New Release: Tor Browser 8.5

[Update 5/22/2019 8:18 UTC: Added issue with saved passwords and logins that vanished to Known Issues section.]
Tor Browser 8.5 is now available from the Tor Browser download page and also from our distribution directory. The Android version is also available from Google Play and should be available from F-Droid within the next day.
This release features important security updates to Firefox.
After months of work and including feedback from our users, Tor Browser 8.5 includes our first stable release for Android plus many new features across platforms.
It's Official: Tor Browser is Stable on Android
Tor Browser 8.5 is the first stable release for Android. Since we released the first alpha version in September, we've been hard at work making sure we can provide the protections users are already enjoying on desktop to the Android platform. Mobile browsing is increasing around the world, and in some parts, it is commonly the only way people access the internet. In these same areas, there is often heavy surveillance and censorship online, so we made it a priority to reach these users.

We made sure there are no proxy bypasses, that first-party isolation is enabled to protect you from cross-site tracking, and that most of the fingerprinting defenses are working. While there are still feature gaps between the desktop and Android Tor Browser, we are confident that Tor Browser for Android provides essentially the same protections that can be found on desktop platforms.
Thanks to everyone working on getting our mobile experience into shape, in particular to Antonela, Matt, Igor, and Shane.
Note: Though we cannot bring an official Tor Browser to iOS due to restrictions by Apple, the only app we recommend is Onion Browser, developed by Mike Tigas with help from the Guardian Project.
Improved Security Slider Accessibility
Our security slider is an important tool for Tor Browser users, especially for those with sensitive security needs. However, its location behind the Torbutton menu made it hard to access.
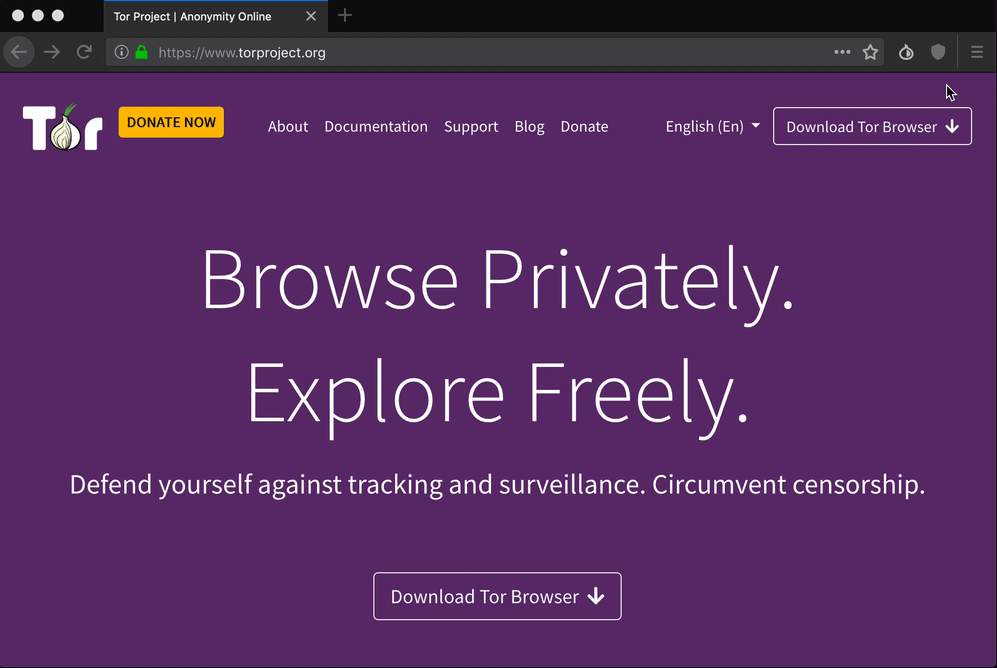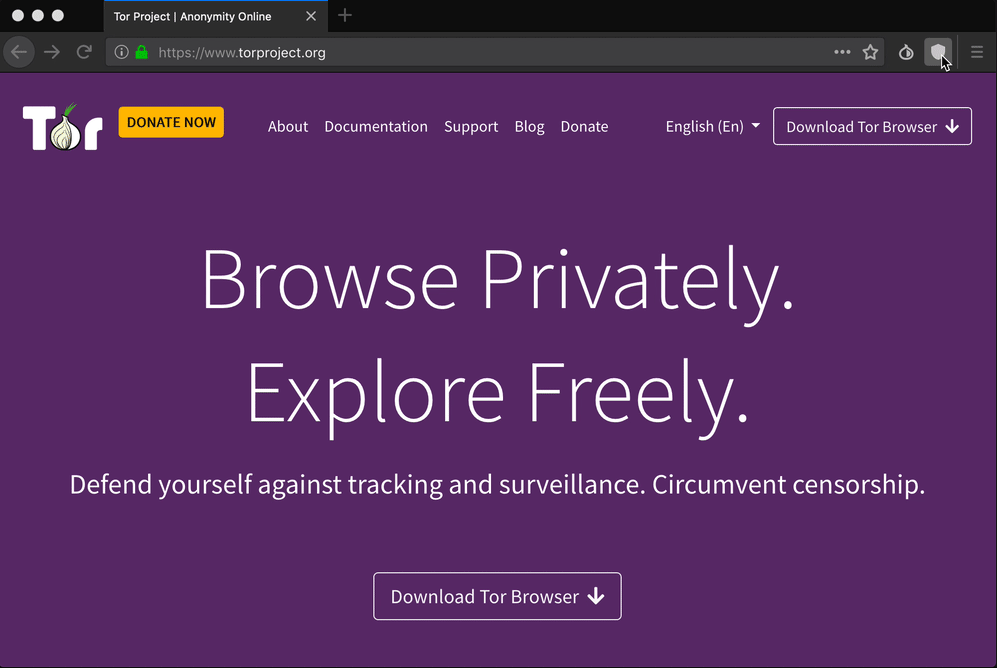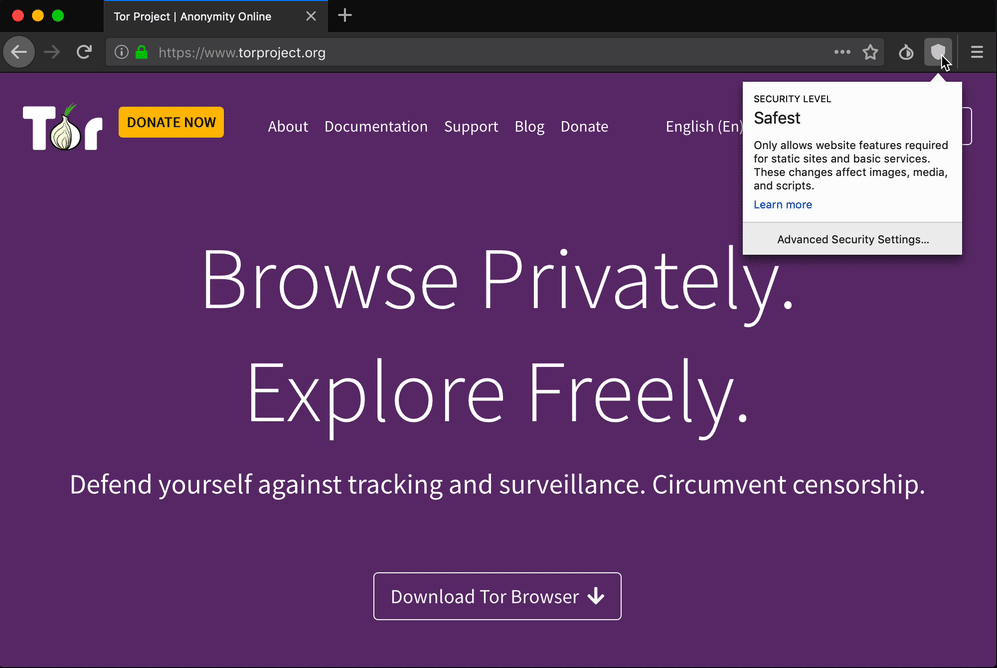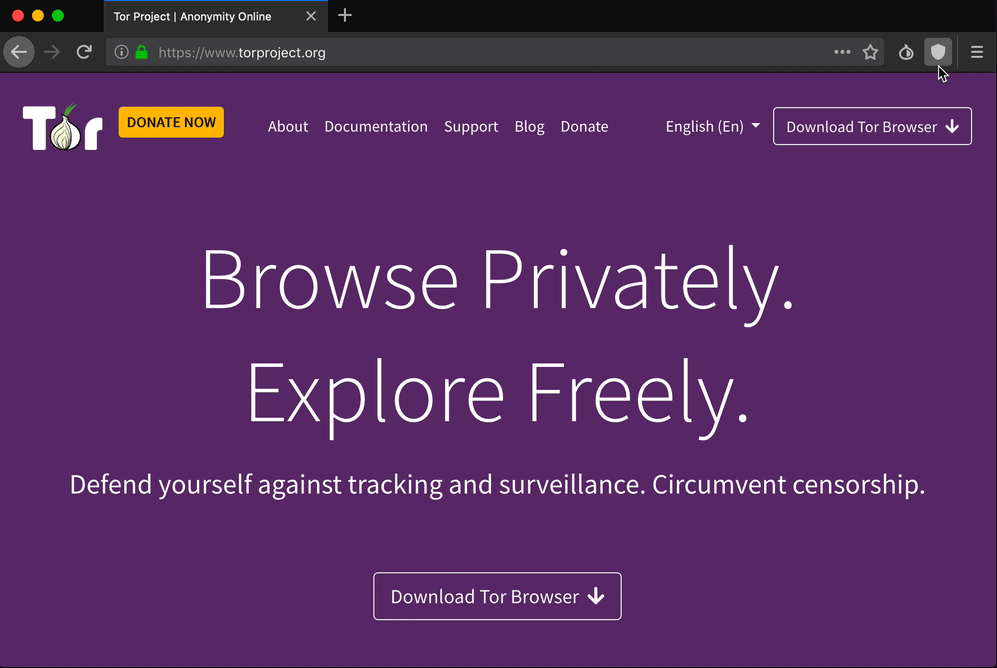
During the Tor Browser 8.5 development period, we revamped the experience so now the chosen security level appears on the toolbar. You can interact with the slider more easily now. For the fully planned changes check out proposal 101.
A Fresh Look
We made Tor Browser 8.5 compatible with Firefox's Photon UI and redesigned our logos and about:tor page across all the platforms we support to provide the same look and feel and improve accessibility.
