New Release: Tor Browser 10.0.3 (Android Only)

After many months of design and development we are very happy to announce the release of Tor Browser 10.0.3 for Android. This is the first Android Tor Browser version in the stable 10.0 series. The Desktop version was released at the end of September. We began working on this project in April 2020 with the goal of rebuilding the Android Tor Browser on top of Mozilla's new Android Firefox Browser, Fenix. Over the last six months, we successfully achieved this goal and we reached feature parity with the previous Android Tor Browser version.
This version is now available from the Tor Browser download page and also from our distribution directory.
Tor Browser 10.0.3 is based on Fenix 82.1.1, and upgrades Go to 1.14.10, NoScript to 1.1.4, OpenSSL to 1.1.1h, and Tor to 0.4.4.5. This release includes important security updates to Firefox.
Having achieved feature-parity with the previous Tor Browser for Android, we will continue working on closing the gap with Tor Browser for Desktop. That includes implementing the "Circuit Display" and "New Identity" features, as well as supporting the Onion-Location header and short ".tor.onion" URLs, among others. Stay tuned!
Over the last four months we adjusted our toolchains, finished our proxy audits, re-implemented the user interfaces, solved numerous build reproducibility bugs, and fixed a lot of issues we encountered due to the switch from Firefox 68esr to Fenix.
Give Feedback
If you find a bug or have a suggestion for how we could improve this release, please let us know. Thanks to all of the teams across Tor, and the many volunteers, who contributed to this release.
Full Changelog
The full changelog since Tor Browser 9.5.4 is:
- Android
- Update Fenix to 82.1.1
- Update NoScript to 11.1.4
- Update OpenSSL to 1.1.1h
- Update Tor to 0.4.4.5
- Bug 10394: Let Tor Browser update HTTPS Everywhere
- Bug 11154: Disable TLS 1.0 (and 1.1) by default
- Bug 16931: Sanitize the add-on blocklist update URL
- Bug 17374: Disable 1024-DH Encryption by default
- Bug 21601: Remove unused media.webaudio.enabled pref
- Bug 30682: Disable Intermediate CA Preloading
- Bug 30812: Exempt about: pages from Resist Fingerprinting
- Bug 32886: Separate treatment of @media interaction features for desktop and android
- Bug 33534: Review FF release notes from FF69 to latest (FF78)
- Bug 33594: Disable telemetry collection (Glean)
