New Release: Tor Browser 8.0a9

Tor Browser 8.0a9 is now available from the Tor Browser Project page and also from our distribution directory.
This release features important security updates to Firefox.
Tor Browser 8.0a9 is the first alpha release based on Firefox 60 ESR. We rebased all of our patches, updated our toolchains to pick up new requirements like Rust support, and fixed the most important usability issues and broken functionality.
We rely on your feedback to make Tor Browser better for users around the world. Releasing a Tor Browser alpha before each stable release gives us a valuable window of time to learn about and fix bugs before the stable release is used by millions.
New Features
If you are comfortable with Tor Browser, we need your help! This alpha has a lot of new features, including a couple major UX changes, and we want them to be in tip-top shape before the stable release hits this September. Here's a taste of what's new:
- Improved Circuit Display:
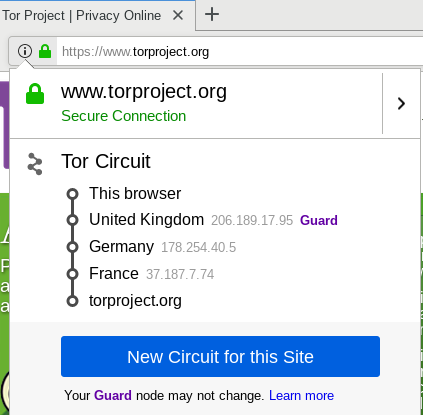
We've heard a lot of confusion about how the first guard in the Tor Circuit Display stays the same for months, even if you select "New Identity." This is by design, so now, we're trying to to better communicate that to the user and better manage expectations about both "New Identity" and "New Tor Circuit for this Site."
- Onion Indicators:

We're trying out a new system for indicating .onion sites' relationships to TLS certificates. We mapped all the current padlock states Firefox has for sites' TLS certificates, and from there, we've built a new system for communicating these states when they are related to .onion sites.
- New Locales: We added support for da, he, sv-SE, and zh-TW to give users speaking those languages an improved Tor Browser experience. The plan is to add even more locales once we are confident we can handle the additional load and disk space requirements.
- New Torbutton Icon: We replaced our old Torbutton icon with a shiny new one. That's the first step in redesigning Tor Browser icons and making them compatible with Firefox's Photon UI. There is more to come in the next alphas.
- Full Sandboxing Support for Windows: We are able to provide full content sandboxing support for 64bit Windows bundles now, thanks to the work done by Tom Ritter.
Additionally, we updated a number of components we ship: Tor to 0.3.4.2-alpha, Torbutton to 2.0.1, TorLauncher to 0.2.16.1, HTTPS-Everywhere to 2018.06.21, and NoScript to 10.1.8.2. Expect more bugs than usual in this alpha.
Known Issues
We already collected a number of unresolved bugs in Tor Browser 8.0a9 and tagged them with our ff60-esr keyword to keep them on our radar. The most important ones are listed below:
- Meek is currently broken. We need to update the browser part for make it compatible with ESR60.
- On Windows localized builds on first start the about:tor page is not shown, rather a weird XML error is visible.
- Maybe related to 2) NoScript does not seem to work properly on Windows builds right now.
- We are not done yet with reviewing the network code changes between ESR52 and ESR60. While we don't expect that proxy bypass bugs got introduced between those ESR series, we can't rule it out yet.
- We disable Stylo on macOS due to reproducibility issues we need to investigate and fix.
- We ran into issues while creating the incremental update files. In order to avoid respinning yet another release candidate and redoing the signing work, we opted into patching our mar-tools locally. For those of you who want to reproduce our builds (please do!) bug 26472 has steps that explain what we did.
Give Feedback and Report Bugs
If you find a bug or have a suggestion for how we could improve these changes, please let us know. There are several ways you can reach us with feedback about this alpha including commenting on this post, emailing us at frontdesk@torproject.org, or contacting the developers at the tbb-dev mailing list. We track all Tor Browser 8 related issues with the ff60-esr keyword in our bug tracker and are happy with bug reports, there, too. Be sure to include as many of these as possible:
- Your OS
- Tor Browser version
- Step by step of how you got to the issue, so we can reproduce it (e.g. I opened the browser, typed a url, clicked on (i) icon, then my browser crashed)
- A screenshot of the problem
- The debug log
- A descriptive subject line (if you're emailing us)
Thank you for your support!
