New Alpha Release: Tor Browser for Android

Mobile browsing is on the rise around the world, and in some parts, it is commonly the only way people access the internet. In these same areas, there is often heavy surveillance and censorship online, so in the past year, we’ve focused on better supporting these users.
There’s never been an official Tor Browser on mobile. Until now.
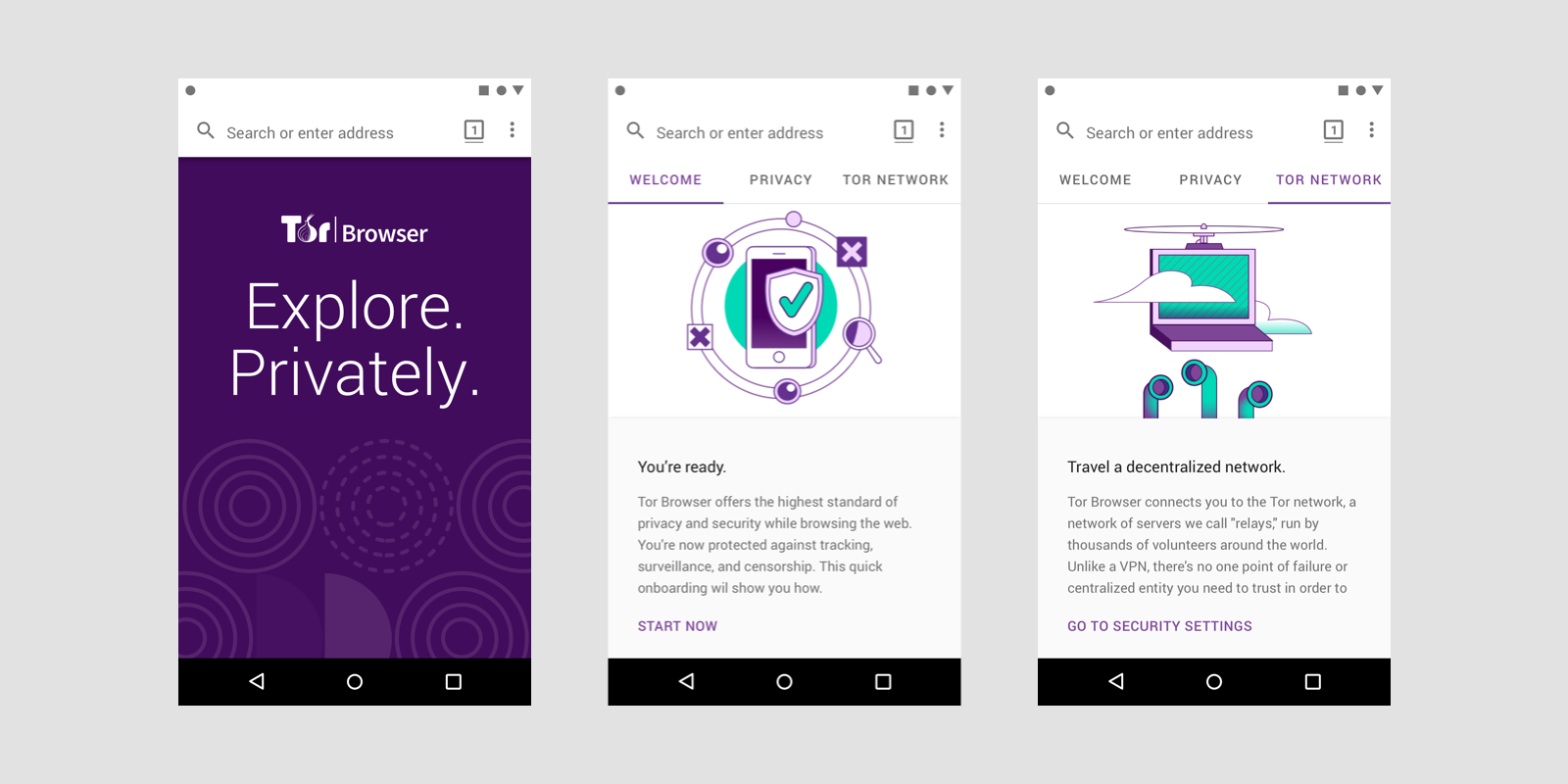
Introducing Tor Browser for Android (alpha), the mobile browser with the highest privacy protections ever available and on par with Tor Browser for desktop. You can download the alpha release on GooglePlay, or you can get the apk directly from our download page. The stable release is slated for early 2019.
