Run Tor Bridges to Defend the Open Internet

We believe everyone should have private access to the open internet, but not everyone is able to enjoy the luxury Tor provides. Freedom to publish, share, and access information online is critical for a healthy society, yet governments and entities around the world deny people this universal human right. All of the relays that make up the Tor network are publicly listed, so that means one way to try to prevent people from using Tor is to blacklist the public IP addresses of all of the thousands of Tor relays.
For example, the governments of China, Iran, and Kazakhstan exercise information control by trying to block Tor.
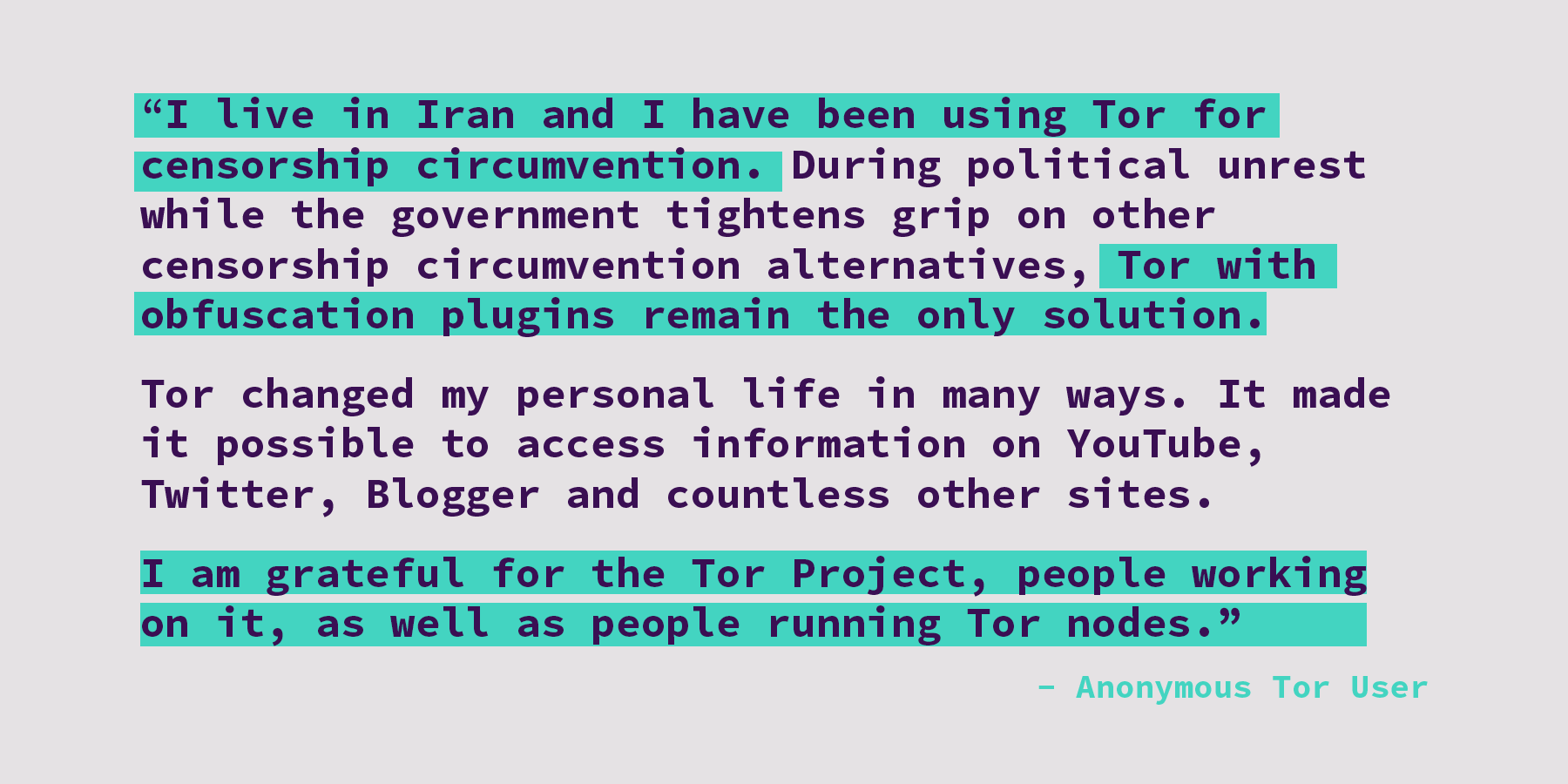
However, thanks to bridges, Tor users are still able to connect to the network when the public Tor relays are blocked. Bridges are private Tor relays that serve as stepping stones into the network. Not only are bridges private, they can also modify their network packets in a way that it's difficult for an observer to conclude that somebody is using Tor. Censored users are able to select bridges from BridgeDB or directly in Tor Browser’s Network Settings.