Changelog
Note: This alpha release is the first one that gets signed with a new Tor Browser subkey, as the currently used one is about to expire. Its fingerprint is: 1107 75B5 D101 FB36 BC6C 911B EB77 4491 D9FF 06E2. We plan to use it for the stable series, too, once Tor Browser 8 gets released.
The full changelog since Tor Browser 8.0a8 is:
- All platforms
- Update Firefox to 60.1.0esr
- Update Tor to 0.3.4.2-alpha
- Update Libevent to 2.1.8
- Update Binutils to 2.26.1
- Update Torbutton to 2.0.1
- Bug 26100: Adapt Torbutton to Firefox 60 ESR
- Bug 26430: New Torbutton icon
- Bug 24309: Move circuit display to the identity popup
- Bug 26128: Adapt security slider to the WebExtensions version of NoScript
- Bug 23247: Show security state of .onions
- Bug 26129: Show our about:tor page on startup
- Bug 26235: Hide new unusable items from help menu
- Bug 26058: Remove workaround for hiding 'sign in to sync' button
- Bug 20628: Add locales da, he, sv, and zh-TW
- Translations update
- Update Tor Launcher to 0.2.16.1
- Update HTTPS Everywhere to 2018.6.21
- Update NoScript to 10.1.8.2
- Bug 25543: Rebase Tor Browser patches for ESR60
- Bug 23247: Show security state of .onions
- Bug 26039: Load our preferences that modify extensions
- Bug 17965: Isolate HPKP and HSTS to URL bar domain
- Bug 26365: Add potential AltSvc support
- Bug 26045: Add new MAR signing keys
- Bug 22564: Hide Firefox Sync
- Bug 25090: Disable updater telemetry
- Bug 26127: Make sure Torbutton and Tor Launcher are not treated as legacy extensions
- Bug 26073: Migrate general.useragent.locale to intl.locale.requested
- Bug 20628: Make Tor Browser available in da, he, sv-SE, and zh-TW
- Windows
- OS X
- Bug 24052: Backport fix for bug 1412081 for better file:// handling
- Bug 24136: After loading file:// URLs clicking on links is broken on OS X
- Bug 24243: Tor Browser only renders HTML for local pages via file://
- Bug 24263: Tor Browser does not run extension scripts if loaded via about:debugging
- Bug 24632: Disable snowflake for now until its build is fixed
- Bug 26438: Remove broken seatbelt profiles
- Linux
- Bug 24052: Backport fix for bug 1412081 for better file:// handling
- Bug 24136: After loading file:// URLs clicking on links is broken on Linux
- Bug 24243: Tor Browser only renders HTML for local pages via file://
- Bug 24263: Tor Browser does not run extension scripts if loaded via about:debugging
- Bug 26153: Update selfrando to be compatible with Firefox 60 ESR
- Bug 22242: Remove RUNPATH in Linux binaries embedded by selfrando
- Bug 26354: Set SSE2 support as minimal requirement for Tor Browser 8
- Build System
- All
- Bug 26362: Use old MAR format for first ESR60-based alpha
- Clean up
- Windows
- Bug 26203: Adapt tor-browser-build/tor-browser for Windows
- Bug 26204: Bundle d3dcompiler_47.dll for Tor Browser 8
- Bug 26205: Don't build the uninstaller for Windows during Firefox compilation
- Bug 26206: Ship pthread related dll where needed
- Bug 26396: Build libwinpthread reproducible
- Bug 25837: Integrate fxc2 into our build setup for Windows builds
- Bug 25894: Get a rust cross-compiler for Windows
- Bug 25554: Bump mingw-w64 version for ESR 60
- Bug 23561: Fix nsis builds for Windows 64
- Bug 23231: Remove our STL Wrappers workaround for Windows 64bit
- Bug 26370: Don't copy msvcr100.dll and libssp-0.dll twice
- Bug 26476: Work around Tor Browser crashes due to fix for bug 1467041
- Bug 18287: Use SHA-2 signature for Tor Browser setup executables
- OS X
- Bug 24632: Update macOS toolchain for ESR 60
- Bug 9711: Build our own cctools for macOS cross-compilation
- Bug 25548: Update macOS SDK for Tor Browser builds to 10.11
- Bug 26003: Clean up our mozconfig-osx-x86_64 file
- Bug 26195: Use new cctools in our macosx-toolchain project
- Bug 25975: Get a rust cross-compiler for macOS
- Bug 26475: Disable Stylo to make macOS build reproducible
- Linux
- All
Comments
Please note that the comment area below has been archived.
