New Release: Tor Browser 9.0

Update [7:30 UTC]: Clarified the amount of locales we support. It's 32 with Tor Browser 9.0.
Update [10:45 UTC]: Added a section about letterboxing.
Tor Browser 9.0 is now available from the Tor Browser download page and also from our distribution directory.
This release features important security updates to Firefox.
Tor Browser 9.0 is the first stable release based on Firefox 68 ESR and contains a number of updates to other components as well (including Tor to 0.4.1.6 and OpenSSL to 1.1.1d for desktop versions and Tor to 0.4.1.5 for Android).
In addition to all the needed patch rebasing and toolchain updates, we made big improvements to make Tor Browser work better for you.
We want everyone in the world to be able to enjoy the privacy and freedom online Tor provides, and that's why over the past couple years, we've been working hard to boost our UX and localization efforts, with the biggest gains first visible in Tor Browser 8.0.
In Tor Browser 9.0, we continue to build upon those efforts with sleeker integration and additional localization support.
Goodbye, Onion Button
We want your experience using Tor to be fully integrated within the browser so how you use Tor is more intuitive. That's why now, rather than using the onion button that was in the toolbar, you can see your path through the Tor network and request a New Circuit through the Tor network in [i] on the URL bar.
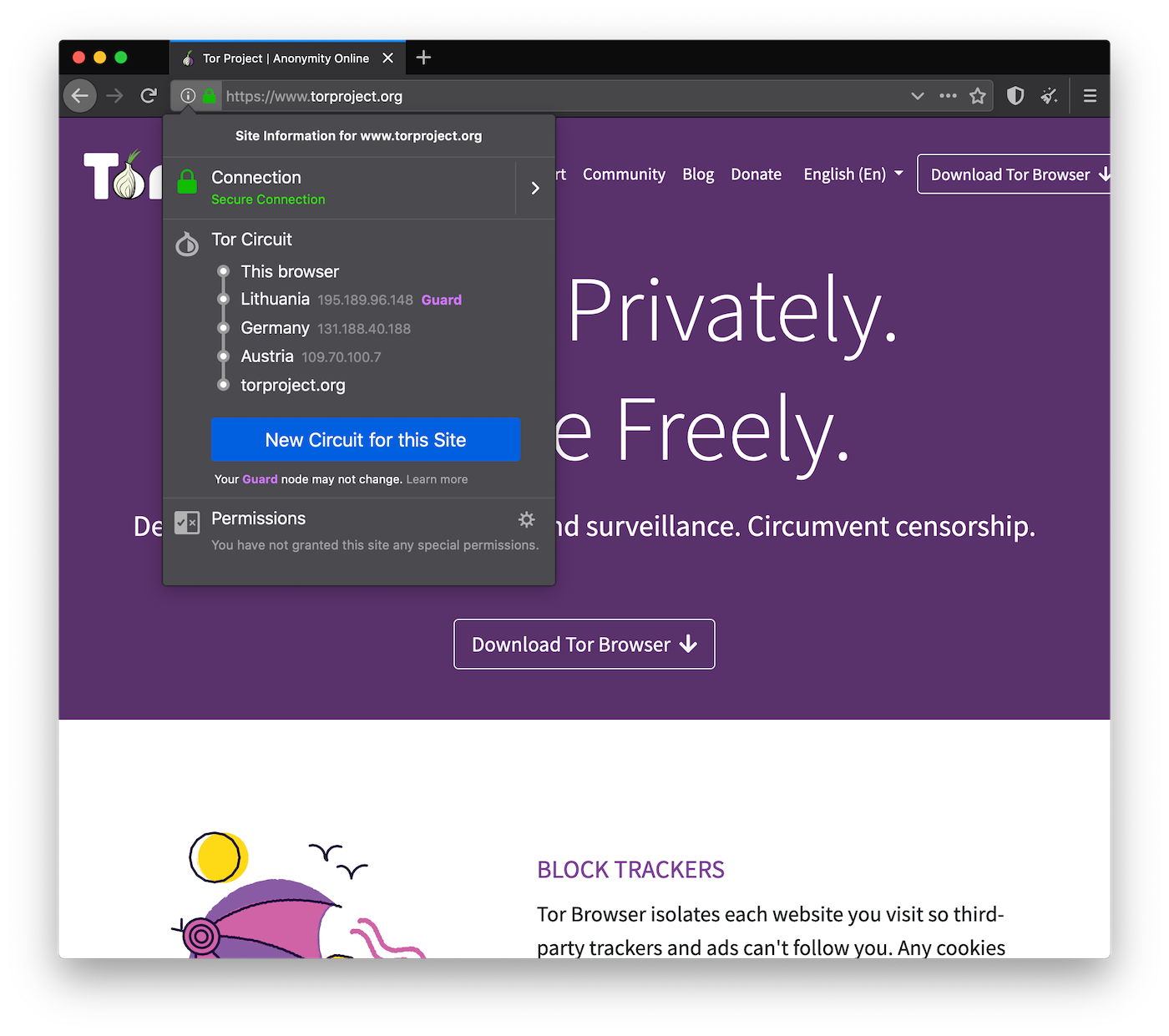
Hello, New Identity Button

Instead of going into the onion button to request a New Identity, we've made this important feature easier to access by giving it its own button in the toolbar.
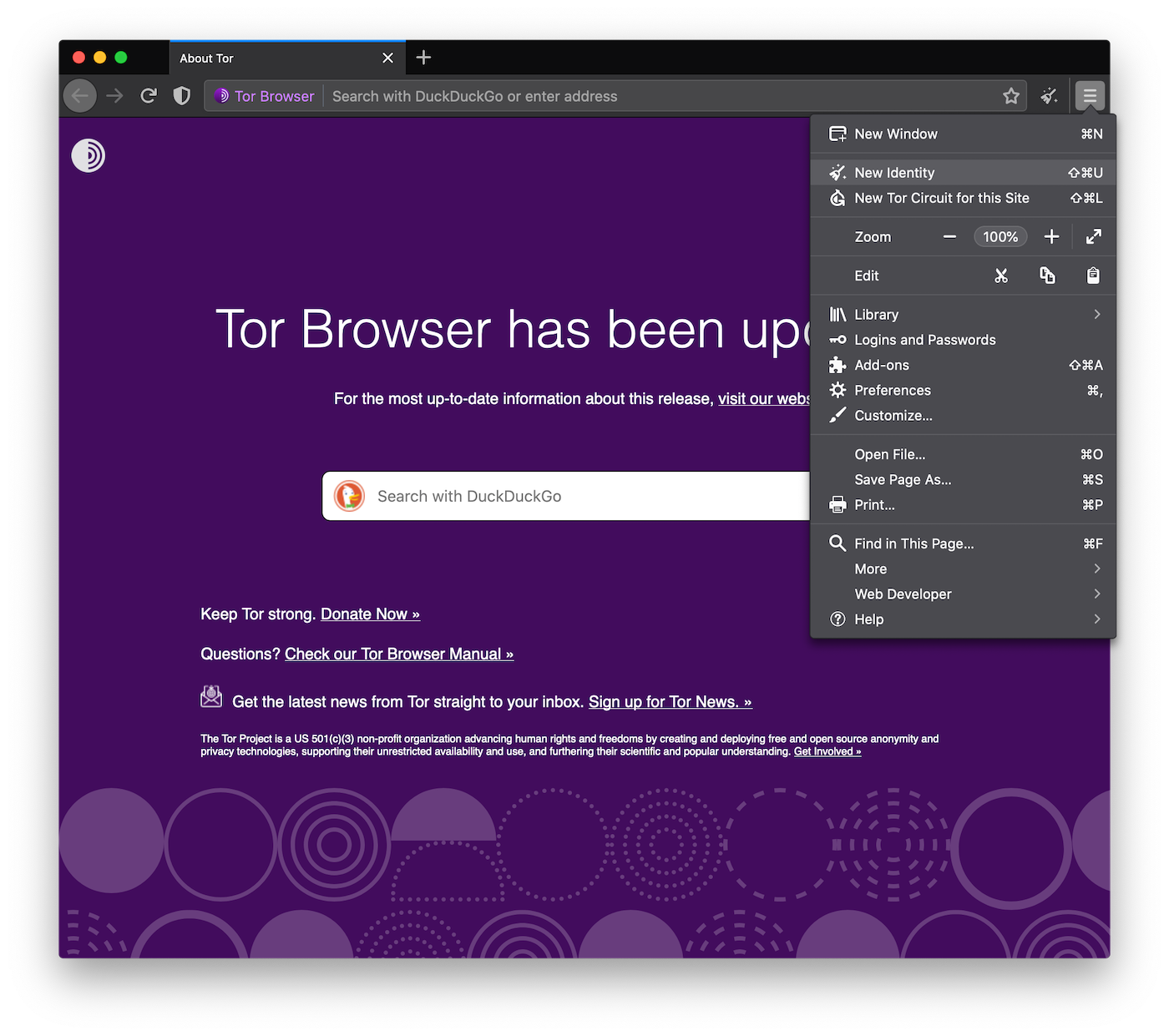
You can also request a New Identity, and a New Circuit, from within the [=] menu on the toolbar.
Torbutton and Tor Launcher Integration
Now that both extensions are tightly integrated into Tor Browser, they'll no longer be found on the about:addons page.
