Tor Browser 4.5 is released

The Tor Browser Team is proud to announce the first stable release in the 4.5 series. This release is available from the Tor Browser Project page and also from our distribution directory.
The 4.5 series provides significant usability, security, and privacy enhancements over the 4.0 series. Because these changes are significant, we will be delaying the automatic update of 4.0 users to the 4.5 series for one week.
Usability Improvements
On the usability front, we've improved the application launch experience for both Windows and Linux users. During install, Windows users are now given the choice to add Tor Browser to the Start Menu/Applications view, which should make it easier to find and launch. This choice is on by default, but can be disabled, and only affects the creation of shortcuts - the actual Tor Browser is still self-contained as a portable app folder. On the Linux side, users now start Tor Browser through a new wrapper that enables launching from the File Manager, the Desktop, or the Applications menu. The same wrapper can also be used from the command line.
We've also simplified the Tor menu (the green onion) and the associated configuration windows. The menu now provides information about the current Tor Circuit in use for a page, and also provides an option to request a new Tor Circuit for a site. Tor Browser is also much better at handling Tor Circuits in general: while a site remains in active use, all associated requests will continue to be performed over the same Tor Circuit. This means that sites should no longer suddenly change languages, behaviors, or log you out while you are using them.
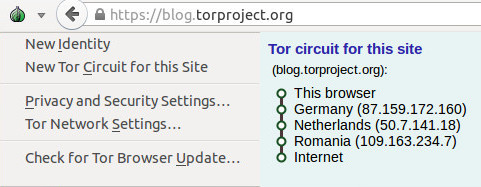
Figure 1: The new Tor Onion Menu
Security Improvements
On the security front, the most exciting news is the new Security Slider. The Security Slider provides user-friendly vulnerability surface reduction - as the security level is increased, browser features that were shown to have a high historical vulnerability count in the iSec Partners hardening study are progressively disabled. This feature is available from the Tor onion menu's "Privacy and Security Settings" choice.
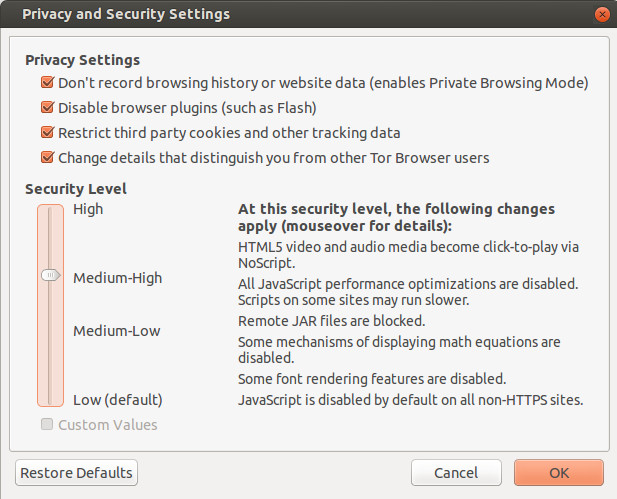
Figure 2: The new Security Slider
Our Windows packages are now signed with a hardware signing token graciously donated by DigiCert. This means that Windows users should no longer be prompted about Tor Browser coming from an unknown source. Additionally, our automatic updates are now individually signed with an offline signing key. In both cases, these signatures can be reproducibly removed, so that builders can continue to verify that the packages they produce match the official build binaries.
The 4.5 series also features a rewrite of the obfs2, obfs3, and ScrambleSuit transports in GoLang, as well as the introduction of the new obfs4 transport. The obfs4 transport provides additional DPI and probing resistance features which prevent automated scanning for Tor bridges. As long as they are not discovered via other mechanisms, fresh obfs4 bridge addresses will work in China today. Additionally, barring new attacks, private obfs4 addresses should continue to work indefinitely.
Privacy Improvements
On the privacy front, the 4.5 series improves on our pre-existing first party isolation implementation to prevent third party tracking. First party isolation provides the property that third party advertisements, like buttons, and "mashup" content that is included on one site will only know about your activity on that site, and will not be able to match it to your activity while you are on any other site. In other words, with first party isolation, Facebook, Twitter, and Google+ can't track you around the entire web using their infamous like buttons.
Specifically, in the 4.5 release, we now ensure that blob: URIs are scoped to the URL bar domain that created them, and the SharedWorker API has been disabled to prevent cross-site and third party communication. We also now make full use of Tor's circuit isolation to ensure that all requests for any third party content included by a site travel down the same Tor Circuit. This isolation also ensures that requests to the same third party site actually use separate Tor Circuits when the URL bar domain is different. This request isolation is enforced even when long-lived "HTTP Keep-Alive" connections are used.
We have also improved our resolution and locale fingerprinting defenses, and we now disable the device sensor and video statistics APIs.
New Search Provider
Our default search provider has also been changed to Disconnect. Disconnect provides private Google search results to Tor users without Captchas or bans.
Full Changelogs
Here is the complete list of changes in the 4.5 series since 4.0:
- All Platforms
- Update Tor to 0.2.6.7 with additional patches:
- Bug 15482: Reset timestamp_dirty each time a SOCKSAuth circuit is used
- Update NoScript to 2.6.9.22
- Update HTTPS-Everywhere to 5.0.3
- Bug 15689: Resume building HTTPS-Everywhere from git tags
- Update meek to 0.17
- Include obfs4proxy 0.0.5
- Use obfs4proxy for obfs2, obfs3, obfs4, and ScrambleSuit bridges
- Pluggable Transport Dependency Updates:
- Bug 15265: Switch go.net repo to golang.org/x/net
- Bug 15448: Use golang 1.4.2 for meek and obs4proxy
- Update Tor Launcher to 0.2.7.4. Changes since 0.2.7.0.2 in 4.0.8:
- Bug 11879: Stop bootstrap if Cancel or Open Settings is clicked
- Bug 13271: Display Bridge Configuration wizard pane before Proxy pane
- Bug 13576: Don't strip "bridge" from the middle of bridge lines
- Bug 13983: Directory search path fix for Tor Messanger+TorBirdy
- Bug 14122: Hide logo if TOR_HIDE_BROWSER_LOGO set
- Bug 14336: Fix navigation button display issues on some wizard panes
- Bug 15657: Display the host:port of any connection faiures in bootstrap
- Bug 15704: Do not enable network if wizard is opened
- Update Torbutton to 1.9.2.2. Changes since 1.7.0.2 in 4.0.8:
- Bug 3455: Use SOCKS user+pass to isolate all requests from the same url domain
- Bug 5698: Use "Tor Browser" branding in "About Tor Browser" dialog
- Bug 7255: Warn users about maximizing windows
- Bug 8400: Prompt for restart if disk records are enabled/disabled.
- Bug 8641: Create browser UI to indicate current tab's Tor circuit IPs
- (Many Circuit UI issues were fixed during 4.5; see release changelogs for those).
- Bug 13651: Prevent circuit-status related UI hang.
- Bug 13666: Various circuit status UI fixes
- Bug 13671: Make bridges visible on circuit display
- Bug 13672: Make circuit display optional
- Bug 13881: Localize strings for tor circuit display
- Bug 13882: Fix display of bridges after bridge settings have been changed
- Bugs 13891+15207: Fix exceptions/errors in circuit display with bridges
- Bug 14324: Show HS circuit in Tor circuit display
- Bug 14866: Show correct circuit when more than one exists for a given domain
- Bug 14937: Show meek and flashproxy bridges in tor circuit display
- Bug 15086: Handle RTL text in Tor circuit display
- Bug 15472: Make node text black in circuit status UI
- Bug 15510: Close Tor Circuit UI control port connections on New Identity
-->
- Bug 9387: Security Slider 1.0
- Include descriptions and tooltip hints for security levels
- Notify users that the security slider exists
- Make use of new SVG, jar, and MathML prefs
- Bug 9442: Add New Circuit button to Torbutton menu
- Bug 9906: Warn users before closing all windows and performing new identity.
- Bug 10216: Add a pref to disable the local tor control port test
- Bug 10280: Strings and pref for preventing plugin initialization.
- Bug 11175: Remove "About Torbutton" from onion menu.
- Bug 11236: Don't set omnibox order in Torbutton (to prevent translation)
- Bug 11449: Fix new identity error if NoScript is not enabled
- Bug 13019: Change locale spoofing pref to boolean
- Bug 13079: Option to skip control port verification
- Bug 13406: Stop directing users to download-easy.html.en on update
- Bug 13650: Clip initial window height to 1000px
- Bugs 13751+13900: Remove SafeCache cache isolation code in favor of C++ patch
- Bug 13766: Set a 10 minute circuit lifespan for non-content requests
- Bug 13835: Option to change default Tor Browser homepage
- Bug 13998: Handle changes in NoScript 2.6.9.8+
- Bug 14100: Option to hide NetworkSettings menuitem
- Bug 14392: Don't steal input focus in about:tor search box
- Bug 14429: Provide automatic window resizing, but disable for now
- Bug 14448: Restore Torbutton menu operation on non-English localizations
- Bug 14490: Use Disconnect search in about:tor search box
- Bug 14630: Hide Torbutton's proxy settings tab.
- Bug 14631: Improve profile access error msgs (strings for translation).
- Bugs 14632+15334: Display Cookie Protections only if disk records are enabled
- Bug 15085: Fix about:tor RTL text alignment problems
- Bug 15460: Ensure FTP urls use content-window circuit isolation
- Bug 15502: Wipe blob: URIs on New Identity
- Bug 15533: Restore default security level when restoring defaults
- Bug 15562: Bind SharedWorkers to thirdparty pref
- Update Tor to 0.2.6.7 with additional patches:
- Bug 3455: Patch Firefox SOCKS and proxy filters to allow user+pass isolation
- Bug 4100: Raise HTTP Keep-Alive back to 115 second default
- Bug 5698: Fix branding in "About Torbrowser" window
- Bug 10280: Don't load any plugins into the address space by default
- Bug 11236: Fix omnibox order for non-English builds
- Also remove Amazon, eBay and bing; add Youtube and Twitter
- Bug 11955: Backport HTTPS Certificate Pinning patches from Firefox 32
- Bug 12430: Provide a preference to disable remote jar: urls
- Bugs 12827+15794: Create preference to disable SVG images (for security slider)
- Bug 13019: Prevent Javascript from leaking system locale
- Bug 13379: Sign our MAR update files
- Bug 13439: No canvas prompt for content callers
- Bug 13548: Create preference to disable MathML (for security slider)
- Bug 13586: Make meek use TLS session tickets (to look like stock Firefox).