Note: For this release, you also need to install Orbot, a proxy application that will connect Tor Browser for Android with the Tor network. For the upcoming Tor Browser for Android stable release, our goal is for Orbot not to be necessary to connect to Tor.
Features
BLOCK TRACKERS
Tor Browser isolates each website you visit so third-party trackers and ads can’t follow you. Any cookies automatically clear when you’re done browsing.
DEFEND AGAINST SURVEILLANCE
Prevent someone watching your connection from knowing what websites you visit. All anyone monitoring your browsing habits can see is that you’re using Tor.
RESIST FINGERPRINTING
Tor aims to make all users look the same, so Tor Browser for Android makes it difficult for you to be fingerprinted based on your browser and device information.
MULTI-LAYERED ENCRYPTION
When you use Tor Browser for Android, your traffic is relayed and encrypted three times as it passes over the Tor network. The network is comprised of thousands of volunteer-run servers known as Tor relays. Watch this animation to learn more about how it works.
BROWSE FREELY
With Tor Browser for Android, you are free to access sites your local internet service provider may have blocked.
What about Orfox?
We're grateful to the Guardian Project for their work developing Orfox, a mobile browser which routes your traffic over the Tor network. With the development of Tor Browser for Android, Orfox will be sunsetted around the time of our stable release, expected in early 2019. You will still be able to use Orbot to route the traffic of all your other apps on Android over Tor.
What about iOS?
There is no official Tor Browser for iOS devices, but we recommend Onion Browser, developed by Mike Tigas.
Help us Improve
Known issue: Our Security Slider is now under ‘Security Settings,’ but because of a small issue, it’s only showing up after you restart the app. We plan on fixing it for the next release.
This is our first version of Tor Browser for Android, so there may be more bugs than usual. If you find a bug or have a suggestion for how we could improve these changes, please let us know. There are several ways you can reach us with feedback about this alpha including commenting on this post, emailing us at frontdesk@torproject.org, or contacting the developers at the tbb-dev mailing list. We track all Tor Browser for Android related issues with the tbb-mobile keyword in our bug tracker and are happy with bug reports, there, too.
Be sure to include as many of these as possible:
• Your Android version
• Tor Browser version
• Step by step of how you got to the issue, so we can reproduce it (e.g. I opened the browser, typed a url, clicked on (i) icon, then my browser crashed)
• The debug log
• A descriptive subject line (if you're emailing us)
Thank you for your support. Happy private browsing.
Comments
Please note that the comment area below has been archived.
Why not available from f…
Why not available from f-droid repo? Will be available in the future?
Greetings
Releasing this app on F…
Releasing this app on F-Droid is more complicated than uploading onto the website and using Google Play. We do want it to be available from F-Droid in the future, but this will take some time and it wasn't a high priority for the first alpha release. Thanks for your interest in it!
We'll be discuss this on https://trac.torproject.org/projects/tor/ticket/27539
Ok, thanks for your answer! …
Ok, thanks for your answer! ;)
Spreading about the release in my blog for Spanish speakers:
https://victorhckinthefreeworld.com/2018/09/07/publicada-la-version-alfa-del-navegador-tor-para-android/
Happy hacking!!
i want to second the f-droid…
i want to second the f-droid suggestion. I am not thrilled about google knowing I use Tor. And downloading the APK and installing it manually is cumbersome. So f-droid gets +1 from me.
But no link at your web site…
But no link at your web site lol :D
What do you mean? See: https…
What do you mean? See: https://www.torproject.org/download/download.html.en and there the Android drop down menu.