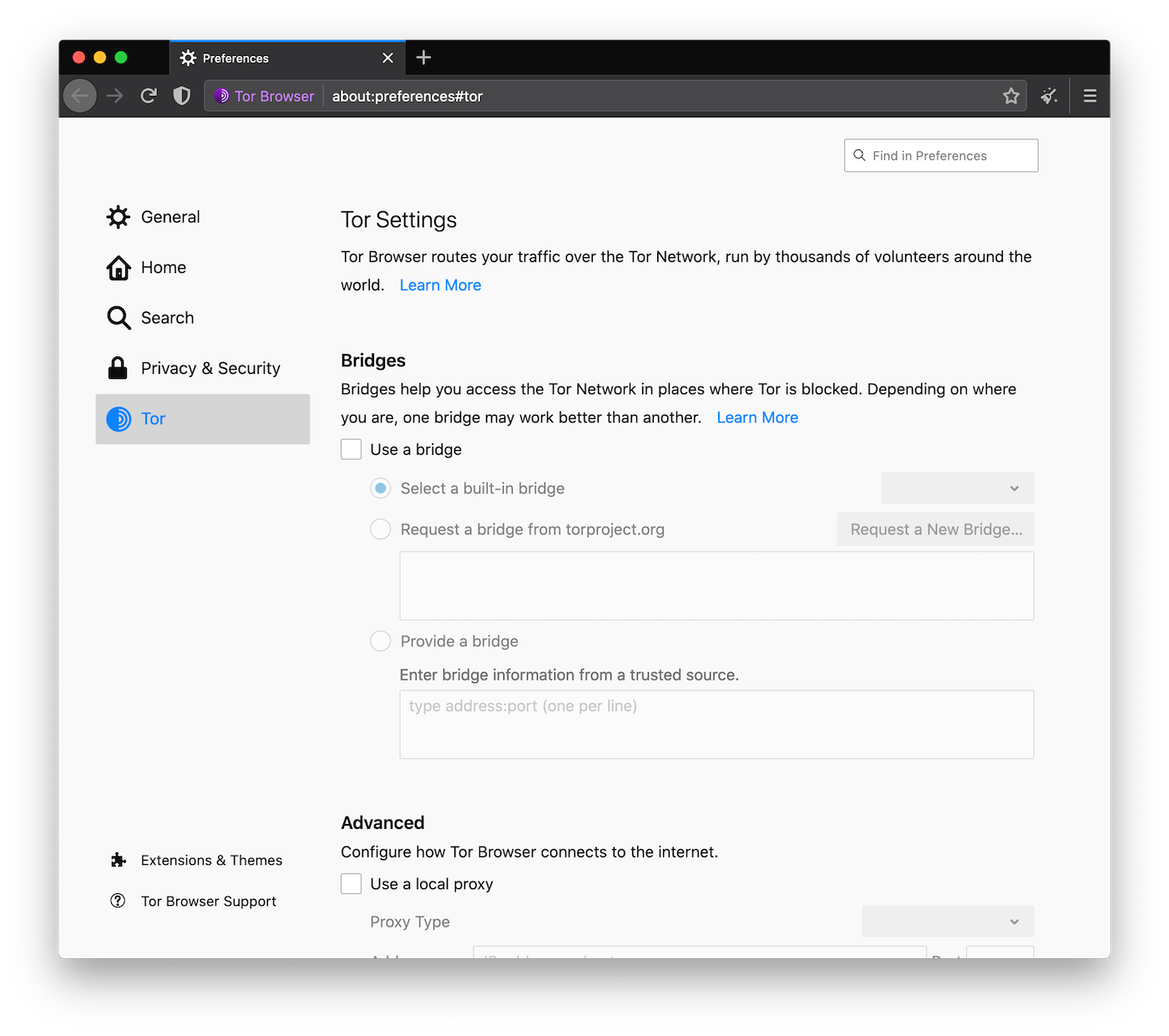
We redesigned the bridge and proxy configuration dialogs and include them directly into the browser's preference settings as well.
Rather than being a submenu behind the onion button, Tor Network Settings, including the ability to fetch bridges to bypass censorship where Tor is blocked, are easier to access on about:preferences#tor.
Letterboxing
Tor Browser, in its default mode, is starting with a content window rounded to a multiple of 200px x 100px to prevent fingerprinting the screen dimensions. The strategy here is to put all users in a couple of buckets to make it harder to single them out. That worked until users started to resize their windows (e.g. by maximizing them or going into fullscreen mode). Tor Browser 9 ships with a fingerprinting defense for those scenarios as well, which is called Letterboxing, a technique developed by Mozilla and presented earlier this year. It works by adding white margins to a browser window so that the window is as close as possible to the desired size while users are still in a couple of screen size buckets that prevent singling them out with the help of screen dimensions.
Better Localization Support
If we want all people around the world to be able to use our software, then we need to make sure it's speaking their language. Since 8.0, Tor Browser has been available in 25 languages, and we added 5 locales more in Tor Browser 8.5. Today, we add support for two additional languages: Macedonian (mk) and Romanian (ro), bringing the number of supported languages to 32.
We also fixed bugs in our previously shipped localized bundles (such as ar and ko).
Many thanks to everyone who helped with these, in particular to our translators.
Known Issue
As usual when preparing Tor Browser releases, we verified that the build is bit-for-bit reproducible. While we managed to get two matching builds, we found that in some occasions the builds differ (we found this happening on the Linux i686 and macOS bundles). We are still investigating the cause of this issue to fix it.
Give Feedback
If you find a bug or have a suggestion for how we could improve this release, please let us know. Thanks to all of the teams across Tor, and the many volunteers, who contributed to this release.
Changelog
The full changelog since Tor Browser 8.5.6 is:
- All Platforms
- Update Firefox to 68.2.0esr
- Bug 31740: Remove some unnecessary RemoteSettings instances
- Bug 13543: Spoof smooth and powerEfficient for Media Capabilities
- Bug 28196: about:preferences is not properly translated anymore
- Bug 19417: Disable asmjs on safer and safest security levels
- Bug 30463: Explicitly disable MOZ_TELEMETRY_REPORTING
- Bug 31935: Disable profile downgrade protection
- Bug 16285: Disable DRM/EME on Android and drop Adobe CDM
- Bug 31602: Remove Pocket indicators in UI and disable it
- Bug 31914: Fix eslint linter error
- Bug 30429: Rebase patches for Firefox 68 ESR
- Bug 31144: Review network code changes for Firefox 68 ESR
- Bug 10760: Integrate Torbutton into Tor Browser directly
- Bug 25856: Remove XUL overlays from Torbutton
- Bug 31322: Fix about:tor assertion failure debug builds
- Bug 29430: Add support for meek_lite bridges to bridgeParser
- Bug 28561: Migrate "About Tor Browser" dialog to tor-browser
- Bug 30683: Prevent detection of locale via some *.properties
- Bug 31298: Backport patch for #24056
- Bug 9336: Odd wyswig schemes without isolation for browserspy.dk
- Bug 27601: Browser notifications are not working anymore
- Bug 30845: Make sure internal extensions are enabled
- Bug 28896: Enable extensions in private browsing by default
- Bug 31563: Reload search extensions if extensions.enabledScopes has changed
- Bug 31396: Fix communication with NoScript for security settings
- Bug 31142: Fix crash of tab and messing with about:newtab
- Bug 29049: Backport JS Poison Patch
- Bug 25214: Canvas data extraction on local pdf file should be allowed
- Bug 30657: Locale is leaked via title of link tag on non-html page
- Bug 31015: Disabling SVG hides UI icons in extensions
- Bug 30681: Set security.enterprise_roots.enabled to false
- Bug 30538: Unable to comment on The Independent Newspaper
- Bug 31209: View PDF in Tor Browser is fuzzy
- Translations update
- Windows + OS X + Linux
- Update Tor to 0.4.1.6
- Update OpenSSL to 1.1.1d
- Bug 31844: OpenSSL 1.1.1d fails to compile for some platforms/architectures
- Update Tor Launcher to 0.2.20.1
- Bug 28044: Integrate Tor Launcher into tor-browser
- Bug 32154: Custom bridge field only allows one line of input
- Bug 31286: New strings for about:preferences#tor
- Bug 31303: Do not launch tor in browser toolbox
- Bug 32112: Fix bad & escaping in translations
- Bug 31491: Clean up the old meek http helper browser profiles
- Bug 29197: Remove use of overlays
- Bug 31300: Modify Tor Launcher so it is compatible with ESR68
- Bug 31487: Modify moat client code so it is compatible with ESR68
- Bug 31488: Moat: support a comma-separated list of transports
- Bug 30468: Add mk locale
- Bug 30469: Add ro locale
- Bug 30319: Remove FTE bits
- Translations update
- Bug 32092: Fix Tor Browser Support link in preferences
- Bug 32111: Fixed issue parsing user-provided bridge strings
- Bug 31749: Fix security level panel spawning events
- Bug 31920: Fix Security Level panel when its toolbar button moves to overflow
- Bug 31748+31961: Fix 'Learn More' links in Security Level preferences and panel
- Bug 28044: Integrate Tor Launcher into tor-browser
- Bug 31059: Enable Letterboxing
- Bug 30468: Add mk locale
- Bug 30469: Add ro locale
- Bug 29430: Use obfs4proxy's meek_lite with utls instead of meek
- Bug 31251: Security Level button UI polish
- Bug 31344: Register SecurityLevelPreference's 'unload' callback
- Bug 31286: Provide network settings on about:preferences#tor
- Bug 31886: Fix ko bundle bustage
- Bug 31768: Update onboarding for Tor Browser 9
- Bug 27511: Add new identity button to toolbar
- Bug 31778: Support dark-theme for the Circuit Display UI
- Bug 31910: Replace meek_lite with meek in circuit display
- Bug 30504: Deal with New Identity related browser console errors
- Bug 31929: Don't escape DTD entity in ar
- Bug 31747: Some onboarding UI is always shown in English
- Bug 32041: Replace = with real hamburguer icon ≡
- Bug 30304: Browser locale can be obtained via DTD strings
- Bug 31065: Set network.proxy.allow_hijacking_localhost to true
- Bug 24653: Merge securityLevel.properties into torbutton.dtd
- Bug 31164: Set up default bridge at Karlstad University
- Bug 15563: Disable ServiceWorkers on all platforms
- Bug 31598: Disable warning on window resize if letterboxing is enabled
- Bug 31562: Fix circuit display for error pages
- Bug 31575: Firefox is phoning home during start-up
- Bug 31491: Clean up the old meek http helper browser profiles
- Bug 26345: Hide tracking protection UI
- Bug 31601: Disable recommended extensions again
- Bug 30662: Don't show Firefox Home when opening new tabs
- Bug 31457: Disable per-installation profiles
- Bug 28822: Re-implement desktop onboarding for ESR 68
- Windows
- Bug 31942: Re-enable signature check for language packs
- Bug 29013: Enable stack protection for Firefox on Windows
- Bug 30800: ftp:// on Windows can be used to leak the system time zone
- Bug 31547: Back out patch for Mozilla's bug 1574980
- Bug 31141: Fix typo in font.system.whitelist
- Bug 30319: Remove FTE bits
- OS X
- Linux
- Bug 31942: Re-enable signature check for language packs
- Bug 31646: Update abicheck to require newer libstdc++.so.6
- Bug 31968: Don't fail if /proc/cpuinfo is not readable
- Bug 24755: Stop using a heredoc in start-tor-browser
- Bug 31550: Put curly quotes inside single quotes
- Bug 31394: Replace "-1" with "−1" in start-tor-browser.desktop
- Bug 30319: Remove FTE bits
- Android
- Update Tor to 0.4.1.5
- Bug 31010: Rebase mobile patches for Fennec 68
- Bug 31010: Don't use addTrustedTab() on mobile
- Bug 30607: Support Tor Browser running on Android Q
- Bug 31192: Support x86_64 target on Android
- Bug 30380: Cancel dormant by startup
- Bug 30943: Show version number on mobile
- Bug 31720: Enable website suggestions in address bar
- Bug 31822: Security slider is not really visible on Android anymore
- Bug 24920: Only create Private tabs in permanent Private Browsing Mode
- Bug 31730: Revert aarch64-workaround against JIT-related crashes
- Bug 32097: Fix conflicts in mobile onboarding while rebasing to 68.2.0esr
- Build System
- All Platforms
- Bug 30585: Provide standalone clang 8 project across all platforms
- Bug 30376: Use Rust 1.34 for Tor Browser 9
- Bug 30490: Add cbindgen project for building Firefox 68 ESR/Fennec 68
- Bug 30701: Add nodejs project for building Firefox 68 ESR/Fennec 68
- Bug 31621: Fix node bug that makes large writes to stdout fail
- Bug 30734: Add nasm project for building Firefox 68 ESR/Fennec 68
- Bug 31293: Make sure the lo interface inside the containers is up
- Bug 27493: Clean up mozconfig options
- Bug 31308: Sync mozconfig files used in tor-browser over to tor-browser-build for esr68
- Windows
- Bug 29307: Use Stretch for cross-compiling for Windows
- Bug 29731: Remove faketime for Windows builds
- Bug 30322: Windows toolchain update for Firefox 68 ESR
- Bug 9898: Provide clean fix for strcmpi issue in NSPR
- Bug 29013: Enable stack protection support for Firefox on Windows
- Bug 30384: Use 64bit containers to build 32bit Windows Tor Browser
- Bug 31538: Windows bundles based on ESR 68 are not built reproducibly
- Bug 31584: Clean up mingw-w64 project
- Bug 31596: Bump mingw-w64 version to pick up fix for #31567
- Bug 29187: Bump NSIS version to 3.04
- Bug 31732: Windows nightly builds are busted due to mingw-w64 commit bump
- Bug 29319: Remove FTE support for Windows
- OS X
- Linux
- Android
- Bug 30324: Android toolchain update for Fennec 68
- Bug 31173: Update android-toolchain project to match Firefox
- Bug 31389: Update Android Firefox to build with Clang
- Bug 31388: Update Rust project for Android
- Bug 30665: Get Firefox 68 ESR working with latest android toolchain
- Bug 30460: Update TOPL project to use Firefox 68 toolchain
- Bug 30461: Update tor-android-service project to use Firefox 68 toolchain
- Bug 28753: Use Gradle with --offline when building the browser part
- Bug 31564: Make Android bundles based on ESR 68 reproducible
- Bug 31981: Remove require-api.patch
- Bug 31979: TOPL: Sort dependency list
- Bug 30665: Remove unnecessary build patches for Firefox
- Bug 30324: Android toolchain update for Fennec 68
- All Platforms
Comments
Please note that the comment area below has been archived.