We currently have approximately 1,000 bridges, 600 of which support the obfs4 obfuscation protocol. Unfortunately, these numbers have been stagnant for a while. It's not enough to have many bridges: eventually, all of them could find themselves in block lists. We therefore need a constant trickle of new bridges that aren't blocked anywhere yet. This is where we need your help.
By setting up an obfs4 bridge, you can help censored users connect to the open internet through Tor.
Setting Up a Bridge
Bridges are relatively easy, low-risk, and low bandwidth to operate, but they have a big impact on people where the internet is under oppressive control. A bridge isn't likely to receive any abuse complaints, and since bridges are not listed in the public consensus, they are unlikely to be blocked by popular services. Bridges are a great option if you can only run a Tor node from your home network, have only one static IP address, and don't have a huge amount of bandwidth to donate -- we recommend giving your bridge at least 1 Mbit/sec and it should run 24/7.
To set up an obfs4 bridge, check out our newly revised installation instructions. We have guides for several Linux distributions, FreeBSD, OpenBSD, and docker. Note that an obfs4 bridge needs both an open OR *and* an open obfs4 port. If you run into any trouble while setting up your bridge, check out our help page.
Once you have set up your bridge, find your bridge’s fingerprint (our post-install instructions explains how) and send an email to bridge-campaign@torproject.org to tell us your bridge's fingerprint (don't confuse it with the bridge's "hashed fingerprint"). Next month, we will randomly select 10 new bridge operators to receive a metallic roots Tor t-shirt as a token of our gratitude for your help defending the open internet. Set up your bridge and email us by September 30 to qualify. (Edit 2019-10-09: Our random number generator has already picked ten winners. While you can no longer win a t-shirt, you can still win our hearts by continuing to set up new bridges!)

The shirt is available in Classic and Slim sizes S - 2XL, and we can ship to most places in the world.
Other ways to help
If you’re not technical enough to run a bridge but want to help censored users, there are other ways you can help:
- Make a donation to the Tor Project to support our work developing and sharing tools for privacy and freedom online.
- Help translate Tor materials and documentation including information on how to set up a bridge.
- Share your support of running and using Tor bridges on social media with the hashtag #RunTorBridges.
Internet freedom is on the decline around the world, but we aren’t giving up. Everyone should be able to exercise their right to freedom of expression online, and by running a Tor bridge, you can help people around the world do so more safely.
Comments
Please note that the comment area below has been archived.
Nice ! I was just thinking…
Nice!
I was just thinking about installing one this week end on a VPS with a ton of bandwidth :D
Hope I'll get the shirt
Woo thanks!
Woo thanks!
Nice timing! lol I had a…
Nice timing! lol
I had a bridge on Windows for many months, now I'm moving it to my Urubu server and hope to have more stability.
\o/
\o/
Just made a bridge and 2…
Just made a bridge and 2 exit relays. Happy to be supporting the tor project (:
Thanks for your help!
Thanks for your help!
My host offers a server that…
My host offers a server that only supports ipv6, not ipv4. Does tor require ipv4? Also, any particular geographic location that is most helpful to locate the server in? Thanks! :)
Tor doesn't require IPv4, so…
Tor doesn't require IPv4, so an IPv6-only bridge would work just fine. The geographic location isn't particularly important but if you get to choose, why not go with a location close to East Asia?
Here are maps of relays and…
Here are maps of relays and a legend:
https://botsin.space/@metricsbot/
https://twitter.com/toratlas
https://blog.torproject.org/comment/280788#comment-280788
Please add the most recent metrics-bot image in a new tab on https://metrics.torproject.org/networksize.html
Tor needs ipv4 unfortunately.
Tor needs ipv4 unfortunately.
My host provides a server…
My host provides a server with ipv6 but not ipv4. Does tor require ipv4? For example, I see the torrc defines the ServerTransportListenAddr using ipv4 notation. Also, any preferred geographic location that will provide the most help for the most people? Thanks! :)
Why do you need a static IP?
Why do you need a static IP?
Whenever your bridge changes…
Whenever your bridge changes its IP address, it loses all of its users because they have no way of learning your bridge's new IP address. That is bad user experience because these users now have to get new bridges. If you don't have a static IP address, we recommend running a snowflake proxy instead.
Does DDNS help here?
Does DDNS help here?
No. Bridges are identified…
No. Bridges are identified by IP addresses and not by domain names.
Because the bridge line…
Because the bridge line contains a numerical IP and not a hostname.
Hey Tor Community. We ship…
Hey Tor Community.
We ship Tor clients to many users.