- Bug 33851: Patch out Parental Controls detection and logging
- Bug 33856: Set browser.privatebrowsing.forceMediaMemoryCache to True
- Bug 33862: Fix usages of createTransport API
- Bug 33962: Uplift patch for bug 5741 (dns leak protection)
- Bug 34125: API change in protocolProxyService.registerChannelFilter
- Bug 34338: Disable the crash reporter
- Bug 34377: Port padlock states for .onion services
- Bug 34378: Port external helper app prompting
- Bug 34401: Re-design Connect screen on Android
- Bug 34402: Re-design Network Settings Screen on Android
- Bug 34403: UI changes for "Only Private Browsing Mode" on Android
- Bug 34405: Re-design about:tor on Android
- Bug 34406: Re-design onion indicators for Android
- Bug 34407: Review all Fenix menu items
- Bug 30605: Honor privacy.spoof_english
- Bug 40001: Start Tor as part of the Fenix initialization
- Bug 40001: Generate tor-browser-brand.ftl when importing translations
- Bug 40002: Ensure system download manager is not used
- Bug 40002: Fix generateNSGetFactory being moved to ComponentUtils
- Bug 40003: Adapt code for L10nRegistry API changes
- Bug 40003: Block starting Tor when setup is not complete
- Bug 40004: "Tor Browser" string is used instead of "Alpha"/"Nightly" for non en-US locales
- Bug 40004: Fix noscript message passing for Firefox 79
- Bug 40005: Modify WebExtensions Menu
- Bug 40006: "Only Private Browsing Mode" on Android
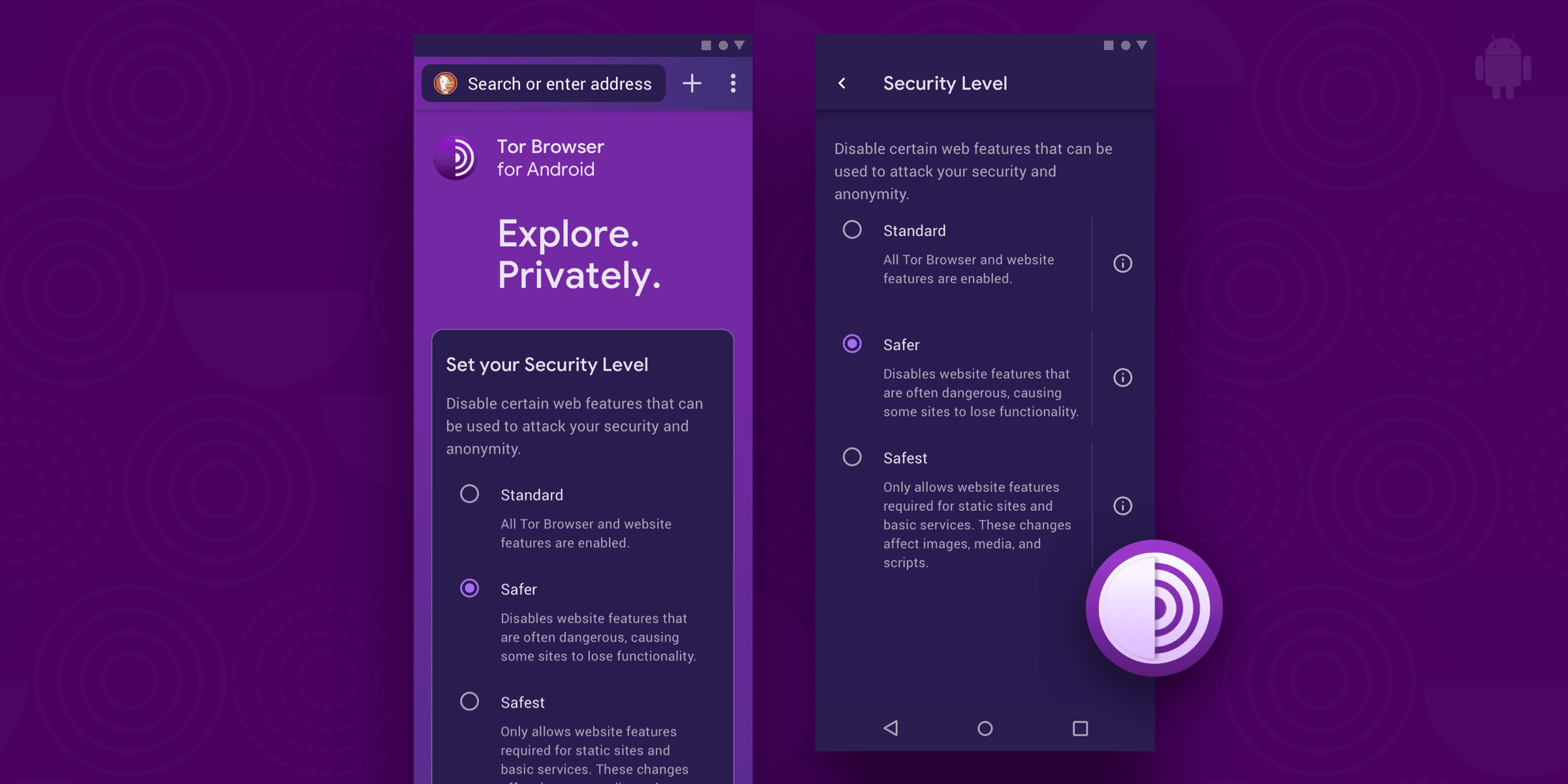
- Bug 40006: Add Security Level plumbing
- Bug 40007: Port external helper app prompting
- Bug 40007: Move SecurityPrefs initialization to the StartupObserver component
- Bug 40008: Style fixes for 78
- Bug 40009: Change the default search engines
- Bug 40010: Verify Sentry is disabled
- Bug 40011: Verify Leanplum is disabled
- Bug 40011: Hide option for disallowing addons in private mode
- Bug 40012: Verify Adjust is disabled
- Bug 40013: Timestamp is embedded in extension manifest files
- Bug 40013: Verify InstallReferrer is disabled
- Bug 40014: Verify Google Ads ID is disabled
- Bug 40014: Set correct default Security Level
- Bug 40015: Modify Fenix Home Menu
- Bug 40016: Modify Fenix Settings Menu
- Bug 40016: Allow inheriting from AddonCollectionProvider
- Bug 40017: Rebase android-components patches to 60
- Bug 40017: Audit Firefox 68-78 diff for proxy issues
- Bug 40018: Disable Push functionality