absolutely massive, well…
absolutely massive, well done guys!
if only it didn't have a…
if only it didn't have a huge amount of bugs
Huge amount? Explain. …
Huge amount? Explain. Other commenters think you may be mistaken.
Hey bobby. Tor tries to be…
Hey bobby. Tor tries to be better everyday. I think you should create a ticket if you find a bug while using,so that the issue can be fixed for you to have a better experience.
Plus one!
Plus one!
just navigator.userAgent …
just
navigator.userAgent
"Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0"
great work!
great work!
just navigator.userAgent …
just
navigator.userAgent
"Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0"
8.0 bug
https://trac.torproject.org…
https://trac.torproject.org/projects/tor/ticket/28290
That's really annoying. I…
That's really annoying. I hope they fix it soon.
Hello from Win7 32bit -…
Hello from Win7 32bit - after upgrade from 8.5.5 to 9.0 - I got wrong size of TBB's window!!! - Now main "HTML-View-control" is surrounded with the white-color window-canvas-border. Just wrong calculations. Early there were no issues of such kind .
This is not a bug, but the…
This is not a bug, but the the new letterboxing feature, preventing fingerprinting via screen size: https://www.zdnet.com/article/firefox-to-add-tor-browser-anti-fingerpri…
They tell you this is a bug…
They tell you this is a bug in sense it should support the dark mode and add black borders.
Yeah, that's https://trac…
Yeah, that's https://trac.torproject.org/projects/tor/ticket/32220.
Correct me if I'm wrong, but…
Correct me if I'm wrong, but with JS disabled, screen size fingerprinting is not possible. If so, the letterboxing can be disabled in about:config under privacy.resistFingerprinting.letterboxing
Thanks. I don't need…
Thanks. I don't need letterboxing security, so it is good to know how to disable it.
Thank you so much, you are…
Thank you so much, you are an absolute saint!
> Correct me if I'm wrong …
> Correct me if I'm wrong
You are wrong. Read the comments below.
nope you can still detect…
nope you can still detect and do fingerprinting just fine even with javascript disabled. something called css3 media queries allows a site to detect specific details about the browser without even running javascript. even letterboxing doesn't protect against this tho. it would have been a much better idea to disable certain options when parsing css media queries. preventing loading external resources while inside a css3 media query block would have done away with css fingerprinting without horrid letterboxing.
> it would have been a much…
> it would have been a much better idea to disable certain options when parsing css media queries. preventing loading external resources while inside a css3 media query block would have done away with css fingerprinting
Are you sure your suggestion would not produce collateral damage, ie. break some websites?
Is screen size…
Is screen size fingerprinting an issue if javascript is disabled?
Yes, it is an issue with…
Yes, it is an issue with JavaScript disabled as well as the size can get determined with CSS alone.
Come again? Are you saying…
Come again? Are you saying letterboxing makes things worse if you use "safer" or "safest" setting?
No, I meant that JavaScript…
No, I meant that JavaScript is generally not required for extracting your real screen dimensions if defenses like letterboxing were not in place.
Thank you, this is very…
Thank you, this is very helpful.
I think the @media rules can…
I think the @media rules can assign a different background url for each different pixel height and width.
Also, I think @media heights and widths can use other types measurements than only pixels.
I think that if TBB sent false width and height, then the webpage usability would suffer from incorrect other @media rules.
So, designating some noncontinuous widths and heights appears to be the best compromise - usability vs lessened fingerprinting potential.
Yeah, that's the idea.
Yeah, that's the idea.
Nice summary. Thank you.
Nice summary. Thank you.
win7 - here is the error: -…
win7 - here is the error:
- https://ibb.co/b59dwJv
- https://ibb.co/FDB8nmD
You mean the white margins?…
You mean the white margins? That's a feature called letterboxing which Mozilla developed to help defending against fingerprinting your screen dimensions: https://www.zdnet.com/article/firefox-to-add-tor-browser-anti-fingerpri….
Recent ubuntu version…
Recent ubuntu version broken. All windows are black.
Disable /etc/apparmor.d…
Disable /etc/apparmor.d/torbrowser.Browser.firefox
torbrowser-launcher has poor developer.
See: https://trac.torproject…
See: https://trac.torproject.org/projects/tor/ticket/32215#comment:1 for an explanation.
Updating newest torbrowser…
Updating newest torbrowser.Browser.firefox on torbrowser-launcher github fix black problem. Add new problem. Apparmor block noscript and httpseverywhere icons for ubuntu 18. Only security level and new identity icon show. Please make new ticket for fix.
- https://ibb.co/Vvrr8cv
- https://ibb.co/Vvrr8cv
Where is the error?
Where is the error?
Once again the "use system…
Once again the "use system colors" setting is being ignored, also my custom page colors are being ignored forcing me to choose between the website's "white page / black text" or the browser-default of black text on a stark white background.
Do you guys know what you turned off, so I can turn it back on? Otherwise I can barely read anything on this page.
Hm. Actually, this should…
Hm. Actually, this should work. Does a normal Firefox 68 ESR work for you (you find bundles on: https://www.mozilla.org/en-US/firefox/enterprise/)? How can I reproduce your issue?
I'm downloading the ESR non…
I'm downloading the ESR non-tor now but, I also have FF-nightly, and palemoon, and waterfox-portable, all of which have never shown this problem. But this is the second (*maybe* third) time an upgrade to TORbrowser causes it to ignore the "custom colors" option.
Last time, I was able to force it back to working by toggling several times between "always" & "never" in the options dialog window. But since this last upgrade I've re-downloaded, and also downloaded the alpha, and made a copy of the browser directory and deleted the original, then re-installed. Whatever is going on, is in my windows profile because it remembers the glitch across versions (downloaded 8.5.5, installed to the desktop, same problem despite being the version I was using) and across directories.
Is there a way to save my bookmarks, and blow away any lingering cruft to show I've ever had TOR installed? I'm running 64b Win-7, and most of the time I'm running TOR from a directory on a Veracrypt encrypted "hard drive" file. What I'm trying to do, is tell the browser to use system colors instead of browser-set defaults, and always override those colors even if the web page I'm viewing specifies other colors.
> Is there a way to save my…
> Is there a way to save my bookmarks, and blow away any lingering cruft to show I've ever had TOR installed?
There are two ways to export and import bookmarks in Firefox: HTML file or JSON file. Remember any custom bridges and search engine additions, too.
As far as I know, Tor Browser does not write to the registry or outside its folder by default, so deleting the folder should delete all traces of it. See if the color option works if you set it and then close the browser to be sure the UI is totally refreshed.
did the exact thing on my…
did the exact thing on my home computer. Now I can't use TOR anywhere.
and no, the non-TOR ESR 68 behaves as expected.
What exact thing did you do…
What exact thing did you do and what is happening? Do you get any error messages?
I was referring to the color…
I was referring to the color setting being ignored, above. Can *you* set custom page colors that are honored? Because neither my chosen colors, nor system colors are honored if I tell TOR to override page-requested colors with my choices...I just get blinding, headache-inducing white.
> blinding, headache…
> blinding, headache-inducing white
Until custom page colors are fixed, maybe turn down your brightness and contrast? Search if your display hardware or OS has a blue light filter, or install something like Redshift.
On installing 9.0, AVG has…
On installing 9.0, AVG has placed 'Win64:Evo-gen [Susp]' in quarantine. Though 9.0 seems to be working. Thank you.
Avast does this also…
Avast does this also. Behavioral shield probably, thinks it's a Trojan. Grabs nssdbm3.dll as well.
"Evo-gen" is likely a false…
"Evo-gen" is likely a false positive. Verision 9.0 is very new; it was released on the day you posted. Your virus scanner provider probably has not updated their virus definition files yet. Wait a few days, update your scanner, restore the file from quarantine, and scan Tor Browser again.
In any case, you could verify Tor Browser's PGP signature.
Updated virus scanner. …
Updated virus scanner. Deleted quarantine. Reinstalled version 9.0. Nothing put in quarantine. Thank you for your time. As version 9.0 still seemed to be working, not sure what difference running version 9.0 without 'Eve-gen' would make, or if you are permitted to say. cheers.
what is this white border…
what is this white border around web pages?!!
This is the the new…
This is the the new letterboxing feature, preventing fingerprinting via screen size: https://www.zdnet.com/article/firefox-to-add-tor-browser-anti-fingerpri…
can there be a downgrade…
can there be a downgrade option, many bugs in 9.0. might just move back to not using Tor browser at all when its like this.