![]()
The new Tor Browser icon was chosen through a round of voting in our community.
We'd like to give a big thanks to everyone who helped make this release possible, including our users, who gave valuable feedback to our alpha versions.
Known Issues
Tor Browser 8.5 comes with a number of known issues. The most important ones are:
- While we improved accessibility support for Windows users during our 8.5 stabilization, it's still not perfect. We are in the process of finishing patches for inclusion in an 8.5 point release. We are close here.
- There are bug reports about WebGL related fingerprinting which we are investigating. We are currently testing a fix for the most problematic issue and will ship that in the next point release.
- The upgrade to Tor Browser 8.5 broke saved logins and passwords. We are investigating this bug and hope to provide a fix in an upcoming point release.
We already collected a number of unresolved bugs since releasing Tor Browser 8 and tagged them with our tbb-8.0-issues keyword to keep them on our radar. Check them out before reporting if you find a bug.
Give Feedback
In addition to the known issues, we are always looking for feedback about ways we can make our software better for you. If you find a bug or have a suggestion for how we could improve this release, please let us know.
Full Changelog
The full changelog since Tor Browser 8.0.9 is:
- All platforms
- Update Firefox to 60.7.0esr
- Update Torbutton to 2.1.8
- Bug 25013: Integrate Torbutton into tor-browser for Android
- Bug 27111: Update about:tor desktop version to work on mobile
- Bug 22538+22513: Fix new circuit button for error pages
- Bug 25145: Update circuit display when back button is pressed
- Bug 27749: Opening about:config shows circuit from previous website
- Bug 30115: Map browser+domain to credentials to fix circuit display
- Bug 25702: Update Tor Browser icon to follow design guidelines
- Bug 21805: Add click-to-play button for WebGL
- Bug 28836: Links on about:tor are not clickable
- Bug 30171: Don't sync cookie.cookieBehavior and firstparty.isolate
- Bug 29825: Intelligently add new Security Level button to taskbar
- Bug 29903: No WebGL click-to-play on the standard security level
- Bug 27290: Remove WebGL pref for min capability mode
- Bug 25658: Replace security slider with security level UI
- Bug 28628: Change onboarding Security panel to open new Security Level panel
- Bug 29440: Update about:tor when Tor Browser is updated
- Bug 27478: Improved Torbutton icons for dark theme
- Bug 29239: Don't ship the Torbutton .xpi on mobile
- Bug 27484: Improve navigation within onboarding (strings)
- Bug 29768: Introduce new features to users (strings)
- Bug 28093: Update donation banner style to make it fit in small screens
- Bug 28543: about:tor has scroll bar between widths 900px and 1000px
- Bug 28039: Enable dump() if log method is 0
- Bug 27701: Don't show App Blocker dialog on Android
- Bug 28187: Change tor circuit icon to torbutton.svg
- Bug 29943: Use locales in AB-CD scheme to match Mozilla
- Bug 26498: Add locale: es-AR
- Bug 28082: Add locales cs, el, hu, ka
- Bug 29973: Remove remaining stopOpenSecuritySettingsObserver() pieces
- Bug 28075: Tone down missing SOCKS credential warning
- Bug 30425: Revert armagadd-on-2.0 changes
- Bug 30497: Add Donate link to about:tor
- Bug 30069: Use slider and about:tor localizations on mobile
- Bug 21263: Remove outdated information from the README
- Bug 28747: Remove NoScript (XPCOM) related unused code
- Translations update
- Code clean-up
- Update HTTPS Everywhere to 2019.5.6.1
- Bug 27290: Remove WebGL pref for min capability mode
- Bug 29120: Enable media cache in memory
- Bug 24622: Proper first-party isolation of s3.amazonaws.com
- Bug 29082: Backport patches for bug 1469916
- Bug 28711: Backport patches for bug 1474659
- Bug 27828: "Check for Tor Browser update" doesn't seem to do anything
- Bug 29028: Auto-decline most canvas warning prompts again
- Bug 27919: Backport SSL status API
- Bug 27597: Fix our debug builds
- Bug 28082: Add locales cs, el, hu, ka
- Bug 26498: Add locale: es-AR
- Bug 29916: Make sure enterprise policies are disabled
- Bug 29349: Remove network.http.spdy.* overrides from meek helper user.js
- Bug 29327: TypeError: hostName is null on about:tor page
- Bug 30425: Revert armagadd-on-2.0 changes
- Windows + OS X + Linux
- Update OpenSSL to 1.0.2r
- Update Tor Launcher to 0.2.18.3
- Bug 27994+25151: Use the new Tor Browser logo
- Bug 29328: Account for Tor 0.4.0.x's revised bootstrap status reporting
- Bug 22402: Improve "For assistance" link
- Bug 27994: Use the new Tor Browser logo
- Bug 25405: Cannot use Moat if a meek bridge is configured
- Bug 27392: Update Moat URLs
- Bug 28082: Add locales cs, el, hu, ka
- Bug 26498: Add locale es-AR
- Bug 28039: Enable dump() if log method is 0
- Translations update
- Bug 25702: Activity 1.1 Update Tor Browser icon to follow design guidelines
- Bug 28111: Use Tor Browser icon in identity box
- Bug 22343: Make 'Save Page As' obey first-party isolation
- Bug 29768: Introduce new features to users
- Bug 27484: Improve navigation within onboarding
- Bug 25658+29554: Replace security slider with security level UI
- Bug 25405: Cannot use Moat if a meek bridge is configured
- Bug 28885: notify users that update is downloading
- Bug 29180: MAR download stalls when about dialog is opened
- Bug 27485: Users are not taught how to open security-slider dialog
- Bug 27486: Avoid about:blank tabs when opening onboarding pages
- Bug 29440: Update about:tor when Tor Browser is updated
- Bug 23359: WebExtensions icons are not shown on first start
- Bug 28628: Change onboarding Security panel to open new Security Level panel
- Bug 27905: Fix many occurrences of "Firefox" in about:preferences
- Bug 28369: Stop shipping pingsender executable
- Bug 30457: Remove defunct default bridges
- Windows
- Bug 27503: Improve screen reader accessibility
- Bug 27865: Tor Browser 8.5a2 is crashing on Windows
- Bug 22654: Firefox icon is shown for Tor Browser on Windows 10 start menu
- Bug 28874: Bump mingw-w64 commit to fix WebGL crash
- Bug 12885: Windows Jump Lists fail for Tor Browser
- Bug 28618: Set MOZILLA_OFFICIAL for Windows build
- Bug 21704: Abort install if CPU is missing SSE2 support
- OS X
- Bug 27623: Use MOZILLA_OFFICIAL for our builds
- Linux
- Android
- Bug 5709: Ship Tor Browser for Android
- Build System
- All platforms
- Bug 25623: Disable network during build
- Bug 25876: Generate source tarballs during build
- Bug 28685: Set Build ID based on Tor Browser version
- Bug 29194: Set DEBIAN_FRONTEND=noninteractive
- Bug 29167: Upgrade go to 1.11.5
- Bug 29158: Install updated apt packages (CVE-2019-3462)
- Bug 29097: Don't try to install python3.6-lxml for HTTPS Everywhere
- Bug 27061: Enable verification of langpacks checksums
- Windows
- OS X
- Bug 27320: Build certutil for macOS
- Linux
- Android
- Bug 29981: Add option to build without using containers
- All platforms
Comments
Please note that the comment area below has been archived.
Thank you very much Tor for…
Thank you very much Tor for your work. But how is Orbot going to go on from now on? The development has been slow even so far and now, is it in any way going to be replaced with Tor Browser? For me, living in Iran, Orbot and it's features have been essential as more of a filtering circumvention tool than a privacy tool.
There is no plan to replace…
There is no plan to replace Orbot with Tor Browser as they provide different features. Orbot will continue to be developed by the Guardian Project. Orfox however will no longer be developed, and Orfox users should migrate to Tor Browser.
Any plan of removing Orfox…
Any plan of removing Orfox from Play Store?
We plan to provide a final…
We plan to provide a final Orfox update, pointing users to Tor Browser:
https://trac.torproject.org/projects/tor/ticket/29955
It's insane to try to have…
It's insane to try to have multiple instances of Tor running on a phone (assuming it works correctly at all). It will result in nobody having the slightest idea of what's configured for what or what's using which instance for what. It will also make traffic analysis easier by putting some traffic over one ingress connection and other traffic over a different ingress connection. The fact that it's a waste of both local and network resources, while true, is perhaps less important.
The whole business of bundling Tor with a browser has caused UNTOLD user confusion about what does what. Judging by the sorts of questions it generates on Reddit and similar, has probably led to people shooting themselves in the foot. Removing any distinction even in the name has made things far worse.
How do you use the orbot app…
How do you use the orbot app if you have tor browser for android installed? It seems orbot is integrated into the tor browser but i don't see a way to route all traffic to from other apps through the tor network using the orbot built into tor browser for android.
Hi ,where I live lately tor…
Hi ,where I live lately tor is having issues. Normally access was not closed, simply launchig orbot and a circuit were fixed in a bit.Now just clicking on orbot bridge a premade you can choose which and anything it may be able to run .
Moreover behind a vpn a good one.
Nice to met you.
I still can watch real OS…
I still can watch real OS from javascript. Try navigator. Why you can't fix this? This is serious security problem.
Cool new logo.
We have this ticket open for…
We have this ticket open for the issue:
https://trac.torproject.org/projects/tor/ticket/28290
However, navigator.userAgent is not the only OS fingerprinting vector, so fixing this one alone will not be enough to prevent detecting the type of OS.
Your OS can be detected in…
Your OS can be detected in various ways. It's pointless to try and hide it. Your OS reacts differently to many things than another OS would, and they're trivial to detect using Javascript for example.
I have been using Tor since…
I have been using Tor since the days of privoxy, or even earlier, and I can confirm that the long standing and apparently intractable issue with OS detection despite using TB has often been discussed over the years and is (or should be) well known to every long time user.
Some technical issues are very hard to solve, and I think that TP is wise to spend its intellectual capital on devising ameliorations of more serious deanonymization and cybersecurity vulnerabilities.
Speaking of which, a million thanks to the hard working Tails team for promptly patching against the latest round of attacks leveraging speculative execution and other hard wired CPU flaws. The most dangerous has even been specifically confirmed to be usable in real world attacks on Tor Browser users, so the rapid fix was terribly important.