Cloudflare`s serves CAPTCHAs…
Cloudflare`s serves CAPTCHAs when browsing websites with this alpha release but not with the stable release, why?
That's because Cloudflare is…
That's because Cloudflare is treating the current stable specially and they have not adjusted so for the alpha yet. We plan to get this fixed soon.
Fix UA first ;)
Fix UA first ;)
Fix UA first ;) This should…
This should be written in a 500px extra extra bold font just to emphasize it
It does surprise me that the…
It does surprise me that the UA has been changed in this release since that makes it stand out from stable Tor Browser as well as (presumably) Orfox. Tor Browser used to always give the same user agent indicating Windows 7 regardless of the true OS, but now my user agent does show my OS.
Found the bug, I think: https://trac.torproject.org/projects/tor/ticket/26146
This as a known issue and it…
This as a known issue and it is tracked in ticket 26146. Considering that the OS is leaked in other ways too and that there are many other higher prioritized tickets concerning the release of the new Firefox-60-based Tor Browser, it could take a while to have this corrected.
Cloudflare always CAPTCHAs…
Cloudflare always CAPTCHAs me, even when I'm using the current version of Tor.
Thanks to Tom Ritter for…
Finally! Been waiting for a first Torfull encounter with ESR60 for months now! Thanks to Tom Ritter for doing the fantastic tireless work on getting sandboxing to Windows, will save countless souls quiet literally! :)
> Linux
> Bug 26153: Update selfrando to be compatible with Firefox 60 ESR
Thanks a ton as well for not forgetting about SelfRando!
Thanks again to the team for the great work, we'll support you as much as we can! <3
Very nice update, it's all…
Very nice update, it's all running good and smooth, but I go to panopticlick.eff.org and the shocker comes when seeing that my user agent LEAKS MY OS even with JS disabled o_0 PLEASE FIX ASAP!!!! NEEDS TO BE SET TO WINDOWS!!!
Btw keep getting this:
Regarding the User Agent…
Regarding the User Agent that's expected as we hardly can hide the OS differences anyway and spoofing the User Agent has dramatic usability penalties depending on the platform. E.g. if we'd use the traditional Windows UA for Tor Browser for Android then all mobile users would suddenly get desktop pages on their phones essentially breaking the browsing experience.
Another example: It turns out that Google Docs break for Mac users as the respective Ctrl key is not working anymore.
So, the idea was to just report the OS and give up spoofing it in the User Agent. I am not sure about the architecture, though, yet. We have https://trac.torproject.org/projects/tor/ticket/26146 for the whole discussion.
Regarding the RequestGuard error: I Opened https://trac.torproject.org/projects/tor/ticket/26545.
I can understand the…
I can understand the reasoning when it comes to mobile, but why just give up the spoofing among desktop OSs just because it's imperfect? I doubt most websites use the advanced OS detection techniques - I've been using Tor Browser for years and all the websites that used OS detection thought I was using Windows (which is not what I actually use). I'm sure many 3rd party trackers themselves are more advanced and detect both the actual OS and the spoofing however I doubt a lot of them penalize the user somehow for it.
perhaps discussed in those…
perhaps discussed in those bugtracs, but...
- the android code is already much different from Windows code
- incorporate ua spoofing into one of groupings in the security slider?
No, the security slider is…
No, the security slider is for *security* trade-offs and has nothing to do with enabling or disabling fingerprinting etc. (in general *privacy*) features. We won't mix both.
True. As mentioned in the…
True. As mentioned in the trac ticket, while font fingerprinting defenses are not perfect, they're perfect enough for JS disabled users and a bunch of other sites and trackers that don't employ OS detection in the first place. The solution ought to be: "Hey let's ameliorate font and OS fingerprinting defenses! In the meantime keep the UA the same since it's simple to do!" rather than the defeatist "Look, we will always lose, we can do nothing, put fire in your clothes and reveal your OS to everybody".