- Bug 13684: Backport Mozilla bug #1066190 (pinning issue fixed in Firefox 33)
- Bug 13788: Fix broken meek in 4.5-alpha series
- Bug 13875: Spoof window.devicePixelRatio to avoid DPI fingerprinting
- Bug 13900: Remove 3rd party HTTP auth tokens via Firefox patch
- Bug 14392: Make about:tor hide itself from the URL bar
- Bug 14490: Make Disconnect the default omnibox search engine
- Bug 14631: Improve startup error messages for filesystem permissions issues
- Bugs 14716+13254: Fix issues with HTTP Auth usage and TLS connection info display
- Bug 14937: Hard-code meek and flashproxy node fingerprints
- Bug 15029: Don't prompt to include missing plugins
- Bug 15406: Only include addons in incremental updates if they actually update
- Bug 15411: Remove old (and unused) cacheDomain cache isolation mechanism
- Bug 15502: Isolate blob: URI scope to URL domain; block WebWorker access
- Bug 15562: Disable Javascript SharedWorkers due to third party tracking
- Bug 15757: Disable Mozilla video statistics API extensions
- Bug 15758: Disable Device Sensor APIs
- Bug 12468: Only print/write log messages if launched with --debug
- Bug 13375: Create a hybrid GUI/desktop/shell launcher wrapper
- Bug 13717: Make sure we use the bash shell on Linux
- Bug 15672: Provide desktop app registration+unregistration for Linux
- Bug 15747: Improve start-tor-browser argument handling
- Bug 3861: Begin signing Tor Browser for Windows the Windows way
- Bug 10761: Fix instances of shutdown crashes
- Bug 13169: Don't use /dev/random on Windows for SSP
- Bug 14688: Create shortcuts to desktop and start menu by default (optional)
- Bug 15201: Disable 'runas Administrator' codepaths in updater
- Bug 15539: Make installer exe signatures reproducibly removable
- Bug 10138: Switch to 64bit builds for MacOS
Here is the list of changes since the last 4.5 alpha (4.5a5):
- All Platforms
- Update Tor to 0.2.6.7 with additional patches:
- Bug 15482: Reset timestamp_dirty each time a SOCKSAuth circuit is used
- Update NoScript to 2.6.9.22
- Update HTTPS-Everywhere to 5.0.3
- Bug 15689: Resume building HTTPS-Everywhere from git tags
- Update meek to 0.17
- Update obfs4proxy to 0.0.5
- Update Tor Launcher to 0.2.7.4
- Bug 15704: Do not enable network if wizard is opened
- Bug 11879: Stop bootstrap if Cancel or Open Settings is clicked
- Bug 13576: Don't strip "bridge" from the middle of bridge lines
- Bug 15657: Display the host:port of any connection faiures in bootstrap
- Update Torbutton to 1.9.2.2
- Bug 15562: Bind SharedWorkers to thirdparty pref
- Bug 15533: Restore default security level when restoring defaults
- Bug 15510: Close Tor Circuit UI control port connections on New Identity
- Bug 15472: Make node text black in circuit status UI
- Bug 15502: Wipe blob URIs on New Identity
- Bug 15795: Some security slider prefs do not trigger custom checkbox
- Bug 14429: Disable automatic window resizing for now
- Bug 4100: Raise HTTP Keep-Alive back to 115 second default
- Bug 13875: Spoof window.devicePixelRatio to avoid DPI fingerprinting
- Bug 15411: Remove old (and unused) cacheDomain cache isolation mechanism
- Bugs 14716+13254: Fix issues with HTTP Auth usage and TLS connection info display
- Bug 15502: Isolate blob URI scope to URL domain; block WebWorker access
- Bug 15794: Crash on some pages with SVG images if SVG is disabled
- Bug 15562: Disable Javascript SharedWorkers due to third party tracking
- Bug 15757: Disable Mozilla video statistics API extensions
- Bug 15758: Disable Device Sensor APIs
- Update Tor to 0.2.6.7 with additional patches:
- Linux
- Bug 15747: Improve start-tor-browser argument handling
- Bug 15672: Provide desktop app registration+unregistration for Linux
- Windows
- Bug 15539: Make installer exe signatures reproducibly removable
- Bug 10761: Fix instances of shutdown crashes
Post update 4/28/2015: Provide screenshots of the Tor Onion menu and Security Slider.
Post update 4/28/2015: Add section headers.
Comments
Please note that the comment area below has been archived.
░░░░░░░░▌
░░░░░░░░▌▒█░░░░░░░░░░░▄▀▒▌ Wow new version
░░░░░░░░▌▒▒█░░░░░░░░▄▀▒▒▒▐
░░░░░░░▐▄▀▒▒▀▀▀▀▄▄▄▀▒▒▒▒▒▐
░░░░░▄▄▀▒░▒▒▒▒▒▒▒▒▒█▒▒▄█▒▐ Much changed
░░░▄▀▒▒▒░░░▒▒▒░░░▒▒▒▀██▀▒▌
░░▐▒▒▒▄▄▒▒▒▒░░░▒▒▒▒▒▒▒▀▄▒▒▌ Such secure
░░▌░░▌█▀▒▒▒▒▒▄▀█▄▒▒▒▒▒▒▒█▒▐
░▐░░░▒▒▒▒▒▒▒▒▌██▀▒▒░░░▒▒▒▀▄▌ Very good job
░▌░▒▄██▄▒▒▒▒▒▒▒▒▒░░░░░░▒▒▒▒▌
▀▒▀▐▄█▄█▌▄░▀▒▒░░░░░░░░░░▒▒▒▐
▐▒▒▐▀▐▀▒░▄▄▒▄▒▒▒▒▒▒░▒░▒░▒▒▒▒▌
▐▒▒▒▀▀▄▄▒▒▒▄▒▒▒▒▒▒▒▒░▒░▒░▒▒▐
Much agreement, such thanks
Much agreement, such thanks Tor Project team !
Nice Haha
Nice
Haha
the Enable/Disable Rules
the Enable/Disable Rules does not appear immediately and you get exposed to trackers because of it. Can you make it a lot easier to do stop all of them from tracking? its on the HTTPS everywhere part but for some reason it does not show the option (to edit the enable/disable rules) without being exposed.
Nice. Good work guys.
Nice. Good work guys.
How come NoScript still says
How come NoScript still says that scripts are allowed when the security slider is set to high?
Hard to say. One reason
Hard to say. One reason could be that the UI is not updated properly. Did you reload the page/load a different one and the problem is still there?
Interesting. The problem
Interesting. The problem seems to have gone away when I tested it again. I think the key is to do what you suggested: reload the page or go to a different one.
Same person again. I posted
Same person again. I posted earlier that reloading seemed to have solved the issue. However, I still think it's bad that the UI doesn't change immediately to reflect the newly-set security settings.
I agree. I have brought this
I agree. I have brought this up with Giorgio (the NoScript author) and we'll work to find a fix for either 4.5.1 or in the next NoScript update.
Checking
Checking https://archive.torproject.org/tor-package-archive/torbrowser/4.5/
$ sha256sum -c sha256sums.txt
sha256sum: WARNING: 75 computed checksums did NOT match
$ sha256sum -c sha256sums.incrementals.txt
sha256sum: WARNING: 105 computed checksums did NOT match
Has something gone wrong?
It works for me modulo the
It works for me modulo the MAR files and the Windows bundles. These have additional signatures that need to get stripped off first. See: https://www.torproject.org/docs/verifying-signatures.html.en (the advanced sections)
Mac download is incorrect.
Mac download is incorrect. It lists osx32 in the URL, but it should be osx64.
Thanks. This should be fixed
Thanks. This should be fixed now.
I love it EXCEPT one thing:
I love it EXCEPT one thing: the fact that there's no "Never show me this again" option for the warning when resizing the window.
For users who already know and understand the risk of resizing the window, this is very annoying.
Even those who don't yet know the risk will get the picture!
You only get it shown three
You only get it shown three times which seemed to be a good trade-off between making sure that users don't get annoyed and making sure that they really notice things and don't just click it away.
I'm not OP but why continue
I'm not OP but why continue to force resizing full windows after three warnings? Couldn't full screen be an exception even when non-full screen sizes are getting resized
Because that might suggest
Because that might suggest to users that full screen is somehow safer than non-full screen
I use TOR on three different
I use TOR on three different devices- with three different monitor sizes.
When the windows open I check the screen size on each with ip-check and https://arthuredelstein.github.io/tordemos/media-query-fingerprint.html.
In all three cases (despite the greatly differing monitor sizes) the window/screen size is always shown as 1000 x X00.
Can I change the screen size to make better use of the available area of the relevant monitor, as long as I increase either value in increments of 100, without compromising anonymity?
Thanks for any information.
wow ! it's so great you
wow ! it's so great you added Tor button on stable version
thanks so much
'Uh oh, spaghettios! There
'Uh oh, spaghettios!
There currently aren't any bridges available... Perhaps you should try going back and choosing a different bridge type!'
I did and the result was the same. Great update but there are NO BRIDGES. NONE, LIKE 0. How can people such as myself who live in censored countries use Tor?
Please someone add bridges obfs3,obfs4, scramblesuit or fteproxy, PLEASE. Keep up the good work and much appreciated in advance.
Hm... Why do you think there
Hm... Why do you think there are no bridges included? I just selected obfs4 and got connected on a Windows 7 machine?