- Bug 40019: Ensure missing Adjust token does not throw an exception
- Bug 40019: Expose spoofEnglish pref
- Bug 40020: Disable third-party cookies
- Bug 40021: Force telemetry=false in Fennec settings migration
- Bug 40022: Migrate tor security settings
- Bug 40023: Stop Private Notification Service
- Bug 40023: Rebase Tor Browser esr78 patches onto 80 beta
- Bug 40024: Disable tracking protection by default
- Bug 40026: Implement Security Level settings
- Bug 40028: Implement bootstrapping and about:tor
- Bug 40029: Rebase Fenix patches to 81.1.0b1
- Bug 40030: Install https-everywhere and noscript addons
- Bug 40031: Hide Mozilla-specific items on About page
- Bug 40032: Disallow Cleartext Traffic
- Bug 40034: Disable PWA
- Bug 40035: Maybe hide Quick Start in release
- Bug 40038: Review RemoteSettings for ESR 78
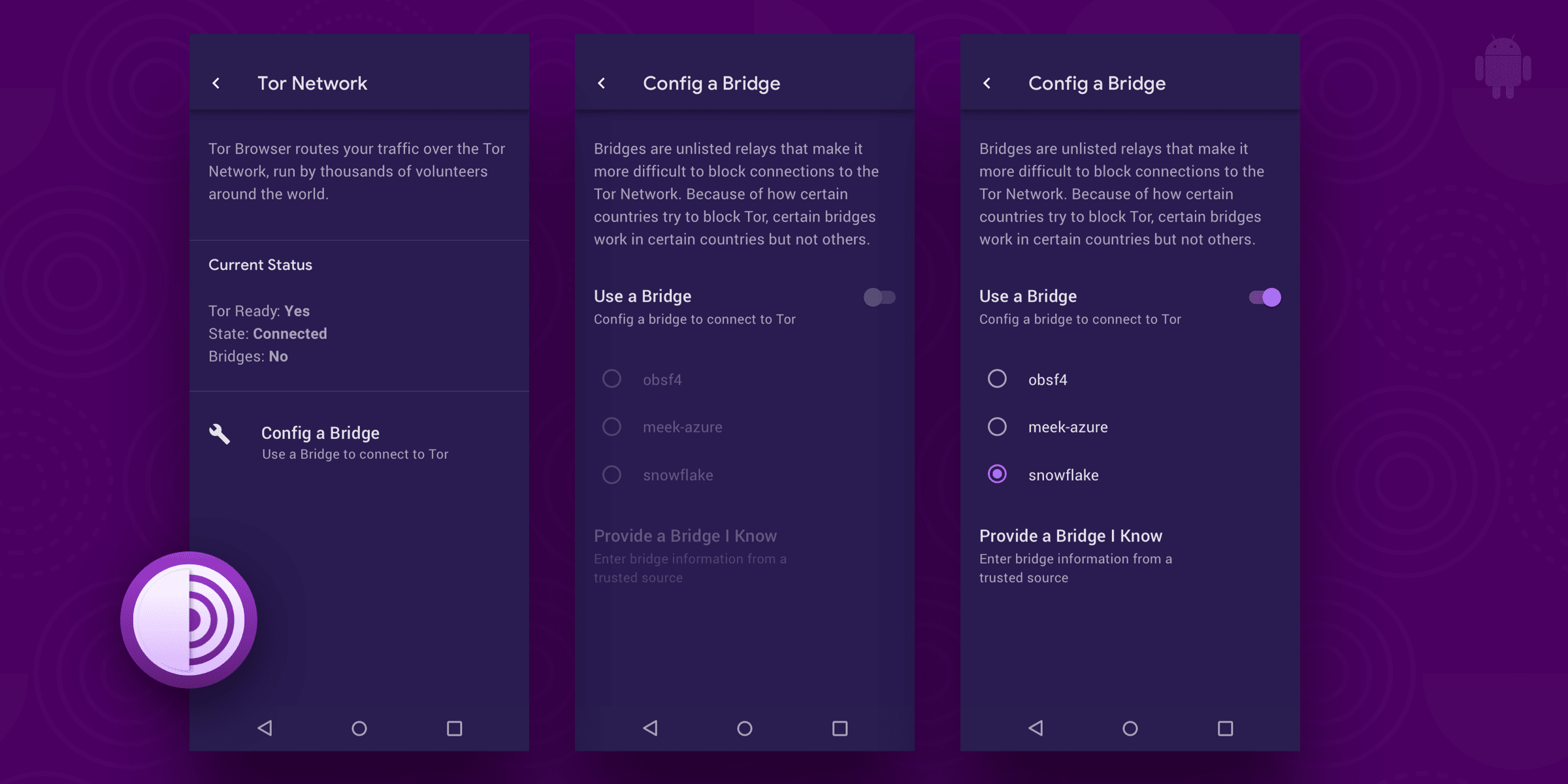
- Bug 40039: Implement Bridge configuration from Connect screen
- Bug 40040: Investigate why bootstrapping fails
- Bug 40041: Implement Network settings
- Bug 40042: Timestamp is embedded in extension manifest files
- Bug 40044: Fixup Connect, Onboarding, and Home screens
- Bug 40048: Disable various ESR78 features via prefs
- Bug 40050: Rebase Fenix patches to Fenix 82
- Bug 40053: Select your security settings panel on start page is confusing
- Bug 40054: Search engines on mobile Tor Browser don't match the desktop ones
- Bug 40058: Disabling/Enabling addon still shows option to disallow in private mode
- Bug 40058: Hide option for disallowing addon in private mode
- Bug 40061: Do not show "Send to device" in sharing menu
- Bug 40062: HTTPS Everywhere is not shown as installed
- Bug 40063: Do not sort search engines alphabetically
- Bug 40064: Modify Nighty (and Debug) build variants
- Bug 40066: Remove default bridge 37.218.240.34
- Bug 40066: Update existing prefs for ESR 78
- Bug 40067: Make date on Fenix about page reproducible
- Bug 40068: Tor Service closes when changing theme
- Bug 40069: Add helpers for message passing with extensions
- Bug 40071: Show only supported locales
- Bug 40072: Bug 40072: Disable Tracking Protection
- Bug 40073: Use correct branding on About page
- Bug 40073: Repack omni.ja to include builtin HTTPS Everywhere
- Bug 40073: Disable remote Public Suffix List fetching
- Bug 40076: "Explore privately" not visible
- Bug 40078: Crash at Android startup from background service
- Bug 40082: Security level is reset when the app is killed