Is on Fdroid now. 2 Versions…
Is on Fdroid now. 2 Versions ,so far.☺
Finally, a Tor browser based…
Finally, a Tor browser based on recent Firefox version.
Android Tor browsers are still identifiable because of screen size and color depth. Are there plans to block this method of fingerprinting?
Yes, we plan to provide…
Yes, we plan to provide similar protections as we have for desktop. For the screen size we have https://trac.torproject.org/projects/tor/ticket/27083. The plan is to shrink the gap between desktop and mobile defenses against tracking with each alpha release and provide the same with the first stable mobile version.
>Tor can't open after update…
>Tor can't open after update on mac 10.9.5
See: https://trac.torproject…
See: https://trac.torproject.org/projects/tor/ticket/27482, in particular comment 12.
Finally, a great privacy…
Finally, a great privacy advancement in mobile history!
7.
So this still uses obit…
So this still uses obit right?
It still uses Orbot, right.
It still uses Orbot, right.
Does not show up on Google…
Does not show up on Google Play on my Android phone, although it does on my PC. Any ideas ?
Will it be available on F…
Will it be available on F-Droid eventually??
Great news! But for now,…
Great news! But for now, which app is considered the most stable/secure/fast ? (Orweb, orfox or alpha?) Obviously it's not alpha yet but I'll give it a shot. Keep doing the great job!
Does Mike Tigas have any…
Does Mike Tigas have any similar redesigns planned for Onion Browser?
Why does it have 3 dots …
Why does it have 3 dots (chrome style) instead of the hamburger menu?
I install it and try it is…
I install it and try it is crash very fast may be
there is bug .
thank you
What device are you using?…
What device are you using? Could you give us steps to reproduce your crashes?
Hey folks! Thanks again for…
Hey folks! Thanks again for this release especially Igor and Mathew! One question: Will there be an alpha version of the TBA after the final stable release is made (just like with TB for Desktop)?
It's not decided yet, but,…
It's not decided yet, but, yes, somehow we need to have a way to test new features before they'll reach the stable channel. We'll think about it.
Does this ship with its own…
Does this ship with its own up-to-date CA certificates or does it rely on Android's system-wide preexisting CA certificates?
what happened to new…
what happened to new identity button in the top bar? now you have ot go into menu and click on it. usedd to be a new identity restart browser icon for so easier convenience
Seems to be based on Chrome…
Seems to be based on Chrome/Chromium this time around, is it not?
No, still Firefox which…
No, still Firefox which allows us to apply more and more the protections we've already developed for the Tor Browser stable.
Any plans for iOS?
Any plans for iOS?
Not yet. We need to try…
Not yet. We need to try Android going first. :)
Thanks for this version!…
Thanks for this version! Spreading this release through my blog @ https://www.savedel.com/2018/09/tor-browser-for-android-launched-download-apk.html
Hi I use TOR for political…
Hi
I use TOR for political activity on Facebook and Twitter, ... in a dictatorship country, I need the best and the safest settings to apply in TOR desktop version to give me better feel, because I'm worried about the country's thought police and their IT experts, not to trace my activities. Many people like to use TOR, but they worry and don't know the safest settings and useful tips to save them from governmental spies. I know how to work with Tor and checked its settings out, but I need some advice from a Tor expert to give me some guides about privacy and security settings.
Another question I have doubt about it is, Is it safe to use Tor with a VPN program? Is it safe? For getting better safety, Is it good to use another VPN with Tor or not? some guys answer yes, some say no! I'm confused.
Sorry, I ask this question here that is not related to this post, but I need a quick answer and it's vital for me and some people who use Tor for political activity and journalists who I know them and I want to help them as well.