Bug: If you open an image…
Bug: If you open an image like https://blog.torproject.org/sites/default/files/styles/full_width/publi… then it doesn't get displayed in the center, something seems broken
Thanks, I opened https:/…
Thanks, I opened https://trac.torproject.org/projects/tor/ticket/26544.
Please add the light and…
Please add the light and dark themes that were added in FF53
https://i.imgur.com/V17nLtc.png
We ship with whatever…
We ship with whatever Firefox ships by default. If the user wants to customize their Tor Browser it's up to them. However, please note that those customizations might make it easier to fingerprint users.
The built in light and dark…
The built in light and dark themes shouldn't affect fingerprinting as AFIK they are based on the old personas system. Changing the density probably would due to window size changes.
But never mind, they are there. It just took a 2nd restart of TB for them to appear for some reason.
Thanks.
I'm just a casual and…
I'm just a casual and regular user of Tor Browser but I'm so excited about this update. Another humongous THANK YOU from this global citizen.
I miss my green onions! …
I miss my green onions! Panicking all the time that my browser has slipped out of TOR. Can you change the gray onion icon to a colored one? It disappears in my peripheral vision if its the same as everything around it. Green for on?
Thanks for the feedback,…
Thanks for the feedback, noted. We are trying to adapt our icons and logos to the new Firefox Photon design and this alpha is the first start in doing so. We'll see how we adjust things so that hopefully everyone will be happy about the final result.
On Windows, the new…
On Windows, the new Torbutton icon looks tiny and slightly pixelated compared to a screenshot in this ticket:
https://trac.torproject.org/projects/tor/ticket/25693
"that hopefully everyone…
"that hopefully everyone will be happy about the final result."
Mozilla seems to have same kind of problems:
https://www.bleepingcomputer.com/news/technology/facebook-google-manipu…
https://fil.forbrukerradet.no/wp-content/uploads/2018/06/2018-06-27-dec…
Thank You to everyone who…
Thank You to everyone who has been working so hard to get us up to speed w/ 60. I can't believe it's finally here! I'm sure you'll get a lot of complaints about the UI especially by the time September rolls around, so be ready for that. Anyway, I just wanted to say "Thank You" and keep up the good work!
Good afternoon! The new…
Good afternoon! The new design of Tor 8.0a9 is absolutely disgusting! The new version of Tor threw me all the settings, plus required the reinstallation of all add-ons! This is swinishness! Thank you for disrespect!
Which new design do you mean…
Which new design do you mean? The one that Firefox ships? That's hardly a thing we can change. Tor Browser is not touching any of your customizations. In particular, it does not touch any of your extensions. Could you give us some steps to reproduce your issue? In particular, which extensions got lost during the update? On which platform? Etc.
Looking For Android browser…
Looking For Android browser ver google
> Full Sandboxing Support…
> Full Sandboxing Support for Windows: We are able to provide full content sandboxing support for 64bit Windows bundles now, thanks to the work done by Tom Ritter.
You need to enable SEH like in libstdc++ to say "Full Sandboxing Support".
SEH support is orthogonal to…
SEH support is orthogonal to full content sandboxing. But, yes, we should think about adding the former to our 64bit builds.
ha hahttps://dxr.mozilla.org…
ha ha
https://dxr.mozilla.org/mozilla-esr60/source/security/sandbox/chromium/…
> Known Issues OMG!!!…
> Known Issues
OMG!!! Finally, it's added to the official post! Keep up this best practice!
> We ran into issues while…
> We ran into issues while creating the incremental update files.
Full update got stuck at "Connecting to the update server..." after partial update failed.
'About Tor Browser' menu didn't show any update in progress.
After pressing 'Hide' button, TBB started to dl the update!
But got stuck at 15 MB when I opened 'About Tor Browser' menu.
After closing and reopening it, it showed it had started to dl from 0 MB.
That looks like some incompatibility between your and FF's update mechanisms.
We are using Firefox's…
We are using Firefox's updater. I guess you have trouble with your network connection which makes it hard to download the big updates (even the incremental ones are several dozens of MBytes this time). Not sure what we could do about that, though.
