New Release: OnionShare 2

The original version of this post can be found on Micah Lee's blog.
OnionShare is an open source tool for securely and anonymously sending and receiving files using Tor onion services. It works by starting a web server directly on your computer and making it accessible as an unguessable Tor web address that others can load in Tor Browser to download files from you, or upload files to you. It doesn't require setting up a separate server, using a third party file-sharing service, or even logging into an account.
Unlike services like email, Google Drive, DropBox, WeTransfer, or nearly any other way people typically send files to each other, when you use OnionShare you don't give any companies access to the files that you're sharing. So long as you share the unguessable web address in a secure way (like pasting it in an encrypted messaging app), no one but you and the person you're sharing with can access your files.
I first saw the need for this tool when I learned about how David Miranda, the partner of my colleague Glenn Greenwald, got detained for nine hours at a London airport while he was trying to fly home to Brazil. Working on a journalism assignment for the Guardian, Miranda was carrying a USB stick with sensitive documents. I knew that he could have securely sent the documents over the internet using a Tor onion service, one of the most underappreciated technologies on the internet, and avoided the risk of physically traveling with them. I developed OnionShare to make this file sharing process over the Tor network more accessible to everyone.
After nearly a year of work from a growing community of developers, designers, and translators, I'm excited that OnionShare 2 is finally ready. You can download it from onionshare.org.
Here's a tour of some of the new parts of OnionShare 2.
- Sharing files with OnionShare
- The macOS sandbox
- Next generation onion services
- OnionShare doesn't zip if you share just one file
- OnionShare addresses are ephemeral by default
- Receiving files with OnionShare
- Only open things from people you trust, or if you know what you are doing
- Public OnionShare addresses
- Running an anonymous dropbox
- OnionShare in your language
Sharing files with OnionShare
Here's what OnionShare 2 looks like. When you first open it, it connects to the Tor network.
Once you're connected, you're in the "Share Files" tab (I'll talk more about the new "Receive Files" tab below).

To securely and anonymously share files with someone, just drag and drop the files into the OnionShare window. Alternatively, you can click the "Add Files" and "Add Folder" buttons to browse your filesystem.
The macOS sandbox
In Windows and Linux there's just a single "Add" button that lets you select both files and folders. The reason for two separate buttons in the macOS version is a bit complicated, but boils down to a cool new security feature: The macOS sandbox is turned on in OnionShare 2, which means that even if someone manages to exploit a vulnerability in OnionShare to try to hack your computer, they still won't be able to access your data or run programs on your computer without first escaping the sandbox.
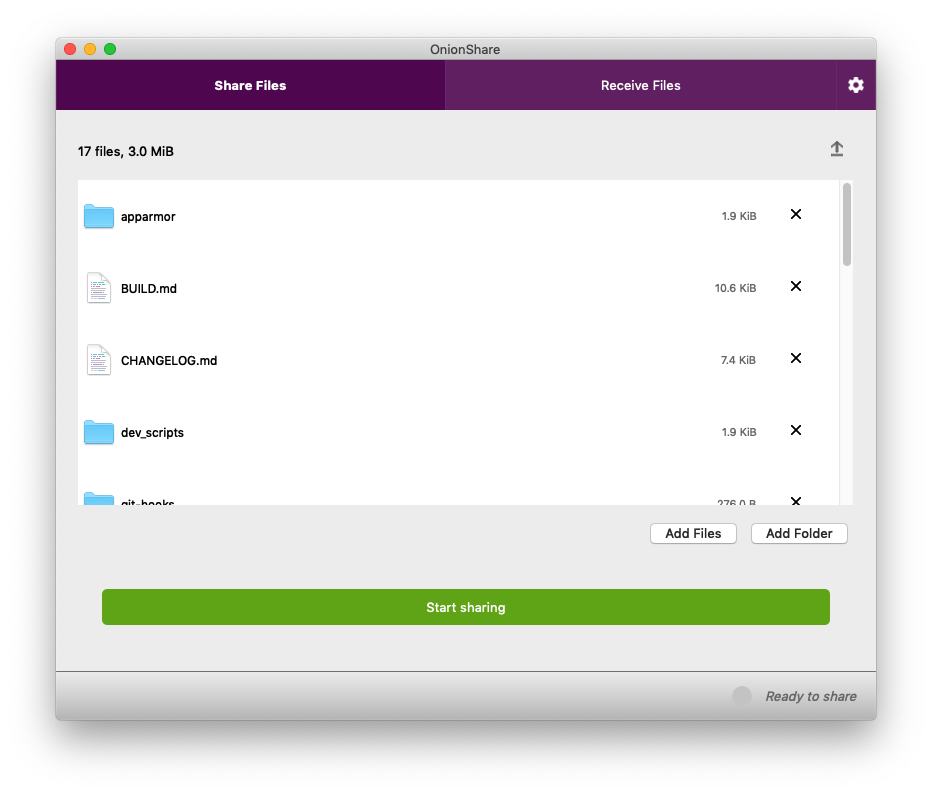
I've dragged all of the files that make up the OnionShare source code into the window. Now, to make them accessible to someone else, I just click "Start sharing".
Next generation onion services
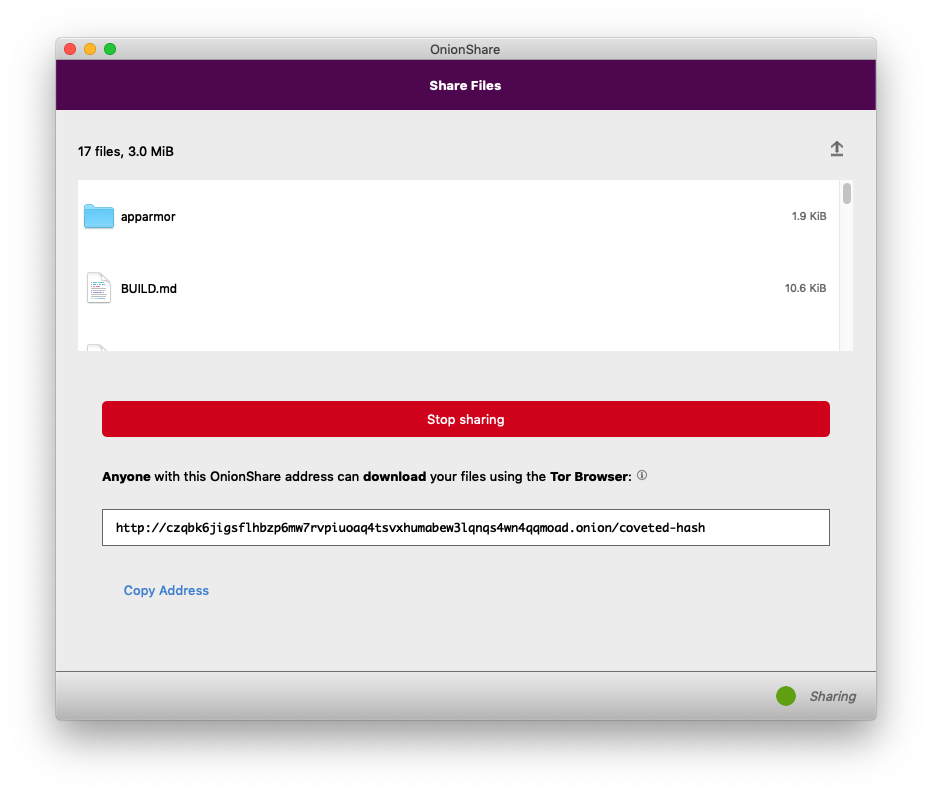
After clicking the button, I wait a few seconds, and then OnionShare gives me an unguessable Tor address to share. This is also new in OnionShare 2: By default, it uses next generation Tor onion services, also known as v3 onion addresses. These are onion addresses that look like lldan5gahapx5k7iafb3s4ikijc4ni7gx5iywdflkba5y2ezyg6sjgyd.onion, as opposed to the old v2 kind, that look like elx57ue5uyfplgva.onion.
v3 onions are much more secure than v2 onions for a variety of reasons, but they can be a bit unwieldy and hard to type (for example, if you're using OnionShare to move files between two computers that are both in front of you). You can still use v2 onion addresses if you want by going into Settings and choosing "Use legacy addresses".