- Bug 40082: Let JavaScript on safest setting handled by NoScript again
- Bug 40083: Locale ordering in BuildConfig is non-deterministic
- Bug 40087: Implement a switch for english locale spoofing
- Bug 40088: Use Tor Browser logo in migration screen
- Bug 40091: Load HTTPS Everywhere as a builtin addon
- Bug 40093: Enable Quit menu button
- Bug 40094: Do not use MasterPasswordTipProvider in HomeFragment
- Bug 40095: Hide "Sign in to sync" in bookmarks
- Bug 40095: Review Mozilla developer notes for 79-81 (including)
- Bug 40096: Review closed Mozilla bugs between 79-81 (inclusive) for GeckoView
- Bug 40097: Rebase browser patches to 81.0b1
- Bug 40097: Bump allowed_addons.json
- Bug 40098: Implement EOY home screen
- Bug 40100: Resolve startup crashes in debug build
- Bug 40112: Check that caching stylesheets per document group adheres to FPI
- Bug 40119: Update Fenix dependencies for 81.1.2
- Bug 40125: Geckoview: Expose security level interface
- Bug 40133: Rebase tor-browser patches to 82.0b1
- Bug 40166: Disable security.certerrors.mitm.auto_enable_enterprise_roots
- Bug 40172: Security UI not updated for non-https .onion pages in Fenix
- Bug 40173: Initialize security_slider in GeckoView at 4
- Bug 40198: Expose privacy.spoof_english pref
- Bug 40199: Avoid using system locale for intl.accept_languages
- Translations update
- Build System
- Android
- Update Go to 1.14.10
- Bug 33556: Add TBB project for android-components
- Bug 33557: Update Android toolchain for Fenix
- Bug 33558: Update tor-onion-proxy-library to use toolchain for Fenix
- Bug 33559: Update tor-android-service to use toolchain for Fenix
- Bug 33561: Update OpenSSL to use Android NDK 20
- Bug 33563: Update Tor to use Android NDK 20
- Bug 33564: Update ZSTD to use Android NDK 20
- Bug 33626: Add project for GeckoView
- Bug 33670: Update rbm.conf to match NDK 20
- Bug 33801: Update Go project to use new Android toolchain
- Bug 33833: Update Rust project to use Android NDK 20
- Bug 33927: Add tor-browser-build project for fenix
- Bug 33935: Fenix's classes5.dex files are not reproducible
- Bug 33973: Create fat .aar for GeckoView
- Bug 34011: Bump clang to 9.0.1
- Bug 34012: Bump cbindgen to 0.14.3
- Bug 34013: Bump Node to 10.21.0
- Bug 34014: Enable sqlite3 support in Python
- Bug 34101: Add tor-browser-build project for application-services
- Bug 34163: testbuild target is broken for Tor Browser 64 bit