No, it looks like your bug …
No, it looks like your bug (2 calls) ;)
AUS:SVC Downloader: cancel
AUS:SVC UpdateService:downloadUpdate - no support for downloading more than one update at a time
Well, that indicates that a…
Well, that indicates that a download is already ongoing and I think it's not unreasonable to not allow download a second update in parallel. Or are you indicating there is a bug somewhere else? If so, could you give us steps to reproduce it?
It got stuck downloading -…
It got stuck downloading - that's all what a user see.
What makes it think it's downloading something twice is unknown.
Intermittent bug.
Windows 10 win64 full update…
Windows 10 win64 full update failed:
The Update could not be installed (patch apply failed)
I guess that's https://trac…
I guess that's https://trac.torproject.org/projects/tor/ticket/26514. It should work eventually but for some reason the update is failing intermittently. Could you report back when you get the update properly applying at last?
full update failed on win64…
full update failed on win64 and logged only this:
failed: 19
I guess that's https://trac…
I guess that's https://trac.torproject.org/projects/tor/ticket/26514. It should work eventually but for some reason the update is failing intermittently. Could you report back when you get the update properly applying at last?
It is a clean 8.0a7 -> a8 -…
It is a clean 8.0a7 -> a8 ->a9, no obfs4 or anything.
Updater logs that hashes match every time.
Deleting UpdaterInfo folder doesn't help.
It doesn't look intermittent.
partial -> full -> partial -> full ->... boring... (4 cycles with no luck, what to investigate?)
(Does this cert check require an internet connection?)
Looks like a race condition…
Looks like a race condition as it doesn't happen on slow machines.
https://www.torproject.org…
https://www.torproject.org/projects/torbrowser.html.en
Where is: sandbox-0.0.16-linux64
It is unmaintained and the…
It is unmaintained and the original maintainer therefore asked us to stop building and distributing it. See: https://trac.torproject.org/projects/tor/ticket/25540.
> Bug 26204: Bundle…
> Bug 26204: Bundle d3dcompiler_47.dll for Tor Browser 8
The latest version of this file seems to be v. 10.0.15063.675, please, update.
You mean that's the latest…
You mean that's the latest version Firefox ships? Because we think about following Mozilla in what they ship in ESR 60.
No, that's the latest…
No, that's the latest security update of 15063 branch. Firefox ships 10.0.15063.674. Why do you think about following Mozilla in what they call security? It's unacceptable for security-conscious software. And it is solely your responsibility to provide security updates for all bundled software you ship.
I created https://trac…
I created https://trac.torproject.org/projects/tor/ticket/26650 to move forward here.
Seems ANGLE is broken: Error…
Seems ANGLE is broken:
Error: WebGL warning: Unable to restrict WebGL limits to minimums. Troubleshoot.jsm:525:18
Error: WebGL warning: Failed to create WebGL context: WebGL creation failed:
* Troubleshoot.jsm:525:18
8.0a8 works.
How can I reproduce that?
How can I reproduce that?
Check about:support on…
Check about:support on Windows?
Thanks, I opened https:/…
Thanks, I opened https://trac.torproject.org/projects/tor/ticket/26649 to track this issue.
Maybe, it can help:…
Maybe, it can help:
unavailable by runtime: ANGLE is disabled
I don't think that#s an…
I don't think that's an issue. That's visible as
D3D11_HW_ANGLEis not available.Still 3 hops instead of four
Still 3 hops instead of four
Tor Browser has Firefox icon…
Tor Browser has Firefox icon instead of the usual Tor Browser icon on the task bar in Linux Mint.
https://i.imgur.com/dRQdejg.png
Thanks for the report. We…
Thanks for the report. We have this ticket:
https://trac.torproject.org/projects/tor/ticket/26519
FCC Message Alert! An FCC…
FCC Message Alert!
An FCC error has occured
We're sorry, an unexpected error occurred with your request.
Reference # 18.2418ae8c.1530208790.8e4a5b
18:04:09.454 TypeError:…
18:04:09.454 TypeError: Argument 1 of PrecompiledScript.executeInGlobal is not an object. 1 ExtensionContent.jsm:489:18
> Update Binutils to 2.26.1…
> Update Binutils to 2.26.1
That's about the Build System ;)
> Update HTTPS Everywhere to…
> Update HTTPS Everywhere to 2018.6.13
to 2018.6.21 ;)
Thanks. I updated the…
Thanks. I updated the changelog to fix this.