(People who use TB under Debian and who have just updated their Debian should be fine too I think; not sure about other popular OS's.)
js is off
js is off
'The new Tor Browser icon…
'The new Tor Browser icon was chosen through a round of voting in our community'
where, what and who is this community? where did you call for voting?
This was done with an email…
This was done with an email on the tor-project mailing list:
https://lists.torproject.org/pipermail/tor-project/2018-October/002034…
The survey expired. Any way…
The survey expired. Any way to view and download the alternatives again?
Yes, they are attached at…
Yes, they are attached at the relevant ticket.
https://trac.torproject.org/projects/tor/attachment/ticket/25702/tb-ico…
The design team at Tor…
So the design team at Tor Project posted an anonymous survey, interpreted it as a community vote, dropped the colors in favor of monochrome, dropped the the onion outer shape in favor of a circle, made half circles for the inner pattern so to be even farther from an onion's anatomy, checked how many companies/apps have the same logo with sightly different color, and then picked this one.
Apparently there are people…
Apparently there are people who like it, despite you not liking it, me included. Your opinion is not any more important than anyone else's.
Nice that you figured out a…
Nice that you figured out a design team :) You can read more about this process here
https://trac.torproject.org/projects/tor/ticket/25702
Antonela, whoever voted for…
Antonela, whoever voted for Leveled, voted for Leveled with leaves: the 2018 version, which is inside the tb-icon-survey.zip attachment. Little did they know you will chop that poor plant.
I confess that I initially…
I confess that I initially misunderstood the icons and panicked, so for five minutes earlier today I somewhat agreed with you, but by now I've been using 8.5 all day and I have decided that I like the new icons and the new security slider. And I am overjoyed (overjoyed!) that TP now has an offical and apparently working version for one of the major brands of smart phones (Android).
Anonymous survey: how else can TP get feedback from the user community? Because we are anons not registered voters.*
Sometimes I get the impression that some posters do everything they can to think of something anything negative to say about anything Tor Project does, but maybe you just panicked like I did because if you weren't ready for it one could have thought someone had fooled us into installing a malicious modification of TB.
[Edit: slightly cut the post to stay on topic, -GK]
It looks like a target or…
It looks like a target or waves, not an onion.
the titlebar icon is ok, but…
the titlebar icon is ok, but I would have subtracted one of the concentric half-rings.
IMO, it is more distinguishable than tbb's recent faded green FF icon.
I don't notice any other change, though I see the bland b&w "new tor circuit for his site" icon in the "hamburger" menu.
The UI defects are FF/mozilla's - though because Moz has contracted Googlechrome Disease.
(Has any moz designer wondered why FF's urlbar/addressbar possess both overflow *and* a 'hamburger' expander/dropdown menus *adjacent to each other* ?)
Considering usability of most gui apps, icon and toolbar design has declined since macos 8/9 and xp/ie6/food.
> I would have subtracted…
> I would have subtracted one of the concentric half-rings.
3 encrypted relay proxies. 3 layers/rings on its icon.
I missed the election (after…
I missed the election (after GCHQ attacked my email I have good reason to avoid mailing lists which means I am excluded from many things, so a small win for the bad guys there) and like most users I initially thought the new TB look suggested someone messing with the supply chain.
FWIW I have been using 8.5 all day and decided I like the new icons just fine :-)
Awesome news, love the fresh…
Awesome news, love the fresh look. Noticed there's a Nightly icon, are the nightly builds public and if so where can i grab em?
The nightly builds are…
The nightly builds are public, and you can find the link to download them on:
https://trac.torproject.org/projects/tor/wiki/doc/TorBrowser/Hacking#Ni…
Currently the nightly builds don't have automatic updates available, so you will have to manually download and install new versions. However we are planning to fix this in the future: https://trac.torproject.org/projects/tor/ticket/18867
I find it stupid I have to…
I find it stupid I have to get to an onion site to download the nightly...
Onion sites are thought to…
Onion sites are thought to be safer than clearnet sites, in the sense of being less susceptible to various ways in which bad guys can mess with DNS. So being sent to an onion means someone did you a favor.
To avoid possible confusion: the exit node does the DNS lookup if you surf to a clearnet site using Tor Browser, but the exit node can fall victim to the same attacks which might misdirect your browser if you were using FF on your own computer. Onions bypass many of these serious DNS issues.
I am an ordinary Tor user not a dev, so if I said anything wrong above I welcome correction.
(I hope to someday soon see a post in this blog explaining the virtues of onions for cybersecurity. There are no magic bullets but onions can blunt many threats, it seems to me, suggesting that the web would be safer for everyone if every website were an onion site. Of course, we'll have to gracefully grow the volunteer Tor network by several orders of magnitude before that becomes practical. But it seems like a good goal to keep in mind.)
Cool, thank you. It works…
Cool, thank you. It works like a charm.
I have a couple of questions.
1 - Do you plan to implement letterboxing into TBB? If yes, when?
2- Why the new Tor release has not been implemented into TBB? Or did I miss something in the changelog (if so, apologies)
3 - Why you have not yet uploaded the deb packages of the last Tor release (4.0.x) on your repos?
Cheers
1 - Do you plan to implement…
Yes. It will be included in the next alpha (9.0a1) which we will be releasing tomorrow.
We first need to test the 0.4.x series in an alpha release before including in the stable Tor Browser.
I see that https://deb.torproject.org/torproject.org/pool/main/t/tor/ has version 0.4.0.5.
Thanks for your reply. Yes,…
Thanks for your reply. Yes, I have already seen that package as well, but if I "apt update && apt upgrade" no upgrade is showed. Tried this on several machines with different architectures.
Cheers.
That's because Tor…
That's because Tor repository release file (May 17th) still offers 0.3.5 branch to Debian Stretch :
https://deb.torproject.org/torproject.org/dists/stretch/main/binary-amd…
https://deb.torproject.org/torproject.org/dists/stretch/main/binary-amd…
Package: tor
Version: 0.3.5.8-1~d90.stretch+1
Exactly. Linux kernel…
Exactly. Linux kernel updates also remain on the branch you first installed until you view all packages and select a different one. Thank you.
OK, but then the question…
OK, but then the question does not change (OK, it changes a little): why hasn't the Tor repository file been updated yet? I am not saying this is necessarily wrong. Not at all. I just do not understand the reason (I do not recall any other situation where this happened) nor I can find any "statement" about this.
Cheers.
0.4.0.5 stable was released…
0.4.0.5 stable was released on May 3, but all of the distro suite names only offer 0.3.5.x. To make your package manager list 0.4.0.x, edit your package manager's software sources configuration (repositories, sources.list) to download from one of the distributions (suites) named "tor-experimental-0.4.0.x-*" as seen here:
https://deb.torproject.org/torproject.org/dists/
Doesn't work for me. The…
Doesn't work for me. The updated package (4.0.5) is there but it does not appear as upgrade on Synaptic. Please fix it.
The security level indicator…
The security level indicator is a huge improvement, thank you very much for implementing this!
However I was quite surprised to see that the slider (radio buttons now) has been still hidden away in the settings tab. I was expecting to see the option to change the security level right in the toolbar icon's menu itself, instead of merely a further explanation. Any plans to implement this as well?
Again, thank you for all the improvements!
Yeah, hopefully one less…
Yeah, hopefully one less icon...
I dunno. It led me to notice…
I dunno. It led me to notice the setting right below it where OCSP is on by default so THE BROWSER WILL LEAK YOUR ENTIRE CLICKSTREAM TO THE CAs. So it has that going for it.
OCSP stapling is set as…
OCSP stapling is set as enabled and required in
about:config, so if a cert uses OCSP, the browser must only contact the cert owner's website, not CAs or issuers. So it has that going for it.Yes, OCSP is enabled (and…
Yes, OCSP is enabled (and this is good, would you prefer trusting a revoked certificate?). OCSP stapling helps a little here, but it certainly is not enough and I see many OCSP queries during my normal usage every day. There is some information leakage because the browser queries whatever URL is provided in the certificate, but these queries are first-party isolated, so querying the same CA for different sites (first parties) should not be linkable. As the Tor Browser Design Document says:
OCSP requests go to Certificate Authorities (CAs) to check for revoked certificates. They are sent once the browser is visiting a website via HTTPS and no cached results are available. Thus, to avoid information leaks, e.g. to exit relays, OCSP requests MUST go over the same circuit as the HTTPS request causing them and MUST therefore be isolated to the URL bar domain. The resulting cache entries MUST be bound to the URL bar domain as well. This functionality is provided by setting privacy.firstparty.isolate to true.
What about HTTPS *.onion?…
What about HTTPS *.onion? Does OCSP on onions leak metadata to the normal Internet? Don't show my comment if it's a zero-day.
It's not a zero-day. In fact…
It's not a zero-day. In fact we might even get to that during our work on sponsor 27 which stands for onion service related improvements. See: https://trac.torproject.org/projects/tor/ticket/24192.
I certainly agree with you…
I certainly agree with you about that! I expected the slider to be right in the menu. This new arrangement makes it harder to find the security settings in my opinion.
It took 2 clicks when it was…
It took 2 clicks when it was in TorButton. I takes 2 clicks now. I wouldn't say placement makes it harder to find. On the contrary, the new shield icon for security level visually changes shading, indicating the level without having to click anything. Nevertheless, there is always room for improvement.
No, we don't have plans. The…
No, we don't have plans. The reason for the current design is that the button on the toolbar is not meant to easily toggle the slider state. It's meant to show you your current state and to offer the option to (re-)set the level if you really need to. It's a global feature affecting the whole browser session and could lead to surprises if used to just change the level for site X.
> It's a global feature…
> It's a global feature affecting the whole browser session and could lead to surprises if used to just change the level for site X.
So are NoScript and its options, and people want those easily accessible too.
Does not seem to be working…
Does not seem to be working on Android Q Beta 3 in Colombia.
What happens for you? Any…
What happens for you? Any errors you got?
I'm on Android Q Beta 4 and…
I'm on Android Q Beta 4 and both the alpha and stable branches fail at various points. If I use bridges, it fails at the 10% consensus stage. If I don't use bridges, it gets 100% consensus, but no webpages ever load.
Yes, Tor Browser based on…
Yes, Tor Browser based on ESR 60 is not working on Android Q, see: https://trac.torproject.org/projects/tor/ticket/30607. This should get fixed with us moving to ESR 68 soon.
What happened to Saved…
What happened to Saved Logins? All my passwords are gone!
Why on earth would you be…
Why on earth would you be saving passwords in Tor?
Kind of defeats the purpose of using it leaving traces of where you go on your device.