Thank You very much
Best
Unknown
First, you are not alone: …
First, you are not alone:
rsf.org
cpj.org
hrw.org
amnesty.org
Second, if you do not already use Tails you should definitely try to obtain and use the current version, Tails 3.9:
tails.boum.org
Tails is an "amnesiac" OS which you boot from a USB or DVD and which will enable you to write documents, etc., as well as to surf over the Tor network using the latest Tor Browser, to access onion sites, etc. "Amnesiac" means Tails leaves no traces on your hard drive; you store documents you need to keep, seriously encrypted, in a special way on the USB or in removable encrypted media which are more easily hidden or destroyed in an emergency. It is ideal for journalism or political activity in dangerous countries (which these days can mean almost any country).
Third, I believe that some Tor Project employees can put you in touch with people who can give you the best current county-specific advice on using Tor, so the best thing would be for you to contact them if that can be done safely. I thought Tor Messenger was very promising precisely to establish such critical initial contact with someone in a dangerous country, but unfortunately Tor Messenger's funding has been pulled and it never got out of beta testing.
Email is not safe but may be your only option.
Riseup.net is a wonderul collective offers email accounts to people other than Nazis and human traffickers and people of that sort
https://riseup.net/en/about-us/politics
but their mail servers
o are in the USA, which may have "intelligence sharing agreement" with your country (assuming it is not USA),
o have been targeted by Hacking Team
o have been seized at least once by FBI (which got nothing and failed to shut down Riseup on that occasion),
o have been targeted with at least one NSL which was initially secret, but Riseup says the information they got was limited to a few accounts only.
This is not encouraging, but nonetheless Riseup may be your best option.
Riseup.net asks users to donate but understands it may be difficult for people who live in dangerous country to safely donate money. Riseup offers a VPN but I don't know how dangerous this would be to try to use from inside your country. To obtain an email account (and access to the VPN), someone who knows you and already has an account needs to vouch for you (because Riseup needs to try to keep genuinely criminal activity off their network). Note that Riseup offers services in several major languages.
You can look here for other providers:
https://riseup.net/en/security/resources/radical-servers
An important and occasionally updated resource:
https://ssd.eff.org/en
Surveillance Self-Defense
Tips, Tools and How-tos for Safer Online Communications
A Project of the Electronic Frontier Foundation
This should help in teaching others:
https://sec.eff.org/
Security Education Companion
A free resource for digital security educators
(Available in several languages).
Riseup has some cybersecurity tutorials oriented towards journalist/activist needs:
https://riseup.net/en/security
https://riseup.net/en/security/resources
Micah Lee has written many posts which offer detailed advice, but some may not be out of date. You can try these:
https://freedom.press/news-advocacy/encryption-works-how-to-protect-you…
https://cpj.org/2015/04/attacks-on-the-press-surveillance-forces-journa…
Concerning pro-journalism orgs with resources (e.g. people, servers) in the USA, as you probably know
o USG has recently withdrawn from UNCHR:
https://en.wikipedia.org/wiki/United_Nations_Commission_on_Human_Rights
o USG has just declared that the ICC is "illegitimate" and that USG intends to neutralize anyone who supports ICC activities (with a strong hint that this project includes CIA kidnappings and secret renditions to places of evil repute):
https://en.wikipedia.org/wiki/International_Criminal_Court
We cannot let these developments dissuade us from fighting for human rights everywhere and however we can, but this does appear to imply that leading human rights organizations like Riseup, Tor Project, EFF, ACLU, HRW, Amnesty, RSF, CPJ are now in even greater danger of being declared illegal by USG or even prosecuted.
You mentioned the need for haste. In generally, doing things quickly is bad for cybersecurity but in many cases there is no other choice.
Good luck!
Suggestions not directly…
Suggestions not directly responsive to your question, but likely to be valuable nonetheless:
One basic strategy to consider, taking account of country-specific "norms" and what "The Authorities" might view as particularly suspicious, is using two or more devices for different roles.
For example, you might have a PC and printer in your home, but use a smart phone when covering street protests or meeting with sources. If so, when you are outside your home, you might use the new Tor for Android for urgent messages, to set up meetings, etc. (You might use a second smart phone in "monitor mode" for countersurveillance in the field, unless using two phones will look strange in your country.) When you are working at home, you might boot Tails from a DVD for further research on the internet, keeping files you download on an encrypted USB stick. To write your story, you might reboot Tails from a USB stick, with networking disabled but with your persistent storage enabled, for extra security while you prepare your document.
