet or at Tor?
Since updating TOR - it won…
Since updating TOR - it won't work for me. I installed the update - wouldn't work - would put in the URL, and it simply wouldn't respond.
Then my PC crashed. When I got it back up the last version of TOR was there again. It worked, but then wanted the update. I updated it.
Now it won't work again....same problem. I put in the URL, hit the arrow or return - and nothing happens. I'm running 2007 Windows Vista, Home Pack Premium Service Pack 2. If it is not compatible, is there a way to revert back to the last version?