There are degrees of privacy…
There are degrees of privacy and security, but everyone should expect minimum degree.
Tor should be everyone's browser instead of Firefox since it is minimum. But it is broken.
Going out on a limb here,…
Going out on a limb here, but your purposes for using Tor might not coincide with his purposes for using Tor.
Same problem here. And now I…
Same problem here. And now I can't save them anymore.
Me too! Can't (re)set a…
Me too! Can't (re)set a Master Password, either, and no passwords are ever saved...
To be honest, I don't know…
To be honest, I don't know right now. As far as I can tell this was no intentional change. We have https://trac.torproject.org/projects/tor/ticket/30565 to track that.
Just a suggestion: Use a…
Just a suggestion: Use a safer password manager such as KeePass or a port/fork of it.
What happened to Saved…
What happened to Saved Logins? It is now empty although the file logins.json still is there
We're currently…
We're currently investigating this issue here: https://trac.torproject.org/projects/tor/ticket/30565
Please feel free to comment there with any details about what you're experiencing. There's also a workaround in the comments there.
Awesome update for Android…
Awesome update for Android.
I have been having all kinds of trouble with it on my phone but everything I looked up was already known and being worked on.
Glad to finally have a stable version for my mobile devices thank you very much for all that you do.
I myself do not use Android…
I myself do not use Android but find it very encouraging that 8.5 is working well on Android phones.
One question: does the Huawei-USG catfight impact Tor users in CN who own Huawei branded phones? I suspect the answer is likely "Yes", and that underscores the importance of finding a donor eager to fund a Tor version for a brand of phone popular in CN. Or am I being unrealistic about Tor Project's chances of helping people in CN?
Huawei is basically mobile…
Huawei is basically mobile hardware. As long as they run software OS based on Android, they can probably run Tor Browser Android.
Lovely. Thank you, Tor.
Lovely. Thank you, Tor.
As a matter of preference I…
As a matter of preference I prefer to have all my icons on the left side of the search bar like it used to be. Is it safe to manually move them back on the left or does that affect the browser fingerprint?
Thanks
I think simply moving them…
I think simply moving them does not affect the fingerprint. To a similar question about flexible space that is horizontal, gk replied, "Yes, that should be fine."
However, I don't know about removing or adding the title bar, menu bar, or bookmarks toolbar. I don't know about changing the icon size "density" or themes. Those things possibly affect vertical height.
My own question:
Does keeping open the Find bar (Ctrl+F) along the bottom of the window affect my fingerprint? Because I keep it open most of the time.
Yes, having additional bars…
Yes, having additional bars open affects the window size reported, see: https://trac.torproject.org/projects/tor/ticket/16456.
@gk so do you confirm it is…
@gk so do you confirm it is OK to move plugins icons from right to the left or wherever we prefer, but it's better to avoid showing the bookmarks bar for example?
Yes.
Yes.
so to use bookmarks much,…
so to use bookmarks much, keep the bookmarks manager window squeezed to the side of the screen?
Or Alt-Tab between them. …
Or Alt-Tab between them. Letterboxing will eventually take care of it so you won't have to anymore.
I'm still getting NoScript…
I'm still getting NoScript popups constantly, and it seems any settings to "always block such and such request" are reset after closing down the browser.
Are there any plans to block all XSS requests by default or otherwise improve this?
Yes, this should be much…
Yes, this should be much better with the upcoming NoScript release (scheduled for today).
@ gk: Many thanks for all…
@ gk:
Many thanks for all your work but PUH-LEEZ explain to me (no doubt I am an idiot but I truly do not find it easy to guess how to get this done) how to check that NoScript is even working in my TB 8.,5 (currently running in Tails 3.14 but I also use Debian). I cannot see a NoScript icon and as far as I can tell from checking add-ons, NoScript should be present but has not been updated since 1 Jan 2019. That sounds bad. Has NoScript been disabled in my TB and if so how can I get it back?
What NoScript version is…
What NoScript version is shown? If it is not 10.6.2 what happens if you click on the gear icon on
about:addonsand do a manual check? If you did not mess with Tor Browser but just set the slider to a non-default level you can easily check whether NoScript is working by trying to watch a video on Youtube. That should not be possible out-of-the-box then. Otherwise, if you feel cautious and feel you need a NoScript icon somewhere then it's perfectly fine to customize your toolbar by dragging that icon onto it.Oh no, I see 10.6.1. Maybe…
Oh no, I see 10.6.1. Maybe that is because I am using Tor Browser 8.5 shipped with Tails 3.14?
What worries me is that I do not see a NoScript icon in the bar at upper right near the UBlock and Tor icons. However, I tired what you suggested and with "Safer" setting it seems my attempt to watch a Youtube video failed, so NoScript probably IS installed and working.
In the past NoScript showed a fearsome monster icon announcing it was blocking 3 out of 5 scripts or something like that. Which people I know hate but I liked to see it. So the vanishing of this is a feature not a bug?
By the way:
Apologies for panicking when I first tried 8.5. I was in a rush and completely misunderstood that the new icons were supposed to be there and that the security slider had moved. I think the new way is better than the old way.
Also, while the onion mirrors appear to be working for Buster can you try to liase with Debian Project to make sure nothing breaks when Buster becomes new stable? Also, can you ask them to look into possibly making popcon torified via Whisperback or something like that. Some things I use all the time vanished from Buster, possibly because privacy minded Debian users fear what an attacker with near global access could learn about our system from an unencrypted popcon report.
The vanishing of the…
The vanishing of the NoScript icon is a feature. You should not need to mess with NoScript's settings at all. That's been part of our security slider redesign, see: https://gitweb.torproject.org/tor-browser-spec.git/tree/proposals/101-s….
Of course, if you want to see the status output NoScript gives you (or want to deal with per-site permissions which is not implemented at the moment), just customize your toolbar and put the icon back.
perhaps 1/3 of those xss…
perhaps 1/3 of those xss alerts ask about the exact domain of the link I had deliberately clicked to open... unless there is a difference - http vs https?
The security levels are…
The security levels are listed in reverse order from before on the slider. I almost started browsing in Standard mode when I meant to be in Safest (now on bottom). Users have been trained for many years to expect Safest on top/highest. Sudden reverse order is somewhat disorienting.
I am unable to install this…
I am unable to install this update the usual way and Tor Browser is asking me to download a fresh copy. Is this going to be fixed?
On what operating system are…
On what operating system are you on? If you set
app.update.logtotrueand then open the browser console with Ctrl + Shift + J and then perform the update check by clicking on the hamburger menu -> Help -> About Tor Browser do you get some error messages that could explain what is going on?Was the DDOS'ing attack…
Was the DDOS'ing attack ticket addressed in any way on this update?
No, this updated only ships…
No, this updated only ships fixes browser related updates and the DDoS you are referring to is probably the one tor needs to deal with.
Watch tor changelog, not tor…
Watch tor changelog, not tor-browser changelog.
You say "Though we cannot…
You say "Though we cannot bring an official Tor Browser to iOS due to restrictions by Apple, the only app we recommend is Onion Browser, developed by Mike Tigas with help from the Guardian Project."
What restrictions prevent you from bringing an official Tor Browser to iOS? I imagine there would be differences between your ideal iOS Tor Browser and what Onion Browser does. Can you talk about that?
https://blog.torproject.org…
https://blog.torproject.org/tor-heart-onion-browser-and-more-ios-tor has some good information here.
Is there an arm64 version…
Is there an arm64 version for Tor Android?
Not yet, alas. We have https…
Not yet, alas. We have https://trac.torproject.org/projects/tor/ticket/28119 to track that.
I've uploaded a test version…
I've uploaded a test version at https://trac.torproject.org/projects/tor/ticket/28119#comment:7. Let us know if that one works for you.
Android packages don't work …
Android package don't work - never installs. Latest LineageOS on angler:
$ adb install -r tor-browser-8.5-android-x86-multi.apk
Performing Streamed Install
[waited > 5 minutes]
^C
Thank you
What happens if you install…
What happens if you install it with Android own means? Like from Google Play or getting it directly from our website to your phone?
I was using the wrong…
I was using the wrong package (needed arm instead of x86). Thanks.
there is still a problem in…
there is still a problem in getting a new "request a bridge from torproject.org" when i request it using my Mac OS running high sierra. the same brige is continually provided.
XX.XX.XX.XX:PPPPP etc..
We are working on it. You…
We are working on it. You can track that in https://trac.torproject.org/projects/tor/ticket/30441.
Please stop publicizing IP…
Please stop publicizing IP:port of bridges.
Indeed, corrected.
Indeed, corrected.
Здравствуйте! Я из России…
Здравствуйте! Я из России. Есть такие программы, называемые "песочницами", они после перезагрузки сбрасывают состояние операционной системы к изначальному - я тут подумал - может быть в Тор сделать нечто подобное? Это будет получше чем механизм "Не сохранять историю" так как всё что делал пользователь в сети будет стёрто после выхода из Тор
"I am from Russia. Eat this…
"I am from Russia. Eat this program." ... No wait, that can't be right, we need a real Russian translator.
"Hello! I'm from Russia…
"Hello! I'm from Russia. There are such programs called "sandboxes", after reset they reset the state of the operating system to the original one - I thought here - maybe in Tor to do something like that? This will be better than the “Do not save history” mechanism since everything that a user has done on the network will be erased after exiting Tor"
(Google translate. I wish there was a good alternative.)
Tails and virtual machines (VM) are sort of like sandboxes....
Thank you for the…
Thank you for the translation! The OP's report turns out to be a useful question, I think.
I endorse the suggestion to try Tails, which incorporates AppArmor so it has some valuable sandboxing. I was recently told that people in Russia *are* still able to use Tails and hope that information is not out of date.
Tails is a complex Debian-based "amnesiac" and torified operating system which works out of the box on any 64 bit PC or laptop.
You boot it either from a DVD you have burned from the latest ISO image or from a USB. You can enhance a Tails USB by creating an encrypted data partition (by pressing a few buttons which calls their very cool script) and you can install additional software using Synaptic in the usual way (but you should try to limit this to minimize the risk of installing something which has not been vetted for use in Tails).
Tails USBs are supposed to be easier to update because you do not need the full ISO image for the next release, but I find that the best way to update a Tails USB is to obtain the ISO image, verify the detached signature, burn to DVD, boot from that while disconnected from the Internet, and then use the handy script to "clone running Tails" onto the USB as an "update" not "reinstall". This preserves the data and always works.