Hi. Thanks for reply. Having
Hi. Thanks for reply. Having still trouble through https://bridges.torproject.org to obtain any kind of bridges. I need the initial connection to be through bridges not connecting to Tor at all (safety reasons). Everything was working perfect until this update, and now there are no bridges listed and I need them. Any ideas? Cheers.
I need this,too. from
I need this,too. from https://bridges.torproject.org/bridges?transport=obfs3
These is no one.
What prompted the change in
What prompted the change in search engine? Are we now getting paid to include disconnect as the default search engine?
We don't get paid for that
We don't get paid for that as it currently stands. But Startpage was not happy with our traffic and showed sometimes CAPTCHAs. Disconnect on the other hand approached us with respect to search engine traffic and donated some money.
I'm very happy with the
I'm very happy with the change, I personally hate the results I get from StartPage. Disconnect results are much better.
I second this. A needed
I second this. A needed change and a great choice.
Hello. I sometimes use
Hello.
I sometimes use startpage, sometimes use duckduckgo. DDG is the default a they don't show captchas. Also, they offer a hidden service to search the web, which I think could be used as the default.
I don't know how good or bad Disconnect is, but if they offered to support the traffic and donated money it might be worth it :)
What about having the hidden service of ddg as the default? Bad idea? Why?
DDG search results are
DDG search results are pretty worthless IMO. Disconnect is much better in terms of search results. I don't think simply offering a HS should mean DDG is the default, rather, good search results should be the deciding factor.
And has anyone asked Disconnect to run a HS? They may be willing.
Disconect.me "approached
Disconect.me "approached [...]" and "offered money". Is there a free lunch? There must be some trade off (NSA wants to see more Tor traffic again?)
As for StartPage sometimes showing CAPTCHAS... Have you seen it a lot? It doesn't happen often, in my experience. And if it happens, perhaps the traffic originates from such IP sources that it is a reasonable measure?
Mmmm...
The change of search engine
The change of search engine made me scratch my head.
1. they tell nothing about them self, for example (server location)
2. they do not explain how they do protect their users (are there any logs?)
3. this made me question their relationship with google, since google
aren't exactly known for protecting their users privacy, rather the opposite.
(there we use another search engine then google)
but beside these questions i got in my head. GREAT JOB!
love the circuit, design & security settings.
well done guys, donations will come! keep up the good work!
Does not work (Windows).
Does not work (Windows). When you try to open any website, the app crashes.
Works fine for me. How can I
Works fine for me. How can I reproduce your problem?
Great to see enhanced
Great to see enhanced usability being a priority - thank you!
Is it safe to install
Is it safe to install adblock plus or adblock edge to this version of the tor browser or will it break something and screw me over?
Tor's standard advice on
Tor's standard advice on extra add-ons as I understand it:
1. Add-ons may introduce privacy leaks
2. Even if an add-on is perfectly written and tested to avoid leaks, its effect of selective blocking of web resources from your browsing can help fingerprint you
Regarding (1), the add-ons you mention, Add-Blocks Plus/Edge are written primarily to prevent annoyance of ads. Some privacy may be a partial side effect. The opposite are add-ons to Firefox like Request Policy or the EFF's Privacy Badger (and Tor's included NoScript) which are primarily privacy tools that have a side-effect of blocking many ads.
Another point most people
Another point most people don't understand: Ad-Block and its ilk do not black ads, they simply stop the ads from showing in the browser.
Even so, there is one other
Even so, there is one other point in favor of not blocking ads: prevent even more websites from hating Tor users due to not giving them revenue in ads. We already have enough problems with cloudflare as it is.
On the other hand, if ads are considered an intrusive and faulty part of web browsing, maybe Tor Browser should block them (not just the tracking part, actually prevent them from showing). TAILS has it I think.
Maybe have adblock incorporated into the security slider? As in the top maximum security we could also block ads?
I like your idea about
I like your idea about blocking ads in the security slider. And another point worth looking into is page rendering speed increases that may come with preventing ads from loading.
Feel free to donate to those
Feel free to donate to those sites, I'm not stopping you, but I don't like those parasitic ads or services. If I want to see ads, i'll go watch a NFL game. And don't blame adblock for websites hating Tor, they hate it even without adblock because the mined data is worthless to them. Tor and ad services are mutually exclusive.
So-called cosmetic filter
So-called cosmetic filter rules do what you write: hiding first-party ads and other annoying HTML elements. However, there are also network filter rules that block loading third-party ads. Please read https://github.com/gorhill/uBlock/wiki/Does-uBlock-block-ads-or-just-hi… for more details.
I'm using tbb 4.5a5 and no
I'm using tbb 4.5a5 and no update notice
Works for me on Linux,
Works for me on Linux, Windows and OS X. Do you still have this problem? On which operating system?
I'm excited to try Tor 4.5
I'm excited to try Tor 4.5 out.
sha256sum
sha256sum torbrowser-install-4.5_en-US.exe
is resulting in different sum than https://archive.torproject.org/tor-package-archive/torbrowser/4.5/sha25…
file was downloaded via clear net connection as well as using several exit nodes, the sha256 sums are always the same, but different from one noted in sha256sums.txt.
whats the issue please?
We sign the Windows bundles
We sign the Windows bundles now to get rid of the scary warning that Windows is showing you after downloading the bundle. You need to strip the signature first to check the sha256sum. It is explained here: https://www.torproject.org/docs/verifying-signatures.html.en (first advanced section)
thank you
thank you
Just to confirm I'm reading
Just to confirm I'm reading correctly: The 4.5 series' automatic updater will now have two forms of automatic update protection: HTTPS and verified MAR files? So even if the HTTPS is somehow broken the updater will check that the MAR is properly signed and reject imposter updates?
Yes.
Yes.
Perfect! Thanks.
Perfect! Thanks.
sha256.txt (from
sha256.txt (from https://dist.torproject.org/torbrowser) says:
d8b31cea99a3497f4630a922b4985505bbcb851190de02a2a500fab4193354c6 torbrowser-install-4.5_en-US.exe
my downloads from dist and download/download-easy.html.en
checked with hashmyfiles:
a3219f359bf3f04056a1c8796d103d1bc2e0bd24f181538f70564b3d19532c3a torbrowser-install-4.5_en-US.exe
gpg says 'Good Signature'
Anyone has any ideas why
Anyone has any ideas why this is happening? I have the same problem. Should I go ahead and use the file that i just downloaded, not caring about the mismatch of the signatures?
You mean mismatch of SHA256
You mean mismatch of SHA256 sums, right? See my comment above why this is happening on Windows and what to do about it.
but the documentation
but the documentation doesn't help
on windows remove the signature with delcert.exe f.e.
then compare the hashes
Why does it not help? What
Why does it not help? What would be a better one?
Where did the proxy settings
Where did the proxy settings tab go?
Where are the settings at?
Is there a different SOCKS Host number and Port now?
Is it still SOCKS 5 or something different?
Thank You:)
That tab is hidden now
That tab is hidden now because it was quite confusing and cluttered the user interface unnecessarily. The settings are not changed compared to previous Tor Browser versions.
Is [redacted] the default
Is [redacted] the default entry (guard) relay? [redacted] based IP. Just it always seems to enter Tor thru this IP. Is this by design?
That is your "Guard" node.
That is your "Guard" node. It is by design. See https://www.torproject.org/docs/faq.html.en#EntryGuards.
You should not post that IP publicly, because knowing that IP gives an adversary a lot of ways to deanonymize you. I set a bad example by doing it in the screenshot, but I didn't want to confuse people with a weirdly redacted IP. The IP from the screenshot is not my normal Guard node, however. I would never publish my real Guard like that.
I redacted your Guard IP for you.
is deleting tor's state file
is deleting tor's state file the best (or only?) way to force it to pick a new guard?
I would like to be able to manually add and remove nodes from my guard list without restarting tor and breaking all of my open circuits, via a control port interface, but I haven't found a way to.
Is it possible to choose a
Is it possible to choose a Guard relay yourself?
big :)) yes
big :))
yes
Norton anti virus flags the
Norton anti virus flags the download saying that it is probably a virus. (Not looking for a debate about anti virus software, just thought someone should probably be made aware of this.)
Great work, everyone. My
Great work, everyone. My thanks to you all.
not working on macpro
not working on macpro
Maybe
Maybe https://blog.torproject.org/blog/end-life-plan-tor-browser-32-bit-macs applies to you?
Yeah, nice illustration
Yeah, nice illustration about the available Mac knowledge on older Mac's.
"not working on macpro"
Assuming that you're talking about an older Mac (not the Black Mac Pro).
All Intel Mac's with the right Mac OS X can run 64 bit applications, even the so called 32 bit early 2006 "Core Duo" Mac's (Macbooks for example) can run Firefox in 64 bit mode perfectly well (but not 'clone' Torbrowser).
The alternative advertised (nice illustration of Mac knowledge again), running Tails from USB for example is far from a user-friendly experience : who did get it actually get it to work? I didn't.
I'm really interested in who did on these Mac's (and which usb brands).
I know there must be a lot of people that have this dropped support problem, there still must be a lot of Mac's from that period running. Probably even more in places where people cannot afford newer machines.
Is this a Tails discussion? No actually not because it was advised as an alternative by Torproject. An alternative that is in my opinion not an alternative because it ain't working.
Anyhow, this dropping Mac support discussion is a lost discussion, sad but true.
On a Quad Core (or More Core) Mac Pro you can easily run Torbrowser and also Tails (at least from dvd) as well.
Please make sure you run at least OS X 10.6 on your Intel Mac anyway.
From different perspectives, functionality, 3rd party application support and security reasons this is the minimal OS X you should run on that or any Intel Mac.
The advantage you get is that it will use the 64 bit possibilities and will give you a faster running Mac as well, even on a early 2006 Core Duo Mac.
So, could it be that you're still running Mac OS X Leopard 10.5 or even Tiger 10.4?
Just upgrade to Mac OS X Snow Leopard 10.6 anyhow.