Also, you might notice that the OnionShare address is using HTTP and not HTTPS, but this is actually perfectly fine. HTTPS adds a layer of encryption between a web browser and a web server, but Tor onion services are already end-to-end encrypted, so HTTPS is not necessary (it's also not feasible without browser warnings: Let's Encrypt doesn't sign HTTPS certificates for .onion sites). Unlike loading normal websites in Tor Browser, when you load onion websites, there is no Tor exit node that could spy on the traffic -- all of the traffic stays within the Tor network.
Now, I need to send this web address to my friend who I'm sharing files with. The easiest way to do this securely is to use an encrypted messaging app like Signal Desktop, Wire, Keybase, or iMessage -- or, if you're oldschool, Jabber/OTR. If the files you're sharing aren't especially sensitive, you can also share this web address in a way that is easily spied on but might be more convenient, like in a Facebook, Twitter, Google Hangouts, Slack, or Discord message, or in an email.
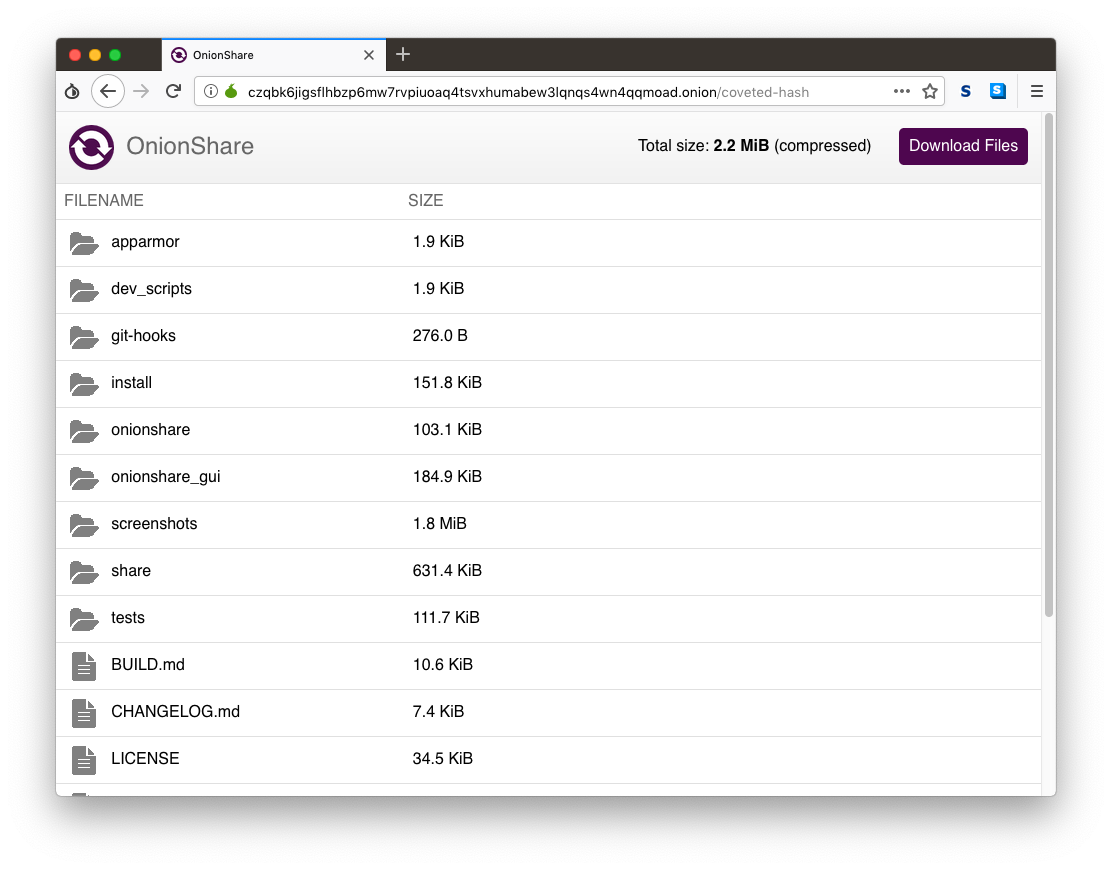
My friend then opens Tor Browser and loads the OnionShare address I sent her. She sees a website with a list of the files I'm sharing, and a "Download Files" button.
The key thing to understand about how OnionShare works is that this website is hosted directly on my laptop, not on a server in a data center somewhere. If I suspend my laptop, that link won't work anymore. If I close OnionShare before the files have been downloaded, then that Tor web address simply disappears from the internet. Because of this, OnionShare always takes place in real-time -- you and the person you're sharing files with need to both be online at the same time.
OnionShare doesn't zip if you share just one file
My friend then downloads the files, which are automatically zipped up. In this case, the zip file is called onionshare_snwga4.zip (the last part of the filename is random), and when she unzips it, she can see a copy of the OnionShare source code I sent. A new feature in OnionShare 2 is that if you share just a single file, it no longer zips it up (but still compresses it with gzip, built into the HTTP protocol).