You do realize that the bugs…
You do realize that the bugs listed in the release announcement here are fixed?
Or what bugs are you referring to?
It seems a lot of people don…
It seems a lot of people don't understand how the changelog works. Maybe the blog post should explicitly say that what's listed are fixes and features. Part of the misunderstanding has probably to do with using the word "Bug" for every ticket on trac, even for user's feature suggestions and the team's own goals and discussions.
Ideally the changelog would be replaced by a written summary of what was fixed and added with a link to the actual changelog at the end.
Commit messages (for example…
Commit messages (for example, descriptions of bug patches) are written in imperative mood, not past tense. Some novices might misunderstand this standard practice. If readers misunderstood the word "Bug", they could have clicked on them and found every ticket is labeled "Fixed".
https://duckduckgo.com/?q=commit+message+imperative
How can a list so varied and gigantic be summarized? On some posts for releases in the past, some changes were simply omitted. And this is a major point release, 9.0. I prefer the link to the actual changelog at the beginning of the summary or list so I don't have to scroll through incomplete paragraphs to reach the original document.
> How can a list so varied…
> How can a list so varied and gigantic be summarized?
161 bugs in the previous version have been fixed in Tor Browser 9.0, as follows:
Bug 31740: Remove some unnecessary RemoteSettings instances
Bug ...
17 major updates from previous versions are included in Tor Browser 9.0, as follows:
Update Firefox to 68.2.0esr
....
You get the idea. As an overall guidance, I think these announcements should cater to ordinary users more than power users, but should offer details for power users who want them, after offering an overview for ordinary users.
> You get the idea. I don't…
> You get the idea.
I don't. They said, "Ideally the changelog would be replaced by a written summary of what was fixed and added." In other words, they want paragraphs, no list and nothing as unhelpful as one total number. Although, it would get the message across better to say "updates" or "fixes" or "bugs fixed/patched" instead of "bugs".
> It seems a lot of people…
> It seems a lot of people don't understand how the changelog works. Maybe the blog post should explicitly say that what's listed are fixes and features.
Good point. It seems likely that most Tor users will not have prior experience reading FOSS type changelogs.
is there a way to block…
is there a way to block cookies like in tor v8.5.5?
Cookies are automatically…
Cookies are automatically cleared when closing the browser, like in previous versions.
He was asking how to…
He was asking how to completely block all cookies. There is no apparent way to do that with 9.0.
How would you do that in a…
How would you do that in a vanilla Firefox 68 ESR? There should be no reason why Tor Browser users could not do the same.
Just look at about…
Just look at about:preferences#privacy and see that there is no UI to block cookies, unlike in normal Firefox.
I haven't used Firefox 68 ESR but at some point Firefox intricated the cookie controls with the tracking protection controls. Maybe ESR or Tor browser removed the whole thing, and with this went the ability to block cookies.
I don't want to help sites to do even anonymous session tracking, especially when I use something like Tor browser. This is disappointing.
Yes, this got integrated…
Yes, this got integrated into Tracking Protection. That UI is misleading in a Tor Browser context, though, as it claims the browser provides privacy by blocking. We don't believe that's actually the case in general and definitely not in Tor Browser's context. That's why we decided to hide the UI.
Now, the functionality is still there. If you need to change the cookie settings just adapt the
network.cookie.cookieBehaviorpreference to the value you prefer.Sites store cookie-files in…
Sites store cookie-files in the user's machine for many reasons. A main one reason is for obtaining behavior and preferences from the users, and so use these or even sell them to who can pay for them. It's so an obvious violation of privacy unless the user have agreed with such. The clear question is: "Did this 9.0 tor version remove this kind of privacy?" Yes or No?
Moreover, about the sugested manual alteration in "network.cookie.cookieBehavior". How is that done? That is, default value set is "1". Could please be specified what is the value and/or modification that should be set to recover the feature like was in the previous version of Tor?
That depends on what cookie…
That depends on what cookie policy you want to have. See: http://kb.mozillazine.org/Network.cookie.cookieBehavior for possible values (there are more meanwhile but those mentioned there might be enough for your purposes).
Cookies are sometimes…
Cookies are sometimes required for websites to properly function regardless of JavaScript. If you block all or create a personalized filter, eavesdroppers can identify your traffic as different from other Tor Browser users across browsing sessions. Instead, click the New Identity button or close the browser to erase all cookies between sessions.
You may be interested in "first-party isolation" and Firefox Containers.
Some of the cookie UI in Firefox was removed in Tor Browser. In Preferences, open "Privacy & Security" in the side menu, find the section at the top titled "Cookies and Site Data", read what it says there, and click the button "Manage Permissions...". To find hidden preferences, open a new blank tab, type
about:config, and type "cookie" in the search box in that tab. Your question mostly relates to "network.cookie.cookieBehavior". I repeat, changing cookie preferences from Tor Browser defaults will lower your privacy.Well, this "solution" is…
Well, this "solution" (i.e. removing the option from the Tor menu) is terribly unpractical to the users. This should be something like an easy doing as always used to be (but not anymore in this version 9). No site at all should have freedom to send or store cookies into our devices, unless explicitly authorized by the users, even if they are temporary or deleted in the end of session. Please, we ask to the Tor team, to return the option to block/unblock all cookies and particular types of cookies..
The option is not gone, it's…
The option is not gone, it's now just not exposed in the UI anymore. Flip the preference and you are done.
How? Where? And which values…
How? Where? And please, which values should be set instead?
That depends, see: https:/…
That depends, see: https://blog.torproject.org/comment/284928#comment-284928.
The cookie settings were…
The cookie settings were made "unpractical" as you call it because users shouldn't be customizing things away from privacy defaults rigorously studied and chosen in their best interests. Users need to be allowed but dissuaded from tweaking and customizing their traffic because doing so actually degrades privacy while they are part of the network and want their traffic to be camouflaged among other Tor Browser users. You would have known that if you cared as much as you claim to do about the topic to actually browse the Tor Project site to research why the developers of Tor Browser did what they did. In short, calm down and RTFM.
"your choice of whitelisted websites acts as a sort of cookie that makes you recognizable (and distinguishable), thus harming your anonymity."
https://2019.www.torproject.org/docs/faq.html.en#TBBJavaScriptEnabled
https://research.torproject.org/
https://www.freehaven.net/anonbib/
So, it is claimed that when…
So, it is claimed that when a user blocks cookies to some sites, this may expose his white-list?! In this case, how is this worse than making his machine a cook-container (as is the default set of this 9.0 version) which stores all kind of garbage during the sessions until finally he closes the browser or changes identity? In what way this could offer a better privacy? Obviously this cannot. And only cannot, as indeed makes the opposite since cookies (and so scripts) allow to extract the user's profile, preferences, etc. that is, the user be can be more easily identified.
> when a user blocks cookies…
> when a user blocks cookies to some sites, this may expose his white-list?!
Their white-list is not directly exposed, but sites can indirectly learn what their whitelist is by comparing the behavior of their browser to other Tor Browsers.
Read these:
https://blog.torproject.org/comment/283202#comment-283202
https://blog.torproject.org/comment/283857#comment-283857
Firefox merged cookie…
Firefox merged cookie preferences with content blocking, which is not present in Tor Browser.
https://user-media-prod-cdn.itsre-sumo.mozilla.net/uploads/gallery/imag…
Please could someone inform…
Please could someone inform an address (or link) to a previous version (or any earlier version such as 8.5.5, 8.0, etc.) of Tor download? I will return to a previous version.
Absolutely loving the new…
Absolutely loving the new Dark theme on Windows, also the GUI redesign. As always, a great job done by guys & gals at TOR; also, that is one massive list of improvements.
Have not tried the updated version on Android, but here's to hoping that bookmark import-export is coming soon.
Thank you people of TOR for the hard work and bringing us this update.
Is the builtin dark theme…
Is the builtin dark theme being used in the screenshots in the post? While the author was talking about features, it would have been nice to slip in if it was.
It's not mentioned as a Tor…
It's not mentioned as a Tor Browser feature as it is one that actually came with Firefox. We just made some adjustments here and there so it fits with Tor Browser.
So, do you state it isn't…
So, do you state it isn't fingerprintable?
It makes things way better…
It makes things way better for users now. Being fingerprintable is usually not a yes/no thing and in this case neither.
Seems that rss is broken …
Seems that rss is broken ... xml problem, apart from this it's beautiful.
thank you all.
Do you have steps to…
Do you have steps to reproduce the rss issue?
>Do you have steps to…
>Do you have steps to reproduce the rss issue?
RSS support was removed from Firefox a while ago.
Hi boklin, I can see that…
Hi boklin, I can see that also (I didn't try a fresh install).
At least, it appears a default RSS rendering stylesheet is gone missing, now they get presented in Firefox' raw XML browser.
Also, clicking the RSS link at the bottom of this blog does brings the file download dialogue. That must be a different issue, but it feels wrong too.
FWIW about the former, please just open these in any previous release.
e.g. https://lwn.net/headlines/rss
or even https://news.google.com/rss
This would be a major feature loss : many many content gets so much "lighter" that way _hence_ accessible at all, over bad networks or hardware. Special thoughts to Google News and others, whose standard web "pages" are so bloated they just will not get entirely loaded or readable _ever_.
RSS FTW! (Tor Project if you hear me, please publish RSS feeds everywhere you can and you haven't yet, starting with this comment feed maybe? Thanks!)
\o/ \o/ \o/ \o/ \o/ \o/ \o/ \o/ \o/ \o/ \o/ \o/ \o/
\o/ \o/ \o/ ONE-CLICK NEW ID \o/ \o/ \o/
\o/ \o/ \o/ \o/ \o/ \o/ \o/ \o/ \o/ \o/ \o/ \o/ \o/
\o/ A DREAM HAS COME TRUE \o/ \o/
\o/ \o/ \o/ \o/ \o/ \o/ \o/ \o/ \o/ \o/ \o/ \o/ \o/
\o/ \o/ THANK YOUUUUUUUUU \o/ \o/
\o/ \o/ \o/ \o/ \o/ \o/ \o/ \o/ \o/ \o/ \o/ \o/ \o/
FF64+: https://bugzilla…
FF64+: https://bugzilla.mozilla.org/show_bug.cgi?id=1477667 - Remove feed reader and live bookmarks support
firefox removed rss
firefox removed rss
You mean Firefox's "RSS feed…
You mean Firefox's "RSS feed preview"? It was removed upstream in Firefox 64:
https://www.mozilla.org/en-US/firefox/64.0/releasenotes/
You can still use the view-source: feature to preview contents of a feed.
Thank you to point upstream…
Thank you to point upstream's removal. Mozilla advertises a "curated addons collection" to replace this feature, but this collection is now empty. So so.