In general, it is best to try to keep anything you want to access in future on strongly encrypted removable media. The default is AES which is becoming worrisome because it so old, and critical features of AES are not yet well understood by the public cryptographic community.
Because different activities and different media engage different Threat Models, it is best to use a small number of different media devices for these different roles, ideally using different strong passphrases, ideally ones you have memorized. EFF's diceware offers a good way to construct long but memorable passphrases with known entropy. Unfortunately, with quantum computing now upon us (or nearly so), you need long passphrases.
Generating long random passphrases requires thought and preparation. Your options include:
o pseudo-random number generator in Tails booted from DVD (less likely that someone who subjects your computer to NSA-quality media recovery will be able to find the random seed you used but you should give the computer enough time to collect good entropy--- if you have trouble generating a long gpg key this is a warning that you probably cannot use this method),
o pseudo-random number generator in your persistent OS (probably better entropy),
o commercial entropy key (but tests suggest these do not produce good entropy, possibly because NSA likes it that way),
o off-line non-computer generation of entropy such as Diceware (but tests suggest cheap dice do not produce good entropy, possibly because NSA likes it that way).
Some people like to use all of these in an entropy smorgasbord.
You can find applications at CRAN and in Debian which generate Diceware passphrases from simulated dice throws. This is a convenient way to get a feel for what kinds of memorization training you will need.
To intelligently generate passphrases you need to start with a threat model such as this:
1 E12 trials per second: Snowden's estimate for NSA supercomputer brute forcing rate c. 2013
1 E4 quantum factor (possibly an underestimate)
3 E7 seconds per year
1 E2 years per century
----
3 E25 alternative passphrases needed
Diceware uses a wordlist with random choices made using pentathrows (five dice):
There are 6^5 = 7776 possible pentathrows, so we compute how many words we need like this:
7776^6 = 2 E23 (good enough for 2013?)
7776^7 = 2 E27 (good enough for 2018?)
But rattling five cubical dice in a box, as Micah Lee recommends, appears to result in like faces sticking together, which very drastically reduces the entropy. Because cheap playing dice are not likely to be adequate for our needs, some people use a computer which they never connect to another device, but use only to generate simulated pentathrows, regularly checking with tools like dieharder the quality of the entropy output by R's default pseudo-random number generator (Mersenne twister, which is much better than the generators which your OS probably uses).
The latest EFF passphrase construction scheme uses "fandom" wordlists (Tolkien loving Tor node operators take note!) with random choices made using trithrows of a dodecahedral die:
There are 20^3 = 8000 possible trithrows, but the wordlists have size 4000, so:
4000^7 = 2 E25 (good enough for 2016?)
Me too was very confused…
Me too was very confused when I required to some expert about the uses of TOR (By Mobile I am saying) added to a VPN.Well ,I have tried more VPN during its own free treal and more or less are all fine working added to Orbot and TBB , obviously data connection is very slow and here is the problem. More slow is a connection and more possibilities there are for MITM attack.So in my opinion especially if you are using socials like Facebook and Twitter ,it may be a good idea speaking to the teams of the Vpns before posting through vpn+orbot+tbb on a social network ,even if you means Facebook onion link and Twitter behind proxy.In both they requires your phone number or ,the code for login is directly sent on your isp messaging app.There are free chat about vpn teams with which you can ask anything from your browser, they are all gentlemen or ladies,I suggest you to chat with them behind a vpn ,not for them,but for your isp ,especially considering the fact that you are living in a Country very well under contoll; from what you have posted and I am understanding. Right? Best regards ☺
I cannot switch circuit with…
I cannot switch circuit with this new browser!!!!!
Where can I download the old one, and disable updating?