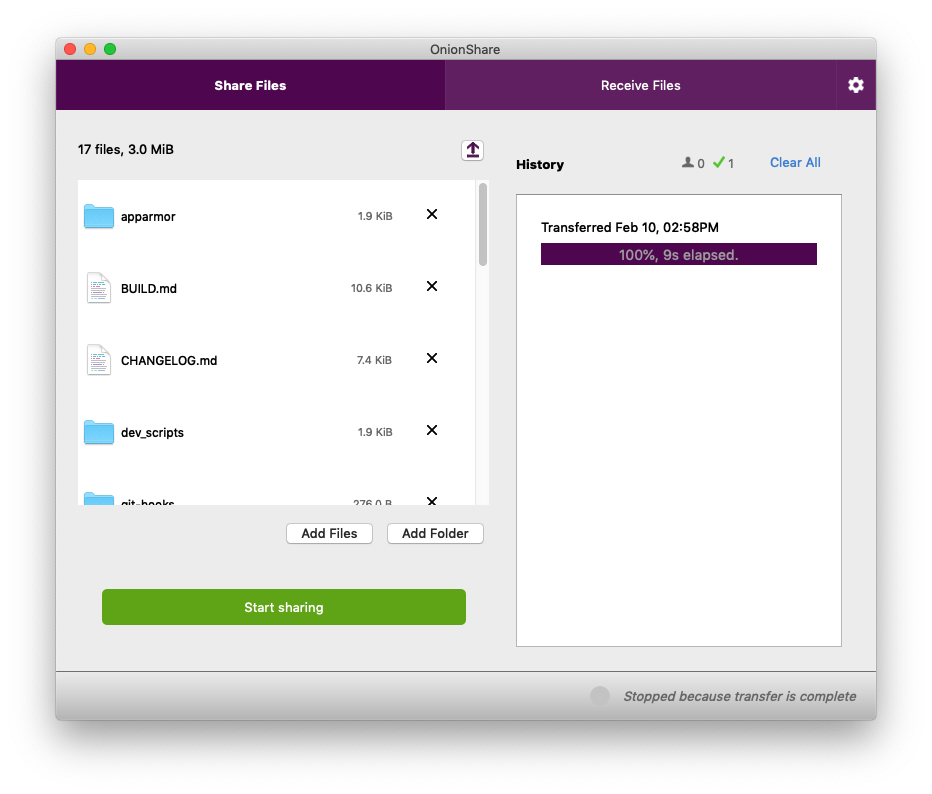
Back on my computer, OnionShare automatically stopped sharing the moment the files finished sending -- and when this happened, the OnionShare address completely disappeared from the internet, never to exist again.
OnionShare addresses are ephemeral by default
OnionShare addresses are ephemeral, and intended for one-time use. (For example, if someone sends you an OnionShare address in a Twitter DM, and a few minutes later you load it and download the files, that address won't exist anymore in the future. If anyone ever gains access to your Twitter DM history, that OnionShare address will no longer work.)
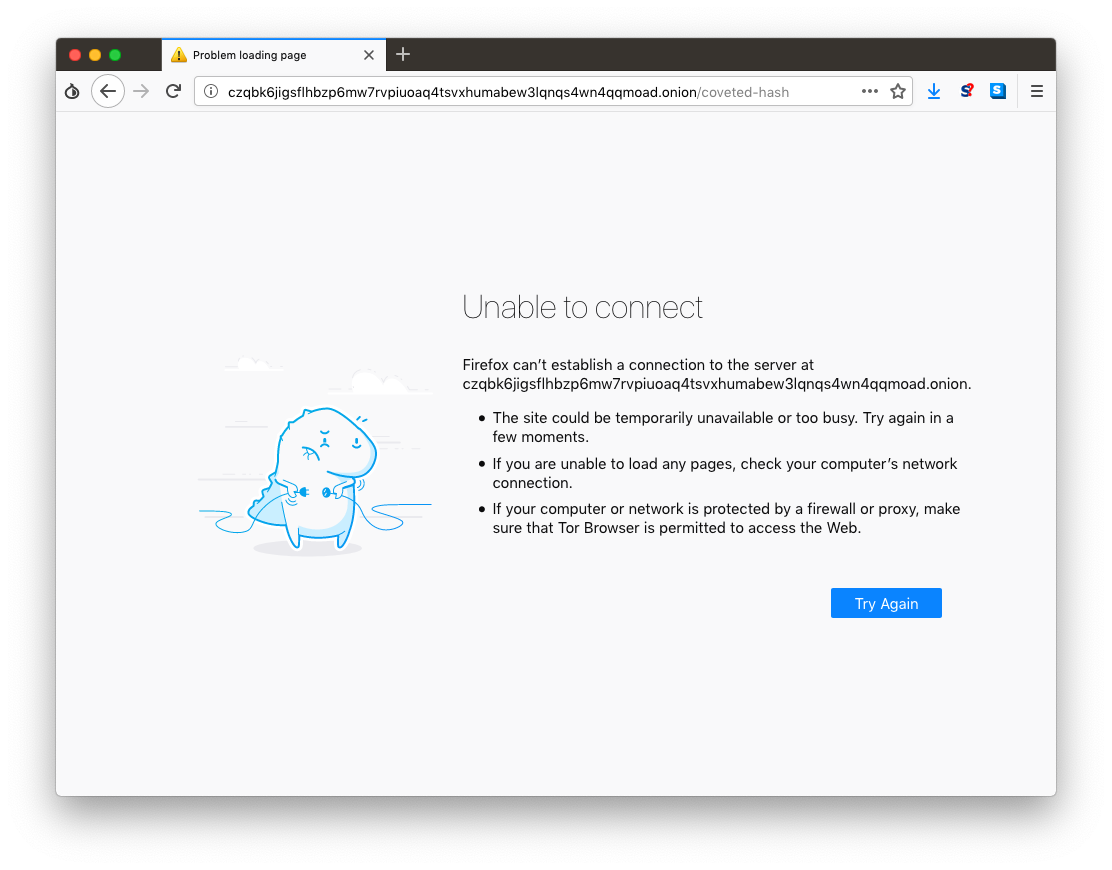
As you can see, after my friend finished downloading the files I sent her, that OnionShare address ceased to exist.
This is the default behavior of OnionShare, but you might want to use OnionShare to send files to a group of people, not just one person, in which case you don't want it to be ephemeral. In this case, you can uncheck "Stop sharing after files have been sent" in the Settings, and then multiple people can download your files, and you'll continue sharing until you manually click "Stop sharing" or close OnionShare.