It's just worth it to do that, and if you were not on Snow Leopard yet this could be the cause of your problem because with Leopard you only can run applications in 32 bit mode and the new Torbrowser is 64 bit.
So, with Snow Leopard you can also run applications in 64 bit mode, even on a 32 bit Mac (unless application developers somehow manage to drop support while even mother-Firefox is still supporting it. Still a safe browser on Mac's too).
Beside the critics part, there is also a special thanks part (gotcha) :
The 4.5 alpha version was already great from the beginning.
The definite 4.5 version is even better.
For example, finally fixed the Info Window and Security Information!
Very good job,
yes developers, I'm very pleased with that and thank you for that and the many more nice to have improvements.
Hey, When trying to install
Hey,
When trying to install on arch from the aur https://aur.archlinux.org/packages/tor-browser-en/
I get this
==> Verifying source file signatures with gpg...
tor-browser-linux64-4.5_en-US.tar.xz ... FAILED (unknown public key 2E1AC68ED40814E0)
==> ERROR: One or more PGP signatures could not be verified!
==> ERROR: Makepkg was unable to build tor-browser-en
Sounds like an arch linux
Sounds like an arch linux bug. Ask the arch developers?
That looks like one of our signing keys (though with only the keyid it is hard to tell). We have 3 subkeys and one master certification key. See https://www.torproject.org/docs/verifying-signatures.html.en.
AUR packages are community
AUR packages are community contributed so the Arch Developers have nothing to do with this. The AUR package just pulls down the official tarballs and tries to verify the signature, so the signing key needs to be in the user's keyring, or the verification step will fail.
This is documented in the deep dark most secret depths of the Arch Wiki: https://wiki.archlinux.org/index.php/Tor#Web_browsing
There's also a way to get makepkg to skip checking PGP signatures (not recommended), hidden in the man page, but who has time to read documentation?
Hey, can you just import the
Hey,
can you just import the key?
gpg --recv-keys 416F061063FEE659
This is for vidalia as it had the same problem, after I imported the key everything went smoothly. Also why has support for vidalia stopped?? It was so easy to use and make relays.
Same issue
Same issue
Disconnect is actually
Disconnect is actually really cool, great work on everything!
Why did you base it on
Why did you base it on firefox 31.6.0 and not the latest 37.0.2 ????
31.6.0 is the current
31.6.0 is the current "Extended Support Release": https://www.mozilla.org/en-US/firefox/organizations/
It still receives security patches but no other changes for 9 month intervals. This makes it easier for us to audit Firefox for privacy issues, as well as maintain our 60+ patches without needing to completely rewrite them every 6 weeks.
We will be switching to Firefox 38 (the next Extended Support Release) this summer.
Please change disconnect to
Please change disconnect to searx.
Disconnect is developed by man who's woked in Google.
I don't want to deal with google.
https://searx.me/
Hrmm. According to
Hrmm. According to https://github.com/asciimoo/searx/wiki/possible-search-engines, searx already uses Disconnect on the back end, at least for some stuff.
I admit searx looks pretty nice as far as DIY search engine projects go, but at the end of the day it is just another one hop proxy for other major search engines. It seems like something we could add to the omnibox as an option, though. If you file a ticket with a patch or a search plugin xml file, I'd probably merge it. But I'm not convinced that it is overall a better default option than Disconnect at this point.
Please don't change
Please don't change Disconnect if there are no issues with it as a company. I really like the search results from Disconnect, while search results from StartPage sucked big time.
As a no-cellphone-having
As a no-cellphone-having tor-for-everything privacy vegan, i've got to say: if your distrust of google causes you boycott things just because they're developed by ex-Google employees... wow. good luck finding an operating system!
I wouldn't trust disconnect.me not to track me any more or less than whoever is running searx.me (though with tor, any site's tracking ability shouldn't be able to extend across browsing sessions). If anyone wants to provide a cpatcha-free way to search Google I'll gladly take it.
Unfortunately both searx.me and disconnect.me are giving me lots of non-matching results for an exact-phrase search I just did ("who compiles the compilers") which using Google directly does not.
Searx is appealing because it is free software, of course, but Tor Browser shouldn't switch to any hosted instance of it without ensuring the operator is ready for the quantity of traffic that being the default entails.
New 4.5 version does not
New 4.5 version does not work with HTTP/S proxy, that is bad. Staying at previous 4.0.8.
It seems that socks autenticators are deterministic, not random. It does not isolate streams of different torbrowsers if they surf the same sites.
What do you mean HTTP/S
What do you mean HTTP/S proxy? Where are you configuring this option in 4.0.8?
The SOCKS authenticators don't need to be random. Tor uses them to provide isolation, not to choose which nodes to use. It still chooses randomly among all available nodes, it just keeps the streams on separate circuits if the auths are different.
> What do you mean HTTP/S
> What do you mean HTTP/S proxy? Where are you configuring this option in 4.0.8?
Privoxy for example. Green onion button - Preferences - Proxy Settings - HTTP/SSL Proxy. (Although Edit - Preferences - Advanced - Network - Settings does not apply the options for some cause). I know that this is not the recommended use case, but prefer using HTTP proxy for the sake of statistics (torbrowser does not give detailed log of HTTP-session up to URL) and a separate chrooted Tor daemon which is more secure. I understand that HTTP proxy is quite uncommon option among majority of Tor users, but do not think that it is completely useless and should be excluded.
> The SOCKS authenticators don't need to be random. Tor uses them to provide isolation, not to choose which nodes to use.
Multiple Tor users may be created on the same system so their separate profiles do not interfered. Their traffic can be interleaved over different SocksPorts, but using IsolateSOCKSAuth instead is more convenient. However If authenticators are deterministic, these system users do not have different chains of nodes when browsing the same sites, and stream isolation is not provided for them in this case.
I think the commenter is
I think the commenter is saying, in the second paragraph, that if you connect multiple Tor Browser instances to the same tor daemon, then tabs with the same urlbar domain on different TB instances will not get isolated circuits; and the commenter proposes adding a unique/random per-TB-instance prefix to the Socks credentials.
Correct, that is what I am
Correct, that is what I am trying to say.
I've 2 questions regarding
I've 2 questions regarding the use of 4.5 version:
(1) After extracting tor-browser-linux64-4.5_en-US.tar.xz, how do I launch Tor Browser using a terminal in Ubuntu?
(2) How can I view real-time logging when using the latest 4.5 Tor Browser?
I wish to see the such a list of messages when connecting to Tor when I am using version 4.5. How do I go about doing it?
Run
Run ./start-tor-browser.desktop --help.
At the bottom, you will see:
Tor Browser Script Options
--verbose Display Tor and Firefox output in the terminal
--log [file] Record Tor and Firefox output in file (default: tor-browser.log)
--detach Detach from terminal and run Tor Browser in the background.
--register-app Register Tor Browser as a desktop app for this user
--unregister-app Unregister Tor Browser as a desktop app for this user
You probably want to run either ./start-tor-browser.desktop --verbose, or ./start-tor-browser.desktop --log. You can also do both at the same time.
I had the same question (and
I had the same question (and surely many other would have it) and was kinda hard to find this answer though (thanks!)... I think it would be good to put this on the main post.
Thanks for the update. But I
Thanks for the update.
But I have a problem with the meek.
It works fine wih windows 8.1,but on another computer with windows 7 ultimate ,the meek doesn't work, the tor stuck in the connecting screen.And other things like obfs4 seems to work
Is it just me or something is wrong?
What does the tor log say?
What does the tor log say? After it fails to connect, there should be a button that offers to copy the log to the clipboard. From there you can paste it into a text program and see what it says. If you see a line like this:
We were supposed to connect to bridge '0.0.2.0:2' using pluggable transport 'meek', but we can't find a pluggable transport proxy supporting 'meek'. This can happen if you haven't provided a ClientTransportPlugin line, or if your pluggable transport proxy stopped running.
If you see a line like that, something is wrong, and you can help us by opening a ticket on the bug tracker.
While it is trying to connect, open the Windows task manager and see if you have processes named meek-client-torbrowser.exe and meek-client.exe.
We can help you debug this. It will help if you can open a ticket. Create an account at https://trac.torproject.org/projects/tor/register and then make a new ticket at https://trac.torproject.org/projects/tor/newticket.
thank you for the reply.
thank you for the reply. unfortunately my problem goes on. there is no process as meek-client-torbrowser.exe or meek-client.exe. I'm going to use the bug tracker.
The ticket is
The ticket is https://trac.torproject.org/projects/tor/ticket/15872.
Sorry to put it over this
Sorry to put it over this channel, have no account on the mailing list.
Apparantly jeffstorrelay $A1BF187A0DCC05EFC6EC08667E69AF8CC9DB1E81 tried to degrade a SSL connection to a server. Connection was not possible due to incompatible ciphers. After changing the exit node the connection was possible as it has been many times before.
I got to say that this 4.5
I got to say that this 4.5 version is a very good release due to all the new updates and improvements!
Thank you very much. Great
Thank you very much. Great work
It's good and all we know
It's good and all we know the exact IP addresses of the circuits but how exactly is this done? Without the relay knowing which node is what?
It shouldnt be possible for a user to know all the circuits in the circuit right? other than the entry/exit not the middle node? Or am I missing something
I dont want to be a target in the future just because somehow a relay might know which node is connecting to which.
Torbutton is asking your
Torbutton is asking your local Tor client about circuit information and your local Tor client is giving that information back. It needs to know this (= the guard, the middle and the exit node) as it is building the circuit in the first place. This all happens on your computer and the relays themselves are not involved in selecting a path through the Tor network.
I love your Work but your
I love your Work but your priority should be to enhance security with stronger encryption. Thats THE main Tor's weakness.
there is more and more abuse of power even in "free" countries like France. Tor have to react.
No matter what algorithm you
No matter what algorithm you use, if an attacker controls both Entry and Exit node then you're deanonymized.
What Tor needs is to attract more people who are willing to run Exit-nodes.