The addon "RSSPreview" does restore the feature, it feels just like the original (simple and light).
https://addons.mozilla.org/en-US/firefox/addon/rsspreview/
No idea about its code quality or security. As an immediate response, I see no better option. Other addons exist, but they look a lot heavier.
Other addons exist, but they…
Just in case:
Yes I know. But as an…
Yes I know. But as an immediate response, I see no better option. I don't know of any RSS reader integrated with Tor, the same way Tor Browser is.
I do not always use browsers…
I do not always use browsers full screen. This latest release displays pages as if they are in a window leaving the page with scroll bars inside a whitespace border.
Thanks! Best feature, just…
Thanks! Best feature, just one click "new identity"!
The performance seems to…
The performance seems to have improved.
Also, the instruction for Using a system-installed Tor process with Tor Browser works again! It was not working for the last release.
See http://ea5faa5po25cf7fb.onion/projects/tor/wiki/TorBrowserBundleSAQ for details.
Nice, thanks for the report…
Nice, thanks for the report back!
For those who use Debian …
For those who use Debian "Buster" and update from the onion mirrors via the version of Tor which comes from Debian with apt-transport-tor, and who also want to use Tor Browser from www.torproject.org, is it better or worse to follow the directions in the link the other commentator provided?
> is it better or worse In…
> is it better or worse
In other words, should you re-torify Tor Browser to go through Debian's tor binary package (repackaged Expert Bundle)?
My 2 cents: Under normal circumstances, I would leave it the way it is: minimal reliance on Debian's tor and less to reconfigure in Tor Browser. From my perspective, disadvantages include primarily that your device holds open a few more network connections, and your ISP can see that. But things are different in an enterprise network or if a dedicated machine runs tor for a LAN for example.
Have since recognized that…
Have since recognized that some of the problems I have experienced using the Debian mirror may be due to clock issues. Has anyone at TP studied what can go wrong if the system clock is failing? Maybe we need to be able to adjust the clock faster using NTP while connecting to Tor network? Also a large clock skew is de-anonymizing even for ordinary browsing. I don't understand why my system clock is so far off even after I have reset it manually.
> what can go wrong if the…
> what can go wrong if the system clock is failing?
Many asynchronous encryption protocols depend on your system clock to be set to accurate time to determine when a key or signature was created, modified and if it is valid, expired, revoked, etc. In a word, it's metadata. This is true for browser TLS/SSL/HTTPS and keys in PGP/GPG. NTP is not usually encrypted, and that has interesting implications for all of those encryption systems that depend on NTP. It shouldn't be necessary to adjust the clock "faster"; just make sure your system time is set before using cryptography. Check your time-zone, and install system updates for time-zones if government laws change (daylight saving time) or if you travel to other countries. If your computer is more than 4 years old and not keeping the time after you reboot, check its CMOS battery that powers the real-time clock when the system is powered off. If you use the NTP Pool project (Debian and Ubuntu do), use a public pool or a secondary (stratum 2) server:
https://www.ntppool.org/
https://support.ntp.org/bin/view/Main/WebHome
https://support.ntp.org/bin/view/Servers/WebHome
Hey, my interface is broken…
Hey, my interface is broken.
My browser window has a white border inside it.
When I use the default window size, there are two stripes on the top and bottom of the window, about two centimeters in size each.
When I maximise the window, the white border becomes a square, with two centimeters of white space on each side of the window.
OS: Fedora 29, Gnome desktop environment, Wayland window manager
Screenshot:
https://share.riseup.net/#p3QL2554C-nYe7ahcBqKfA
its the same under ubuntu 19…
its the same under ubuntu 19.04 with all sites opened having this white bars changing in size while i change the windowsize.
I'm a Hongkonger. Thanks for…
I'm a Hongkonger. Thanks for maintaining / developing Tor Browser! It's good to know there will always be a browser that would (likely) work, even if the gov were to impose GFW-style censorship in HK.
Will snowflake work in China in the future? Currently, only meek-azure works, right?
I live in mainland…
I live in mainland. According to some of fellow activists, snowflake bridge works for oftentimes, but you need to reconnect over and over again. Despite this, it's a little bit faster to connect via snowflake than meek. (I haven't tested myself)
I'd love to hear whether…
I'd love to hear whether either or both of you are able to use Tor Browser to surf to sites such as citizenlab.ca and hrw.org and theguardian.com!
I am concerned that influential US publications such as Wired are not saying anything about Tor's role in getting the word about what is happening inside China. If you feel it is safe to try this, have either of you considered using Wired's Secure Drop site to tell your story to a reporter?
As you probably know, there is great concern among ordinary Americans who have friends who are dual citizens or living in China about what is happening.
Are you sure Wired's…
Are you sure Wired's SecureDrop site is up to date with security patches? It's not listed in the SecureDrop directory nor in an older directory on Tor Project's Trac. But many other publications are listed.
> Are you sure Wired's…
> Are you sure Wired's SecureDrop site is up to date with security patches?
No. And I have not had much joy urging news organizations to perform even a casual audit of their own SecureDrop sites. Maybe you can help by joining the effort to check up?
> Maybe you can help by…
> Maybe you can help by joining the effort to check up?
SecureDrop.org's list is supposed to hide obsolete instances. If you click under "Want to get your instance listed?" to go to the submission form, it says "Freedom of the Press Foundation may perform routine, automated tests against your SecureDrop .onion service and your landing page, to verify uptime and version information, and to perform basic security checks against our landing page recommendations." Basically, contact SecureDrop or Freedom of the Press Foundation.
I checked the onion…
I checked the onion addresses given in the directory at SecureDrop.org against the onion addresses given in landing pages where these were available with security "highest" (The Washington Post messed up even that simple requirement), and the addies: I checked seem to all be OK:
Al Jazeera
aljazeerafo4sau2.onion
Buzzfeed
ndg43ilvrrj465ix.onion
Daily Beast
bcwyjiwj25t44it6.onion
Gizmodo
gmg7jl25ony5g7ws.onion
Global Witness
37fmdxug33hhyi2g.onion
HuffingtonPost
rbugf2rz5lmjbfun.onion
Lucy Parsons Labs
qn4qfeeslglmwxgb.onion
Public Intelligence
arujlhu2zjjhc3bw.onion
The Guardian
33y6fjyhs3phzfjj.onion
TheIntercept
intrcept32ncblef.onion
Vice Media
e3v3x57ykz25uvij.onion
It is not obvious which of these are running the latest version of SecureDrop. It seems that sometimes when a news org does take the trouble of updating their SecureDrop (obviously it would be unwise to trust one which doesn't!), this results in a new onion address being generated, but the news org may then sometimes forget to tell SecureDrop.org about the change.
Thanks to all reporters who try to goad their editors into letting them cover human rights stories!
> It's not listed in the…
> It's not listed in the SecureDrop directory
I am told by someone who claims to work for one of the listed publications that this directory is itself out of date, and he appears to be correct.
I think the problem is that SecureDrop depends upon news orgs to be sufficiently organized :-/ to update their entry in the directory when they change their onion, but there is no reason to think they are doing that. Sigh...
SecureDrop uses cron-apt to…
SecureDrop uses cron-apt to pull its update and 16.04 LTS security updates nightly. Config here:
https://github.com/freedomofpress/securedrop/tree/develop/install_files…
Wired's instance is on the latest SecureDrop version, 1.1.0, according to this public endpoint:
http://k5ri3fdr232d36nb.onion/metadata
This would indicate that cron-apt is running. Beyond that, nobody but the Wired SecureDrop admin would have any (legitimate) visibility into the state of the system.
Securedrop instances aren't always listed in the directory - sometimes they don't want to be, don't know about it, or don't meet criteria around the landing page or the instance setup as listed here:
https://securedrop.org/directory/submit/
I don't think I stated what…
I don't think I stated what I was told very well, which is not inconsistent with what you just said. This is very helpful, and I hope more potential whistleblowers and sources will try SecureDrop.
Particularly valuable for US publications would be inside information on how FBI is abusing JTTF in various cities to harrass peaceful protesters and political dissidents. Also on the new CBP Fusion Center which accesses NSA databases apparently including recordings of phone calls and text messages.
FPF human here! With some…
FPF human here! With some probably not entirely satisfactory answers:
SecureDrop uses cron-apt to pull its update and 16.04 LTS security updates nightly. Config here for the interested:
https://github.com/freedomofpress/securedrop/tree/develop/install_files…
Wired's instance is on the latest SecureDrop version, 1.1.0, according to this public endpoint:
http://k5ri3fdr232d36nb.onion/metadata
This would indicate that cron-apt is running. Beyond that, nobody but the Wired SecureDrop admin would have any (legitimate) visibility into the state of the system. If there were failures in applying Ubuntu security updates however, I would expect the SecureDrop application version to lag behind.
Securedrop instances aren't always listed in the directory - sometimes they don't want to be, don't know about it, or don't meet criteria around the landing page or the instance setup as listed here:
https://securedrop.org/directory/submit/
Potential whistleblowers should always do some anonymous research first (preferably via Tor Browser, on a device they control, and on a network they're not previously associated with) on the organizations they plan to contact. A SecureDrop directory listing is a strong indicator that a given org is taking the setup of their instance seriously, but it's not definitive and there may be orgs that are a good choice to leak to that are not listed there.
Over the last few years this…
Over the last few years this seems like the biggest improvement between major versions, both in performance and UI design. It's wonderful. Hopefully we'll see the number of users increase.
According to https:/…
According to https://browserspy.dk/headers.php , the new Tor Browser 9.0 reveals my user-agent on the wire as:
Mozilla/5.0 (X11; Linux x86_64; rv:67.0) Gecko/20100101 Firefox/67.0
Reveals platform in HTTP header (even in Safest security mode, no JS). Also, wrong Firefox version.
about:support properly says:
Mozilla/5.0 (Windows NT 10.0; rv:68.0) Gecko/20100101 Firefox/68.0
Workaround: I used about:config to set general.useragent.override to the same value as about:support says. Tested, seems to work.
Please fix. Thanks.
This is not what the user…
This is not what the user agent is supposed to be. It should be "Mozilla/5.0 (Windows NT 10.0; rv:68.0) Gecko/20100101 Firefox/68.0".
Do you have the same user-agent in a new install of Tor Browser 9.0?
DAMMMNN!! Hopefully firefox…
DAMMMNN!! Hopefully firefox allows/themes on the preferences page soon. Want dark theme all around. Nice work :D
Avast just quarantined…
Avast just quarantined mozavutil.dll and nssdbm3.dll when updating to torbrowser 9.0 as Evo-gen !!! Are they essential??
yes
yes
Sorry. But i don't like…
Sorry. But i don't like these white borders inside the tor browser. shit on fingerprinting. Is there a place where i can switch this off?