Receiving files with OnionShare
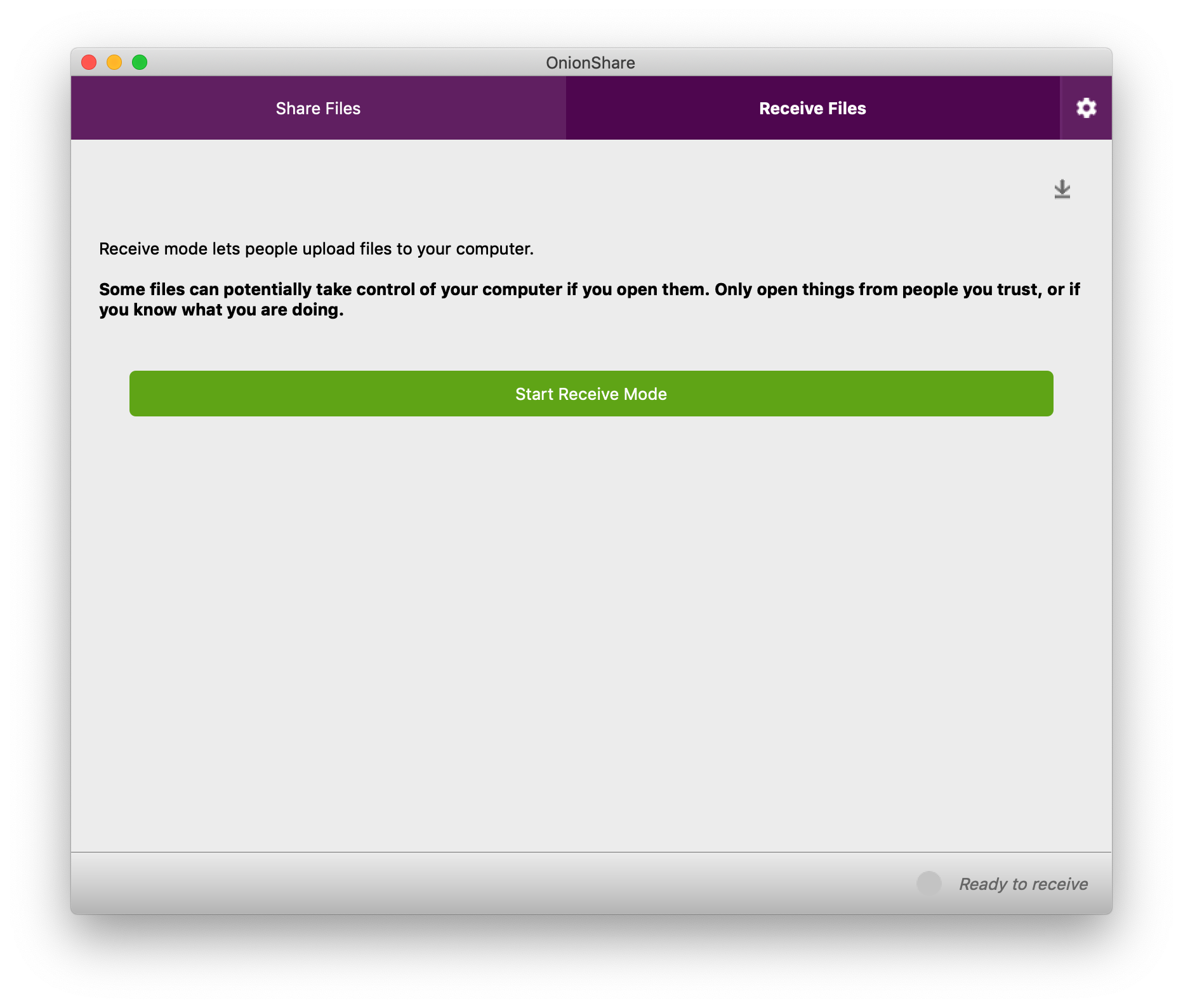
All of this is, more or less, how OnionShare has always worked. But the "Receive Files" tab is brand new to OnionShare 2. And it's still just the beginning -- we have plans for adding more tabs to OnionShare in the future, such as a static website sharing tab.
When you use OnionShare to receive files, you turn your computer into an anonymous dropbox -- I like to think of it is a super lightweight version of SecureDrop that anyone can run on their own laptop, for free, without needing to set up any infrastructure or do any systems administration. (However, it's not as robust, or secure, as SecureDrop, which enforces isolated environments in a way that OnionShare can't.)
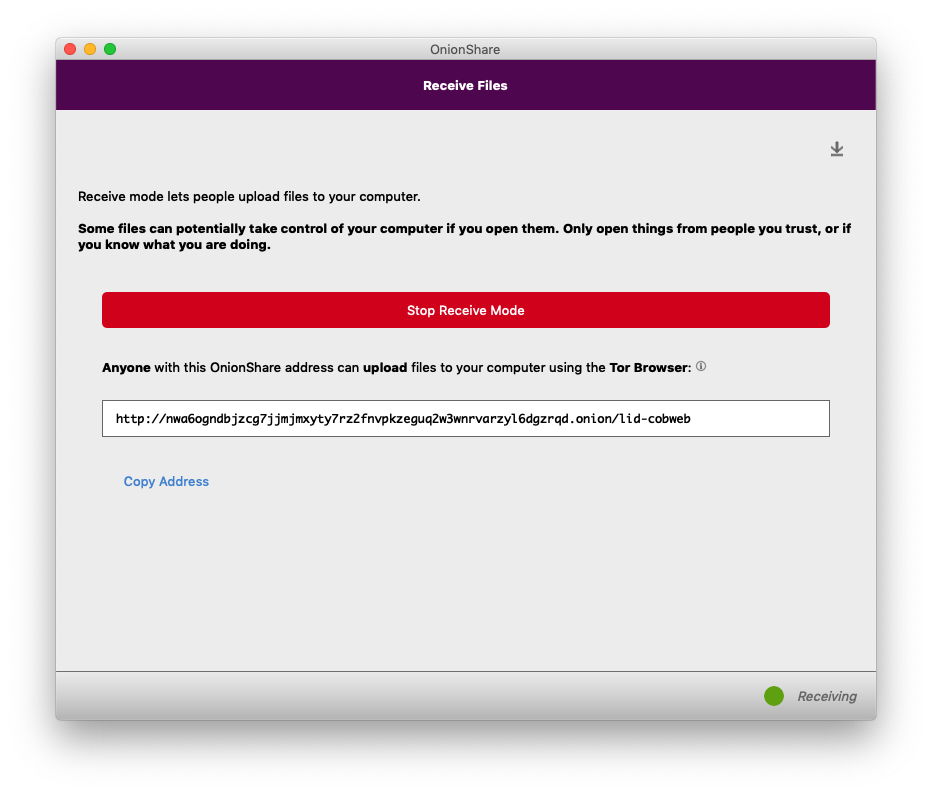
A few seconds after I clicked "Start Receive Mode", OnionShare gave me an unguessable Tor address, which I share with my friend the same way I did with the share mode address. But this time, instead of me sending files to her, she can send files to me, and all she needs is Tor Browser -- she doesn't need OnionShare herself.
If I publish this OnionShare address, anyone can send files to me, without me having any way to know who they are (because they'll be using Tor), and in a way that is end-to-end encrypted, so eavesdroppers spying on either of our networks can't access the files, or even realize that we're using OnionShare. To network eavesdroppers, all they'll be able to tell is that we're both using Tor.