"Amnesiac" means Tails tries not to leave traces on hardware of your activities. Very important if you are whistleblower or human rights worker or a reporter. The idea is that you boot Tails from a DVD and store any data on a seperate encrypted USB data stick, or boot Tails from a USB with an encrypted volume holding your data. You can use Tails both for websurfing and chatting, or in "off-line mode" for the most dangerous stuff like preparing a leak or writing a news report.
(As we see from the charges the USG has dumped on Assange under the 1917 Espionage Act, one of the worst of all the many horrid laws the US Congress passed during some wartime panic and never repealed, writing the news is now very dangerous "even in the USA".)
Anyone can obtain the current tails ISO image for free at tails.boum.org.
Tails Project is a sister project of both Debian Project and Tor Project and all three projects correlate their releases. All of them have responded quickly to such emergencies as the latest speculative execution attacks and other horror shows.
I'm concerned about the new…
I'm concerned about the new security level button. When you click it, it goes to the settings page and right under that is a bunch of options that look really tempting to enable (who wouldn't want to click a check box that says it "blocks deceptive sites"?). This is exposing millions of users to options that make them easier to track by making them easier to fingerprint.
I think having the slider available directly when you click the icon is better because it doesn't make people think that the slider is just one of many different customizations that you are encouraged to make to the browser.
Also I don't really like the new icon but I guess I'll get used to it. That's just aesthetics.
Thanks for the feedback. We…
Thanks for the feedback. We have been thinking a lot about your idea but ultimately decided against it because the risk we saw is that the slider could easily be used for just quickly toggling the slider level as needed for the current site neglecting that it is a browser-wide feature affecting all the other tabs open, too. So, foremost the icon on the toolbar is meant to inform you about your current settings. If you need to change the level (which is meant to not be done very often) then you can do so on the advanced settings.
(Not OP) > the risk we saw…
(Not OP)
> the risk we saw is that the slider could easily be used for just quickly toggling the slider level as needed for the current site
I can kind of understand that. However experienced users know full well that it's a browser-wide setting. You could argue it's a good change because it makes it harder to change the slider mid-session, which isn't really recommended. However this change also makes it harder to change the slider level even after a new-identity restart, too. ('click onion, move slider' vs. 'click shield, click more settings, click security level, close preferences tab')
Personally I think I would have opted to keep the existing slider button and popover dialog, and just made it so the button icon changes with the active security level. However it's not a big deal for me, only because I don't mind using multiple TBB instances/installations at different security levels.
I'm all for making TB easier for new users. But remember that, I'm quite sure, the majority of your userbase is existing users. It's important to think about them too.
> I don't mind using…
> I don't mind using multiple TBB instances/installations at different security levels.
Obligatory warning for most people: https://support.torproject.org/tbb/tbb-36/
Oh! What's the reasoning…
Oh!
What's the reasoning behind this?
Behind the warning? It might…
Behind the warning? It might subtly break things for you if you install multiple versions of Tor Browser, e.g. on macOS (see for instance: https://blog.torproject.org/comment/282122#comment-282122). Or one messes up by using the wrong Tor Browser instance for site X. Or...
Okay, okay, I get the hang…
Okay, okay, I get the hang of it :)
Thanks for your reply!
Didn't know this, but, as…
Didn't know this, but, as long as it works and nothing breaks, is there still any risk? It works fine for me. Anonymity-wise, I think it would be a good thing, because it encourages more isolation and more frequent new identity clicks. If you use the same instance and keep it open a long time, you're dirtying up its fingerprint/cookies/etc. It also because they're separate processes it might reduce damage of certain attacks. The only downside I see, other than something breaking, is extra resource usage. Am I missing something?
Even better is to use qubes and open each TB instance in its own whonix VM. (I use qubes but my PC doesn't have enough RAM for a lot of VMs at the moment, so I run several TBs in one VM)
What about using a dedicated…
What about using a dedicated page for that, or a pop-up? My main concern isn't so much that users won't find it as easy to change, but that they're being exposed to settings they should never touch.
I don't know. I think we…
I don't know. I think we accommodated your concern by making the toolbar icon mainly an icon to *show* the current state. Having "Adavanced Security Settings" is IMO already an implicit warning for users who do not know what they are doing.
I would support a dedicated…
I would support a dedicated page and a floating warning on the other pages because the other pages are accessible from that page in the sidebar for navigation. A pop-up would make it like the old icon that developers seem to want to move away from. They want to publicize its current status and integrate the buttons into the browser but don't favor making the security level easier to change. But learning how to properly use "Safest" should not be hidden but encouraged. There is a link in the shield button to Learn More, but it should be prefaced by informing the user there are levels of higher security than the one in play out of the box, "Standard", and three levels in all. Encourage them to Learn More; don't frighten them by saying "Advanced Settings".
"because the risk we saw is…
"because the risk we saw is that the slider could easily be used for just quickly toggling the slider level as needed for the current site neglecting that it is a browser-wide feature"
May you are right with "could easily be used",in general i don't think so, but the trend from the (Big)Soft business to hide settings deep in menus or mostly cut control is really annoying.
Please make this hide and cut game with this wonderfull soft(TBB), too.
Not sure what you mean, but:…
Not sure what you mean, but: we made the slider more accessible for *both* advanced users and less advanced ones and got it out from being buried somewhere in Torbutton's settings to make it easier to use. So, no, we did not bury it anywhere in the browser, quite to the contrary. Seems to me like a win-win actually. :)
What I absolutely miss in…
What I absolutely miss in TBB is the ability to lock the browser with a password when minimized. Do you plan to implement such a function?
That's not planned yet. I am…
That's not planned yet. I am not even sure that's actually doable. Does Firefox offer such an option?
I think the new icon and…
I think the new icon and layout is great.
But after the update, my saved password was lost.
I'm in big trouble now.
And when can the settings of the noscript be saved?
For the password/login…
For the password/login problem we have https://trac.torproject.org/projects/tor/ticket/30565. Saving NoScript settings to a file is tracked in https://trac.torproject.org/projects/tor/ticket/27825. Persisting settings can already be done by setting
extensions.torbutton.noscript_persisttotrue, but that is *not* recommended.Hello! Thanks for your…
Hello!
Thanks for your efforts!
Tor browser is now showing up on the Google Play Store.
But, I have seeing something unusual or questionable.
It is showing that Released on May 21, 2019.
Updated on May 19, 2019.
How about it!?
How can an app get updated before it is released???
Is there something went wrong?
It's not clear to me what…
It's not clear to me what Google is tracking here. We probably have uploaded the .apk on May 19th already and made some last tests and pressed the "Release" button on May 21st. Not sure whether there is anything we can do to improve the situation.
So, to sum up, I don't think there is anything wrong here in the sense of someone tampering with Tor Browser.
Ow! Thanks for your reply…
Ow!
Thanks for your reply.
Best!
Ha. Yes, indeed. It's a…
Ha. Yes, indeed. It's a little funny Google is leaking this information. For this release, we used Google Play's "Internal Testing" channel before we released it publicly, so first we uploaded it on May 19 and after testing it we released it for everyone (coordinated with the desktop release) on May 21.
1. What happened with fonts…
1. What happened with fonts in TB for Android? Latin characters are ugly and cyrillic characters are extremely ugly.
2. I use Orbot for some other applications and don't want to delete it. However I don't want to keep multiple tor instances in my phone memory. This forces me to use this workflow: When I need TB, I run it, it connects to the network (while Orbot is running to serve another apps) and after I done something with it I should explicitly quit and disconnect.
3. Part 2 leads to another thing that I liked in separate Orbot/Orfox: Orfox is instantly ready to go due to Orbot is running as a service for all apps. With TB for Android I forced to wait while it connects to network.
Regarding to 1. is that new…
Regarding to 1. is that new in the stable version or does that show up in alpha versions as well? It's not exactly clear to me whether you tried the alphas before and are now suddenly seeing issues with the stable release.
Regarding 2. and 3.: Yes, there are trade-offs here. It's a very awkward user experience to download an app and then when starting it you got told "Oh, by the way you need another app installed in the first place to run your app". That's pretty confusing to new users while old Orfox users would be totally fine with that. We opted for following the desktop approach to provide a unified experience across all the platforms we support and making sure you have a running Tor before you start browsing. What happened in the Orfox case when Orbot was installed but currently not connected to the Tor network was that you would get weird proxy connection errors with no further explanation about what is going on which is very confusing as well.
1. That was in alpha…
1. That was in alpha versions too. I haven't used it too much, I've installed some builds. So when the stable release came out I installed it, but the fonts issue remains.
2 and 3. Generally I agree with you that it is better for newcomers. I just described my experience with that.
Anyway, thanks for all that, good work!
Could you file a bug about…
Could you file a bug about the font issue in our bug tracker (https://trac.torproject.org/projects/tor)? Or add some screenshots here showing the problem?
Didn't you guys agree the…
Didn't you guys agree the bundled Tor use will be made optional so power users can toggle it off if they've got Orbot? Can you please reconsider? I've been waiting for the stable version for that to materialize. The bundled Tor isn't working for me so I need this urgently to upgrade.
We agreed that we remove…
We agreed that we remove Orbot, which we did. I don't think we want to go back to a browser that needs an additional app to be usable at all. Imagine the situation for someone who just learned about Tor Browser. It sounds exciting, right? But suddenly when run you get told "Hey, in order to run this awesome up you actually need to install first another awesome app". That's an awful user experience we don't want to have. Rather, we want to provide the same flow across all platforms we have.
Why is the bundled Tor not working for you?
It did after I removed and…
It did after I removed and reinstalled the app.
I am not saying make Orbot a dependency for everyone again, but just have an option even buried in the prefs that allows it.
We have https://trac…
We have https://trac.torproject.org/projects/tor/ticket/28786 for running a Tor, say, system-wide and not the one shipped with Tor Browser.
Thank you for the new v.8.5 …
Thank you for the new v.8.5 . Mine (Windows x64bit) is running smoothly.
what happended to the idea…
what happended to the idea of a user months ago to make securityslider icon colorful? red-yellow-green like a traffic light.
Don't know if this played a…
Don't know if this played a role but some people are red-green colorblind. In fact this is not uncommon in human males.
Colors may be ambiguous. …
Colors may be ambiguous. Which level will be red? What does it intend to mean versus what users think it means? Also, some countries may have different meanings for colors.