I mean... Sorry. But when not... Maybe this is time to choose another browser...
Sure there is an option to…
Sure there is an option to do that but it is not recommended if you are resizing your windows:
privacy.resistFingerprinting.letterboxingis the preference governing this feature.Letterboxing is great at…
Letterboxing is great at softening the fingerprint in those rare cases where you accidentally resize or maximize a window. However doesn't it decrease the uniformity if people start using it intentionally, given all the possible window and height combinations?
Is using the default window size still recommended?
Yes, the default size is…
Yes, the default size is still recommended. But, if users are resizing their window they should get some protection now. Before that we only had the notification bar popping up and essentially saying "Don't do that! Danger!" which was kind of lame. Now, we have something better to offer which fits more to our privacy-by-design goal.
Maybe you should still…
Maybe you should still display the pop-up, although to be honest it seem ineffective, people have understandably just gotten too used to annoying popups and notifications and instinctively close or ignore them. I see people maximizing their Tor browser all the time out of habit.
> Maybe you should still…
> Maybe you should still display the pop-up
+1. But rewrite its message to explain letterboxing. It won't get in the way like before, either, because there's now empty space due to letterboxing above the page area. Hell, if you could make the whole letterbox border all around flash yellow three times, it might grab their attention long enough that they'd actually read it. It's ridiculous the lengths we have to go to get people to look into a pitifully simple message, "Danger. This harms you and your fellow community. Please don't do it." I mean, I might as well be talking about climate change! Convenience and coveting seem to be conquering every other decisonal factor.
Talking about flashing…
Talking about flashing colors to grab attention, I happened across this neat CSS animated warning on RedHat's bugzilla. Simply disable javascripts and refresh. https://bugzilla.redhat.com/
And thank you very much,…
And thank you very much, from one of your loyal users who complained loudly about the old bad way of handling accidental resizing.
Just to be sure: this new letterboxing feature will still provide some anti-fingerprinting protection regardless of which security setting ("safest", "safer") you are using, right?
Yes. The security trade-offs…
Yes. The security trade-offs users make are orthogonal to the privacy protections the browser offers and that's important.
Can TP seek funding from…
Can TP seek funding from Raspbian.org or RaspberryPi.org to
o make a Tor Browser for the Pi?
o make the Raspbian repo into an onion?
o design a Pi to Pi secure chat? (Would be very useful in places like Santiago and Hong Kong, where neighbors need to talk to neighbors.)
o offering a battery making the Pi mobile?
If it helps, I use Pi-3 and have heard that Pi-4 has some problems with overheating.
I don't have an answer for…
I don't have an answer for designing a Pi to Pi secure chat, but...
> Tor Browser for the Pi?
There is a more active comment thread about Tor for Pi in this blog post and ticket #12631 for ARM architecture.
> make the Raspbian repo into an onion?
You seek Peter Palfrader. He manages the onions for both Tor Project and Debian (name in footers at bottom). While you're asking Tor Project to reach out, ask Raspbian to reach out to TP at the same time, too. Coordinate introducing them.
> a battery making the Pi mobile?
Could've done a web search before asking. Those exist. Bookmark stores that sell electronics components:
https://duckduckgo.com/?q=adafruit+similar
https://www.reddit.com/r/arduino/comments/1zocsq/alternatives_to_make_a…
https://www.quora.com/What-are-some-other-popular-websites-similar-to-S…
For good measure, also bookmark "maker" sites, hobbyist robotics sites, hackaday.com, and "single board computers".
> You seek Peter Palfrader…
> You seek Peter Palfrader. He manages the onions for both Tor Project and Debian (name in footers at bottom). While you're asking Tor Project to reach out, ask Raspbian to reach out to TP at the same time, too. Coordinate introducing them.
Would if I could but have been unable to contact any of the suggested entities.
Thanks for the tip about Pi batteries.
Thank you for this nice…
Thank you for this nice update, nothing will ever be 100% but 99.999%, threats are renewed every hour, just a question to those who criticize: Who is able to do better than the Tor Project on time current?
Simplicity, security, development, freedom of speech to users, speed to fill the gaps, seriousness in the realization ...? Nobody!
It's very very hard for them, how many different platforms and configurations for each of us? a lot ... they have enormous pressure, do not forget that they carry our lives at arm's length ...
Thank you Tor Project
Plus one. I add a shout-out…
Plus one.
I add a shout-out to Tails Project too. I rely on Tor and Tails because I use Tails for just about everything I do on-line, and many things I do off-line too!
Is there any way to disable…
Is there any way to disable the letterboxing feature or change the size or color of the border area?
> change the size or color…
> change the size or color of the border area?
Size? Yes, drag the window borders. Maximized or fullscreen? Not without recompiling. The dimensions of the inner area snap to intervals of 200 px by 100 px. It's intentional so everyone's browser fingerprints will look more alike, but leaving the window at its starting size is best for privacy. For more information, scan yourself on a browser fingerprinting site such as EFF's panopticlick, but note that Tor Browser's traffic is designed to appear as similar as possible to other Tor Browsers. It isn't practical and is basically pointless for Tor Browser's traffic, coming from the Tor network, to look like normal "clearnet" browsers.
Color? They're working on it: Bug #32220. Stay tuned.
Tor browser no longer…
Tor browser no longer launching after this update. Tried both upgrading from 8.5.5 and installing a fresh one. I'm using Trisquel 8 x86.
What error messages are you…
What error messages are you getting if you start it from the commandline like
./start-tor-browser.desktop --debug?Same problem as Dustin…
Thanks very much for the update.
I'm having the same problem as Dustin. Updated from v8.5.5 and then tried fresh install and it won't start.
My OS is Kubuntu 14.04.6 LTS i686 (I know, I should upgrade).
Starting it from command line I get:
user@computer:/opt/tor-browser_en-US/Browser$ ./start-tor-browser --debug
./firefox.real: error while loading shared libraries: libatomic.so.1: cannot open shared object file: No such file or directory
user@computer:/opt/tor-browser_en-US/Browser$
(Permissions, owner and so on are fine, it was working correctly up to v8.5.5)
Looks like it's working…
Looks like it's working after installing package
libatomic1:i386 (4.8.4-2ubuntu1~14.04.4). Couldn't findlibatomic.so.1anywhere in my file system (apparently isn't installed by default) and that package seems to provide the library.Thanks! I've filed https:/…
Thanks! I've filed https://trac.torproject.org/projects/tor/ticket/32259 to fix that issue. Sorry for the inconvenience.
Confirmed working again…
Confirmed working again after installing the said package. Thanks to user@computer for the workaround.
Launching './Browser/start…
Launching './Browser/start-tor-browser --detach --debug'...
./firefox.real: error while loading shared libraries: libatomic.so.1: cannot open shared object file: No such file or directory
Congratulations on #9! …
Congratulations on #9!
Looks pretty okay over here. No complaints yet. Still, I'm going to wait until the first wave of bug fixes before I settle in.
Going to 68 is a big jump!
After update! Tor browser is…
After update! Tor browser is just complete black... i use parrot os/Debian
Are you using torbrowser…
Are you using
torbrowser-launcher? If so, then https://trac.torproject.org/projects/tor/ticket/32215#comment:1 might help you.after the upgrade (8.5 -> 9…
after the upgrade (8.5 -> 9.0 ), when starting up, the error message "Startup is not possible because api-ms-win-crt-convert-L1-1-0.dll is missing on the computer. Try reinstalling the program."
(use a online translate :\ )
Win 7.
Hey! This is a security…
Hey! This is a security software, and it is not intended to be used on an OS without security updates.
See: https://blog.torproject…
See: https://blog.torproject.org/comment/284654#comment-284654.
Tor Browser 9 leak my OS! On…
Tor Browser 9 leak my OS!
On https://ipleak.net/ I see "Platform: Linux x86_64". This is true! But I like to see Windows NT 10.0 there.
User Agent is okay. Mozilla/5.0 (Windows NT 10.0; rv:68.0) Gecko/20100101 Firefox/68.0
I am using Tor Browser 9.0…
I am using Tor Browser 9.0 under Tails 4.0, with security set to "safer".
I just tested this and got the same result reported above:
> Your User Agent: Mozilla/5.0 (Windows NT 10.0; rv:68.0) Gecko/20100101 Firefox/68.0
> Platform: Linux x86_64
No idea whether this is a serious issue.
On the bright side, the IP shown is that of the exit router, and the test site reports no DNS leaks either. No leaks about plugins or mime either.
Used TB 9.0 under Tails 4.0…
Used TB 9.0 under Tails 4.0 with security set to "safest", which disables Javascript.
Then IPleaks is unable to detect anything but the fact that my circuit used a particular exit node and the fact that I followed a link from this blog.
Of course this setting may make some sites less functional.
Same here IPLeak is showing…
Same here IPLeak is showing my correct Platform :(
Crashes before it can even…
Crashes before it can even start for me. Error 0xc0000005. I had to roll back to 8.5.5.
Do you have some anti-virus…
Do you have some anti-virus/firewall software installed that could interfere here? If so, which? Could you test whether uninstalling it (disabling is often not enough) gets Tor Browser working again?
Where are the cookie options…
Where are the cookie options to block all cookies?
It is not recommended to…
It is not recommended to change cookie options from Tor Browser defaults. Just use the security level shield and New Identity features. Customization of network behavior (such as which cookies you accept and reject) will make your traffic conspicuous from other Tor Browser users and easier to be tracked. New Identity clears cookies. If you accept the risks and want to change cookie options anyway, find them in the Preferences menu.
There is no user interface…
There is no user interface for that anymore. But you can adjust the
network.cookie.cookieBehaviorpreference inabout:configto the respective mode you want to have.i have problem after update…
i have problem after update when open tor "The program can’t start because api-ms-win-crt-runtime-l1-1-0.dll is missing from your computer. Try reinstalling the program to fix this problem." im using windows 8.1 pro 32bit.
See my answer at https:/…
See my answer at https://blog.torproject.org/comment/284654#comment-284654.
after update this error…
after update this error coming up "The program can’t start because api-ms-win-crt-runtime-l1-1-0.dll is missing from your computer" im using windows 8.1 pro.
See my answer at https:/…
See my answer at https://blog.torproject.org/comment/284654#comment-284654.
i have just a little…
i have just a little cuestion
how can i eliminate the frames around the pages?
After update i have problemm…
After update i have problem.
Stuck on connect to tor window. Black screen, no buttons.
https://imgur.com/lzbuhYK
I use parrot os.
See: https://blog.torproject…
See: https://blog.torproject.org/comment/284657#comment-284657.
Window is blacked out for…
Window is blacked out for Debian. Currently unusable.
See: https://blog.torproject…
See: https://blog.torproject.org/comment/284657#comment-284657.
where is tor-browser-9.0…
where is tor-browser-9.0-android-x86_64-multi.apk in https://www.torproject.org/download/#android?