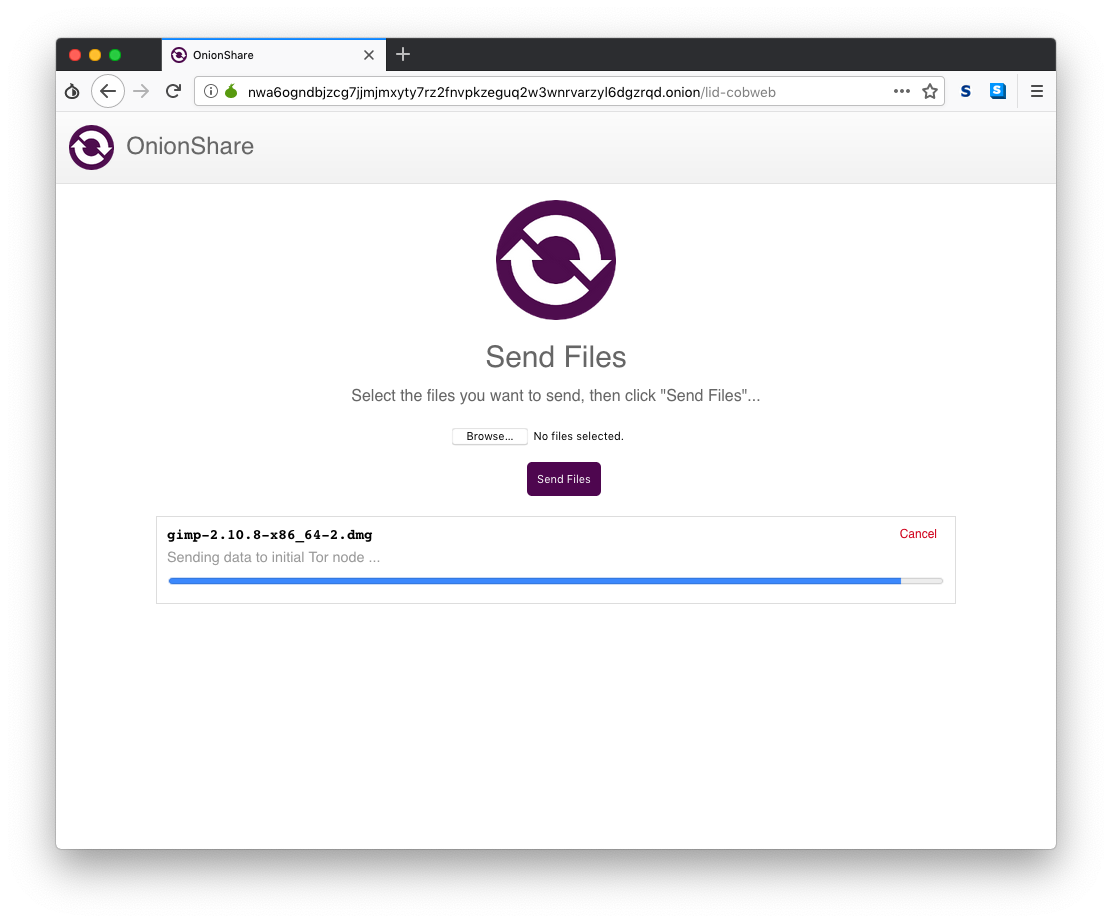
My friend simply clicks Browse, finds the files she wants to send, and clicks "Send Files".
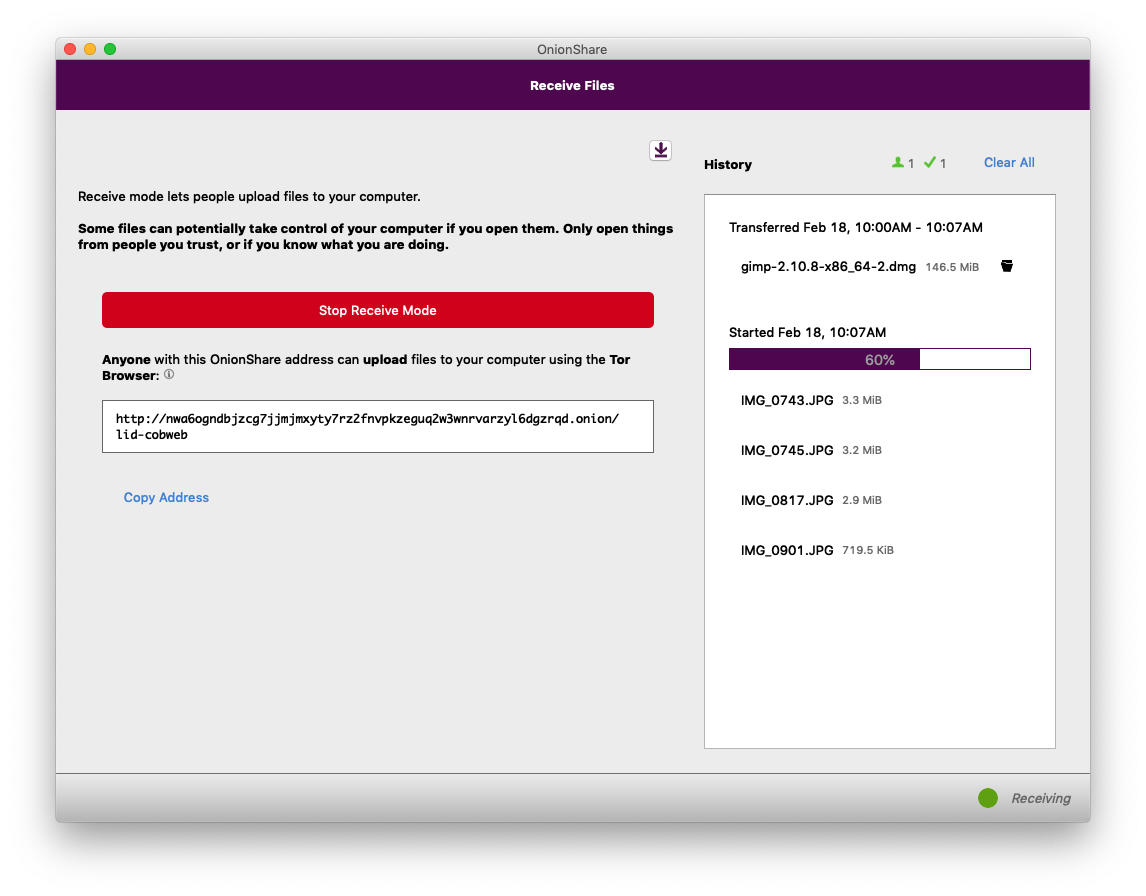
Over in OnionShare on my computer, I can see the status of all of the files that I'm receiving. Because OnionShare uses Tor onion services, I don't actually have any way of knowing who is sending files to me -- if I want to make it so only very specific people can send me files, I need to securely share the OnionShare address to only those people. My computer will continue to act as an anonymous dropbox until I click "Stop Receive Mode", or close OnionShare. And, just like with share mode, if I suspend my laptop, the OnionShare address stops working.
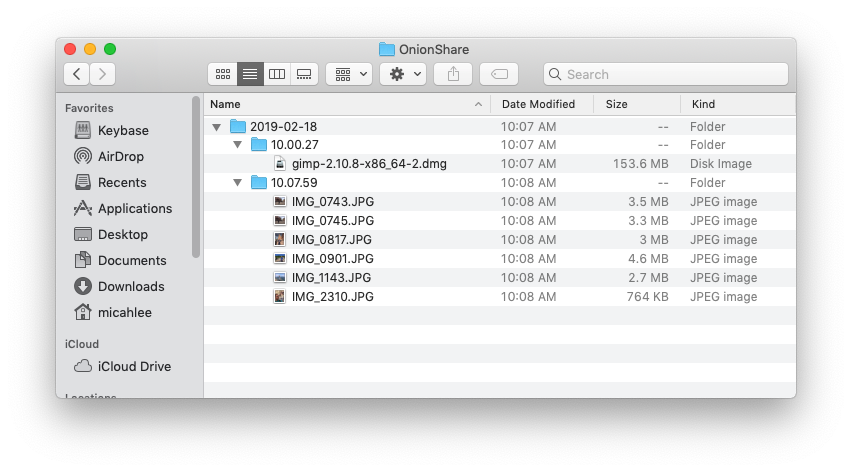
The files that I receive get saved to ~/OnionShare, and they're automatically organized by date and time.
Only open things from people you trust, or if you know what you are doing
Now that you know how the "Receive Files" tab works, be very careful with it, and make sure to take the prominent warning to heart:
Some files can potentially take control of your computer if you open them. Only open things from people you trust, or if you know what you are doing.
