Siti Networks In India Wants Me to Pay to Unblock Tor
by kushal | June 25, 2018

Siti Networks is one of the biggest cable broadband providers in India. They operate in 21 states and provide internet
connection in major cities as well as to many rural villages.
A few days ago, I took a broadband connection from them and Tor Browser failed to connect to the network. After digging more, I found they have blocked all the primary directory authority IP addresses and most of the fallback IP addresses (129 of 150). They are also blocking more than 50% of the default bridge IP addresses.
traceroute shows the following for all blocked addresses:
```
1 ROUTER (192.168.1.1) 2.429 ms 2.688 ms 2.953 ms
2 * * *
3 172.31.16.41 (172.31.16.41) 6.344 ms 8.057 ms 8.026 ms
4 172.31.1.37 (172.31.1.37) 7.949 ms 7.940 ms 7.915 ms
5 * * *
6 172.31.1.57 (172.31.1.57) 8.311 ms 3.188 ms 5.327 ms
7 172.31.1.1 (172.31.1.1) 4.815 ms 5.243 ms 4.306 ms
8 * * *
9 * * *
10 * * *
11 * * *
...
```
When I first called Siti Networks' technical support, they said nothing is blocked in their network, which is obviously false.
Later in the day they confirmed to me they are blocking Tor, because someone senior in the management chain thinks “Tor is very insecure and dangerous for the users."
They also suggested if I pay more to get a static IP, they will remove all blocks from my connection, including Tor. I refuse to pay more.
Their actions are in direct opposition to the net neutrality recommendations from the Telecom Regulatory Authority of India (TRAI).
Breaking Through This Censorship
When Tor is blocked, pluggable transports and bridges can help people circumvent the censorship and connect to the network. Even though Siti is violating Net Neutrality recommendations from TRAI and wants me to