Tor users need to find trusted friends who live in free counties and are willing to run a private bridge for the censored friend.
sure, and that's why i use a
sure, and that's why i use a bridge in a trusted country ( we never cant be 100% sure..) and blacklist some exitnodes .
I really dont understand why Tor doesnt take the encryption problem seriously.
I suppose central agency can decrypt tor today, the NSA anyway, so if your enemy know the right person, tor become useless.
Excuse me, encryption is the
Excuse me, encryption is the only thing that Tor always have been doing really well.
Encryption have for some time now been a well understood technology, and the thing easiest to get right and secure in an anonymity solution. Even today when Tor have improved a lot in other areas which they used to ignore during the pre-TBB time, I feel confident that encryption is still the hardest thing to break in Tor.
Encryption is indeed the
Encryption is indeed the hardest thing to break in Tor for THE PUBLIC.
Have been getting a Click
Have been getting a Click jacking warning when trying to complete a captcha on a file host.
Happens when trying to enter the text and again when trying to copy / paste the jumbled text from one box to another.
Never got such a warning in previous versions
For example: set highest
For example: set highest security level or forbid Javascript globally in the NoScript settings, then load a Cloudflare-protected page like
https://support.cloudflare.com/hc/en-us/articles/203306930-Does-CloudFl…
When you start typing the captcha, you'll get a ClearClick alert from NoScript and have to unlock the input field to complete the captcha.
BTW: If Javascript is allowed, Cloudflare generates a simpler captcha that doesn't trigger a ClearClick alert.
Question is Why ? Is it a
Question is Why ?
Is it a bug ?
Is it just a false positive ?
And what's changed in NoScript since previous version where I never saw any clear click warning on anything I clicked.
Yes, it happens to me too.
Yes, it happens to me too. As you say, this didn't happen on any previous versions.
Does gk have an idea why it is happening now, and how to solve this 'problem'.
Thanks
Yes, this happens to me
Yes, this happens to me too.
It's a bit inconvenient.
Does anyone know why it is happening now - 4.0.8 was fine.
Any ideas how to solve the problem?
This is a regression which
This is a regression which seems to be caused by a weird interaction with a different bug fix. See: https://trac.torproject.org/projects/tor/ticket/14985 for details. We hope to get that one fixed in the next point release due in about a week.
"...menu now provides
"...menu now provides information about the current Tor Circuit in use for a page, and also..."
Fantastic. First step in the right direction like Vidalia -with all features- was.
And in TAILS this is a PROBLEM cause of integration in browser??
I haven't seen the new 4.5.
Is info about Crypto algorithm and Media Info
reintegrated or is there something special not?
Thanks for your efforts. In
Thanks for your efforts. In theory, Tor Browser 4.5 is a very great browser. But I have some issues plaguing me.
All provided Bridges Functions didn't work after upgrading to 4.5.
flashproxy, fte, fte-ipv6, meek-amazon, meek-azure, obfs3, obfs4, scramblesuit.....all died.
I saw the Pluggable Transports working through my system monitor, but all shut down automatically within a few seconds.
Now I have to enter my custom bridges manually.
Another issue, the tor onion menu sometimes displayed but sometimes not displayed.
I have tried it in both of my two computers (WinXP & Win7), but same outcome.
I am not a new user to Tor Browser. But I don't know how to solve these issues. Anyone can help? Thanks!
obfs4 works fine here, on
obfs4 works fine here, on Windows 7
Oh, my god. People who are
Oh, my god. People who are living in heaven will never understand hell. I'm living in the region occupied by an evil red regime. All universal values are invalid here. We don't have a normal internet but a very very fu*king big and powerful intranet. So, Tor and Bridges to Tor, and or meek are very important for me. Please optimize the Bridges Function. Thank you very much.
??? I was commenting that
???
I was commenting that obs4 isn't broken, which is what the original message seemed to suggest.
How about you tone down the drama a bit?
I'm so sorry. Perhaps, we
I'm so sorry. Perhaps, we have misunderstanding with each other's words.
I meant that maybe the bridges function (especially meek) in new version 4.5 was being blocked by the GFW.
I am very helpless. I need technical supports to solve this issue.
Thanks!
There was a meek bug
There was a meek bug affecting windows users: https://trac.torproject.org/projects/tor/ticket/15872. Maybe you hit that one. It should be fixed in the next release.
Are you sure that
Are you sure that the
https://dist.torproject.org/torbrowser/4.5/sha256sums.txt
file is showing the correct sha256sums ? cause when I download:
https://dist.torproject.org/torbrowser/4.5/torbrowser-install-4.5_en-US…
instead of sha256sum of:
d8b31cea99a3497f4630a922b4985505bbcb851190de02a2a500fab4193354c6
I get a different sum. What should I do?
run f.e. delcert.exe first
run f.e. delcert.exe first
I assume you were referring
I assume you were referring to the sha256sum of torbrowser-install-4.5_en-US.exe?
If you're using the Windows version of Tor Browser 4.5, may I suggest that you also use gpg4win to verify the signature of that software.
This is what I did after reading your above post:
Using gpg4win, I verified that Tor Browser 4.5 (Windows platform) had not been tampered with.
However my computation of the sha256sum of torbrowser-install-4.5_en-US.exe is a3219f359bf3f04056a1c8796d103d1bc2e0bd24f181538f70564b3d19532c3a
which is different from the one published in https://dist.torproject.org/torbrowser/4.5/sha256sums.txt
Perhaps mikeperry, arma or erinn would like to explain the discrepancy?
Windows bundles are signed
Windows bundles are signed now using the authenticode method to avoid scary warnings if you try to run the installer after downloading it (or in some cases to be able to run the installer at all). This signing happens after the build and thus changes the SHA256 sum. In order to use the advanced verification method outlined on https://www.torproject.org/docs/verifying-signatures.html.en you have to strip that signature off first. One tool mentioned there doing this is osslsigncode. There might be other tools which are easier to use for Windows users though.
i would like to know..tor
i would like to know..tor
"Update Tor to 0.2.6.7 with
"Update Tor to 0.2.6.7 with additional patches: "
Does this mean Tor 0.2.6.7 is now stable and can be compiled from source and used?
Another thing.. Don't you think that the default search engine for Tor Browser should be DuckDuckGo over its Hidden service? This makes more sense than Startpage.
In terms of search results,
In terms of search results, Disconnect is far better than DuckDuckGo, as it uses Google, while DuckDuckGo does not. I for one am really happy with Disconnect, so much so I made it the default search engine for my non-Tor Browsers like Chrome and Firefox.
It makes no sense (to me) to use a search engine simply because it has a hidden service, if the search results are poor.
DDG is terrible results and
DDG is terrible results and questionable security. Disconnect is very good so far much better than startpage.
DDG search results are quite
DDG search results are quite good, often better than those from Startpage. What surprised me is that a direct search at Google sometimes gave me results than I did not get by searching over Startpage.
DDG is better than
DDG is better than StartPage, but both are far worse than Disconnect. And I wouldn't call DDG results "quite good."
On Windows, the privacy and
On Windows, the privacy and security settings screen doesn't show any description for the current security level unless I change it
Update, this only happens
Update, this only happens when javascript is disabled
I guess what happens is that
I guess what happens is that you don't use the security slider to disable JavaScript (i.e. set its mode to "high"). In this case you are using the slider's custom mode (the "Custom Values" checkbox should be checked now) which results in no descriptions.
Has Transparent Torification
Has Transparent Torification mode been deprecated?
It sure looks like it. Do
It sure looks like it. Do you know a workaround? mikeperry? Anyone?
It does not. Just the UI is
It does not. Just the UI is not visible anymore. All the relevant settings should still be working. You probably need to configure everything via about:config now.
Tor Browser > Edit >
Tor Browser > Edit > Preferences > Advanced > Network > No proxy
(
export TOR_SKIP_LAUNCH=1; <i>path-to-tor-browser-dir</i>/Browser/start-tor-browser --verbose)Quick and dirty about:config
Quick and dirty about:config method floods Browser Console with errors (i.e.
originalProxy is nullindomain-isolator.js) though.or instead, set
or instead, set
TOR_TRANSPROXY=1before launchsee
see also:
[geshifilter-code]https://groups.google.com/d/msg/qubes-users/FXgO2cB8qxs/vmNqiPDs0YoJ[/g…]
On April 21st, 2015
On April 21st, 2015 Anonymous said:
When I drag text from Kwrite, if the character is Chinese, to the text field of Tbb 4.5a5, the copy one is going to be an unrecognized symbol.
Plus, dragging Chinese text from Knotes to both Tbb 4.5a and 4.08 is also effected.
reply
Yes here the same, if the
Yes here the same, if the download file name is Japanese.
Does this work? apt-get
Does this work?
apt-get install tor-browser
I am currently using TBB
I am currently using TBB 4.0.8; and usually, i have been noticed about a new update.
However, TBB has not shown an notification about the 4.5 update. Is this normal?
In this case, yes. We are
In this case, yes. We are waiting with an in-browser update for about one week to see whether everything is really working as expected.
re attack surface area why
re attack surface area
why not have a means to disable frames? 90% of the time they merely exist to let me know how many likes (and let facebook know that i've been there and elsewhere)
Could you explain about font
Could you explain about font features disabled
If you hover over the
If you hover over the description then you get the details. Currently we disable SVG OpenType and Graphite font rendering.
Fedora 20, downloaded using
Fedora 20, downloaded using 'torbrowser-launcher', it fails with "SIGNATURE VERIFICATION FAILED!", and on the command line:
gpg: Signature made Tue 31 Mar 2015 10:35:12 AM EDT using RSA key ID D40814E0
gpg: Can't check signature: public key not found
I have no idea why it is downloading the 4.5a5 version today when you say above in the blog post that you are not releasing 4.5 to public consumption in this week. I try to get and verify the file myself (after importing the correct key manually to my keyring using your instructions at www.torproject.org/docs/verifying-signatures.html.en):
gpg --verify sha256sums.txt.asc tor-browser-linux64-4.5a5_en-US.tar.xz
gpg: Signature made Tue 31 Mar 2015 10:35:12 AM EDT using RSA key ID D40814E0
gpg: BAD signature from "Tor Browser Developers (signing key) "
"BAD signature"? I got this all three times I tried cleaning and re-downloading, even with another user on the system.