All of the warnings about not opening email attachments apply just as much here. In this example, I received gimp-2.10.8-x86_64-2.dmg, which is an installer for the open source image editing software GIMP. But, it could easily be a modified version of that installer that has malware hidden inside. And if someone sends you .docx or .pdf files, they could contain malware that could try to hack you through a vulnerability in Microsoft Word or Adobe Reader. How to safely open files you receive is outside of the scope of OnionShare. Use this feature with caution.
Public OnionShare addresses
OnionShare 2 has a new feature: Public mode. But before explaining what it does, first I'll explain how OnionShare addresses work without it.
By default, OnionShare addresses look http://[tor-address].onion/[slug], where the slug is two random words out of a list of words 7,776 words (technically, this is a 2-word diceware passphrase).
The idea is that if an attacker could figure out the tor-address part of the address, they still can't download the files you're sharing, or upload files to your computer, without first knowing the slug. The slug is, essentially, a password. (This is less important when using v3 onion services. The old v2 onion services have a known issue where, if the onion connection happens to get facilitated by a malicious Tor node, that node could learn the tor-address part. This is one of the reasons that v3 onions are more secure.)
But the slug is only two words, so what stops the attacker from guessing it, by guessing every possible 2-word slug? The wordlist that OnionShare uses is public, after all.
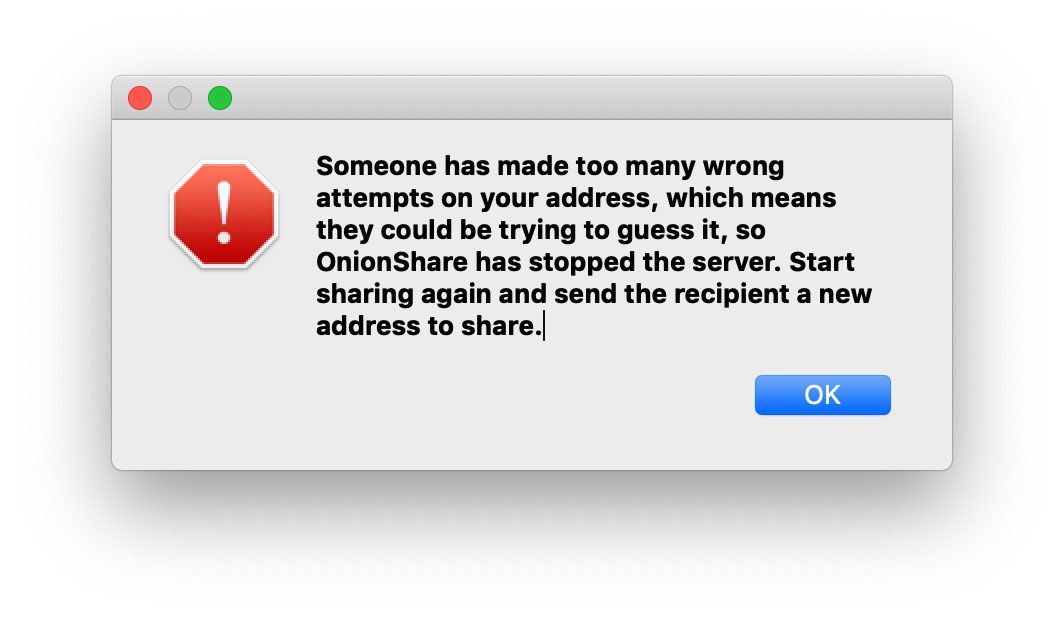
OnionShare counts how many 404 errors (file not found web requests), and on the 20th 404 error, it assumes that someone it trying to guess the slug and automatically stops the server.
This gives the attacker 20 chances to guess the two words correctly. Because the words are chosen from a list of 7,776 words, that means there are 7,776^2, or over 60 million, possible slugs. Which basically means that if an attacker tries to guess the slug, they have a 0.00003% chance of getting it right within their only 20 chances, and a 99.99996% chance of failing, and forcing OnionShare to stop sharing.
This works great, but what if you want anyone to be able to load your OnionShare address?
For example, let's say you want to anonymously publish some files. You disable the "Stop sharing after files have been sent" setting, drag the files into OnionShare, start sharing, and tweet the OnionShare address. It turns out that anyone on the internet that sees the tweet can force your server to stop just by making 20 404 errors. (This situation actually happened, by the way, and their server kept shutting down because people kept making 404 errors.)
This is the use case that public mode was built for. If you want to publicly share an OnionShare address, just go to Settings and check the box next to "Public mode". When you start sharing, the OnionShare address will look like http://[tor-address].onion/, without the slug, and the server will remain up no matter how many 404 errors it gets.
Running an anonymous dropbox
You've seen receive mode, which is great for allowing people to privately send you files. But if you want to allow anyone to privately send you files, there are a few settings you'll want to consider using.
First, you'll definitely want to enable public mode.
Second, you'll also want to go into Settings and enable "Use a persistent address". With this setting, when you stop an OnionShare server and then start it again, you'll get this exact same onion address as you had last time. This gives you the flexibility to, for example, reboot your computer and start OnionShare again, without having to switch OnionShare addresses.
And finally, you may want to run your anonymous dropbox on a headless Linux server, rather than your normal daily workstation. OnionShare comes with two binaries, onionshare (the command line version) and onionshare-gui (the graphical version). Both of them share the same configuration file -- in Linux, this is in ~/.config/onionshare/onionshare.json. So, using the graphical version of OnionShare, choose all of the settings that you'd like, and then copy onionshare.json to your server, and run OnionShare like this:
OnionShare in your language
Finally, one of the things I'm most excited about OnionShare 2 is that it has now been translated into twelve new languages, making OnionShare accessible to a considerable swath of humanity. Some of the major languages that OnionShare 2 is translated in include Spanish (400 million native speakers), Portuguese (215 million), Russian (170 million), and Japanese (130 million). (These numbers come from Babbel magazine.)
The new languages include: Bengali (বাংলা), Catalan (Català), Danish (Dansk), French (Français), Greek (Ελληνικά), Italian (Italiano), Japanese (日本語), Persian (فارسی), Brazilian Portuguese (Português Brasil), Russian (Русский), Spanish (Español), and Swedish (Svenska), and more languages will be included in the future. If you're a native speaker of a non-English language and are interested in contributing to OnionShare, you can find instructions for helping on the wiki.
I hope you like OnionShare 2!
Comments
Please note that the comment area below has been archived.
Awesome! Love the new…
Awesome! Love the new version!!!! Great work
> Unlike services like email…
> Unlike services like email, Google Drive, DropBox, WeTransfer, or nearly any other way people typically send files to each other, when you use OnionShare you don't give any companies access to the files that you're sharing.
This is the truly essential point, I think: OnionShare finally shortcircuits the "customer as product" model (or perhaps I should say "company as parasite sucking out the very life of its victims" model) which has come to dominate global consumerism.
> The easiest way to do this securely is to use an encrypted messaging app like Signal Desktop, Wire, Keybase, or iMessage -- or, if you're oldschool, Jabber/OTR.
I appreciate that trying to explain all of those methods in detail in one post would threaten to overwhelm readers who may never have used any of those things. But I think you need to provide all the details, including how you recommend people to register for (and pay for?) chat accounts, under the assumption these will be used soley for passing OnionShare2. Bear in mind that the people who most need to communicate are not likely to possess sustainable disposable income.