You can switch your circuit…
You can switch your circuit by clicking on the "i" icon (identity box) on the left site of the URL bar as the 8.0 release blog post, the onboarding in the upper left corner of your starting page and the update notice (in case you updated) on the first page after the update explain.
But why cant the gurd be…
But why cant the gurd be changed?
Now i use the same "guard" all the time
for some reason the add on…
for some reason the add on tab used be able to search the add on the in the serach field now it pop up new window and shows you the add on based on the serach in the firefox add on site now. used to be able to query the list in the tor browser what is happening?
This is a huge advance for…
This is a huge advance for billions of people all over the world, because so many ordinary citizens (and all are at risk from govt/corp surveillance) use either Google or Microsoft smart phones, and now they can protect their friends and family with Tor!
(Tsigas has worked as a tech expert for ProPublica, so even though his TorBrowser is not offically part of the Tor Project, I think its trustworthy.)
Thanks to all who are working on this, and best wishes for future development and adoption at scale. I hope TP's media team is reaching out to reporters at TheRegister, Wired, Arstechnica, The Guardian, The Intercept, to try to ensure that people all over the globe are aware that they can easily protect themselves by using Tor on two of the most widely used smart phones. I'd name media outlets in India, South Asia, Africa, and Latin America, but I'm not sure how many people use these brands of phone there, or which papers if any are courageous enough to popularize Tor usage. But I sense that at least in India and some parts of South America there are enormous opportunities to grow the Tor community and I hope this achievement can be part of how we do that.
Onion Browser, not Tor…
Onion Browser, not Tor Browser.
How will Tor deal with the…
How will Tor deal with the rooting vs non-rooting issue? This is something Orbot struggled with before you; do you plan on requiring root or not?
It's not planned yet to…
It's not planned yet to require that.
I hope you won't require…
I hope you won't require root to use tor for android, not everyone is fine with rooting their phone or tablet.
Please don't require root…
Please don't require root for tor.There are so many android phones and tablets that finding a root method, other than kingroot or kingoroot or something like those apps, is impossible for all of them. If Tor browser for Android will require root some people may not be able to use tor anymore. Everyone can get an Android phone/tablet not everyone can root them, I would say it's better to not require root access.
Tell me, is there a version…
Tell me, is there a version on the MacBook?
Yes, just use the stable Tor…
Yes, just use the stable Tor Browser 8 which we released last week, see: https://www.torproject.org/download/download-easy.html.en
I wait for the final version…
I wait for the final version of Tor Browser to use it without Orbot Proxy :)
Here an article in Spanish about it: https://www.ardilu.com/apps/tor-browser-android
Good is it now supports IPv6…
Good is it now supports IPv6 websites.
Please host APK on onion fdroid repo!
Written with tor-browser Android
Where is the tor circuit map…
Where is the tor circuit map which shows the network the browser is going through?
Behind the "i" icon on the…
Behind the "i" icon on the left side of your URL bar.
Sorry I cannot find the i…
Sorry I cannot find the i icon
Can't move to SD Card. Orfox…
Can't move to SD Card. Orfox can...
So when is it coming to IOS?
So when is it coming to IOS?
When I can use official Tor…
When I can use official Tor Browser on iOS?
Brilliant! Supporting your…
Brilliant! Supporting your efforts all the way. Thanks heaps!
It's good that you are…
It's good that you are releasing a TBB for Android, however I don't think you have fully explained the reasons for it. What exactly was the motivation for it vs simply improving Orfox, and why will Orfox be discarded when TBB for Android comes out? I thought Orfox was made from the same basic code as Firefox for Android and TBB for Linux.
The reasons were that the…
The reasons were that the Guardian Project did not have the resources to maintain Orfox anymore (they did a great job, though!) and we thought providing an application (Tor Browser) not just for desktop platforms but for Android as well with a unified style, branding, functionality etc. would be a huge win both for us and our users.
what's this fucking "guard"…
what's this fucking "guard" that never changes ?? you have been hacked "tor project" or what ??
Keeping the same guard can…
Keeping the same guard can actually help protect you from common deanonymization attacks. The reason is not obvious but has been explained in previous comments from time to time.