I have no slider. regular…
I have no slider. regular mouse click on the new black shield icon shows the current setting "safest" with a little text information and 'advanced settings at bottom. advanced setting goes to options/preferences. There are only radio dots for each of the three "slider" settings.
using tbb 8.5 (based on 60.7.0esr)
That's good and expected. We…
That's good and expected. We moved away from the slider to three radio buttons for the three security levels.
tbb 8.0.9: browser…
tbb 8.0.9: browser.safebrowsing.id ; Firefox
tbb 8.5: browser.safebrowsing.id ; navclient-auto-ffox
if somebody enables safebrowsing navclient might be no good choice.
On Android: system language…
On Android: system language leaks to sites
Which site did you test with?
Which site did you test with?
Any site that shows their…
Any site that shows their content based on the system's language. Twitter, Youtube, and so on. The language is also shown on panopticlick.eff.org, for example. System language is Russian.
Okay, I opened a ticket for…
Okay, I opened a ticket for this. I'm not sure it's a bug. https://trac.torproject.org/projects/tor/ticket/30605
Thank you for the new stable…
Thank you for the new stable version. However, I expected to control which kind of JavaScript I could block, XSS attacks and so on with No Script and, because of the new layers of security, I only have two options: blocking all JavaScript, which doesn't seem me very useful in some pages, or blocking JavaScript in only pages which aren't HTTPS. Is there any kind of solution?
You can customize NoScript…
You can customize NoScript blocks in the NoScript icon as before. NoScript is reset when you click New Identity, change the Security Level shield, or close Tor Browser. When you begin a New Identity session, set your Security Level. As you browse, allow what you need temporarily in NoScript. Reset NoScript when you don't need it. The longer you browse with NoScript customized, the more your activity can be identified as the same person.
NoScript is reset when you…
In fact that's not the case right now: https://trac.torproject.org/projects/tor/ticket/27732
Good to know. Thank you…
Good to know. Thank you. Everybody, if you mess with NoScript, hit Revoke Temporary and look at Per-site Permissions when you start a New Identity!
Russian version on Android:…
Russian version on Android: Browser uses Yandex Search (Duckduckgo not selectable) and pages are in Russian instead of English.
Thanks, I created a ticket…
Thanks, I created a ticket for this - https://trac.torproject.org/projects/tor/ticket/30606
I think the Tor Project…
I think the Tor Project should discourage downloading the Android app from F-Droid unless it is through an official repository, and should also request F-Droid to take down the versions of the app from their main repository. As you know, the main F-Droid repository apps are signed with an F-Droid key not from the Tor Project (as is all other apps in the repository). This should make the app not considered an official release and should be considered a security risk. What makes it worse, as far as I know, these apps are signed with a private key that resides on the F-Droid server. And on top of all that, you then have people with Tor Browser for Android apps signed with different keys making them incompatible for updates depending on what source they originally downloaded from.
I haven't tried checking yet, but I assumed the app on the official Guardian Project repository is signed with the same keys as the app on Play or the one that can be downloaded from the Tor Project site. If so, this should be become the Tor Project's official repository to obtain the app and all apps signed with unofficial keys be removed. (And of course, the Tor Project can have their own official repository, which should be the only means anyone obtains the app on F-Droid.)
The Tor Project (as on the Tails site) promote and have well-documented pages rightly telling people they should verify their downloads and showing them the steps to take to do so. So there should be no encouragement for people to download apps from a repository signed with keys that are not official from the Tor Project developers. I would also bet many people don't even know the apps on the main F-Droid repository are not officially signed by the apps' developers. Many probably think the apps are uploaded by developers like they are on Play, and F-Droid has no indication the app they are installing are not officially signed by the app's developers. All of this this is very misleading and heightens security risks.
The Tor Project should either make their own official F-Droid repository or make the Guardian Project's repository official, and then have instructions on torproject.org on how to add the repository to F-Droid, and then request that all other apps not officially signed by Tor developers be taken down.
Indeed, currently we provide…
Indeed, currently we provide Tor Browser on F-Droid through our partners at the Guardian Project. They run their own F-Droid repository and they upload the apk we build (the same one available on our website and on Google Play). Hopefully, in the near future, we'll upload the apk we build directly to F-Droid (we're making progress on this, see https://trac.torproject.org/projects/tor/ticket/27539) and F-Droid will distribute our signed apk after it reproducibly builds it.
that's good news. thanks.
that's good news. thanks.
CVE-2019-9815: Disable…
Of course, you can say that you cannot do anything with it, but it is your responsibility to warn users that they should disable HT/SMT on Intel CPUs to use Tor Browser safely.
"Systems affected: Mozilla…
"Systems affected: Mozilla Firefox versions prior to 67, Mozilla Firefox ESR versions prior to 60.7" (source)
"Fixed in Firefox ESR 60.7" (source)
Tor Browser 8.5 --> hamburger menu --> Help --> About Tor Browser
"8.5 (based on Mozilla Firefox 60.7.0esr)"
I'm using what is allegedly…
I'm using what is allegedly the "most secure operating system" - OpenBSD and don't understand this:
"Sometimes the most recent version of Tor Browser on OpenBSD is behind the current release. The available version of TB on OpenBSD should be checked with:
pkg_info -Q tor-browser
"
That command returns tor-browser-8.0.9 for me on OpenBSD 6.5 -current.
But https://2019.www.torproject.org/download/download-easy.html.en shows only versions "8.0.8" is available for release on other platforms. Then there's https://www.torproject.org/download/ which offers versions "8.5". What version I'm supposed to be using remains a mystery. I have a flashing exclamation mark over the onion icon in Tor Browser, but when I select it, the only options are New Identity or Settings. You need to make this a lot less ambiguous and confusing, please.
You should use the one on…
You should use the one on https://www.torproject.org/download/. There you find the current stable and alpha versions. https://2019.www.torproject.org/download/download-easy.html.en points to an archived version of our website. Yes, you have the flashing icon as a hint that the current version you run (8.0.9) is outdated and needs an update (8.5).
2019.www.* is the old site. …
2019.www.* is the old site. Don't expect it to be up to date.
pkg_info queries an OpenBSD repository mirror. Mirror servers take time to synchronize with each other. Maintainers of OpenBSD, not Tor Project, prepare packages for those repositories. Tor Project does not manage official OpenBSD OS repositories just like it does not manage official Linux OS repositories. Tor Project manages a Tor Project DEB repository. The most recent release of Tor Browser is 8.5, but the most recent snapshot of tor-browser on OpenBSD mirrors is version 8.0.9. Fortunately, BSDs ship an ABI that can run binary executables that are built for Linux. Download Tor Browser 8.5 from torproject.org, and search for how to run a Linux binary/program on OpenBSD or FreeBSD. Otherwise, install 8.0.9 from OpenBSD, and wait for their maintainers to update their mirrors to 8.5, the version immediately after 8.0.9.
This blog post page is so…
This blog post page is so screwed up in Tor without Javascript enabled. It goes into an insane page reload loop that makes it impossible to scroll/view content. I wonder if any Tor developers actually use Tor browser without Javascript or have done basic QA on this site. Dissapointed.
I've never experienced what…
I've never experienced what you describe.
For a while beginning with when blog.torproject.com 'installed' its current commenting system, the "Reply" link on each comment disappeared after I had posted *one* comment on a blog post. That strange defect went away one or more years ago.
This may be useful for comparison to your TBB circumstances: I'm using release TBB in Windows 7 with TBB Security Level set at "safest" and NoScript set to rarely allow any domains - and those only temporarily. (I'd like a NoScript timer feature, BTW)
Also, though NoScript's WebExtension rewrite lacks as much control as the pre-Quantum NoScript had, I try to set NoScript "universal" ("permanent") settings to their strictest.
Exception: I had checkboxed allow bookmarklets in pre-Quantum NoScript.
Further off-topic...
Quantum's crippled NoScript forces me to create additional keyword searches ('searchmarks'? 'keymarks'?) as workaround substitutes for *some* bookmarklets. The pragmatic quantity of keyword 'searchmarks' is limited by my memory of the "unusual" keyword that each keyword 'searchmark' requires.
> I've never experienced…
> I've never experienced what you describe.
I can confirm both that this behavior does occur with slider on "Safest" and that it has been discussed in the blog before.
@ the OP:
I have found that setting the slider to "Safer" fixes the problem. If you forget to reset the slider before coming here, just hit "new identity", change the slider, and reenter the URL.
That's https://trac…
That's https://trac.torproject.org/projects/tor/ticket/22530.
I have just downloaded and…
I have just downloaded and installed Tor Browser 8.5 and NoScript extension is missing. So I cannot quickly check (by hovering the mouse over the icon) what is the 'script situation' with the current site. Should I install it?
Plus on the about:preferences#privacy page
Cookies are also enabled by default
Tracking protection: 'never'.
Prevent accessibilitiy services: unckecked ...
All the base settings seem to be risky...
How did you decide the…
How did you decide the extension is missing? We just don't show it on the toolbar anymore to not confuse user's with NoScript settings. It should show up in `about:addons`, though. And, sure, you can just customize your toolbar and drag the icon back to it if you think that's something you need.
All the settings you mentioned seem to be as they should.
> We just don't show it on…
> We just don't show it on the toolbar anymore to not confuse user's with NoScript settings.
Ah. I wish this I had known this before I panicked. I think I agree with the change but the timing (just after the ferocious NoScript disabling fiasco) was unfortunate.
Developers, note that OP's…
Developers, note that OP's perception of "risky" base settings and wanting to customize them are because they scrolled on the
about:preferences#privacywhich is opened by the new security shield.Why does the Tor app for…
Why does the Tor app for android need permission to access photos, music and documents?
The app doesn't actually…
The app doesn't actually need to access these files (photos, music, documents). Unfortunately, this is how Google explains apps requesting access to the external device storage. The device storage is where files are downloaded. Therefore, this permission is not really about accessing these files but being allowed to save files. We opened a ticket for explaining why we request each permission - https://trac.torproject.org/projects/tor/ticket/30604
Update HTTPS Everywhere to…
It updates rulesets to 2019.5.20, and then Firefox updates it to 2019.5.13 version which overwrites rulesets to 2019.5.13. Amazing.
I like the onion logo on the…
I like the onion logo on the left side of the url bar and I also liked the security slider. Not sure why those needed to be messed with
You can customize your…
You can customize your toolbar again and drag the icon back to the left side or, really, wherever you want to have it. We "messed" with the slider to make it easier accessible and more usable for everyone.