Ooops, we'll add it shortly:…
Ooops, we'll add it shortly: https://trac.torproject.org/projects/tor/ticket/32222.
Just curious: would it be…
Just curious: would it be impossible to make a version of Tor Browser for Raspbian?
Thanks to the entire Tor and Tails teams for all your hard work!
https://trac.torproject.org…
https://trac.torproject.org/projects/tor/ticket/12631
Someone please correct me if…
Someone please correct me if I am wrong, but I believe this does not apply to the Pi, which uses armhf architecture not arm for its repos.
This is why I cannot simply use the existing Debian repos to load arm software into the Pi.
It would be wonderful if Tor…
It would be wonderful if Tor Project can help RaspberryPi Foundation set up an onion mirror for their existing mirror. This would presumably be much easier than developing a TB for the Pi.
I see that the cited discussion
https://trac.torproject.org/projects/tor/ticket/12631
mentions a problem with Pi-2 overheating. It seems that this would be a problem with Pi-4 also. But I am using Pi-3 which apparently does not suffer from this kind of problem.
gk wrote (6 months ago):
> I wonder, generally, whether we should call the OS-arch combination linux-armhf here instead of just linux-arm, following Debian (especially as we might want to support 64-bit as well in the future).
I should explain that I am aware that armhf is somehow distinct from arm architecture, but I don't understand the differences.
> armhf is somehow distinct…
> armhf is somehow distinct from arm architecture, but I don't understand the differences.
Basically, hf = "Hardware Floating-point". The processor includes a circuitry unit for floating-point arithmetic, fractional numbers. Processors without one must calculate fractional arithmetic in Software.
How can i switch off this…
How can i switch off this pop-under thing under the urlbar?
browser.urlbar…
browser.urlbar.maxRichResults;0
browser.urlbar.oneOffSearches;false
browser.urlbar.quantumbar;false
there's still something left from this drop down menu.
The UA was messed with AGAIN…
The UA was messed with AGAIN. This has lead to many sites not being accessible for users on Tor.
Which ones? Do you have…
Which ones? Do you have examples?
For what it is worth, I have…
For what it is worth, I have been testing Tor Browser 9.0 as provided in Tails 4.0, and with security set to "safest" and "safer" I have been experiencing no problems whatever at the sites I tried (mostly news sites).
I got a "firefox.exe -System…
I got a "firefox.exe -System error"
The program can’t start because api-ms-win-crt-runtime-l1-1-0.dll is missing.
I tried a clean install but same error,
Running Win7 64 bit
here is a similar screenshot
https://filestore.community.support.microsoft.com/api/images/2b64f209-5…
You need to update your…
You need to update your Windows system to have the latest updates. One of those (which got offered by Microsoft a while ago) has the .dll files you need.
And another one of those has…
And another one of those has d3dcompiler_47.dll ;)
Seeing as you're always…
Seeing as you're always asking Tor users for specifics, could you try being a little less vague?
Specifically what version of the .dll is required?
No-one in their right mind (or having any past experience with Microsoft products) is going to install patches willy-nilly that can break a currently working system - especially users on OS's that Microsoft would like to fade away.
So, version numbers, 32/64, dates etc for the .dll would be helpful - or just link them here.
At the moment I have to butcher an old version of Tor to get something working without helpfully updating to something that is non-functional.
Please test properly before release, make less assumptions and give your users a little more choice and control.
Thank you.
Having your operating system…
Having your operating system up-to-date is essential for Tor Browser providing the guarantees it offers. So, my advice here is using the update mechanism of your Windows system to get all the security updates you missed so far (and the .dlls you need).
The DLLs are bundled in the…
The DLLs are bundled in the Universal C Runtime (CRT) update:
https://support.microsoft.com/en-us/help/2999226/update-for-universal-c…
For specifics of what's inside it, click "File information".
> especially users on OS's that Microsoft would like to fade away.
Try Tails. It runs in RAM from a bootable USB or DVD and won't affect the OS on your HDD. Simply shut down, remove the Tails media, and start up to login to your original OS. In Tails, mount your HDD partitions to access files on your HDD.
I strongly recommend migrating to Linux for your situation. Linux Mint, Ubuntu, Zorin OS Core or Lite are for beginners. Others are listed on distrowatch.com. Ease the process by searching for cross-platform alternatives to your Windows software on alternativeto.net or alternative.me. Some might already be cross-platform. Others could be replaced by Linux-native alternatives or installed as Windows software under Wine or Mono. Pay attention to licenses as well: GPL, BSD, MIT, Apache, or commercial/proprietary.
It's possible to download the .dll by itself from a third party site, but then it's harder to determine if the file was tampered with. It's possible that versions of .dlls built for Windows versions so much newer than yours may not run on yours anyway. 32/64 isn't really relevant for the .dll because both will have been published unless one isn't necessary. The 32/64 architecture of your OS on which the .dll will be running, however, is very relevant because that is not easily changeable and thus defines which .dll(s) is/are needed.
Deviating from official support and even simply community support to extremes of choice and control also means accepting that you will do a lot of everything by yourself including adopting responsibilities for support, upkeep, etc. of your niche or forked project.
You're welcome.
Not latest.I have only 2011…
Not latest.I have only Windows 7 2011-2016 security updates and Tor 9 does work.
> Bug 13543: Spoof smooth…
> Bug 13543: Spoof smooth and powerEfficient for Media Capabilities
and non-powerEfficient ;)
> Bug 28896: Enable…
> Bug 28896: Enable extensions in private browsing by default
This removes the security feature of Firefox.
So I am using TB8 with …
So I am using TB8 with "extensions.torbutton.use_nontor_proxy: true".
Is it okay to upgrade to TB9? I had disabled Tor related add-ons and I have no intention to enable them.
Can someone confirm TB9 works with extensions.torbutton.use_nontor_proxy nicely?????
What have you found in the…
What have you found in the docs? It should work as before.
NO. DO NOT UPGRADE. I LOST…
NO. DO NOT UPGRADE.
I LOST MY CONFIG AND BOOKMARKS WHEN DOWNGRADING TO 8.5.
Firefox doesn't support…
Firefox doesn't support downgrade.
I kept extensions.torbutton…
I kept
extensions.torbutton.use_nontor_proxyswitched to true.Then In about:config I switched
extensions.torlauncher.start_torto false. Then changednetwork.proxy.socksto my SOCKS proxy address andnetwork.proxy.socks_portto my SOCKS proxy port.It seems to work, the only issue I have is some brief "freezing" when changing the noscript security settings. Also the browser freezes for a moment when trying to access the Tor settings.
If someone has a better way to use Tor Browser with a non-Tor proxy in TB9, please comment. Many people use Tor Browser alone without Tor network and I think it shall be possible to do so.
Can you stop adding white…
Can you stop adding white-textbox completely?
Think for users who have less screen: 1024x768, 1366x768, and so on.
Please add a checkbox to disable it!! TB8.5 does not have this problem!
You can disable it if you…
You can disable it if you think you don't need it by flipping
privacy.resistFingerprinting.letterboxingenabled tofalse. But that is not recommended."less screen" is the most…
"less screen" is the most reasonable complaint I've seen about letterboxing to this post. Save that one. I had wondered also about Android displays but didn't say anything.
I can not locate signatures …
I can not locate signatures (md5, sha1, sha256) on TB 9 verification page (or anywhere else on web site):
https://support.torproject.org/tbb/how-to-verify-signature/
The signatures can be…
The signatures can be downloaded on https://www.torproject.org/download/ (see the
Siglinks). If you look for hash sums they can be found in the respectivesha256sumsfiles in https://archive.torproject.org/tor-package-archive/torbrowser/9.0/.about:telemetryTelemetry is…
about:telemetry
Telemetry is collecting release data
What makes you believe that…
What makes you believe that data is actually collected?
Of course, it is collected…
Of course, it is collected. Read the docs, see the errors of telemetry in console, check the prefs it adds...
Error: TelemetryStopwatch:…
Error: TelemetryStopwatch: key "WEBEXT_CONTENT_SCRIPT_INJECTION_MS" was already initialized ExtensionTelemetry.jsm:109:31
was already initialized
I have a LAN tap and can…
I have a LAN tap and can help test the reported issue if someone tells me exactly what to look for in a TCP dump. I would use tcp_dump in Tails on the monitoring machine and then use Wireshark to examine the dump.
Wouldn't Wireshark show…
Wouldn't Wireshark show encrypted Tor traffic? In the case of spyware Tor is a double edged sword because it's not easy to monitor what data leaves your computer if the spyware uses Tor.
When I want to test what data some program sends out I do it in a Whonix workstation. I'm not sure that's possible with Tor browser inside Whonix though.
Would love to hear about some other possible setups to both analyze the traffic and send it over Tor. Or, leaving Tor aside, some way to trick a program or the OS into sending requests even when not connected to the Internet so that you can see what requests would be sent to the outside world.
Since telemetry is on the…
Since telemetry is on the Firefox side rather than in the tor binary, it seems theoretically possible to deproxy the browser so it communicates via the normal internet and so Tor's encryption is absent, but the telemetry data itself, if sent, is probably wrapped in Mozilla's TLS certificate. But OP left out that
about:telemetrysays, "upload is disabled."OP knows about "Bug 30463:…
OP knows about "Bug 30463: Explicitly disable MOZ_TELEMETRY_REPORTING" ;)
> When I want to test what…
> When I want to test what data some program sends out I do it in a Whonix workstation. I'm not sure that's possible with Tor browser inside Whonix though.
The idea is that you have a test machine running Whonix and a monitoring machine running Tails (say) which is behind the LAN tap at bottom of the "T". To anthropomorphize, the test machine has no idea that the LAN tap even exists, much less that it is copying every packet sent from the test machine to the router (or vice versa; you need two test machines and two captures to study bidirectional traffic). You take the capture on the monitoring machine using tcpdump with the option to drop privileges and later study the capture using wireshark (on a Debian machine, say). The last step does not require root privileges since you are using wireshark to study an existing packet dump not to make one (which would be dangerous to do using wireshark with root privileges).
You can also use Tails to capture WLAN traffic using airodump-ng, and later study the packets using Wireshark.
None of this tests what happens after traffic leaves your LAN or local WiFi.
Tails is very useful for all kinds of other things besides legitimate monitoring of your own devices/network, of course.
Someone PLEASE HELP! After…
Someone PLEASE HELP!
After I upgraded to 9, there is NO OPTION to set custom proxy
and the browser is IGNORING extensions.torbutton.use_nontor_proxy congiguration.
I NEED TO USE my proxy with tor browser. I was able to disablr tor addons and use any proxy.
HELP! I REALLY NEED IT BACK!