pay more money in order to enjoy the privacy and protections Tor Browser provides, I am thankfully still able to connect to the network through built-in bridges. You can set them up in Tor Network Settings.
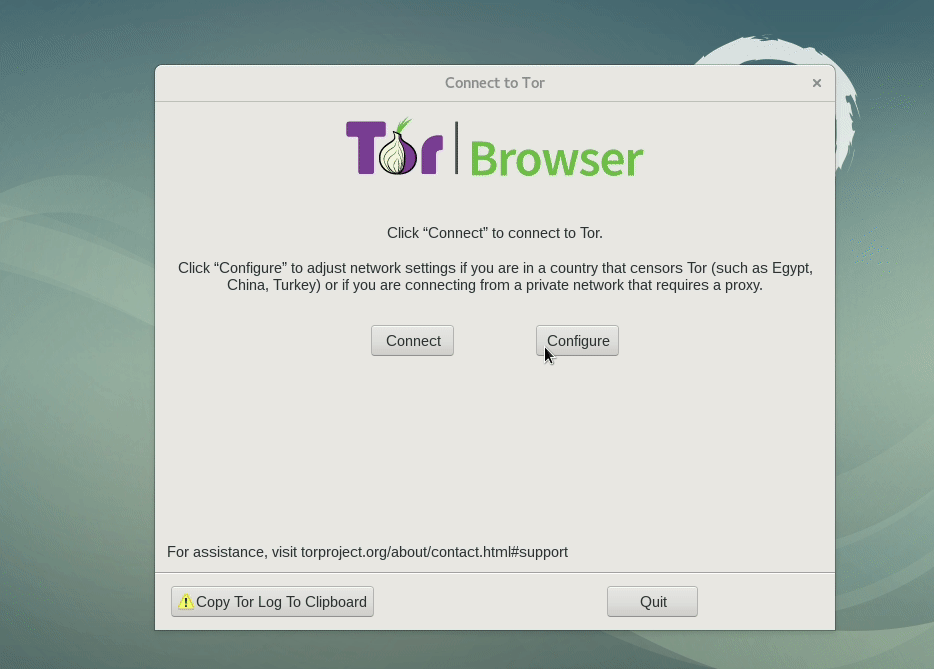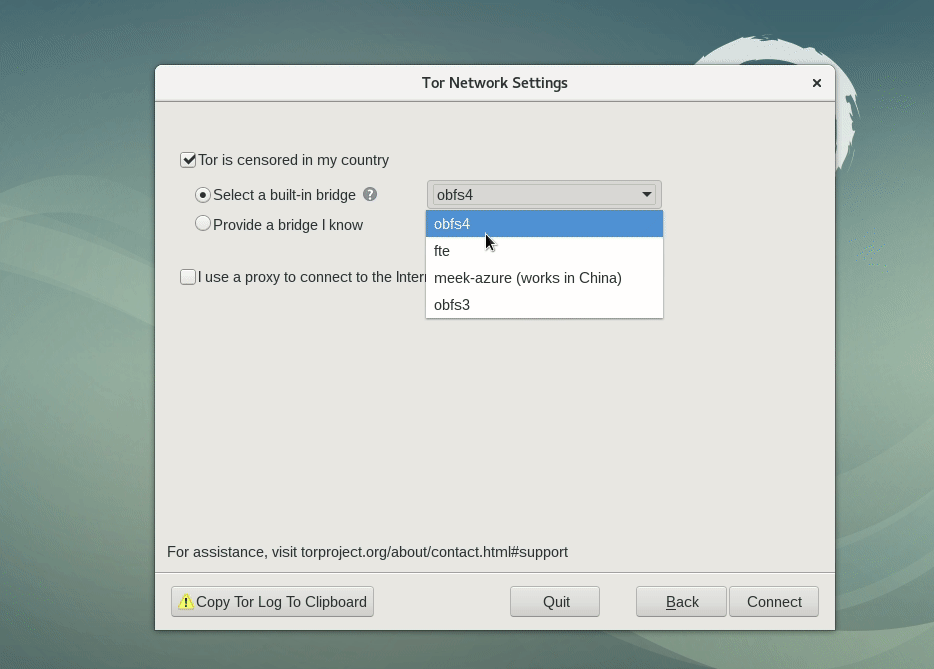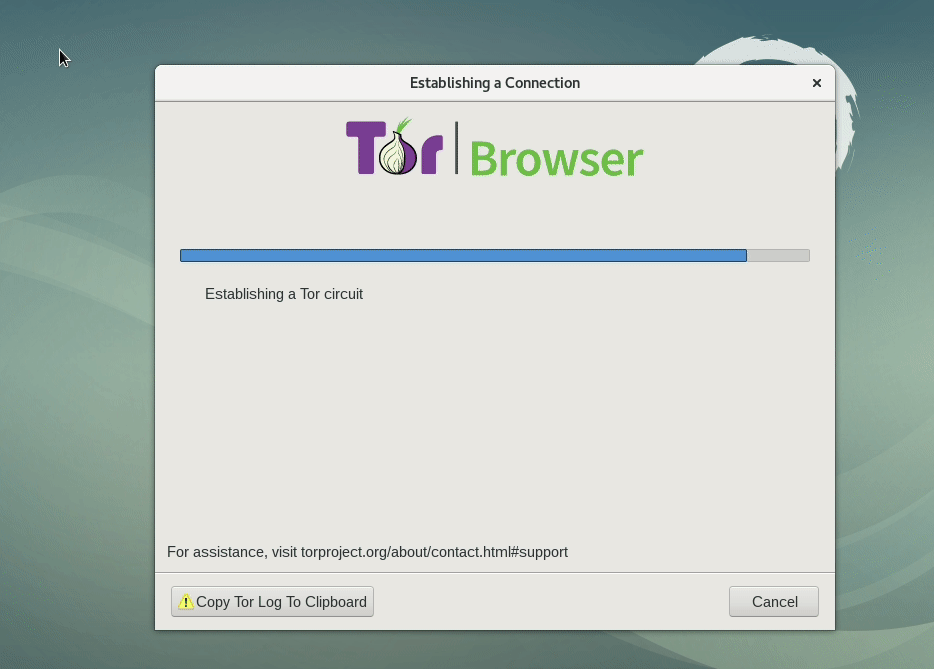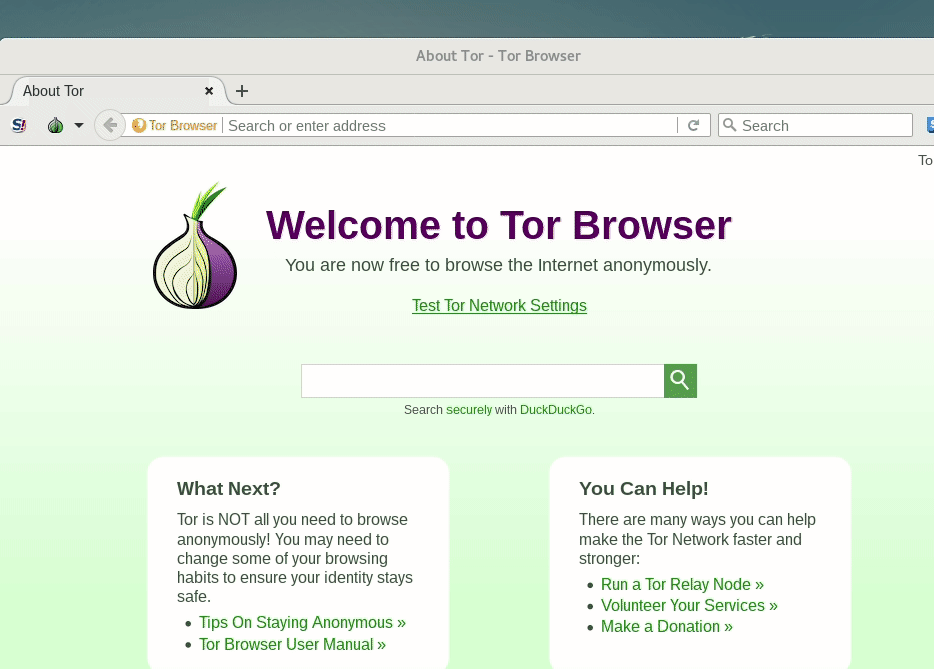
If you can't connect to any of the default bridges, you can find other bridges to try at bridges.torproject.org and get some custom bridge details.
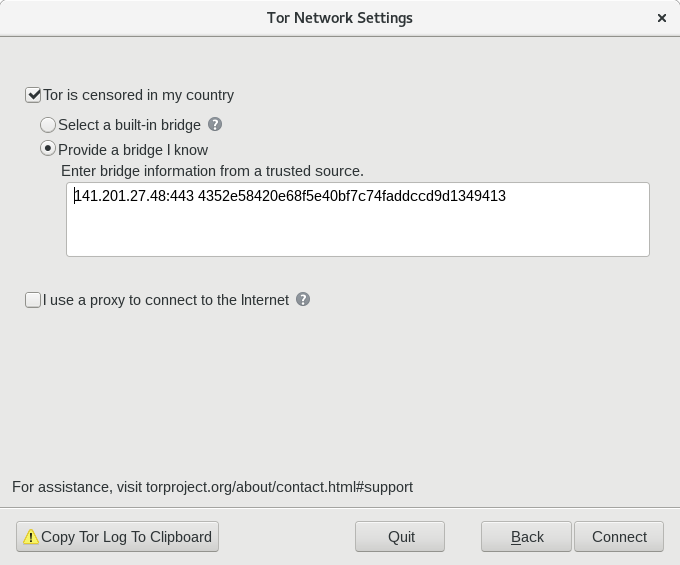
You can add those to your Tor Browser in the Network Settings configuration window.
In case the bridges URL is also blocked, you can send an email to bridges@torproject.org from a Gmail, Riseup, or Yahoo account, with the line "get bridges" by itself in the body of the mail. You will get some additional bridge IP addresses as a reply.