The toolbar redesign on…
The toolbar redesign on desktops is a big disappointment. Confusing the user by removing the noscript button (with a, well, familiar interface) is not the right thing to do, in my opinion. Noscript shouldn't be wrapped into something else. Also, the new security slider(?) button is useless, for it just indicates the current security level (one have to click on the button to just see the level) but doesn't allow to change it. That was the intention, as far as I can see, and this is really odd.
> Noscript shouldn't be…
> Noscript shouldn't be wrapped into something else.
It's no more wrapped than it was before. It's just the icon was moved. NoScript is for power users and probably lowers usability for new users. You can drag the icon back to the toolbar, although I sort of agree that a new installation ought to tell users that a NoScript icon is available.
> one have to click on the button to just see the level
The shading on the icon changes. None, half, and totally filled in.
> doesn't allow to change it.
Security level icon -> Advanced Security Settings...
what prefs in Tor Browser…
what prefs in Tor Browser for Android can I set to stop the Orbot connect screen? on desktop I can disable Tor Launcher, but I can't do it here.
Without a new identity button I have to quit and restart Tor Browser every time I want to cleanup after a session.
Yes, we don't have the…
Yes, we don't have the option yet to not use the Tor shipped with Tor Browser for connecting to the Tor network. https://trac.torproject.org/projects/tor/ticket/28786 is for this task. And, yes, we did not get to implement a New Identity option either, alas. https://trac.torproject.org/projects/tor/ticket/28800 is for that.
Icon looks like half-covered…
Icon looks like half-covered target.
Did Tails fork its version…
Did Tails fork its version of Tor Browser 8.5 from the Tor Project version?
In Tails 3.14 (current version of Tails), Tor Browser icon is purple (Tails themed) not green (Tor themed) and Noscript icon does not appear. Further, the security slider is disguised in a new icon in TB. Further checking add-ons in TB shows that the version of Noscript was last updated on 1 Jan 2000 which cannot be right. Further, Noscript appears to be disabled in all security slider settings.
Anyone know what is going on? I cannot find an explanation at tails.boum.org so I ask here.
Sorry, sorry, sorry, I was…
Sorry, sorry, sorry, I was in a rush and did not even realize that the blog was not one I had read before. Reading it solved my confusion except for the missing NoScript icon in the toolbar, but in another comment above gk explained that too.
After using TB 8.5 for an hour I decided I like the new slider, the new icons, the purple, and all is right with the world again. Except for what governments are doing to reporters and dissidents and Muslims and human rights workers of course (vomit).
@ gk: I am using the…
@ gk:
I am using the version of Tor Browser 8.5 included in Tails 3.14 (the current version).
Apologies for not understanding that the security slider move is intentional. I think I agree with the objections raised by two posters. Understand what you said about why you made the change but it seems education is the answer not creating new potential for goofs.
I have a more serious issue: I am not seeing the Noscript icon at all. Further, checking add-ons seems to show that NoScript has not been updated since 1 Jan 2000. That cannot be right. (Ublock origin seems sensible in comparison.) As far as I can see Noscript has been disabled in TB 8.5 as included in Tails 3.14. Surely that is not intentional? Or am I missing something?
gk said in another reply…
gk said in another reply above that the nonappearance of the NoScript icon where it used to be is intentional, so never mind.
With all the issues last…
With all the issues last month with NoScript suddenly disappearing due to an expired certificate, why on earth would this new release drop the NoScript Icon from the visible menu. Shouldn't this icon be prominently displayed in plain view, so we can at least feel comfortable that it is present and active?
That's because the NoScript…
That's because the NoScript UI in itself is confusing (we have even bug reports in our own bug tracker about it) and there are risks that you make changes in its settings that make you stand out of Tor Browser users. Tor Browser users should not need to mess with NoScript at all. But you are of course free to add it back to your toolbar if you feel more comfortable that way. (FWIW: you got a big yellow warning that the extension got disabled with a link to learn more (I think) that you would get even if the NoScript icon is not visible on the toolbar anymore).
I was one of those who…
I was one of those who panicked (embarrased) but now I think I agree with the change. The timing was unfortunate but I think we're all good now.
> Tor Browser users should…
> Tor Browser users should not need to mess with NoScript at all.
Many users don't want ads or scripts that cripple responsiveness, so they have to mess with NoScript. All or nothing is not feasible all the time.
That's a big fingerprinting…
That's a big fingerprinting risk for what it is worth. But, yes, *if* one really feels okay with that risk there is always the option to customize the toolbar and get the NoScript icon to appear again.
Noice. Thanks.
Noice. Thanks.
How to enable copy pasting…
How to enable copy pasting of text in the Tor Browser for Android?
Does long-pressing on the…
Does long-pressing on the text highlight part of it? If you select the text you want to copy, then you remove your finger the browser should show you an options menu with options for "copy". When you want to paste the text, long-pressing in a text box should show an options menu with "paste".
Why do "improvements in UX"…
Why do "improvements in UX" always mean hiding user security choices behind menus?
Some time ago, turning images/javascript on and off disappeared from the options into the about:config.
Now the security settings slider has disappeared into the options,
Could you please give an option that makes...
1. images on/off
2. javascript on/off
3. security slider
...available through some option?
In other words, please stop making security choices a pain in the ass. This is not Internet Explorer.
You needed two clicks for…
You needed two clicks for setting the slider deep down in the Torbutton menu and had no clue afterwards which security state you are actually in because there was no hint in the browser UI about that. Now, you need two clicks to set the slider and see your security level prominently in the UI. So, I don't see how we regressed here in the sense that we suddenly started hiding things in menus?
Regarding your other points: I am not convinced we should have an option to disable images. There might even be some obscure
about:configsetting supporting that already. I don't know. JavaScript is best disabled with the security settings by choosing the highest level.In about:config, set…
In about:config, set permissions.default.image to 2 which allows you to manually choose to load an image from some page, but images will not be loaded by default. This behavior will be noticed by the webserver at the other end of your Tor circuit and will make you stand out way out. But sometimes there might be good reason to take the risk of deanonymization to an attacker with near global presence.
Hello! Isn't there the…
Hello!
Isn't there the option to view circuits in Tor browser for Android?
I can't finding that. :-(
Still not implemented. :(…
Still not implemented. :( See: https://trac.torproject.org/projects/tor/ticket/25764.
Hi, When will the point…
Hi,
When will the point release be issued that fixes the rest of the accessibility bugs on Windows?
Thanks.
In June. The exact date is…
In June. The exact date is not set yet. We still need to polish our patches and test them properly. I know this takes long but the work is not trivial. :(
Have you considered that…
Have you considered that exposing
about:preferencesevery time someone changes the security level may encourage them to believe that changing other settings listed on that page is equally okay? Why are "Safer" and "Safest" now called "Advanced" settings which newbies are trained in most other contexts to interpret as to avoid changing them from their default "Standard"?Yes, we did. There is…
Yes, we did. There is earlier in this blog an explanation of our reasoning by me. I hope it makes some sense.
I've been using Tor long…
I've been using Tor long enough to have some appreciation of how difficult it is to design a user interface which confuses no-one given the technical threats Tor users face, the enormous linguistic diversity of Tor user base, the technical knowledge diversity of the Tor user base, all on top of the fact that TP must build TB on top of FF, NoScript, etc., which are made by others who design their own interfaces to meet their own criteria. It is inevitable that there be some back and forth as we search for the current optimum UI.
Hi there, The app seems to…
Hi there,
The app seems to have a problem with connecting to Bridges? I run a bridge (obfs4) and am trying to connect using my known good (work just fine in desktop TBB) Bridge config line. Unfortunately in the app it doesn't work at all.
Any chance bridge connections will get some love soon?
Mike
Are you entering the bridge…
Are you entering the bridge details the same way on desktop as on mobile? Which parts do you add? type ip:port fingerprint cert=... iat-mode=...?
[b]NoScript v10.6.2[/b]…
NoScript v10.6.2 released - (May 22, 2019)
NoScript - Mozilla-Extension - Firefox (en-US)
: https://addons.mozilla.org/en-US/firefox/addon/noscript/
NoScript - ChangeLog : https://noscript.net/changelog
NoScript - FAQ : https://noscript.net/faq
NoScript - Forum : https://forums.informaction.com/viewforum.php?f=3
NoScript - Redit : https://old.reddit.com/r/noscript/new/
> It's Official: Tor Browser…
> It's Official: Tor Browser is Stable on Android
>
> Tor Browser 8.5 is the first stable release for Android. Since we released the first alpha version in September, we've been hard at work making sure we can provide the protections users are already enjoying on desktop to the Android platform. Mobile browsing is increasing around the world, and in some parts, it is commonly the only way people access the internet. In these same areas, there is often heavy surveillance and censorship online, so we made it a priority to reach these users.
This is a huge milestone for our community! Even though I avoid using smart phones (which renders me suspicious according to the IJOP app categories just revealed at hrw.org--- US does like CN, only with great secrecy while CN wants their citizens to know they will suffer govt reprisals for "social deviance" or failure to follow the state religion (CCP), or political dissidence) I am greatly heartened.
Thanks also to the media outreach team for some all too rare positive mentions in some tech publications; see in particular
zdnet.com
First official version of Tor Browser for Android released on the Play Store
After eight months of alpha testing, Tor Browser for Android is now ready for rollout.
Catalin Cimpanu for Zero Day
21 May 2019
> Today, the Tor Project released on the Google Play Store the first stable version of the Tor Browser for Android. This new mobile browser integrates the Tor protocol stack into a standalone browser and replaces Orfox as the main way to navigate the Tor network from an Android device. Tor Project developers have been working on this browser for eight months now, since September 2018, when they first released an alpha version for public testing. "We made it a priority to reach the rising number of users who only browse the web with a mobile device," said Isabela Bagueros, Executive Director of the Tor Project. "These users often face heavy surveillance and censorship online, so it is critical for us to reach them." "We made sure there are no proxy bypasses, that first-party isolation is enabled to protect you from cross-site tracking, and that most of the fingerprinting defenses are working," the Tor team added.
And it continues in that positive vein. Wow, how nice to see a reporter saying nice things about Tor Project! :-)
Some websites there is no…
Some websites there is no tor circuit when you click on the information icon. Why?
Not sure. Do you have…
Not sure. Do you have examples?
I guess he observes that bug…
I guess he observes that bug - https://blog.torproject.org/comment/280775#comment-280775
Unfortunately I still have no reproduction steps.
(May be issue appears on new- tabs and existing- tabs, after "Youtube watching on other tabs" , but I am not sure)
Great, thanks for the…
Great, thanks for the Improved Security Slider Accessibility! I love it this way.