- Bug 34187: Update zlib to use Android NDK 20
- Bug 34360: Bump binutils version to 2.35.1
- Bug 40010: Add nss project for application-services
- Bug 40011: Add sqlcipher for application-services
- Bug 40029: Clean-up all projects to remove fennec bits we don't need for fenix
- Bug 40031: Add licenses for kcp-go and smux.
- Bug 40039: Remove version_path in nss project
- Bug 40040: Wire geckoview, application-services, android-components, and fenix together
- Bug 40054: Adapt build.android script in tor-browser project for fenix
- Bug 40055: Integrate building Glean in offline mode
- Bug 40057: Include translations into build process in the fenix world
- Bug 40058: Build Fenix with tor-android-service and tor-onion-proxy-library
- Bug 40060: Set Fenix Version Name in build
- Bug 40061: Remove Android SDK 28
- Bug 40065: Bump debootstrap-image ubuntu_version to 20.04.1
- Bug 40068: Bump versions for Fenix 81.1.0b1 dependencies
- Bug 40072: Tor libraries are missing in final .apk after switch to 81.1.0b1
- Bug 40076: Use our android-components repo on GitLab
- Bug 40078: Bump Gradle version for Fenix to 6.5.1
- Bug 40084: Generation of AndroidManifest.xml is not reproducible
- Bug 40085+40086: classes.dex files are not reproducible in Fenix
- Bug 40087: Deterministically add HTTPS Everywhere into omni.ja
- Bug 40088+40117: Use MOZ_BUILD_DATE for extension manifest timestamps
- Bug 40093: Ensure application-services libs do not include libc networking symbols
- Bug 40094: Aarch64 fenix rust cross-compilation fails
- Bug 40095: The pattern for the apk variable in build.android is matching too much
- Bug 40097: Update toolchain for Fenix 82
- Bug 40101: Pick up Fenix 81.1.1
- Bug 40105: Enhance Gradle dependency script (sort deterministically and exclude .module files)
- Bug 40106: Support using geckoview as well
- Bug 40108: android-components does not bundle tooling-glean-gradle archive, only .pom file
- Bug 40113: Nightly Android should use Nightly branding
- Bug 40115: Update components for switch to mozilla82-based Fenix
- Bug 40121: Use updated glean_parser for application-services as well
- Bug 40124: Remove unused torbrowser-android-all (and related) targets
- Bug 40125: Remove fenix-* projects
- Bug 40129: application-services is missing rustc in PATH
- Bug 40130: More mobile clean-up
- Android
Comments
Please note that the comment area below has been archived.