Clearly Onionshare2 is immediately useful for anyone who needs to share files with someone they already know, but passing the temporary onion address safely can still be a stumbling block for those who don't own (or trust) a smart phone or chatroom providers. Further reasons for distrusting such smart phone vendors as Google, Microsoft, Samsung, and even Apple are currently in the headlines.
The discontinued but very promising Tor Messenger was the only chat service I felt I could actually use with no fuss or muss, and one of its best features was that it was sufficiently platform-independent that I did not need to try to use a particular device and chat tool to communicate with an Android user and some other device and chat tool to communicate with someone who uses another brand of smart phone. It would be truly wonderful if TP can find some way to reboot the TM project, perhaps beyond the long reach of FBI threats. Antarctica perhaps? (With climate change, it's becoming more habitable in the summer.) Sealand? Highly elliptical and thruster varied orbits in a stealth space vehicle?
> If the files you're sharing aren't especially sensitive, you can also share this web address in a way that is easily spied on but might be more convenient, like in a Facebook, Twitter, Google Hangouts, Slack, or Discord message, or in an email.
Steganography can be very useful here. One hears that some people have been pulling FBI's nose (or... some other body part?) by sending strongly encrypted information steganographically hidden inside porn images. Because if you wish to appear unsuspicious, what could possibly be more normative than sharing porn? :-) Better yet, there are two levels in the steganography: the less hidden message contains a pointed insult to any agent who is hip to the scheme and manages to find and decrypt the less hidden message. The real message is more deeply hidden.
BTW, it is generally agreed that the purpose of "the 5G revolution" (aka the only infrastructure "improvements" [?] actually being built in America) is to enable ubiquitous streaming (and for the porn industry, highly lucrative) hidef videos. And who could object to that? Only the Anti-Sex League and the FBI. The expected explosion in traffic could actually help Tor users to become lost in the noise. But only if TP is prepared to handle its share of all this traffic.
> When you use OnionShare to receive files, you turn your computer into an anonymous dropbox -- I like to think of it is a super lightweight version of SecureDrop that anyone can run on their own laptop, for free, without needing to set up any infrastructure or do any systems administration.
It would be truly wonderful if, in the very near future, I could obtain news from my favorite trusted news source by anonymously purchasing an anonymous subscription and anonymously receiving news in my personal dropbox (with the onion address shared only with the news outlet, we hope). It would be like 1774 all over again! :-)
My desire and hope is that the anonymous onion address would be very difficult to correlate with the reams of data which Google/GRU/Boots/Facebook/FBI and all those other bad guys have been collecting about us, so that (I hope) the news company would truly treat our subscriptions as its sole revenue source, not its intrusive covert collection of reams of personal information about our habits, health, finances, family, friends, and interests.
I don't know whether this naively Utopian suggestion has any chance of being realized, but I'd like to see genuine journalism saved from the likes of Bezos/Drump.
> For example, let's say you want to anonymously publish some files.
Are you talking to Tails Project about their development of Tails Server? I don't know much about that but it seems possible that brainstorming might be beneficial to all.
> If I publish this OnionShare address, anyone can send files to me, without me having any way to know who they are (because they'll be using Tor), and in a way that is end-to-end encrypted, so eavesdroppers spying on either of our networks can't access the files, or even realize that we're using OnionShare. To network eavesdroppers, all they'll be able to tell is that we're both using Tor.
I hope TP and like minded NGOs will manage to arrange OnionShare2 training for all those reporters whose response (some years ago) to the insistence that any journalist who refuses to adopt strong encryption is not properly practicing their profession, was a howl of horror. Because those people presumably can learn and have learned the lesson of the Snowden leaks all the many disclosures prompted by those leaks. The bigger challenge of course will be to evade the Texas School Board by getting Onionshare training into high school civics classrooms all over America.
And then--- more posts please! :-)
Two good project that you…
Two good projects that you should follow :)
https://briarproject.org
https://cwtch.im
The first is (1) only usable…
The first is (1) only usable on Android phones (2) only available through an app store. Privacy advocates are likely to worry about both of those characteristics. We need something we can use which is so strongly protected that the evil phone vendor has no idea we even have that software on the phone we bought from them, much less how we are using it.
The second looks promising (open source) but if I understand correctly, to use it your communicants also need to have it properly built and installed and building from source might be too daunting for many people who need to use anonymous communication (e.g. journalists).
One aspect of TM which I particularly liked was that it was a Tor Project product and every simple and easy to use.
> [Briar is] only available…
> [Briar is] only available through an app store
Their site hosts an APK and instructions to install it, or use F-Droid. Unlike Google Play store, F-Droid hosts FOSS APK reproducible builds with PGP signatures. It isn't as easy as using the F-Droid app, but an APK can be downloaded through Tor and then installed offline. The F-Droid client app itself is FLOSS and hosted on gitlab.com
I think Tor Messenger would have been alternately hosted on F-Droid. I think Tor Browser Android will in the future. OONI is alternately hosted there, and Orbot claims to be.
Your point (1) stands as does black box hardware, but look into the custom firmware ecosystem.
> building [Cwtch] from source might be too daunting
The homepage introduces it as an experimental prototype, and often one of the drawbacks of trying out those is building from source, so not surprising. The homepage warns against trusting it at this stage, too, as it should. It's also based on Ricochet whose design has faced other skepticism such as binding a self-hosted, static onion address to a user's public profile and device presence.
>It would be truly wonderful…
>It would be truly wonderful if, in the very near future, I could obtain news from my favorite trusted news source by anonymously purchasing an anonymous subscription and anonymously receiving news in my personal dropbox (with the onion address shared only with the news outlet, we hope). It would be like 1774 all over again! :-)
Wouldn't this be accomplished if the news source provided an onion service website and an option to pay with anonymous cryptocurrencies (Monero, zcash, ...)? Why would you use OnionShare for that?
I think that is what I was…
I think that is what I was trying to suggest--- sorry I did not write more clearly!
There are some questions about the security of Zcash and other current generation cryptocurrencies but I hope these will be resolved in our favor.
Great piece! Great ideas!…
Great piece! Great ideas! Thanks
Great piece! Great ideas!…
Great piece! Great ideas! Thank you
> Highly elliptical and…
> Highly elliptical and thruster varied orbits in a stealth space vehicle?
Fascinating. Let's crowdfund a Cubesat running Gitlab or Gitea for Elon to launch. ;) One step closer to a literal IPFS.
But back on topic, thank you, Micah!
Unlike services like email,…
Tor is not alone in this. The same can achieved over ipv4 with tooling + RSA, Tor or i2p...
Is this just an uploader…
Is this just an uploader/downloader with NO encryption at all?
If so, this is better than OnionShare 2 because the server(file holder) don't know about decrypted file.
https://share.riseup.net/
All data sent and received…
All data sent and received through OnionShare is end to end encrypted using Tor’s V3 onion protocol.
As Micah Lee's post…
As Micah Lee's post explained, connections to any onion are strongly encrypted end-to-end, in addition to being strongly anonymized.
Not sure why I was unable to…
Not sure why I was unable to comment on micahflee/onionshare/issues/832 so here is my complaint: I'm sad that the timeout while "50% loading relay descriptors for internal paths" is the first issue that could me an advanced user. On my network, TorBrowser does not timeout while using the meek plugin but OnionShare does using meek_lite, but at least they can make the timeout limit the same as TorBrowser's.