One problem is big with Tor browser for a while, Google Captcha challenge aren't working properly. You enter the right solution but Google Captcha say wrong. Is there a fix or a work around? Thanks
Do you have an example…
Do you have an example website we can use to test the captcha?
I have not posted here for…
I have not posted here for the last 3 or 4 releases as I appreciate what you do and didn't wish to complain. I do miss from 4 changes ago the 8? squared section allowing you to choose search engines at your fingertip even though I know it is gone for security reasons. Also, I see that the next release, if I understand correctly, will stop the NoScript flash page that overshadows the screen and is relentless as a damn captcha. I do so much miss the, literally, iconic logo icon that said TOR. I loved looking at that Tor icon. It was pure class. Thanks anyway for Tor!
> 8? squared section…
> 8? squared section allowing you to choose search engines at your fingertip
Type keywords in the address bar, and search engine icons fall under it. Press Enter for the default search engine. Another way, customize the toolbar and drag "Search" box. Click the magnifying glass to see search engine icons. Another way, open hamburger menu, Preferences, Search, and pick a default, enable, disable, or reorder.
I miss that green onion logo…
I miss that green onion logo. My fault for not voting. Green onions are more versatile than purple onions; just riffing... Again, thank you for your constant work on Tor.
I would like to use it as my…
I would like to use it as my main browser on Android. However you can not download images and downloads can not be canceled and sometimes the tabs that I have open are blank or reload.
Does this still happen with…
Does this still happen with the stable release? Which Android version and device do you have? Do you have an example link which we could test the download issues with?
For the hard work of the Tor…
For the hard work of the Tor team and delivering.
Anyway, thank you again for this great update.
Regarding the issue with…
Regarding the issue with transferring bookmarks, that is a problem. We're still considering the best solution here because Firefox Sync is not available on Android. We were more concerned with stabilizing Tor Browser on Android, so that was our priority. Now we'll concentrate on solving bugs and making the browser more usable (including migrating bookmarks from the Alpha version to Stable). We still have a lot of work in front of us.
People actually voted for…
People actually voted for that logo? It's terribly bland, generic, and meaningless.
I was initially taken aback…
I was initially taken aback also, but after using 8.5 for an hour or so I decided I like the new icons, the new security slider, and can live with the absence of the ferocious NoScript symbol in the tool bar.
By the way, some Tor Browser newbies found it very offputting that when they tried to watch a youtube video they saw the NoScript icon which they misinterpreted I think as some nasty hacker messing with them, not as a the good guys preventing their browser from doing something dangerous. I think it would be very useful if Tor Project posts in this blog an explanation of how to watch youtube videos as safely as possible using Tor Browser. If this is in fact possible to do, of course--- some people tell me it is. The post should explain why watching youtube videos without protections can be dangerous, in particular why NoScript is likely to object.
when they tried to watch a…
Indeed. The icon of NoScript on click-to-play yellow sheets does not look like any icons of Mozilla or Tor Project. As Tor Project hid the icon from the toolbar, it is not introduced anymore as a bundled component, but jarringly introduced when browsing casually.
They should ask people on…
They should ask people on deviantArt.
A contest commending their…
A contest commending their strengths could raise interest about Tor Project and increase collaboration with communities less aware of privacy tools and practices.
why are there to versions on…
why are there to versions on f-droid ? which is the right one ?
There is an alpha version (…
There is an alpha version ("Alpha" in the name) and a stable one. If you feel like trying to find bugs and test out the latest features use the alpha one, otherwise sticking to the stable one sounds like a good idea.
So it will only be on the…
So it will only be on the guardianproject repo? Not regular F-droid?
I noticed some small issues with the current F-droid listing, the license link is 404 and the "Alpha" still says it requires Orbot.
A changelog link would be nice also.
We should have Tor Browser…
We should have Tor Browser in regular F-Droid soon, see: https://trac.torproject.org/projects/tor/ticket/27539.
Great job! Thank you.
Great job! Thank you.
Is it known that this and…
Is it known that this and the previous versions of TOR does not work while within a sandbox?
"DLL Initialization Failed.
C:\program files\sandbox\SbieDll.dll failed. The process is terminating abnormally."
I have tried opening a bug report, but something is broken about it and it refuses to let me log into it. Sorry.
sandboxie worked properly…
sandboxie worked properly until TBB 7.5.x
i searched the (old) forum, could read 'sandboxie does not support TorBrowser' and nothing about this dll-error.
finally i moved to Linux to be able to use a sandbox.
I am excited about the first…
I am excited about the first Android Tor Browser release! When are you going to update the TBB manual? It is not for mobile but only for desktop.
I would like to introduce my mum to TBB - she attended a conference, discovered the Internet is a weird place and now feels the need of some protection - but I hesitate to do that until there will be a proper Tor Browser Manual for Android. Why?
Simply because she is close to 70, she loves her tablet (the only technological devices she uses in order to surf the Internet) but her mind is not exactly elastic with technology (an example: she has a bunch of post-it where she wrote the whole procedure in order... to print a document :-D ). So, she needs a kind of support for when I am not there (and I do not want she feel mortified or not smart enough when something goes wrong: for her this would mean giving up immediately with TBB and going back to something else).
Thanks.
We have plans in the works…
We have plans in the works to get an Android manual up and running, though I don't have a specific ETA to give you. Thanks for your feedback!
Usability feedback from your…
Usability feedback from your mum would be valuable. Read:
https://blog.torproject.org/strength-numbers-usable-tools-dont-need-be-…
https://blog.torproject.org/tors-open-research-topics-2018-edition (under Application Research: Usability)
https://blog.torproject.org/tor-tails-ux-identifying-user-needs-cryptor…
https://en.wikipedia.org/wiki/Contextual_inquiry
Antonela or Pili might like to establish contact with you.
Popup-GUI from…
Popup-GUI from HTTPSEverywhere2019.5.6.1 more blurry, than versions before.
If this is intentional, why not asking Facebook&Co, masters of practical gui for users... .
HTTPS Everywhere is not made…
HTTPS Everywhere is not made by Tor Project. It's made by Electronic Frontier Foundation, EFF.
For the first - New icon is…
For the first - New icon is not bad and nice, thanks, BUT
1) I do not understand - WHAT DOWS ITS IMAGE ACTUALLY MEAN??? Onions??? O-O-O-O-O.... ?? )))
2) so - PLEASE BACK OLD GOOD GREEN ALL-WORLD ICON - as it is clear and already usual for Tor-users!
and Really, -
* new icon - does not brings any EXTRA value to users
* new icon - brings disharmony to stable users' perception of TBB
* new icon - is aligined with new logos\colors of site only (users do not care about)
* old icon - is usual
* old icon - is good for VISUAL observation as it was GREEN (green is known good color for sedation - it is about Human Psychology!)
* old icon - shows the World map - not some strange circles (regualar users know nothing about onion-circles, they need stability and protection - Green World is normal symbol of such things)
My vote is for OLD ICON! (purpule colors of site and browser you may keep - they are traditional for now already)
NEW ICON: "You are the…
NEW ICON: "You are the target" (Shooting target)
OLD ICON: "You are [probably] not alone!" (The world is not ending at your country - just look)
No no, Tor users are being…
No no, Tor users are not being targeted for mind control by TP, which would be bad; rather, the world is about to be torified, which will be good. Let me explain.
The purple icon indicates that Tor Project is plotting to take over University of Washington. And ComicCon. Then Microsoft Research. Then Microsoft itself. Then the Amazon globe. Which means taking over the entire freakin' world! Yeah!
(I confess I initially panicked over the purple, which is probably why I now find purple-hating angst funny. Maybe laughing at our own tendency to over-react is part of trying to maintain our sanity. On another level we know that looking out for minor visual discrepancies really can be a clue that Something Has Gone Seriously Wrong, so we should forgive ourselves for sometimes panicking when suddenly things look a little different from what we are used to.)
If given only those two…
If given only those two options, I would go with the green globe as well. A target doesn't give the right impression, nor represents "internet", but a simple globe for "internet" is maybe too generic.
Hi I am new to Tor , and not…
Hi
I am new to Tor , and not that tech savvy . My issue is that after installing Tor on Linux , thur the pen drive , Tor will get connected once on the linux system but the moment I close the window the Tor disappears and there is no Icon can be seen on the main page. Yes of course there is file which I some how extracted by watching few you tube videos. Now how can I install on the pen drive ?
Kindly advise
Regards
Could you elaborate? What do…
Could you elaborate? What do you mean by the main page? Do you mean the desktop area? Are you running Linux from the USB pen drive or just Tor Browser from the pen drive?
I downloaded and installed Tor Browser for Windows, but now I can't find it.
You can install Tor Browser on the pen drive by extracting or moving the tor-browser folder to the pen drive before you first open Tor Browser. The browser won't work if you move the folder after you first open the browser. Open the tor-browser folder, and open the file named start-tor-browser.
The Tor Browser tar.xz on Linux might not install a desktop icon because there are many varieties of Linux desktop environments that configure icons differently. Search the web for help to configure your desktop environment (GNOME, Cinnamon, KDE, Xfce, ...) main menu icons.
Bug 25013: Integrate…
Why for Android only?
Because we only needed it…
Because we only needed it for Android included directly. It was the least amount of work while working on a more generic solution for the ESR 68 transition.
Bug 29903: No WebGL click-to…
Hey, we don't want that fingerprinter active by default!
I kinda hate the security…
I kinda hate the security levels altogether. Id like to be able to manually control permissions by tracker like I always have without having to go into my addon settings, go to noscript and make an exception manually for each domain or page or override the security settings of all pages. Noscript is allowed to override, but at safest, scripts are greyed out on the trusted setting. Sometimes a site just won't work without scripts, but I always stay at safest by default. So a temp trust would be useless if it needs scripts. Can I please get noscript back on the toolbar? This feels like tor browser with training wheels.
Yes, you can. Just customize…
Yes, you can. Just customize your toolbar as you wish.
Bug 28002: Fix the…
and, probably, many others have already been backported to 8.0.9, so the changelog is not correct.
Thanks, fixed.
Thanks, fixed.
Hello, is there a way to…
Hello, is there a way to change the logo to the old one?
No.
No, unless you mess with the code every time you get a Tor Browser update.
Tor Browser is Stable on…
Tor Browser is Stable on Android? Time to update https://support.torproject.org/#tormobile
Security Level replaced Security Slider? Time to update https://tb-manual.torproject.org/security-slider/