Minor bug on the resizing
Minor bug on the resizing feature, on Windows, right after starting Tor Browser or clicking new identity and before it is fully loaded and resized if I minimize the window by clicking the tray bar icon, the window disappears and doesn't come back again
I go to
I go to https://bridges.torproject.org/bridges?transport=obfs4 to get my bridges like I normally would, and I get a message saying that there are no bridges available at the moment and that I should try later, why???
https://trac.torproject.org/p
https://trac.torproject.org/projects/tor/ticket/15866 might be the reason.
I notice that while using
I notice that while using tor 4.5 and opening a normal browser the normal browser sometimes lost internet connection.
Great Update. But i have an
Great Update. But i have an issue. The download window doesn't get updated anymore. Downloads appear but the download rate and the transferred amount isn't updated every few msec. Only pressing F5 updates the window.
When i move the button for the download window to the toolbar it doesn't work in this version.
I am on Windows 7.
This is probably
This is probably https://trac.torproject.org/projects/tor/ticket/13579.
Sometimes Tor Browser 4.5
Sometimes Tor Browser 4.5 doesn't show circuit in the Onion menu.
I see all menu, but no circuit related information.
Yeah, I got the same issue.
Yeah, I got the same issue. The Onion Menu just appeared at the first and second time after installation. But I never see it so far.
That might be the case
That might be the case because you are loading an internal page which does obviously not involve a Tor circuit. But hard to say without having an example which fails.
Same problem here. Whether
Same problem here. Whether or not the Tor circuit is shown is hit and miss. I can find no pattern to it. Very frustrating. To me it's important to look at the circuit. One time all three servers showed being in the same country. BUT I CAN'T ALWAYS FIND OUT.
Flash proxy doesn't
Flash proxy doesn't work.
30.04.2015 22:14:15.493 [NOTICE] DisableNetwork is set. Tor will not make or accept non-control network connections. Shutting down all existing connections.
30.04.2015 22:14:15.493 [NOTICE] Opening Socks listener on 127.0.0.1:9150
30.04.2015 22:14:17.430 [NOTICE] Bootstrapped 5%: Connecting to directory server
30.04.2015 22:14:17.431 [NOTICE] Bootstrapped 10%: Finishing handshake with directory server
30.04.2015 22:19:17.430 [WARN] Problem bootstrapping. Stuck at 10%: Finishing handshake with directory server. (DONE; DONE; count 1; recommendation warn; host 4D6C0DF6DEC9398A4DEF07084F3CD395A96DD2AD at 0.0.1.0:1)
30.04.2015 22:19:17.430 [WARN] 1 connections have failed:
30.04.2015 22:19:17.430 [WARN] 1 connections died in state handshaking (TLS) with SSL state SSLv2/v3 read server hello A in HANDSHAKE
Did you follow the steps at
Did you follow the steps at https://trac.torproject.org/projects/tor/wiki/FlashProxyHowto? They are necessary in order to use flash proxy.
Wait, you're giving people
Wait, you're giving people the option to activate Flash???
I think even listing the "privacy settings" is a mistake. Just a chance for uninformed or unfocused or tired people to accidentally turn Tor Browser into Internet Explorer.
Human error exists, why do you encourage it??
Flashproxy != Flash (plug
Flashproxy != Flash (plug in). Assume that's what you've mixed up here ?
Would it be possible to
Would it be possible to integrate the "fake readout" functionality of CanvasBlocker https://addons.mozilla.org/en-US/firefox/addon/canvasblocker/ in Tor Browser, maybe in one of the higher security levels? That would avoid the annoying canvas warning doorhanger
Thx for big update! You are
Thx for big update! You are the best!
There is a problem with the new search engine disconnect. You click on the search result, target site see your https-referer (http not). The exact result is not in plain text, still a problem?!
Example:
Use disconnect and search for https://referer.rustybrick.com/
Then click on it. See the result.
Test done with Tor 4.0.8. (Win)
One of the best improvements
One of the best improvements is the isolation of different tabs. However I would like to know if there is anything else to be further isolated for the tabs to look like from different browser windows, for example are cookies isolated between tabs, whether as first party or third-party? What happens to the connections of addons, does the downloads of DownThemAll get isolated as well or could such addons even get correlated with the connections from browser tabs?
First, there is no tab
First, there is no tab isolation. What is happening is that different things (like circuits, caches, DOM storage etc.) are isolated to the URL bar domain. (Eventually this will happen for cookies as well but we are not there yet.) This means having google.com open in two tabs would send all requests over the same circuit using the same parts of the cache, the same parts of the DOM storage etc.
Then there are things like update checks of extensions or downloading extensions via the add-on manager in the browser that don't have a URL bar domain: they get put onto an own, different circuit currently.
We are currently reworking our Tor Browser design document (https://www.torproject.org/projects/torbrowser/design/) which should have all the details shortly.
If you open a new second
If you open a new second window, are the cookies and more separate to the first window?
Does this mean that it's more private if you use two windows over two tabs in one window? thank you.
No and no. As I said the
No and no. As I said the isolation is neither tab nor window based: solely the URL bar domain matters.
Got a tor browser warning of
Got a tor browser warning of someone hack attempting to make me click a link. I never saw this feature before. I closed tor immediately
In some page always Noscript
In some page always Noscript says: Potential clicjjacking.
Is this a error?
This is probably
This is probably https://trac.torproject.org/projects/tor/ticket/14985. We are working on it.
Your tremendous efforts with
Your tremendous efforts with this latest TB v4.5 are fantastic and deeply appreciated!
There are however, two issues that seem troublesome but may or may not be intended temporary or permanent design features ...
1) The NoScript Whitelist does not seem to be working properly because Whitelisted items seem to disappear randomly for unknown reasons and must be constantly re-added.
2) As a few others have noted in the comments above, some of the provided bridge transport types don't seem to be working. For example, "meek-azure" worked in v4.0.8 and v4.5a5 but, hangs in v4.5.
3) In the TB v4.5a5 options, there was a "TEXT" Applications "Content Type" that allowed the selection of a preferred Action. This was very useful but, seems to be missing in v4.5.
THANKS Again for your dedication!
Problem with downloading
Problem with downloading from cloudflare
V. 4.5:
doesn't work. error message from cloudflare:
"ERROR: Wrong IP. If you are using proxy, please turn it off / Or buy premium key to remove the limitation"
Tried with different IP, same problem. Tried with different security slider (second lowest), same problem. Tried with temporary allow all scripts on this site, same problem.
V. 4.0.8 with temporary allow all scripts on this site: no problem on same file, downloaded it two times on different IP.
So:
- There is a problem with the new security things on 4.5. Or Cloudflare only blocks some tor-exit-nodes. I think it's problem with the new setting things..
Thanks for help
How can I reproduce your
How can I reproduce your problem?
gk, it's me again. Just
gk, it's me again. Just reproduced it with another file, same problem with 4.5.
Try the link I gave you.
Then click on "Download from nitroflare.com"
Now temporary allow all scripts on this site cause of easier captcha, enter it.
Next site: On the left (free download) at the botton click on "slow download". Then it appears a beautiful page with real cloudes. Click on close on the right.
New popup appears, close it. Now you see the name of the file and MB.
Click on free download. it should start a timer from 60s to 0. If this doesn't appear and something like "you can download only in xx minutes) you have to do the same thing again with a new identity. Cause someone had already used this IP for downloading in the last 2 hours.
If you come to the timer 60 to 0 at 0 there is a captcha. Do it. Then "slow download", then "click here for download". And now the problem with 4.5: "ERROR: Wrong IP. If you are using proxy, please turn it off / Or buy premium key to remove the limitation"
With 4.0.8 it it starts the download.
.
Okay, I think you have hit
Okay, I think you have hit https://bugs.torproject.org/15933, too.
ok, thanks again. please
ok, thanks again. please remove link to copyright content above.
Done.
Done.
thanks!
thanks!
How about making 256 bit
How about making 256 bit encryption the default setting when the Security Slider is set to 'high'? I've read 128 bit encryption is Tor Browser's default setting but 256 is available if a client goes into 'about:config' and modifies some settings.
so great,thanks!
so great,thanks!
The new update is just
The new update is just Fantastic. Thanks Tor project for your hard work into Tor browser 4.5. Keep up the good work.
Who has ever heard of
Who has ever heard of Disconnect before ? What reason is there to trust it ?
hello, when i am downloading
hello, when i am downloading a file (for instance a picture) from the net using firefox or the tor browser, it happens quite often that it already exists a file with the exact same filename as the file i'm downloading in the folder where i want to put it. then i have to say "no, i don't want to overwrite the file" and change the filename of the file i'm downloading. my question is if it is possible to make firefox or the tor browser automatically rename files if their filename already exists? (also this specifically to tor browser cause of the "don't add add-ons to tor browser issue" any methods besides installing downthemall or the like) and someone might pass this issue to mozilla and debian i think. would save me a lot of time:) thanks!
Any ideas, anyone?
Any ideas, anyone?
bad- media.autoplay.enabled c
bad-
media.autoplay.enabled
clipboard.autocopy
clipboard.autocopy is false
clipboard.autocopy is false by default in Tor Browser 4.5
FINALLY we can see our
FINALLY we can see our circuit. Orbot would tell you what relays your traffic went through but not Tor Browser (unless I missed it in some obscure place). Well done.
Can we expect a complete
Can we expect a complete vidalia replacement for tor browser so we can see all relays and all circuits? What about android tor browser? Its pretty poor atm.
A very important security
A very important security update that I hope will be implemented is the following:
Tor Browser could make sure that the relay pair(Entry, Middle, Exit) aren't from the same country(such as: USA->USA->USA(worst case), USA->Russia->USA(just as bad), USA->USA->Russia(bad)).