The new UI is a mess. We…
The new UI is a mess.
We dont have the choice to enable dekstop site before entering to a site.
Yes UI has gone backwards…
Yes UI has gone backwards/broken.. Home page has gone and won't save passwords. Why not allow option of bookmarks for the homepage?
This is a decision Mozilla…
This is a decision Mozilla made.
Fantastic. Thanks for this…
Fantastic. Thanks for this. Is Tor Project going to make its F-Droid repo available any time soon? Unfortunately, Guardian Project's one is usually very slow in making new Tor Browser release available.
about:config is not working…
about:config is not working...it is vital for us to fine-tune the app.
Yes, and however Tor Browser…
Yes, and however Tor Browser is based on Mozilla Firefox for Android, and that app is opinionated and doesn't allow as much customization. Tor Browser generally does not have different opinions, and access to about:config will remain restricted because "fine-tuning" is harmful to privacy.
"fine-tuning" helped users…
"fine-tuning" helped users immediately patch significant bugs such as Mozilla's expired certificate disabling NoScript, javascript executing on the Safest security level, and YouTube not playing Opus audio until a new version of Tor Browser was released that officially patched it. Removing access puts more work and responsibility on you to release official updates much faster.
https://support.torproject…
https://support.torproject.org/tormobile/tormobile-7/
It is already available on…
It is already available on Guardian Project's repo
You forgot to mention that…
You forgot to mention that now it has a rapid release cycle ;)
Can we use Snowflake now?
Can we use Snowflake now?
No, not yet.
No, not yet.
Snowflake isn't available in…
Snowflake isn't available in the bridge selection menu, but it was available in Alpha. And there's an option to open a new tab in Tor browser from the launcher: https://filebin.net/y0038q9v46djw154. Also, file uploads don't work, and changing the theme crashes the app
how do you change your…
how do you change your identity if there is no specific functionality?
That was not available in…
That was not available in the old app. It is still a missing feature.
https://gitlab.torproject.org/tpo/applications/tor-browser/-/issues/288…
Correct me if I'm wrong, but…
Correct me if I'm wrong, but it's always possible to change the identity by closing the Tor Browser app. On desktop too, you can close all windows of Tor Browser to forget the session and reset the identity instead of using the button for New Identity.
Are you sure you shipped Tor…
Are you sure you shipped Tor 0.4.4 and not 0.4.1.x? Fresh install shows Tor 0.4.1.x on the bootstrap logs...
Yes. https://gitlab…
Yes. https://gitlab.torproject.org/tpo/applications/tor-android-service/-/is…
You say you shipped Tor 0.4…
You say you shipped Tor 0.4.4.5. On a fresh Android bootstrap logs it says it's Tor 0.4.1.5-rc
Why
Please explain the new additional permissions requirements.
Lost all my bookmark when…
Lost all my bookmark when updating from the older version, again!
Need some way to backup bookmarks on Tor Browser; maybe implement simple export/import?
I can't download anything…
I can't download anything from any websites since updated to the new version of TorBrowser. I have tried many times. Even cannot download from torproject.org
Thank you so much!
Thank you so much!
Snowflake isn't available in…
Snowflake isn't available in the bridge selection menu, but it was in Alpha. And there's an option to open a new tab in Tor browser from any home launcher:
https://filebin.net/1un3wtawb7xvocl0/new_tab.png?t=1ketzuz6
Also, file uploads don't work.
The new version of Tor…
The new version of Tor Browser for Android is very doubtful:
1) access to the hidden about:config menu is closed.
2) access for deep editing of the torrc settings file is closed
3) the browser has a lot of dangerous permissions.
4) the list of downloads is saved and not cleared.
5) the cache storage is not completely cleared from the browser menu.