Has anyone else had their…
Has anyone else had their twitter accounts locked out and about to be suspended after the new Tor update? I just lost my account after the new update and noticing before I was locked out Tor looked completely different with a large white border around the screen which made all pages online smaller. Could whatever Tor did in their update have made twitter accounts using Tor seem as "suspicious activity?"
Twitter was asking me to confirm my phone number. Before all they would ask is just type in your phone number. Today after the new Tor update it was asking me to CONFIRM the phone number I would need the actual phone in order to do so. The twitter account I have isn't originally mine and the person whose account it originally belonged to no longer has access to that phone number.
The ONLY other time this happened to me was weeks ago I lost two twitter accounts after installing an addon that would revert back to twitter's classic theme instead of the God-awful forced new twitter interface. The addon was just a simple user-agent switcher they explained it as it makes it appear as IE instead of as "mobile." The two accounts I lost at that time were also asking for me to confirm the phone number instead of just typing in the phone number which would let you log in normally.
I just got an email back from twitter's support saying they have unlocked the account. Now I'm afraid I might lose it again.
Here's how the new update looks with the new thick white border and it's how ALL pages online look regardless of where you go. The scroll bar on the right never appeared before either. Pages now at default zoom show that scroll bar on the right suggesting it's a larger screen when it's not.
https://imgur.com/a/daF3xMu
Windows TBB 9.0
The locking out has nothing…
The locking out has nothing to do with the white margins around your content. This is a feature called letterboxing, that helps defending against fingerprinting your screen size. It got developed by Mozilla a while back: https://www.zdnet.com/article/firefox-to-add-tor-browser-anti-fingerpri….
I just got an email back…
Write Twitter back to tell them that you use Tor because you represent a majority of internet users who support greater personal privacy [1, 2, 3, 4, 5, 6, 7, 8, 9] and that Twitter's automated defenses, not your behavior or content, are preventing you from being their return customer or "maximizing user engagement".
Link to this comment if you want, but I don't think would be as effective as your own personal stories.
не работает после обновления…
не работает после обновления выдает ошибку на windows 7 32 bit "запуск программы невозможен так как на компьютере отсутствует api-ms-win-crt-convert-l1-1-0.dll 2019" как мне исправить это? до этого обновления браузер работал отлично!
You need to update your…
You need to update your Windows system. This .dll together with other security updates got shipped a while ago.
if somebody has troubles to…
if somebody has troubles to launch TBB (standalone) with firejail:
old launcher - ALL tabs crashing, no browsing:
Exec=firejail sh -c '"PATH/tor-browser_en-US/Browser/start-tor-browser" --detach || ([ ! -x "PATH/tor-browser_en-US/Browser/start-tor-browser" ] && "$(dirname "$*")"/Browser/start-tor-browser --detach)' dummy %k
new launcher - works properly:
Exec=firejail PATH/tor-browser_en-US/Browser/start-tor-browser
Bug 25214: Canvas data…
Bug 25214: Canvas data extraction on locale pdf file should be allowed
*local
Thanks, fixed.
Thanks, fixed.
https://play.google.com…
https://play.google.com/store/apps/details?id=org.torproject.torbrowser
Updated
October 22, 2019
Size
Varies with device
Installs
1,000,000+
Current Version
60.9.0
???
Should be better now.
Should be better now.
browser is not working
browser is not working
What do you mean? What error…
What do you mean? What error messages do you get?
big bugg after the update…
big bugg after the update
the tor browser opens in start and not the other so i cant use bridges
What do you mean? Can you…
What do you mean? Can you give us steps to reproduce your problem?
New tor can't be started…
New torbrowser can't be started with system tor on a Linux machines. Tor launcher cat't be deleted
You don't need to remove Tor…
You don't need to remove Tor Launcher for using your system Tor, see: http://ea5faa5po25cf7fb.onion/projects/tor/wiki/TorBrowserBundleSAQ.
I think the introduction of…
I think the introduction of letterbox is crazy.
I want to delete the tor used for 10 years.
No need to delete it. You…
No need to delete it. You can just disable that feature if you want, by flipping
privacy.resistFingerprinting.letterboxingtofalse.no thumbnails on xhamster.com
no thumbnails on xhamster.com
context menu (rightclick) on…
context menu (rightclick) on a link or button doesn't work properly. it opens the link immediately. happens in tbb only.
Hm. On which system? I just…
Hm. On which system? I just tested on a 16.04 Ubuntu with 9.0 and just the context menu opens.
same here on arch + xfce. ui…
same here on arch + xfce. ui.context_menus.after_mouseup;true solves it.
looks like the changes with…
looks like the changes with the proxy settings broke stuff like zeronet, i2p and freenet (probably because it seems like there's no option to block the proxy on certain addresses), and foxyproxy doesn't seem to help it. i'll back off to 8.0 again, but this should really be fixed, messing with what works can be annoying.
How did that break? You can…
How did that break? You can still set all the proxy settings in your
about:config.first of all as always i…
first of all as always i appreciate all the hard work you guys put into keeping us safe out there!
but this version 9.0 isnt that supposed to be a stable version?
i cant run tor i fullscreen, theres missing like 15mm on each side of the screen.
also i miss the old blog version, this one looks really messy. cant see who wrote what to who and where the new comment comes in.
beside that great work!
It is a stable version, yes…
It is a stable version, yes. You can disable the letterboxing feature (see the blog text for what it is about) in your
about:configby flipping a preference (privacy.resistFingerprinting.letterboxingtofalse).The blog is a sad story. We try to get that fixed but it seems that it is hard. The worked is tracked in http://ea5faa5po25cf7fb.onion/projects/tor/ticket/31114.
thanks for your respons gk,…
thanks for your respons gk, really appreaciate it because it made me go back to the outdated version that kept crasching. about the old version 8.5.5. it refuse to update from the browser. well the the update starts but then it refuse to launch the browser when the update is done. just wanted to let you know, there seem to be something hindering it from launching.
hope you guys find a fix for the blog. also i wish to have a dark version of the blog because this one (white/light) kills my eyes.
how can i give the tor browser a dark theme? i saw someone mentioned that there is a dark theme. much appreciated!
> it refuse to launch the…
> it refuse to launch the browser when the update is done.
Check if your drive has enough space on the partition where you installed Tor Browser.
> how can i give the tor browser a dark theme?
Hamburger menu [≡] -> Add-ons (Ctrl+Shift+A) -> Themes
The letterbox border is not colored yet. It is planned to be.
> The blog is a sad story. …
> The blog is a sad story.
I worry about the fact that the PKI cert is so different from what I expect for a sensitive site. I am concerned that the blog I see may be a malicious clone of the real blog because I cannot reasonably assure myself of its relationship to Tor Project from the cert. If you disagree that this is an issue, please ask a TP expert to post explaining why it is not a serious issue.
It would also be very helpful to have a post advising how to use TB properly. E.g. I suspect most users do not know how to take advantage of sandboxing and try to store downloaded files in the wrong directory, or to use terminals in the wrong directory, etc.
If I understand you…
If I understand you correctly, you are in the habit of deliberately maximizing the TB window. If so, can you explain?
As a user who loudly demanded the new letterboxing protection against too easy window size fingerprinting, because I sometimes *accidently* maximize the window, I am sorry to see how much confusion it is causing. I hope the users who are unhappy soon find you can live with it.
I too have technical problems with the blog, but only if I forget to change the security setting from "Safest" to "Safer" before submitting a comment. I can live with that. The way I see it, quashing bugs, doing research into growing the Tor network, expanding the Debian onions to other distros, to CRAN, Raspbian, etc, and keeping them healthy, reaching out to some of the more reasonable members of the Fourth Estate to combat FBI's anti-Tor FUD, etc, etc. is more important. But yeah if TP can fix all those it would be great to improve the blog :-)
all levels of security are…
all levels of security are much appreciated! however not everyone is living in a dictator state, hiding from the the fbl or being a criminal. i simply just choose my time when i need extra level of security, for example when doing bank transactions and not for all times. i use tor for everything and in long terms some of the features can get really annoying. i didnt buy a bigger screen so that i could see smaler windows. stay safe out there, unless youre a bad person then i couldnt care less what happen to you guys because i dont think bad people deserve any kind of protection what so ever :)
> all levels of security are…
> all levels of security are much appreciated! however not everyone is living in a dictator state
You seem to not have read the basic overview that Tor's effectiveness depends on strength in numbers. No matter where you live or what you do with it, the protection you enjoy depends in part on whether your co-users, bouncing around the global Tor network and out of exit nodes, look like you when you all come out wherever your exit nodes happen to be. I would love so much for you and every newbie to interact with the map of circuits that was in Vidalia. Tor is not meant to act or be used differently for people logging into their local bank or watching meme videos than it is for people facing criminalization by whichever government's present-day incarnation of laws you happen to be subject to offline. Competency in using Tor demands a global perspective. Walk in someone else's shoes -- That is what the mutualist biome you enter when you layer up and travel through the Tor network tries to do for you, digitally, if you just let it.
maybe it is easier to accept…
maybe it is easier to accept it if it has black edges instead of white because it really looks like a bug that makes the window smaler than it actually is. because when you clearly see it is the wrong size it gets really annoying.
but as gk mentioned it is easy fixed for those who want it in its original size. the more security, anonymous and privacy settings it has the better as long as people can choose to opt out from them if they are not nessaccary.
i think the biggest problem is when people are not computer geeks but still want privacy and security they dont know how to change all these things. in that case, next to the blog link there could be a tutorial link for example. with videos and images showing and explaining. im sure there are volunteres out there with some video and photoshop skills who can make an easy understood and still profesional looking guide for those who need.
"Api-ms-win-crt-convert-l1-1…
"api-ms-win-crt-convert-l1-1-0.dll missing" error.Tor does not start(Win 7 64-bit).
why have you guys changed…
why have you guys changed the "new identity" icon? i liked the onion one. no big deal really but it was easier to see and therefore find.
in privacy settings i unchecked all search suggestion results but i still keep getting sucksuckgo up while im writing in the adress bar.
im on kubuntu 19.04
thx in advance
If you don't want to have…
If you don't want to have DuckDuckGo just remove it from your search engines in
about:preferencesor don't set it not as the default engine at least?The onion was _not_ the icon for New Identity but rather the toolbar button into the depth of the Torbutton menu where New Identity was just one of the options to pick from. So, we tried with the broom to give a better visualization for what is going on when you press the New Identity button.
Yes, the broom is better,…
Yes, the broom is better, thank you!
Search suggestions are not…
Search suggestions are not the search engine icon. See how to hide or remove search engines. To hide the drop-down under the address bar, read a previous comment.
RUSTFLAGS=-Clinker-plugin…
RUSTFLAGS=-Clinker-plugin-lto is missing
Hi, when will it be released…
Hi, when will it be released for Android?