Your question is a FAQ and it is unfortunate that Tor Project documentation is so chaotic that the answer is hard to find. So hard that I could not find it myself when I tried just now. Sigh.
Go read there docs on how…
Go read there docs on how entry guards work. Its supposed to be the same for a while.
Guard nodes are trusted…
Guard nodes are trusted nodes that are used as your entry point for the tor network, they rarely change to lower the chances of getting a compromised route.
please add support for…
please add support for chrome os, thanks.
Tor browser seems a good fit…
Tor browser seems a good fit for the upcoming privacy & security focused phone Librem 5. Have you any plans to cooperate with them (puri.sm)?
No, there are no plans yet.
No, there are no plans yet.
Loving the new mobile…
Loving the new mobile browser, already noticing a huge performance increase over orfox. Curious on your plans for replacing orbot, I'd still like to see tor ran as a backgorund app as it's useful for other apps built to support orbot like courier.
so what happened to: https:/…
so what happened to: https://blog.torproject.org/mission-improbable-hardening-android-securi…
what does this release add to the issues above? back to square 1?
please optimize it for x86…
please optimize it for x86 devices.i cant open it because of it
It's on our ToDo list but…
It's on our ToDo list but might not be ready for the next alpha(s).
Thank you for this upcoming…
Thank you for this upcoming Tor release for Android. I am currently experiencing major attack events on my device. I am using Orbot and Orfox. This is what they do:
1) Orfox 'Settings' are greyed out with elements of the pullfown lidt misding (Orfox Settings entry for example).
2) A node with the IP 81.4.0.60, with a declared origin as South Africa but actually in Britain, shows up often on the phone. Online tracing tools which helped expose it, also claim it to have been responsible for many brutal attacks.
3) A list of nodes registered to 185.220.x.x appear to be static and slways resident. When I 'exclude' this bloc of nodes, Orbot aborts.
Is this an attack on Tor? I am not a terrorist but tortured illegally and most severely with advanced remote electromagnetic weapons systems. I have written much to expose the crimes. This could also be an attempt to hide the exposures but I am more concerned about how they are trying to break Tor in order to scvomplish that.
> A node with the IP 81.4.0…
> A node with the IP 81.4.0.60, with a declared origin as South Africa but actually in Britain, shows up often on the phone.
That is not your Guard node, is it? The Guard node is supposed to show up at the start (only) of most circuits your Tor Browser creates.
You can look at the invaluable site torstatus.blutmagie.de to gather statistics on current Tor nodes. I have found it is not unusual for the legal country address of the domain to differ from the actual location, if that's what you are talking about. E.g. a node operator might live in Germany but run a Tor node on a remote server which is physically in the USA.
> Online tracing tools which helped expose it, also claim it to have been responsible for many brutal attacks.
Was the information you found dated? If it was months or years old, it probably has nothing to do with the behavior of the computer currently using the IP you cited.
There is supposedly some way to report a possibly misbehaving Tor node, but I can't find any information in Tor Project documentation pages.
> I am more concerned about how they are trying to break Tor
This should be of interest to Tor users who remember the Carnegie-Mellon scandal:
aclu.org
Government Hacking Makes Everyone Less Safe
Danny Yadron, Legal Intern, ACLU
Jennifer Stisa Granick, Surveillance and Cybersecurity Counsel, ACLU
13 Sep 2018
On Android Kit Kat 4.4.2 Tor…
On Android Kit Kat 4.4.2 Tor Browser continue where I left.
All tabs are open.
Settings are to close all tabs after quitting Tor Browser but it doesent close.
Sorry for my bad English
In my opinion more than TBB…
In my opinion more than TBB that it's giving you issue on Kitkat ,it could be Orbot.Try to get the suggest version of Orbot for Kitkat on Fdroid for example is well laleable and descripted. I had a lot of issue using Kitkat device on Tor.Don't know why .No so expert. I HOPE YOU CAN SOLVES SOON.
i think i found a bug with…
i think i found a bug with this release. if you try to download any file that has apk extention it doesnt work even if security tab is set to standard. why?
edit: after investigating,…
edit: after investigating, this torbrowser fails to download any file fully not just apk. so to reproduce this try to download any file and it wont show anything in downloads tab, however you could see tor traffic on orbot. when the file is downloaded in the background you could check your download folder to find the file named foo.pdf.part
this applies to any file.