This is how it looks on…
This is how it looks on Linux Mint 19 with a dark theme in Cinnamon: https://i.imgur.com/Zy7MnET.png
This isn't a bug report, more of a question of where this could be fixed to look better. Firefox? TBB? The theme maker?
Hi, how can I disable…
Hi, how can I disable javascript now?
To disable javascript you…
To disable javascript you can click the onion, select "Security Settings", then select the "Safest" level. If you don't want to change the security level, you can go to the addons page (entering about:addons in the URL bar), click on the Noscript preferences button, then uncheck the "script" check-box on the DEFAULT sites.
This doesn't work
This doesn't work
I'ts nice
I'ts nice
please fix the icons to make…
please fix the icons to make them change color with firefox test pilot's color thing
NoScript is broken on Linux…
NoScript is broken on Linux 64-bit 8.0a9 but it was fine on the previous alpha. It's disabled because "NoScript is incompatible with Tor Browser 60.1.0." The version is 10.1.8.2 like it's supposed to be.
Huh, it's running fine here…
Huh, it's running fine here. Did you modify the previous alpha before the update somehow? Does that happen as well with a freshly downloaded Tor Browser 8.0a9?
The "sig" for the 64bit" "8…
The "sig" for the 64bit" "8.0a9" from the TOR download page could not be verified with the downloaded program.
And the fingerprint from above: 1107 75B5 D101 FB36 BC6C 911B EB77 4491 D9FF 06E2, brings up the current (signing key - 15 Dec 14 to 24 Aug 20) when you search on a "keysever", so I am unable to the verify the downloaded program.
Please Advise - email address: siranger@protonmail.com
Which command did you use…
Which command did you use and what error are you getting?
This release has been signed by a new subkey, so it's possible that you need to refresh the Tor Browser key:
gpg --refresh-keys 4E2C6E8793298290
With both the "torbrowser…
With both the "torbrowser-install-win64-8.0a9_en-US.exe" & "torbrowser-install-win64-8.0a9_en-US.exe.asc" in the same folder, I right clicked on the 8.0a9 install file and selected "Verify". This normally come back with a msg saying the two file verify, but this time I got a msg saying "The Data could not be verified."
Is there a way to attached an image file here?
I downloaded the installer…
I downloaded the installer twice from the Project page, and installed and then re-installed 8.0a9. I got the same result both times:
1. After clicking "Test Tor Network Settings" link to reach https://check.torproject.org/?lang=en_US , the page says the browser is configured to use tor, but it is not tor browser in big orange letters.
2. There is no green padlock on "https" pages, and info from the address bar says the pages are NOT encrypted.
I have deleted 8.0a9 from my windows machine, and I will watch for further commentary here.
check.torproject.org does…
check.torproject.org does not recognize the new Tor Browser version yet. We have this ticket to track the issue:
https://trac.torproject.org/projects/tor/ticket/26566
Do you have an example of an https page where there is no green padlock? Is it happening on some https pages only, or all of them?
I'm back, and re-downloaded…
I'm back, and re-downloaded the 8.0a9 installer from https://www.torproject.org/projects/torbrowser.html.en#downloads-alpha on Windows for a test. All https sites that I checked report as not secure, nor encrypted. Onion sites report as secure. Here goes:
Tested - NOT ENCRYPTED, NOT SECURE
https://check.torproject.org/?lang=en_US
https://www.startpage.com/
https://search.disconnect.me/
https://en.wikipedia.org/wiki/Main_Page
https://searx.me/
Tested - ENCRYPTED, SECURE
https://3g2upl4pq6kufc4m.onion/ ... duckduckgo onion
http://ulrn6sryqaifefld.onion/ ... searx onion
Thank you for your reply, and best wishes.
Hello ... I'm the same…
Hello ... I'm the same person as before who posted about no green padlocks. I have re-tested TB 8.0a9 today, and I'm getting green padlocks plus security certificate data. Some tested websites follow:
https://www.theguardian.com/world
https://www.startpage.com/
https://www.nytimes.com/
https://www.rt.com/
https://www.bbc.com/news
https://www.washingtonpost.com/
https://www.reuters.com/
https://www.aljazeera.com/
https://theintercept.com/
I don't know what changed, or how it changed - but thanks.