Another would be making sure relays aren't from same region. Such as Europe->Europe->Europe. It would be best like: Europe -> Anything -> Asia.
Another thing would be checking from which jurisdiction you're at and from that choose which would be best entry.
For example, if you're from Europe or USA then you choose Entry as Asia or Russia.
The first part seems like a
The first part seems like a good idea to me but I'm no expert. Anyone with knowledge think this would increase anonymity and security?
I agree. Especially since
I agree. Especially since the "Show Circuit" feature doesn't work consistently. The user should have SOME choice about countries to avoid or not to double up on. Using the same country for all three servers never seemed like a good idea to me. You do not know who runs the servers. There's no guarantee that three servers in three different countries aren't jointly "coordinated", but allowing the user to force servers from different jurisdictions seems like a good idea to me.
Has there ever been a Full
Has there ever been a Full Changelog longer than the Changelog for Tor Browser 4.5?
There are a serious issues
There are a serious issues with recaptcha from google.
Google has changed the recaptcha system from text to images, but with tor browser we cant see the images to solve the captcha.
I tried disable Noscript and HTTPS and nothing
I can't believe I can only
I can't believe I can only find one complaint about this.
GUYS I ALSO HAVE THIS ISSUE.
THIS IS MAJOR ISSUE
I cannot login to websites using Google Recaptch ever since they changed it. I am just stuck. HELP!! Damn how can I display this damn Google Recaptcha. The old ones from Google worked fine, but this new one with Image selection doesn't work with TOR!!!!!
Major issue, non-workable
same for me.. very sad
same for me.. very sad
damn thing!!! google new
damn thing!!! google new reCAPTCHA made a change a few days ago.
TOR can no longer work with google new recaptcha.
Makes it non-usable
I am a newbie to TOR, I
I am a newbie to TOR, I started with 4.0.7 and Vidalia which I still use with 4.5 as it gives me more information than the new "Tor circuit information...".
I know that you do not maintain Vidalia but I would appreciate your comments on the following warning message I just got: "Potentially Dangerous Connection! - One of your applications established a connection through Tor to "127.0.0.1:443" using a protocol that may leak information about your destination. Please ensure you configure your applications to use only SOCKS4a or SOCKS5 with remote hostname resolution."
I am rather confused since I have not specifically configured and application.
Any informastion would be welcome.
Thanks
I too, still use Vidalia and
I too, still use Vidalia and have gotten that warning. And I've seen a few queries elsewhere on the net. But no actual answers. I know the Tor project doesn't support the continued use of Vidalia, but the thing is, I don't the problem is Vidalia-related. That makes it even more curious that no one has even addressed your query, going on nearly 2 months.
whilst viewing a forum I
whilst viewing a forum I accessed through Hidden Wiki via TOR, a window popped out from the no-script feature of TOR and advised me to press the image in the pop-up window to avert a skipjack play!
I did but nothing happened so I pressed the URL in the pop up window and the original forum window became accessible again but slightly different with the same info!
I had set the TOR 4.5 setting to the max in security so i was a bit surprised about this!
prior to accessing the forum I had set the "about;config" to kill any java access by the program
is there anything to concern about this - I am a bit bemused as to what the whole thing was about !!
Probably an instance of
Probably an instance of https://bugs.torproject.org/14985 which should be fixed in 4.5.1.
Great stuff, loving the
Great stuff, loving the constant and cosistent updates/patches!
I really upgraded from 4.08 to 4.5 TBB but when I go to the addons menu, it gives me an error:
XML Parsing Error: undefined entity
Location: about:addons
Line Number 359, Column 15:
How can we reproduce this?
How can we reproduce this? Did you try that with a clean, new Tor Browser 4.5 as well?
Yep, it seems when
Yep, it seems when installing over a older version, tor doesn't even get updated (even though installation is successful) and causes problems like this. Completely New installation doesn't have this problem
Hi, I have the same issue
Hi,
I have the same issue after disabling TorButton plugin. Is it connected something to this? Thanks.
What is the status on using
What is the status on using Enhanced Mitigation Experience Toolkit? Is it safe to use with TBB on Windows? I know it's created by Microsoft and it's closed source so what are the possible negatives as well as positives from using this?
It is currently not working
It is currently not working well with Tor Browser: https://bugs.torproject.org/13893.
Is it safe to keep browser
Is it safe to keep browser and form history when using TBB? Are there any problems associated with doing this?
I'd also like to know this,
I'd also like to know this, anyone?
It seems Adblock Edge is
It seems Adblock Edge is gonna get discontinued in June. Is it ok to use µBlock, its successor or no?
Why do you think Adblock
Why do you think Adblock Edge is particularly safe to use in TorBrowser in the first place?
Would enabling bridges in
Would enabling bridges in TBB add more security/anonymity to the browser or is it worse than default connection settings?
Super release 4.5! One
Super release 4.5! One question: how would changing TBB's user agent to a default firefox/chrome affect anonymity/fingerprinting?
We are using a default user
We are using a default user agent, that of the Firefox ESR we base Tor Browser on. We choose the Windows one for fingerprinting reasons, though.
Would it help with reducing
Would it help with reducing fingerprinting if we changed the user agent to the one in the default mozilla firefox browser instead of the ESR?
Much slower IMO. But thanks
Much slower IMO.
But thanks for the hard work.
When can we expect an
When can we expect an automatic upgrade from 4.08 to 4.5, and is it safe to use 4.0.8?
Next week will be an
Next week will be an automatic update available to 4.5.1 and yes 4.0.8 is still safe.
Thanks for your excellent
Thanks for your excellent work, I really appreciate the Tor Browser and the work you do. There is too much censorship in England - blocking of sites due to copyright, surveillance, and draconian porn laws.
Strange behavior : Cross
Strange behavior : Cross browser remembering page search info
I already noticed for a while (some versions) that search keywords are not cleaned. The keywords you can type below if you search for certain words in a webpage.
If you choose a new identity or even close the browser and startup again, if you open the search (page) window you'll see that old keyword again.
That could maybe compromise your local privacy a bit (depending on the keyword).
Then I was slightly wondering if a script on a website even could read one way or another that keyword as well. Because if you don't clean that field you'll take that information with you to every website you visit, leaving some sort of a track behind you (if website owners managed to read that information that keyword or even phrase Torbrowser is storing).
It's even getting better (worse) now because I discovered that it even goes further then that. Just had the strange experience that the keyword could not be erased anymore, it just came back, could only replace it by something else but not leave the search field empty anymore, and to my surprise finally that it even showed up in another normal Firefox browser where I also could not clean that same keyword appearing again!
If a keyword even can sho up in a normal Firefox version, then it maybe could really directly compromise your identity if a website could read that information (yes, you should visit the same page with a normal browser and sometimes with Torbrowser, but maybe some people do in some cases?).
Okay (not), I took another fresh Torbrowser installer and installed a fresh Torbrowser on my desktop. Opened it, looked for the keyword field and there was the same last word I typed in the old Torbrowser/Firefox browser again.
Took another fresh Firefox, the same word was there also again.
Tried it with other non-mozilla browsers, no keywords given.
Went to another user account, opened a Firefox browser, no keyword.
So it was a user account related and mozilla browser related problem.
Now, this behavior of not cleaning a keyword and even taking it with it to a normal Firefox browser and not being able to clean the search word (a dot, number or even an empty hit of the space bar) is in my opinion a bit alarming.
I think that means that some persistent information is/or was stored outside Torbrowser (why?), somewhere in a related mozilla directory where it does not get/or cannot be cleaned and is eventually used by every mozilla browser you open in that account.
I did have to do a serious system (caches etc.) clean up in safe boot modus to get rid of this persistent keyword storage problem since I did not know exactly where to look for cleaning this behavior.
(For the humorous people, it wasn't a special word, just a normal search on a normal page, no malware expected overthere. Browsers startup in safe modus did not help either).
Do other users have seen or experienced this kind of behavior of persitenly remembering the page search word as well?
Torbrowser version I was using 4.5 on a Mac.
Remembering the keyword after renewal or browser restart was already there in older Torbrowser versions. Cross browser remembering looks like new behavior.
Thanks for the attention.
how to decript file ?
how to decript file ?
It's been a week, but the
It's been a week, but the auto-updater doesn't seem to be working.
Running Tor Browser 4.0.8 on Windows, using the updater in Help -> About Tor Browser shows "Tor Browser is up to date" even though it's not.
I could just download the binaries, but I thought this was worth pointing out.
Yes, I think this is
Yes, I think this is intentional.
https://www.torproject.org/projects/torbrowser/RecommendedTBBVersions
They're leaving 4.0.8 as a valid version for now until they iron out a few more wrinkles.
Thank you for the quick
Thank you for the quick response, and all your hard work on Tor. :)
I use http://file2hd.com/ to
I use http://file2hd.com/ to download videos from Youtube over TOR.
With up to and including TOR 4.0.8 everything worked fine. After entering the URL, clicking "I have read and agree to the Terms of Service" and marking "Movies" as the files I wanted I would see (for example):
http://youtube.com/Peter Pop feat Lora Singuri in doi - Low Quality 240p [File2HD.com].mp4
http://youtube.com/Peter Pop feat Lora Singuri in doi - Low Quality 240p [File2HD.com].flv
http://youtube.com/Peter Pop feat Lora Singuri in doi - Standard Quality 360p [File2HD.com].mp4
http://youtube.com/Peter Pop feat Lora Singuri in doi - HD 720p [File2HD.com].mp4
I would then click on the file quality I wanted and the download would start.
However, with 4.5, I still get up to choosing the file quality I want but after clicking on the file the next screen is again the Start screen: asking me to enter the URL, click on " I have read and……." and chose ,for example, Movies. The file I have just chosen does not download. If I fill the details again, the file still does not download, I am sent back to the Start screen again.
Please help.
Thanks
PS thanks for an otherwise excellent piece of work.
This is
This is https://bugs.torproject.org/15933 which will be fixed in Tor Browser 4.5.1 which should get released tomorrow.
What security slider
What security slider position equals the default setting of 4.0.8?