I have also been testing the network and measuring censorship with the OONI Probe mobile app. You can use it to test your network, too.
I will be reaching out to TRAI with this news. Has your network in India also been censored? Let me know in the comments or in #tor on IRC.
Comments
Please note that the comment area below has been archived.
OT: RE: https://lists…
OT:
RE: https://lists.debian.org/debian-user/2017/08/msg01420.html
RE: https://lists.torproject.org/pipermail/tor-talk/2018-May/044171.html
This continues to be a problem in Tails 3.7.1 and in Debian when
configured with the .onion URLs. (and running Tor)
To quote the second URL above:
###
In Synaptic, when fetching new package lists:
Failed 0 B InRelease tor+http://vwakviie2ienjx6t.onion/debian/ stretch
InRelease
All of the other chosen entries are correct, but for some reason
this same error crops up every time and there is no apparent
workaround. Can someone please contact the admin behind this
and enable complete functionality for this URL+InRelease
THIS IS NOT A NEW ISSUE. This problem was first reported
to Debian's mailing list on Fri, 25 Aug 2017:
https://lists.debian.org/debian-user/2017/08/msg01420.html
The thread ended without any clear resolution. In addition
this problem was reported to several other areas of the web.
I don't know what it takes to find the person responsible
and get him to fix it.
####
I hope someone can fix this issue. Thanks.
And most recent: https://lists.torproject.org/pipermail/tor-talk/2018-June/044274.html
Topic: Tails: Failed InRelease - tor+http://vwakviie2ienjx6t.onion/
Occupy NSA! theintercept…
Occupy NSA!
theintercept.com
The Wiretap Rooms
The NSA’s Hidden Spy Hubs in Eight U.S. Cities
Ryan Gallagher, Henrik Moltke
25 Jun 2018
Atlanta
51 Peachtree Center Avenue
Chicago
10 South Canal Street
Dallas
4211 Bryan Street
Los Angeles
420 South Grand Avenue
New York City
811 10th Avenue
San Francisco
611 Folsom Street
Seattle
1122 3rd Avenue
Washington, D.C.
30 E Street Southwest
Here's a step-by-step guide…
Here's a step-by-step guide on how to circumvent Internet censorship with Tor on different operating systems: https://sites.google.com/view/howtos/how-to-circumvent-internet-censorship-with-tor
Hope it helps!
Hi Kaushal..can you pls…
Hi Kaushal..can you pls update whome you spoken to unblock your ips and which location
we will invetigate
rawat_rajendra@yahoo.com
May I know who are you? Are…
May I know who are you? Are you an official from Siti Networks?
Hi Kushal, I am…
Hi Kushal,
I am particularly interested in knowing "How" they are able to censor traffic. It's also very worthwhile knowing who sold them this censor. If a company can sell it to them, they could do it to others as well. And obviously this looks like a pretty complicated piece of software if they are able to fetch bridge ip addrs on the fly and censor them.
I've observed heavy amount of censorship on Jio. A few tricks enabled me to know that they were using Netsweeper 4.11.1. I tried the same tricks on your ISP and they don't work. If you're willing, you can switch on Wireshark and try to connect to a few censored websites (on non-tor network) like torrentz.eu and observe which ip addr sends you the "This website is blocked as per Govt of India..." packet. Then try to Nmap that, or atleast post that on a public forum for people to analyze. Only a Siti User can do that, otherwise I would have tried it myself.
Cheers,
Jaskaran Singh
Just using Tor with bridges…
Just using Tor with bridges is an easier way out. I don't think they are using any dynamic blocking of bridge IPs.
another alternative is to…
another alternative is to use snowflake but it's still only in linux&mac alphas and there aren't many proxies run by people's browsers there
> traceroute shows the…
> traceroute shows the following for all blocked addresses
Can you post traceroute to google.com?
Hathaway in Bangalore which…
Hathaway in Bangalore which is in partnership with jio is also blocking default connections to tor network *facepalm*