I am using Windows. The…
I am using Windows. The Check Tor Project page of 8.0a9 has orange graphics. The page
reports that although the browser is configured to use Tor, the browser itself is not tor browser. Also, the address bar information ("i" encircled) reports that encrypted pages are not encrypted ... starting with the Check Tor Project page itself! I have downloaded the installer twice from the project page, and installed 8.0a9 twice. I have used the Tor button installation method, also. The results are the same each time. Thanks for all that the Tor team has done for us. I will use 8.0a8 for now, and hope to see more information in the comments.
This is an issue with check…
This is an issue with check.torproject.org which does not recognize the new Tor Browser version yet. We have a ticket to track this issue:
https://trac.torproject.org/projects/tor/ticket/26566
On Windows, the Check Tor…
On Windows, the Check Tor Project page reports that the browser is configured for Tor but is not Tor Browser ... in orange font. Also, encrypted pages are reported by the encircled "i" icon in the address bar as NOT ENCRYPTED (I'm not shouting, just kind of excited - that's all). I have downloaded the installer twice from the project page, and installed 8.0a9 twice. I have also used the Tor button update option. I get the same results each time. Thank you for your hard work to help us all. I'll use 8.0a8 for now until some clarification results.
I'm still not seeing my two…
I'm still not seeing my two earlier comments while you've answered my later ones. Censorship?!
Wow, I can see that as…
Wow, I can see that as someone stated (not very politely), TP is staggering under a long long list of issues to fix just to keep TB from becoming more insecure week by week, in the face of so many technical threats.
Quick comment on appearances: IMO, security/privacy should always be prioritized over cosmetics. My main concern with FF's changing design (have they never heard of "if it aint broke dont fix it"?) forcing TB to follow suit is that regular users will be confused by appearances, possibly even harmed owing to some misunderstanding based on previous experience of using TB.
> 2016 IRS Form 990 and…
> 2016 IRS Form 990 and other forms expected like usual in late 2017
Nu? It's Jun 2018 and Form 990 nowwhere to be seen.
Yes, we are late. It seems…
Yes, we are late. It seems the auditor takes more time than expected this time.
High contrast windows themes…
High contrast windows themes mess up the browser. I'm currently typing black on black.
Please add bridge relay's…
Please add bridge relay's country to circuit display.
I opened https://trac…
I opened https://trac.torproject.org/projects/tor/ticket/26648 for that request, thanks.
Backport? https://bugzilla…
Backport? https://bugzilla.mozilla.org/show_bug.cgi?id=1430092
We are already discouraging…
We are already discouraging Windows users to run Tor Browser as admin. Thus, I think it's not needed to backport this patch.
I removed NS when I meant to…
I removed NS when I meant to temporarily disable it. Are there any NS settings specifically for TorBrowser or can I just download it from the add-ons page? Yes or no is sufficient.
I think you can just…
I think you can just download it from addons.mozilla.org.
Why --disable-stylo -…
Why
--disable-stylo
--disable-jemalloc
missed in about:buildconfig?
Good question, I don't know…
Good question, I don't know. In fact those are not the only configure flags that are missing in
about:buildconfig. I guess that's a Firefox bug.FWIW I opened https://trac…
FWIW I opened https://trac.torproject.org/projects/tor/ticket/26911 to track this issue.
ADVANCED_LAYERS available by…
ADVANCED_LAYERS
available by user: Enabled for Windows 7 via user-preference
->:
GPU_PROCESS
failed by runtime: Failed to connect GPU process
(#3) Error Killing GPU process due to IPC reply timeout
(#4) Error Failed to connect GPU process
(#5) Error Receive IPC close with reason=AbnormalShutdown
Hello, Is that mean the…
Hello,
Is that mean the current version base on the 52.x version of Firefox will be discontinued any time soon ?
The problem with this new version is that gtk3 is required, which mean dbus too along with some other lib that will help the remote seats
It will be discontinued in…
It will be discontinued in September as there won't be any Firefox security updates anymore then for ESR52.
ogni volta che cerco di…
ogni volta che cerco di aprire tramite Torbrowser un file .onion mi da il seguente errore:
-Impossibile stabilire una connessione con il server proxy
Firefox è configurato per utilizzare un server proxy che non risulta raggiungibile.