Low, which is the default
Low, which is the default setting in 4.5 as well.
so on 4.0.8 what was the
so on 4.0.8 what was the security level? I am not sure where to have the slider? I mean should I have it at the highest setting when going to onion sites etc, was 4.0.8 technically set on high or low?
Why is TBB "secure" window
Why is TBB "secure" window size when it is used as default? Why not set window size default for all TBB users as full screen, would that not give the same amount of privacy from being fingerprinted?
most max windowsize are
most max windowsize are different.
Yesterday I came across a
Yesterday I came across a plugin called "Disable Plugin & Mimetype Enumeration " which hides your plugins/mimetype from sites. Is this already implemented into TBB or is it okay to just to use this addon?
why hide them? All Users ve
why hide them? All Users ve the same. this plugin makes u unique :(
Is there a bug regarding DNS
Is there a bug regarding DNS lookup?
I have reported above a message (via Vidalia) re a connection made to 127.0.0.1:443.
Today I am getting reports of such connections, not to 127.0.0.1 but to 19X.X6.2X4.21X.
On github (https://github.com/ethans/switchy/issues/455) someone reported the same thing a few days ago.
The final remark from github is:
This is very dangerous because DNS lookup is being done through ISP which is what TOR is informing me of when DNS lookup should be done through TOR
Could GK please respond as a matter of urgency?
Thanks
How can I create a ticket to
How can I create a ticket to file a suspected bug report via https://trac.torproject.org/projects/tor/newticket when I always receive the answer;
TICKET_CREATE privileges are required to perform this operation. You don't have the required permissions.
How do I get the 'required permissions'?
Thanks
Have you tried logging in?
Have you tried logging in? You can either make an account (this is the recommended way if you want to hear about progress on your ticket), or use the cypherpunks account listed on the front page of the wiki.
Arma thanks. I have tried to
Arma thanks.
I have tried to create an account, via TOR, but I just keep getting the response that the page thinks my submission is Spam.
I then try to fill in the Captcha but I never get it right. Even using a magnifying glass to try to 'guess' what the letters are in the captcha, I fail every time.
I can understand the need to guard against spam, but is it necessary to make the captchas so difficult to understand?
Why does Tor only use 3
Why does Tor only use 3 relays as opposed to 4, 5 or more? Which one would provide more anonymity?
You might
You might enjoy
https://www.torproject.org/docs/faq#ChoosePathLength
Can someone explain why i´m
Can someone explain why i´m connecting to the same exact Ip/node every time use tor browser?(the first of 3 ip´s) It has not changed since i downloaded it a couple of days ago.
What if this node is computerized?
I thought the point of Tor was to connect to different nodes every time.
Certificate
Certificate management/validation (repeated question)
1) The standard available option "When an OCSP server connection fails, threat the certificate as invalid" is not activated.
Why not?
2) What could be the reason that if you do activate this OCSP check, that one can experience getting more and more error pages like 'secure connection failed'.
It really seems to increase last several months. A lot of times even directly after startup Torbrowser and trying to connect to a secure webpage.
Does this seem to point at the possible questionable 'quality' of the exit node?
3) Since the beginning of the Alpha version of the 4.5 Torbrowser I did see on a regular basis this mysterious middle node "?? 104.236.37.219" . It seems the only one that's giving this question mark message.
Did you notice/know? What's up with this node?
Thanks for you work <3
Thanks for you work <3
Hello, when i activate
Hello, when i activate menu-bar with "view/toolbars --> menue bar and bookmarks - can someone read or track this changing?
think windosize wont change. can someone tell me plesse
thx 2016
4.5 will not install on my
4.5 will not install on my Windows XP. When I download 4.5 it reaches 34.1 MB and hangs there until Tor Browser asks Zone Alarm for internet access (something I already permitted). When I give it the permission it already had, the download finishes at 34.1 MB though the file is supposed to be 34.2 MB.
When I try to install it it does nothing.
"will be prompted to update automatically by their Tor Browser, while users of the stable 4.0.8 will receive the same prompt in about a week’s time"
I have not received this prompt.
WHAT ARE CONCERNED TOR USERS
WHAT ARE CONCERNED TOR USERS SUPPOSED TO DO.
I have had no response from arma or gk about what may be a bug in the dns lookup of 4.5, so I registered at trac.tor.
I submitted a report but it was rejected as possible spam, probably because I submitted it over TOR!!!
The way to get the system to believe that it is not spam was to 'try' to fill out the indecipherable captcha that I have complained about above.
I tried but, as reported above, I failed.
What am I supposed to do?
DNS look-up Regarding my
DNS look-up
Regarding my recent post on this.
I have just found an old Tor item from 2012:
https://blog.torproject.org/category/tags/dns-bypass
The solution given is:
To fix this dns leak/security hole, follow these steps:
Type “about:config” (without the quotes) into the Firefox URL bar. Press Enter.
Type “websocket” (again, without the quotes) into the search bar that appears below "about:config".
Double-click on “network.websocket.enabled”. That line should now show “false” in the ‘Value’ column.
I have just gone into about:config and have found “network.websocket.enabled”. Should this be set to 'false'.
For the sake of users, could Arma or GK please respond? As I have said, if the trac captures were not so difficult to understand, I would submit a bug report.
Thank you
^Are you the same guy who
^Are you the same guy who wrote the following?
"Is there a bug regarding DNS lookup?
I have reported above a message (via Vidalia) re a connection made to 127.0.0.1:443.
Today I am getting reports of such connections, not to 127.0.0.1 but to 19X.X6.2X4.21X."
"WHAT ARE CONCERNED TOR USERS SUPPOSED TO DO."
ALL TOR USERS AFAIK aren't supposed to use the outdated & non supported Vidalia anymore.
A thousand thanks to
A thousand thanks to mikeperry and the other devs for all their work!
My experience using the Tor Browser version included in Tails 1.4 has so far been inconsistent and confusing, for reasons which are unknown to me and quite possibly independent of the significant improvements in the new browser. My problems seemed to cease when I stopped using the privacy slider and manually reverted to my old (wrong) way of using the browser, among a few other changes, but I am cautiously optimistic that eventually I'll e able to use the slider without experiencing ill effects.
> Are you the same guy who wrote the following?
No.
> ALL TOR USERS AFAIK aren't supposed to use the outdated & non supported Vidalia anymore.
That can't be right, since Vidalia is used in Tails 1.4. If I am wrong, say so because then I must have a bad PGP key, a bad detached sig, and a bad iso image.
hi guys, i have error in my
hi guys,
i have error in my tor browser
Tor failed to establish a Tor network connection.
Establishing an encrypted directory connection failed (done - 0.0.1.0:1).
09/06/2015 10:45:46 a.m..198 [NOTICE] DisableNetwork is set. Tor will not make or accept non-control network connections. Shutting down all existing connections.
09/06/2015 10:45:48 a.m..164 [NOTICE] Opening Socks listener on 127.0.0.1:9150
09/06/2015 10:45:50 a.m..101 [NOTICE] Closing no-longer-configured Socks listener on 127.0.0.1:9150
09/06/2015 10:45:50 a.m..101 [NOTICE] DisableNetwork is set. Tor will not make or accept non-control network connections. Shutting down all existing connections.
09/06/2015 10:45:50 a.m..101 [NOTICE] Closing old Socks listener on 127.0.0.1:9150
09/06/2015 10:45:51 a.m..286 [NOTICE] Opening Socks listener on 127.0.0.1:9150
09/06/2015 10:45:52 a.m..418 [NOTICE] Closing no-longer-configured Socks listener on 127.0.0.1:9150
09/06/2015 10:45:52 a.m..418 [NOTICE] DisableNetwork is set. Tor will not make or accept non-control network connections. Shutting down all existing connections.
09/06/2015 10:45:52 a.m..418 [NOTICE] Closing old Socks listener on 127.0.0.1:9150
09/06/2015 10:45:56 a.m..740 [NOTICE] DisableNetwork is set. Tor will not make or accept non-control network connections. Shutting down all existing connections.
09/06/2015 10:45:56 a.m..741 [NOTICE] DisableNetwork is set. Tor will not make or accept non-control network connections. Shutting down all existing connections.
09/06/2015 10:45:56 a.m..741 [NOTICE] DisableNetwork is set. Tor will not make or accept non-control network connections. Shutting down all existing connections.
09/06/2015 10:45:56 a.m..741 [NOTICE] Opening Socks listener on 127.0.0.1:9150
09/06/2015 10:45:58 a.m..153 [NOTICE] Bootstrapped 5%: Connecting to directory server
09/06/2015 10:45:58 a.m..163 [NOTICE] Bootstrapped 10%: Finishing handshake with directory server
09/06/2015 10:45:59 a.m..729 [NOTICE] Closing no-longer-configured Socks listener on 127.0.0.1:9150
09/06/2015 10:45:59 a.m..729 [NOTICE] DisableNetwork is set. Tor will not make or accept non-control network connections. Shutting down all existing connections.
09/06/2015 10:45:59 a.m..730 [NOTICE] Closing old Socks listener on 127.0.0.1:9150
09/06/2015 10:45:59 a.m..730 [WARN] Problem bootstrapping. Stuck at 10%: Finishing handshake with directory server. (DONE; DONE; count 1; recommendation warn; host 4D6C0DF6DEC9398A4DEF07084F3CD395A96DD2AD at 0.0.1.0:1)
09/06/2015 10:45:59 a.m..730 [WARN] 1 connections have failed:
09/06/2015 10:45:59 a.m..730 [WARN] 1 connections died in state handshaking (TLS) with SSL state SSLv2/v3 read server hello A in HANDSHAKE
he was working properly but derrepente began to show me the error, and try to change the providded bridges in flashproxy, fte,fte-ipv6, meek amazon meek azure, meek google, obfs3 (recommended), obfs4 and scramblesuit but none run,
if any of you could assist me it would be greatly appreciated, my mail if you have any tutorial to solve this failure is steven341992@hotmail.com
thank you very much