We can switch to a shipped bridge config by default, seeing this post.
Hope thats ok.
Who is "we"? :)
Who is "we"? :)
> We can switch to a shipped…
> We can switch to a shipped bridge config by default
From the old General FAQ: You should make every Tor user be a relay. "Many Tor users cannot be good relays."
Does running a bridge on AWS…
Does running a bridge on AWS lead to ban? Is it against their policy?
Take a look at https://trac…
Take a look at https://trac.torproject.org/projects/tor/wiki/doc/GoodBadISPs and please edit the wiki page if anything is outdated.
Just setup a bridge :) maybe…
Just setup a bridge :) maybe consider changing the link on the email address in the blogpost to an actual mailto link though ;)
Oops, good catch.
Oops, good catch.
You can also run snowflake…
You can also run snowflake proxies by just installing a browser addon, see: https://snowflake.torproject.org
I use a VPN service without…
I use a VPN service without a static IP, anything I can do to help? Can I buy a T-shirt?
You could always run a…
You could always run a snowflake by installing the browser extension: https://snowflake.torproject.org.
Add that operators should…
Add that operators should probably not run a bridge on the same IP address as an exit or middle relay. Or any daemon that could attract network administrators who block it.
Add that users of Tor Browser who selected "This computer goes through a firewall that only allows connections to certain ports" or are behind a FascistFirewall would be helped if some operators use official, frequently-used web port numbers such as 80, 443, 8080, 110, 993, 995. Neither the support FAQ (1, 2, 3, 4) nor the TB-manual (1, 2) tell readers to try "This computer goes through a firewall" before trying bridges. They should.
More documentation for bridge operators:
https://2019.www.torproject.org/docs/bridges.html.en
https://2019.www.torproject.org/docs/pluggable-transports.html.en
https://trac.torproject.org/projects/tor/wiki/TorRelayGuide
https://blog.torproject.org/research-problem-five-ways-test-bridge-reac…
https://blog.torproject.org/research-problems-ten-ways-discover-tor-bri…
Thanks a lot But this web…
Thanks a lot
But even this web-page is not accessible in Iran!
What's the easiest way to…
What's the easiest way to get a list of a few obfs4 bridges if you are in China? You can't request them via e-mail, since both RiseUp and Gmail are banned in China.
Try requesting an obfs4…
Try requesting an obfs4 bridge directly in Tor Browser by going to Tor's network settings, clicking "Tor is censored in my country", and then going to "request a bridge from torproject.org".
Hi, I wanted to set up my…
Hi,
I wanted to set up my raspberry pie as a bridge - but it seems FreeBSD doesn't have an obfs4proxy-tor pkg for aarch64/arm64 :(
I notice occasionally I get…
I notice occasionally I get a Google IP address and it stops me from loading or searching, with their message that there is "unusual activity" in my Browser (Tor,of course).I am thus forced to close Tor and then reopen.
Can you tell me why that is happening?
By the way I am using what is called LOW High Speed, for cost reasons. It is half the cost of full High Speed and satisfies my needs as I don't play games nor do I use Social Networks.
Roger
> I am thus forced to close…
> I am thus forced to close Tor and then reopen.
It may not be necessary to close Tor Browser. You could make a "New Tor Circuit for this Site". If it doesn't work, you could log out of the site, make a new circuit, and try logging in again.
> Can you tell me why that is happening?
Read the FAQ sites:
Speed is irrelevant to the problem you describe. Fast connections still see captchas and warnings.
Just added a bridge to go…
Just added a bridge to go with my relay. The more the better.
snowflake is great, but what…
snowflake is great, but what will made the normal user run a bridge? it should be very simple, maybe just a click, it should be a switch in torbrowser or config in tor binary's torrc file. not in firefox/chrome.
On macOS, when using Tor…
On macOS, when using Tor Browser 8.5.5 with a custom obfs4 pluggable transport from BridgeDB, after I log in my university network account and establish a 3-hop connection to an https site, will the university network server/administration be able to log/see the IP address of the first node in my Tor circuit?
Do you know of any Tor Project documentation that has the answer to this question? If so, what is the URL?
The university network does not use Deep Packet Inspection. The first/bridge node in my circuit is configured with Tor 0.4.1.5 on Linux.
Thanks
> will the university…
> will the university network server/administration be able to log/see the IP address of the first node in my Tor circuit?
Yes, they will see that you're connected to an IP and communicating encrypted traffic, but hopefully they do not know that the IP is a Tor bridge. For more information, turn on Safer or Standard, and click on the grey buttons labeled "Tor" and "HTTPS" here:
https://www.eff.org/pages/tor-and-https
Got mine setup last…
Got mine setup last Wednesday!