OnionShare v3 looks like a…
OnionShare v3 looks like a better naming for your wonderful app.
Onionshare has great…
Onionshare has great features and even more potential. The devs are very sharp. Placing a lot of emphasis on simple and intuitive design with features that are useful for the greater public. Too often do devs release software that caters to a niche group.
I think onionshare can be taken even further to allow for fairly large communities to form.
A possible solution to large scale public file sharing and chat within onionshare could be to provide a dynamic onionshare address or link hosting/directory service. Whereby an onionshare user could easily create and host a website that other OS users could post/list their OS address on.
Each address could be coupled with a small description of what each user is sharing. A drop down menu beside each address could list all available files for the given address.
This eliminates the need for a complex search function or DHT. Instead a simple integrated search function could be included in the hosting service to allow visitors to quickly find interesting files, OS address descriptions, and or OS chat users.
When Onionshare users no longer want to share their files or chat address publicly, they can either choose to shut down their onion share app or click "unpublish my file index/chat address". The "link service host" gets a push notification that automatically removes the onionshare address and its related file index from their directory service.
The OS "link/directory host" could in effect provide a central location for users to find other like minded OS users based on their description.
As a failsafe/backup to the "link/directory hosting service", other OS users could opt in to mirror a "service". This allows for decentralization of popular link/directory services and eliminates a single point of failure.
> Onionshare has great…
> Onionshare has great features and even more potential. The devs are very sharp. Placing a lot of emphasis on simple and intuitive design with features that are useful for the greater public. Too often do devs release software that caters to a niche group.
Plus one!
BTW, I hope and presume that OnionShare2 will soon appear in the Debian repositories? And will be included in the next edition of Tails?
It seems that a very old…
It seems that a very old version of Onionshare is in the Debian software respository, but for Jessie (Debian oldstable) not Stretch (Debian stable). Is it not possible to get Onionshare2 into stable or at least testing?
Outstanding! Wonderful!…
Outstanding! Wonderful! Significant accomplishment! Thank you mica
OnionShare uses some sort of…
OnionShare uses some sort of "installer" that triggers some Windows thing on locked down systems.
However TBB "installs" and runs just fine.
So OnionShare is no good.
It sounds like "some Windows…
It sounds like "some Windows thing on locked down systems" is no good
TBB installs fine. The…
TBB installs fine. The system doesn't block based on which app, all else works fine. But on whatever the installer for OnionShare IS doing that TBB does NOT do, such as triggering some native WindowsOS installer functions. It's even a Windows popup block notice, not some 3rd party bs.
OnionShare is simply not guerrilla enough.
looks like i need to…
looks like i need to manually update each time on Ubuntu - why when i already use the old version
Windows. I was able to…
Windows. I was able to download 96KB file (from my computer) via OnionShare
but after dowloading completed - OnionShare crashes.
Downloaded, verified,…
Downloaded, verified, installed OnionShare-2.pkg, but OnionShare.app fails to open. No firewall or av is blocking it. Is there a link that specifies OnionShare 2 system requirements? If no link specifies system requirements, do you know what are the system requirements? Thanks. Platform: MacOS 10.10.5 Intel
Run '/Applications…
Run '/Applications/OnionShare.app/Contents/MacOS/onionshare-gui --debug' and post the log and the OS version here https://github.com/micahflee/onionshare/issues/new
This is truly a great work!…
This is truly a great work! Thank you for putting so much effort into making file transfers that safe.
Why isn't OnionShare 2…
Why isn't OnionShare 2 listed in the "our projects" section of the torproject.org home-page, where do we download it from ?
You can download it at https…
You can download it at https://onionshare.org/
It is developed by Micah Lee, a member of our community.
Wouldn't it get more…
Wouldn't it get more exposure at torproject.org? Not everyone wants to wade through blog posts to find useful anonymity tools. Even those that are willing to will no doubt experience blog fatigue at some point. Quick links with small descriptions is the way to go IMO.
+1 to having onionshare.org…
+1 to having onionshare.org links available on torproject.org
Plus one. Onionshare2 is an…
Plus one.
Onionshare2 is an important software which should be made available as a properly signed package in all the major repositories, especially Debian stable and testing.
Can TP work with Debian to see that this happens?
Or did FBI threaten Debian Project with being terminated with extreme prejudice if they made it practical for large numbers of at-risk users to obtain and install OnionShare2 with no fuss or muss?
@ Steph: Actually--- unless…
@ Steph:
Actually--- unless I misunderstood ML's instructions at the OnionShare site, it seems you must obtain the actual OnionShare2 software using a git pull from github, which most ordinary citizens do not know how to do without help.
It would be *much* easier to obtain and install if it were available through major distribution software repositories, especially the Debian repos.
Tor Messenger was easy to install and use!
Did FBI secretly threaten Tor Project? First they came for Tor Messenger, next will they come for Tor Browser? I hope not but TM was so promising (and so frighenting to the bad guys) that one has to wonder.
>> Did FBI secretly threaten…
>> Did FBI secretly threaten Tor Project?
>> First they came for Tor Messenger, next will they come for Tor Browser?
AFAIR "Tor Messenger" was just stopped.
So, WHERE DID YOU SAW articles about "Tor Messenger" & FBI ?
I use the old version of…
I use the old version of OnionShare which was included in the Debian oldstable (Jessie); unfortunately noone put a later version in Debian stable (Stretch).
> You can download it at https://onionshare.org/
Actually, Micah's instructions begin
> Start by getting the source code:
>
> git clone https://github.com/micahflee/onionshare.git
Can you even use git over Tor? Is it safe to install on a Tails USB stick? If one lacks code-reading fu, how to verify that the code has not been altered?
Next one must install dependencies via the Debian package manager and finally builds OnionShare from source. I could probably do that but was unable to get over the git issue.
I have downloaded and tried…
I have downloaded and tried it, but everytime I click on "start sharing" the app. quit...
Follow the debugging…
Follow the debugging instructions here https://github.com/micahflee/onionshare/wiki/Developing-OnionShare#debu… and post the log and the OS version here https://github.com/micahflee/onionshare/issues/new
so far I have used send…
so far I have used send.firefox.com for sending encrypted files as I now only learn the existence of OnionShare.
this firefox send system looks very simular* to the OnionShare system but I fear will not have the same security.
will get OnionShare installed to try it.
*load ff website
put a file to send in a box and receive a url
send the url to the addressed person by email or ?
the addressee copuy/paste the url in a web browser and get to click a button to download your file.
after the download, that url is destroyed and cannot be used anymore.
What is the command line…
What is the command line switch to let the share stay alive (instead "Stopped because transfer is complete") to let many persons download a file?
tried to install onion share…
tried to install onion share via ubuntu terminal.. and get error regards python3-distutils :( any tips ? i tried various sources to resolve this and nothing helped me.. thanks in advance
Please report this issue…
Please report this issue with any relevant information. https://github.com/micahflee/onionshare/issues/new
Does it really connect…
Does it really connect immediately without prompting? Doesn't that potentially flag your traffic for using public Tor relays? Wouldn't it be safer to start by asking if you want to connect or configure similar to what a new Tor Browser install does?