Verificare la correttezza delle impostazioni del proxy.
Verificare se il computer ha una connessione di rete funzionante.
Se il computer o la rete sono protetti da un firewall o un proxy, assicurarsi che Tor Browser abbia i permessi per accedere al web.
ho configurato le configurazioni avanzate come descritto in più siti, ma niente, consigli o soluzioni?
grazie
When visiting a handful of…
When visiting a handful of onion links, I'm told I can't view them because I need a Tor browser. Not a lot of sites, just a few...but enough to make it a pain in the butt.
I also had this issue a…
I also had this issue a couple weeks ago. I remember seeing a white page with the same message and a PGP code. Don't recall all the details. Switched to latest stable and didn't see it on there.
Tor NOTICE: Bootstrapped 78%…
Tor NOTICE: Bootstrapped 78%: Loading relay descriptors
[07-03 07:03:37] Torbutton INFO: tor SOCKS: https://www.https-rulesets.org/v1//latest-rulesets-timestamp via
--unknown--:ecf65b5110e2bf7556687a10f2353282
Tor NOTICE: Bootstrapped 80%: Connecting to the Tor network
Yes, HTTPS-Everywhere is…
Yes, HTTPS-Everywhere is trying pretty early to check for ruleset updates. Torbutton notices this, but as Tor is not ready yet, this attempt will fail.
Please help me about this…
Please help me about this problem.
Tor failed to establish a Tor network connection.
Loading authority certificates failed( clock skew - 6457 in microdesc flavor consensus from CONSENSUS -?).
Tor needs an accurate clock…
Tor needs an accurate clock on your computer to work properly. It seems that's not the case right now for you, which is why it is breaking. So, to solve this make sure to adjust the current time on your machine accordingly.
moz-extension addon was…
moz-extension addon was blocked e.g. feedbro is not working at all
Oh shit! Backport?https:/…
Oh shit! Backport?
https://bugzilla.mozilla.org/show_bug.cgi?id=1447551
If we need it, yes. I am not…
If we need it, yes. I am not sure we do yet, though. Do you have a scenario in mind where we would?
I'm unsure about the…
I'm unsure about the functionality of the security slider in TB version 8.0a9. My security slider has been set to "safest" since browser installation. JavaScript seems to be enabled at that setting. Sites that should have been broken with JavaScript disabled were not. After I used about:config to disable JavaScript, sites that should be broken with security slider set to "safest" were broken. So, I think there may be a problem.
When I start 8.0a9, the …
When I start 8.0a9, the "Welcome to Tor Browser" page is blank white, and many tabs are not enabled. Then, when I click on "New Identity" in the tor onion button, the browser reopens with the correct Welcome page. From that point on, browser navigation seems normal. Thank you.
8.0a9 has started a new…
8.0a9 has started a new dysfunctional behavior. It repeatedly reloads itself. I've included "reload" in the toolbar and, when the browser is convulsing, I can drop the toolbar menu down where it shows "stop" instead of "reload". Hitting "stop" just right to shut off this browser cycling is tricky. That fix usually doesn't last long. Sometimes, a reinstall will smooth things out for a while. But then ... e-yup, right back to the same shenanigans. I think 8.0a9 turns out to be quite rascally, and you have my sympathy ... NOT trying to sound condescending, either. Best wishes to you all at tor project, and thank you for your dedication and help.
thanks a lots,
thanks a lots,
New update just fucking…
New update just fucking broke my browser.
"The proxy server is refusing connections"
Should was installing old to let it work again.
cant download with internet…
cant download with internet download maneger its critical to add its add on to new version other download do not work with all websites
Did not see a real dark…
Did not see a real dark theme.
I switch dark theme on, but the only thing that changes are the window tabs above.
Not the content of the website;
still appears in white.
What to do?!
Which Tor Browser version…
Which Tor Browser version are you using on which platform? And does it work with a regular Firefox 60.4.0esr? (see: https://www.mozilla.org/en-US/firefox/organizations/all/ for test bundles)
The program can't start…
The program can't start because api-ms-win-crt-convert-l1-1-0.dll is missing from your computer. Try reinstalling... which doesn't work.
You need to apply updates to…
You need to apply updates to your Windows version. The missing library was shipped in of of those and you are missing very likely security updates, too.