Thanks, I opened https:/…
Thanks, I opened https://trac.torproject.org/projects/tor/ticket/27701 to investigate this further.
hi. I know this is unrelated…
hi. I know this is unrelated but can you copy/mark text from a webpage opened with this browser?
looks like this doesn't work properly or that Im doing something wrong.
one more thing, i am failing…
one more thing, i am failing to copy any text using this browser
im loving this release…
im loving this release already, you guys have done so well in the past to keep the tor browser stable i sincerely appreciate all of what you guys have done. i would like to see the mobile version be sd card compatible that's the only real issue ive seen so far but rather than that im pretty impressed the release of this has came as early as it did. excellent work people!
Hello, I've been using Tor…
Hello,
I've been using Tor Browser for Android Alpha for over a week now and it's working great! So far my only complaint is that I can't download any sort of media with TBA (i.e. Images, Files, etc), where as I'm able to using Orfox. When is the next expected alpha update?
Thanks for your hard work!
What month is the stable…
What month is the stable release?
have you tried to find out…
have you tried to find out why selecting or copying text from pages opened with this browser doesnt work properly?
I tried it and it was…
I tried it and it was brilliant all except I couldn't change my UA at all. I go to general.useragent.override and change it but it doesn't stick. A quick check shows my UA. Which I don't like. Otherwise you can set everything up as if you're on a PC.
as other commentators…
as other commentators pointed out the 'i' button doesnt appear to me either, just the lock and that doesnt show 'new id'
is there a ticket for this?
Yes, there is no circuit…
Yes, there is no circuit display yet on Tor Browser for Android and we are working on it. It's part of our feature parity plan to Tor Browser for desktop. We might have it available in the next alpha but if not then in the one after it.
how to get new identity?…
how to get new identity? just close the browser?
I think that you can set up…
I think that you can set up or changes your identity on Orbot ,clicking on setting and change it .On refresh icon very easy. Have a nice day.
Tor Browser for Android is…
Tor Browser for Android is great. But I notice that I can't download images and I can't add other search engine apart from the ones provided by Tor Browser. I can't hold down on search box and add default search engine of my own choice.
If you can fix that it would be great as I love DuckDuckGo Onion and Searx Onion search engine
Me too,I can't share a file…
Me too,I can't share a file once hold on it because nothing it happens. But as far as concerns adding new search engine it seems that in the last one realise at the least on my device is working. I had first TBB for android from the tor project site trough Google Chrome and the updates app trough F Droid .By the way has been not necessary to change key ,sign was the same ,fortunately. Try it out now from Fdroid or where you prefere last one version. Goodluck.☺☺☺.
The app in now available on…
The app in now available on Fdroid ☺.That's very nice news. THANKS A LOT.
I'm visiting family and…
I'm visiting family and logging into their wifi with a small tablet. Can they see what I browse and other activities such as email? I was given their password to login. Will Tor or Onion help with preventing their seeing my activity?
I used xiomi redmi note 4…
I used xiomi redmi note 4 android phone.I can't use "tor browser for android" app for downloading anything.There shows bugs.I don't understand what is the problem.When I clicked to download anything then tor browser stopped and shows bug....
Plz help me
You are probably hitting…
You are probably hitting https://trac.torproject.org/projects/tor/ticket/28705. We'll have that fixed in the upcoming release, Tor Browser for Android 8.5a7 which will get out in less than two weeks.
How long we've to wait more…
How long we've to wait more to get the final release of Tor Browser for Android?
Probably about 2 and a half…
Probably about 2 and a half months. The current plan is to release Tor Browser 8.5 at the end of March (including the mobile version).