This harms anonymity. It's dangerous to use it.
Can you expand on (5)? …
Can you expand on (5)?
Access to about:config is harmful to anonymity, and the others are not different from the previous version.
Hello I am not the one who…
Hello I am not the one who wrote the comment, but your response raised my eyebrow.
"Access to about:config is harmful to anonymity"
This is correct, it IS harmful... and? True or not we should be allowed to modify the app at our own will accepting the risks.
It is our decision to use whether there is a need or not, even if the app where to be pitch perfect, we still should be allowed to modify it.
Yes, and you are free to…
Yes, and you are free to build the app yourself and modify it however you want.
https://gitweb.torproject.org/builders/tor-browser-build.git/tree/README
Please join us on IRC if you would like some help.
So we can't access about…
So we can't access about:config because we might enter a configuration which makes us easier to track but we can run a custom configuration which might not be getting used by anyone else in the network? A lot of the app seems like it was done with only half the effort and most answers given here don't solve anything and actually just provides more questions
Tor Browser is free software…
Tor Browser is free software, and you may modify it however you want, but the Tor Project isn't required to provide access to about:config for similar reasons that Mozilla decided not to provide access by default.
In fact, contrary to your comment that "A lot of the app seems like it was done with only half the effort", this app was created with great care. You can see our process on the following ticket and its child tickets:
https://gitlab.torproject.org/tpo/applications/tor-browser/-/issues/336…
Please don't assume the worst.
Are font size and display…
Are font size and display size in the Android 9 settings supposed to affect websites?
So I like the look of this…
So I like the look of this version (Its a massive improvment) and I'm wondering if there will be an explanation to installing extensions, like "Is it the same as firefox?" "does it harm the overall performance of tor?".
Also the search engines, whats up with duckduckgoONION? Those this mean we can go to every onion site we desire?, and whats up with youtube as an search engine option? I had no idea it was even a thing.
(If this question were answered, please inform me)
PS: if broken english is present notify me.
The extensions are the same…
The extensions are the same as Firefox. The DuckDuckGoOnion is the same website as duckduckgo.com but it is an onion address (.onion). You should not see very different results, but your connection with DuckDuckGo is more secure.
Thanks, I thought it was…
Thanks, I thought it was something that was integrated to firefox as a prank, something totally unecessary or some stupid thing like a youtube search engine (tried out, I cannot find any purpose or use for it)
PS: I'm feeling relieved that is an optional search engine that puts an extra layer to this onion.
> whats up with…
> whats up with duckduckgoONION?
https://web.archive.org/web/20150420124527/https://duck.co/blog/friends…
https://twitter.com/DuckDuckGo/status/351417664083734528
DuckDuckGo searches only the "clearnet", the normal World Wide Web. It does not give you onion websites as results. There are other search engines that are accessible only inside the Tor network that give you *only* onion websites as results.
> whats up with youtube as an search engine option? I had no idea it was even a thing.
https://support.mozilla.org/en-US/kb/add-or-remove-search-engine-firefox
https://mycroftproject.com/
https://superuser.com/questions/7327/how-to-add-a-custom-search-engine-…
hello developers, when will…
hello developers,
when will you allow users to choose select country codes as exit/entry/strict nodes? this is missing ever since we bid farewell to Orbot. also i have a valid reason here. facebook wont allow users to post any media if they are coming from a different country node.
on desktop we can select countries but here we cant. facebook onion too blocks any upload of media be it just a simple image. will give an error.
i really beg you to allow users to choose countries nodes like we can on desktop.
thank you and stay
Selecting exit/entry nodes…
Selecting exit/entry nodes is harmful for anonymity and will probably never be implemented.
Image uploading such as…
Image uploading such as google images doesnt work
Is there a plan to get rid…
Is there a plan to get rid of new permissions that are now required when installing the Tor Browser?
I opened https://gitlab…
I opened an issue for tracking this: https://gitlab.torproject.org/tpo/applications/fenix/-/issues/40109
It's not bad but the chance…
It's not bad but the chance of checking the onion circuit like on desktop still misses. I hope we can get this feature in the next release.